ITIL Overview Elaine Riedel SECURA Insurance ITIL Information













- Slides: 20

ITIL Overview Elaine Riedel – SECURA Insurance

ITIL • Information Technology Infrastructure Library, ITIL is defined as a framework with a set of best practices for delivering efficient IT support services. . Companies adopt ITIL to realize their business benefits faster with defined processes and enabled by the right technology. • ITIL is the most widely adopted best practice for IT Service Management (ITSM) worldwide.


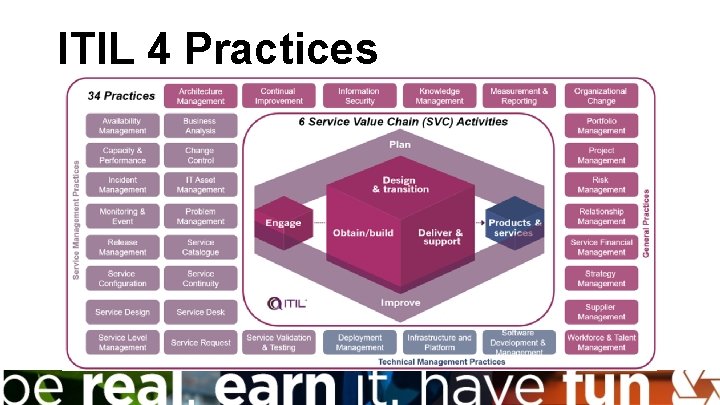
ITIL 4 Practices

Most Implemented ITIL 4 Processes • Request Mgmt: I want something NEW from IT. • Incident Mgmt: I had something and now it isn’t working. • Problem Mgmt: One or more incidents with the same root cause. • Change Mgmt: Minimize risk to business operations by coordinating changes in the IT environment. • Asset Mgmt: Tracking all IT assets (hardware, software, servers, routers, etc. )

