ISOIEC 27001 2005 Specification for information security management










- Slides: 25

ISO/IEC 27001: 2005 Specification for information security management systems Presenter: Joe Otway 1

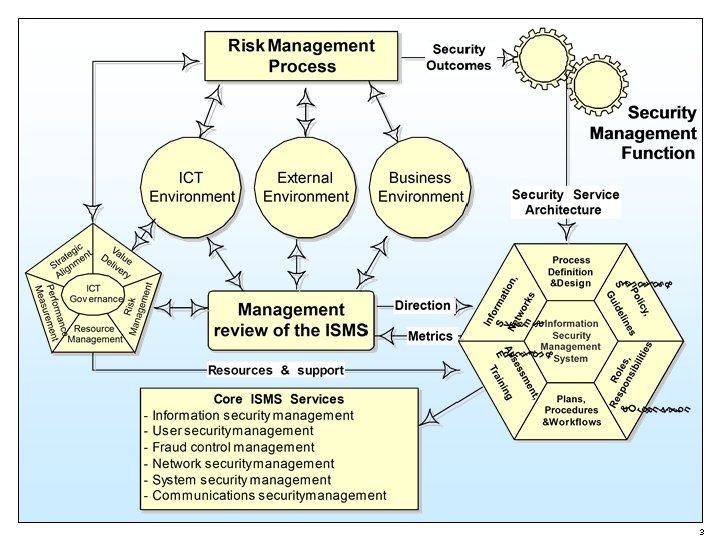
ISMS Concept The ISMS delivers security outcomes via security services that embody service management (ITIL, BS 15000 or AS 8018) processes and documentation. 2

3

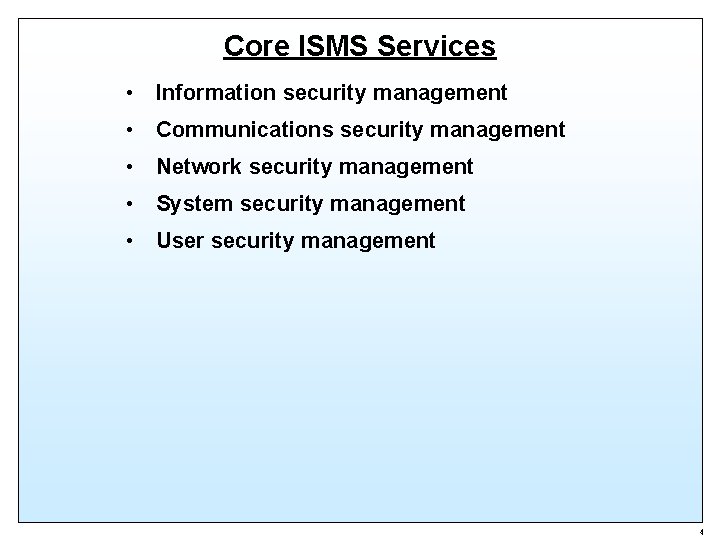
Core ISMS Services • Information security management • Communications security management • Network security management • System security management • User security management 4

Additional ISMS Services • Assessment, education & training • Asset management • Fraud control management • Compliance monitoring • Business continuity management • Incident management • Third party access management • Cryptography management • Intrusion prevention & detection • Software security management • Technical surveillance countermeasures 5