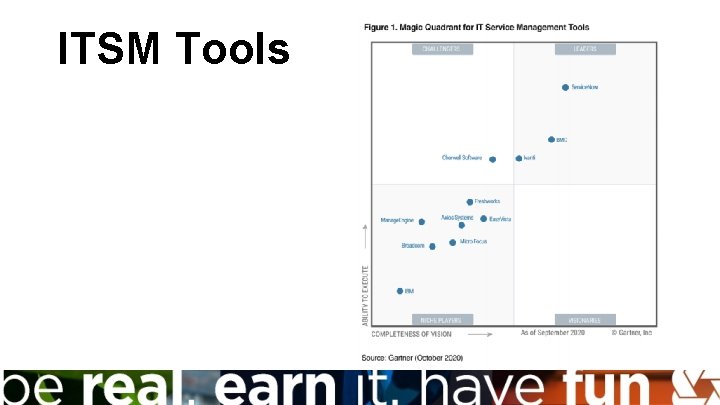
ITSM Tools

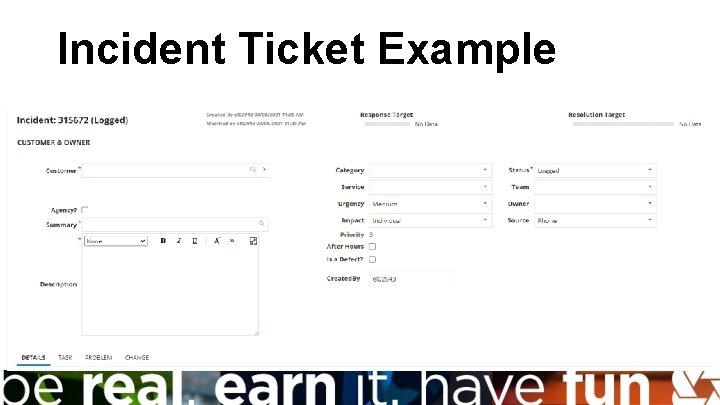
Incident Ticket Example

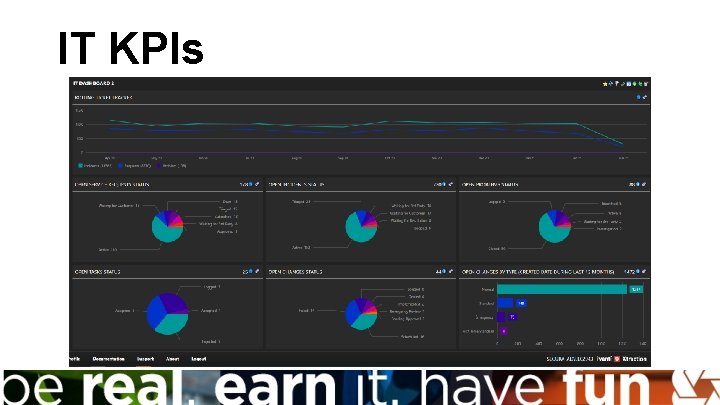
IT KPIs

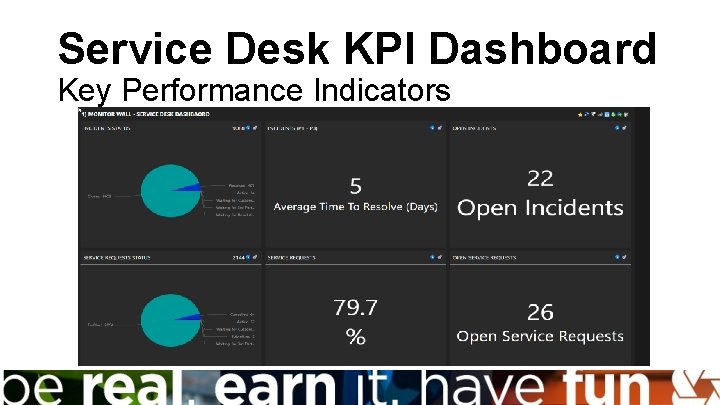
Service Desk KPI Dashboard Key Performance Indicators

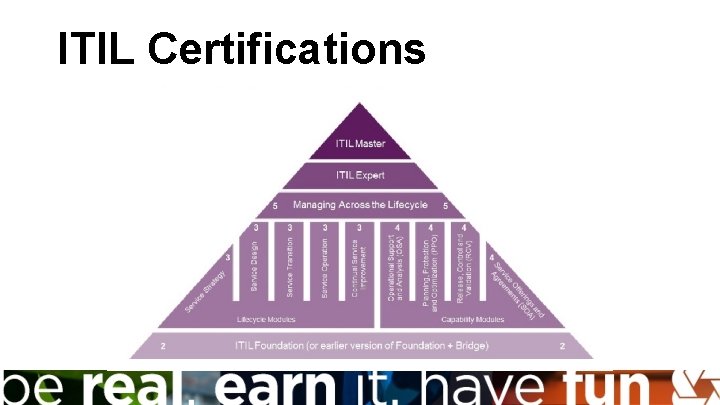
ITIL Certifications

Questions? ?

Information Security Practices and Certifications for Hacking into Your Career Brian Lindow SECURA Insurance

Latest Scary Stats • April 15 th 2021; US Formally Attributes Solar. Winds Attack to Russian Intelligence Agency • Ransomware damage costs to companies will be over $11. 5 billion in 2019 • A business will fall victim to a ransomware attack every 14 seconds • Biggest attack vector is by phishing email • 95% of all cyber attacks are financially motivated • 95% of all successful cyber attacks is cause by human error • The average time to identify a breach in 2020 was 228 days • Estimates show there have been as many as 192, 000 coronavirus-related cyberattacks per week in May 2020 alone, a 30% increase compared to April