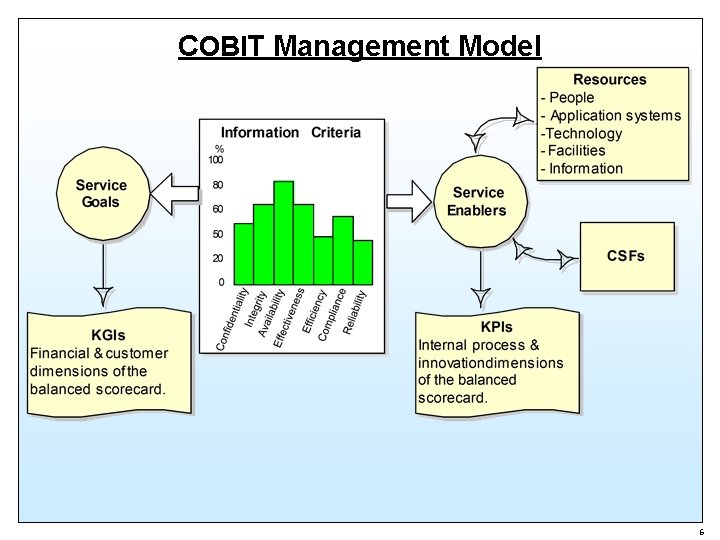
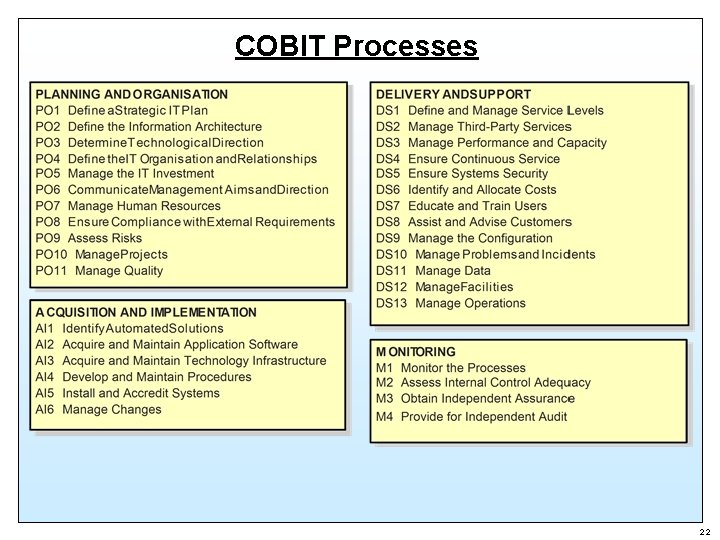
COBIT Management Model 6

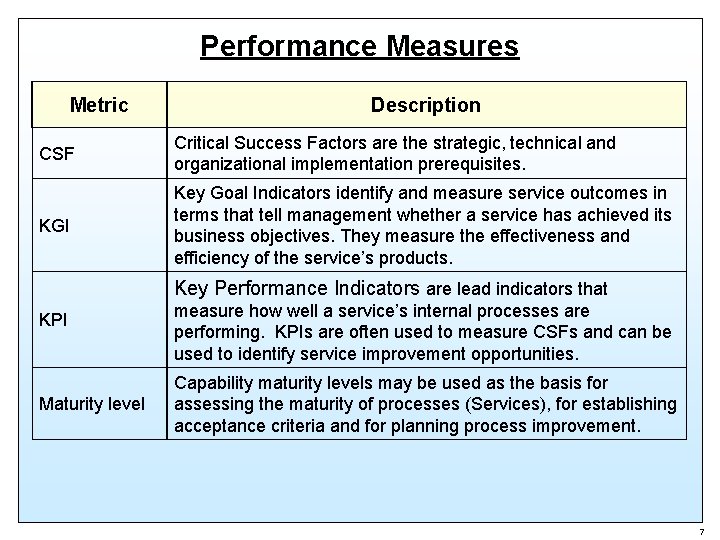
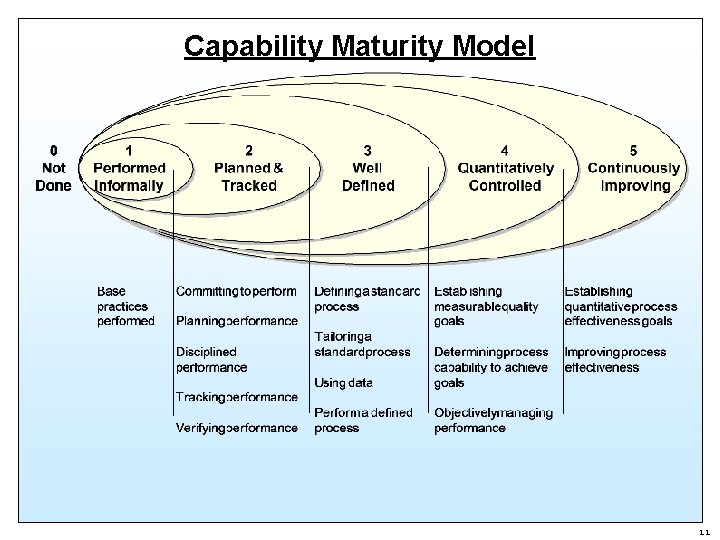
Performance Measures Metric Description CSF Critical Success Factors are the strategic, technical and organizational implementation prerequisites. KGI Key Goal Indicators identify and measure service outcomes in terms that tell management whether a service has achieved its business objectives. They measure the effectiveness and efficiency of the service’s products. Key Performance Indicators are lead indicators that KPI Maturity level measure how well a service’s internal processes are performing. KPIs are often used to measure CSFs and can be used to identify service improvement opportunities. Capability maturity levels may be used as the basis for assessing the maturity of processes (Services), for establishing acceptance criteria and for planning process improvement. 7

Example Critical Success Factors (CSFs) • Management agree the Service’s specification (goals & architecture) • Management agree the Service’s annual plan & budget • Service is integrated with ICT Governance framework • Appropriate resources (personnel & tools) are available to implement the Service’s annual plan • All Service personnel have the levels of competency necessary for them to function effectively & efficiently • Tools are available to audit the integrity of the Services’ information, systems and networks • Risks are managed effectively & efficiently • Incidents are managed effectively & efficiently • Service is managed effectively & efficiently 8

Example Key Goal Indicators (KGIs) • The ISMS has been audited this planning cycle • All ISMS Services have been audited this planning cycle • All ISMS Services are effective (satisfy their SLA’s) • All ISMS Services are efficient (satisfy their budgets) • No incidents reported • All incident investigations result in improvement proposals • All Service BCCPs have been tested and updated this planning cycle 9

Example Key Performance Indicators (KPIs) • Percentage of ISMS Services audited this planning cycle • Number of non-conformities revealed by audit • Percentage of ISMS Services that satisfy their SLA’s • Percentage of ISMS Services that satisfy their budgets • Number of incidents reported • Percentage of reported incidents investigated • Percentage of improvement recommendations implemented • Percentage of staff turnover • Average duration of Service security patch/upgrade application cycle • Average duration of Service change application cycle 10

Capability Maturity Model 11

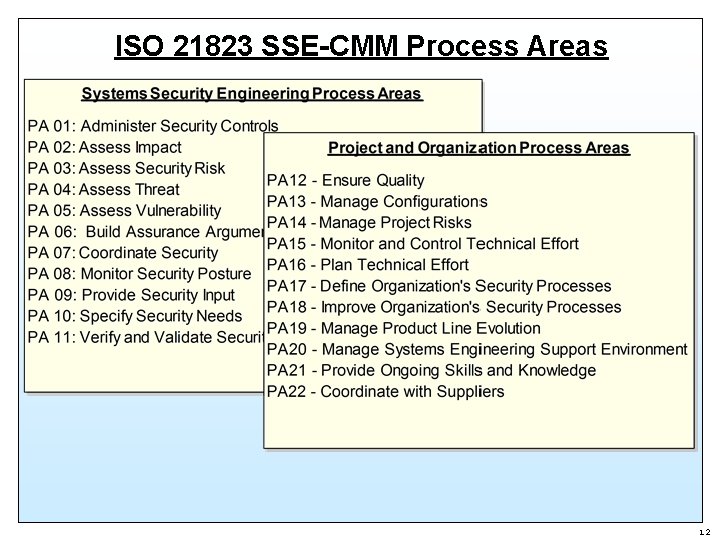
ISO 21823 SSE-CMM Process Areas 12

Capability Level 0 - Non-Existent Risk assessment for processes and business decisions does not occur. The organization does not consider the business impacts associated with security vulnerabilities and with development project uncertainties. Risk management has not been identified as relevant to acquiring IT solutions and delivering IT services. The organization does not recognize the need for IT security. Responsibilities and accountabilities are not assigned for ensuring security. Measures supporting the management of IT security are not implemented. There is no IT security reporting and no response process to IT security breaches. There is a complete lack of a recognizable system security administration process. There is no understanding of the risks, vulnerabilities and threats to IT operations or the impact of loss of IT services to the business. Service continuity is not considered as needing management attention. 13