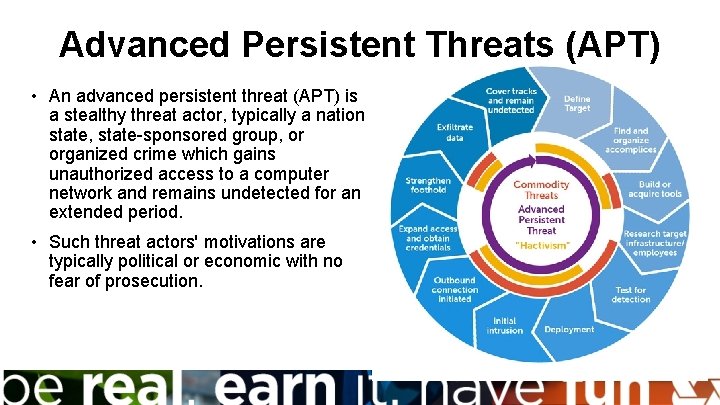
Advanced Persistent Threats (APT) • An advanced persistent threat (APT) is a stealthy threat actor, typically a nation state, state-sponsored group, or organized crime which gains unauthorized access to a computer network and remains undetected for an extended period. • Such threat actors' motivations are typically political or economic with no fear of prosecution.

Social Engineering

Social Engineering • “You don’t need as many technical skills to find one person who might be willing, in a moment of weakness, to open up an attachment that contains malicious content. ” • Only about 3% of the malware the bad actor runs tries to exploit a technical flaw. The other 97% is trying to trick a user through some type of social engineering scheme. • Classic phishing and spear phishing emails still work • Phone Impersonations or known of Vishing • Social Media Pretexting

Pillars of Information Security • Confidentiality, Integrity, and Availability (CIA) • Defense in Depth with layers of security controls • The employees are the new “human firewall” and keep training • A breach is a matter of “when” and not “if” • Practice the cyber breach response including the roles of the executives • Focus on protecting the “crown jewels” • “Zero Trust”: Newer concept centered on the belief that organizations should not automatically trust anything inside or outside

Careers in Cyber Security • Information Security Analyst/Engineer/Architect • Security Systems Administrator • Identity and Access Management (IAM) Analyst, Authentication and Authorization • Security Operations Center (SOC) staff • Forensic Security Analyst • Information Security Management/Chief Information Security Officer (CISO) • Penetration Tester/Ethical Hacker Information Security careers to grow by 31% in next ten years

Certifications in Cyber Security Courses can be taken by a wide variety of high education institutions • Certified Information System Security Professional (CISSP) • Certified Information Security Manager (CISM) • Certified Ethical Hacker (CEH) • Certified Cloud Security Professional (CCSP) Vendor specific such as: • Cisco Certified Network Professional (CCNP) • Microsoft 365 Certified: Security Administrator Associate • AWS Certified Security

Defending with Machine Learning • New vendors provide a device that plugs into the network/cloud and “learns” from looking at patterns in the network traffic. • The device capabilities include • Machine learning capabilities • Complex algorithms and probabilistic mathematics • Figures out the usual pattern of each user and device in a network. • After detection, the software can alert or stop the attack
 Https://www.servicetonic.es/service-desk/que-es-un-sla/
Https://www.servicetonic.es/service-desk/que-es-un-sla/ Itil brief overview
Itil brief overview Reidels
Reidels Riedel ryszard biografia
Riedel ryszard biografia Małgorzata pol riedel
Małgorzata pol riedel Ssi vorteile rechner
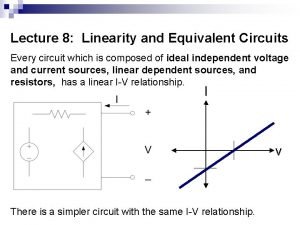
Ssi vorteile rechner Electric circuits by james nilsson and susan riedel
Electric circuits by james nilsson and susan riedel Riedel frota
Riedel frota Klaus riedel
Klaus riedel Nilsson riedel
Nilsson riedel Mexikaner ramstein
Mexikaner ramstein Theran riedel
Theran riedel Nature and use of fire insurance
Nature and use of fire insurance Iso 27001 itil
Iso 27001 itil Itil information technology infrastructure library
Itil information technology infrastructure library Elaine ferneley
Elaine ferneley Elaine allegretti barking and dagenham
Elaine allegretti barking and dagenham Elaine shi
Elaine shi Elaine falconer
Elaine falconer Dr elaine clark
Dr elaine clark Elaine mandel
Elaine mandel