Capability Level 1 - Initial/Ad-Hoc The organization considers IT risks in an ad hoc manner, without following defined processes or policies. Informal assessments of project risk take place as determined by each project. The organization recognizes the need for IT security, but security awareness depends on the individual. IT security is addressed on a reactive basis and not measured. IT security breaches invoke “finger pointing” responses if detected, because responsibilities are unclear. Responses to IT security breaches are unpredictable. Responsibilities for continuous service are informal, with limited authority. Management is becoming aware of the risks related to and the need for continuous service. 14

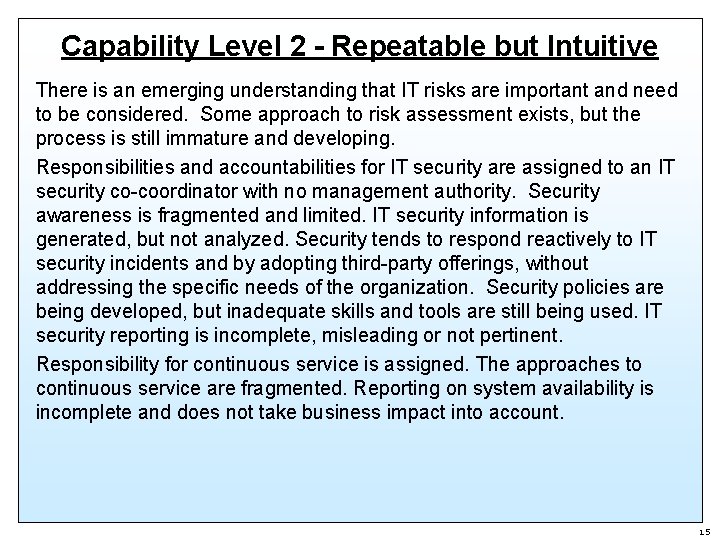
Capability Level 2 - Repeatable but Intuitive There is an emerging understanding that IT risks are important and need to be considered. Some approach to risk assessment exists, but the process is still immature and developing. Responsibilities and accountabilities for IT security are assigned to an IT security co-coordinator with no management authority. Security awareness is fragmented and limited. IT security information is generated, but not analyzed. Security tends to respond reactively to IT security incidents and by adopting third-party offerings, without addressing the specific needs of the organization. Security policies are being developed, but inadequate skills and tools are still being used. IT security reporting is incomplete, misleading or not pertinent. Responsibility for continuous service is assigned. The approaches to continuous service are fragmented. Reporting on system availability is incomplete and does not take business impact into account. 15

Capability Level 3 - Defined Process An wide-wide risk management policy defines when and how to conduct risk assessments. Risk assessment follows a defined process that is documented and available to all staff through training. Security awareness exists and is promoted by management. Security awareness briefings have been standardized and formalized. IT security procedures are defined and fit into a structure for security policies and procedures. Responsibilities for IT security are assigned, but not consistently enforced. An IT security plan exists, driving risk analysis and security solutions. IT security reporting is IT-focused, rather than business-focused. Ad hoc intrusion testing is performed. Management communicates consistently the need for continuous service. High-availability components and system redundancy are being applied piecemeal. An inventory of critical systems and components is rigorously maintained. 16

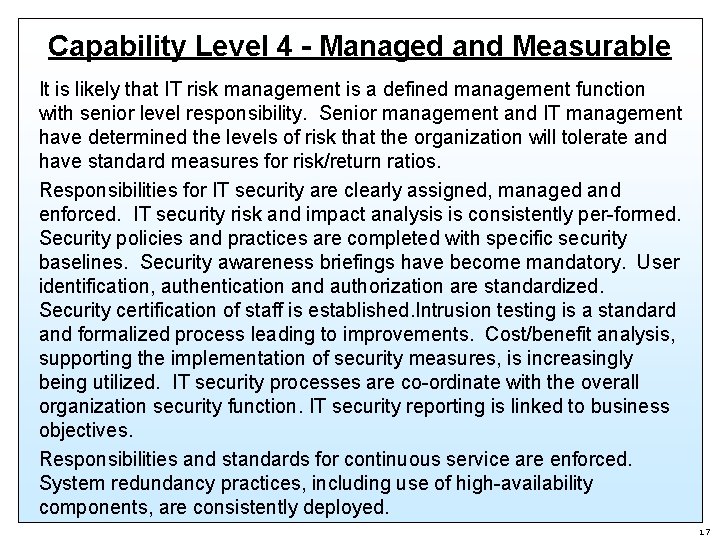
Capability Level 4 - Managed and Measurable It is likely that IT risk management is a defined management function with senior level responsibility. Senior management and IT management have determined the levels of risk that the organization will tolerate and have standard measures for risk/return ratios. Responsibilities for IT security are clearly assigned, managed and enforced. IT security risk and impact analysis is consistently per-formed. Security policies and practices are completed with specific security baselines. Security awareness briefings have become mandatory. User identification, authentication and authorization are standardized. Security certification of staff is established. Intrusion testing is a standard and formalized process leading to improvements. Cost/benefit analysis, supporting the implementation of security measures, is increasingly being utilized. IT security processes are co-ordinate with the overall organization security function. IT security reporting is linked to business objectives. Responsibilities and standards for continuous service are enforced. System redundancy practices, including use of high-availability components, are consistently deployed. 17

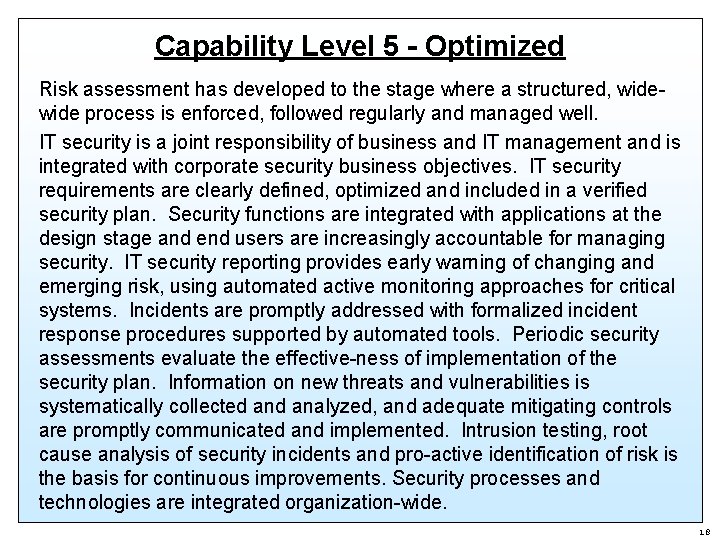
Capability Level 5 - Optimized Risk assessment has developed to the stage where a structured, wide process is enforced, followed regularly and managed well. IT security is a joint responsibility of business and IT management and is integrated with corporate security business objectives. IT security requirements are clearly defined, optimized and included in a verified security plan. Security functions are integrated with applications at the design stage and end users are increasingly accountable for managing security. IT security reporting provides early warning of changing and emerging risk, using automated active monitoring approaches for critical systems. Incidents are promptly addressed with formalized incident response procedures supported by automated tools. Periodic security assessments evaluate the effective-ness of implementation of the security plan. Information on new threats and vulnerabilities is systematically collected analyzed, and adequate mitigating controls are promptly communicated and implemented. Intrusion testing, root cause analysis of security incidents and pro-active identification of risk is the basis for continuous improvements. Security processes and technologies are integrated organization-wide. 18

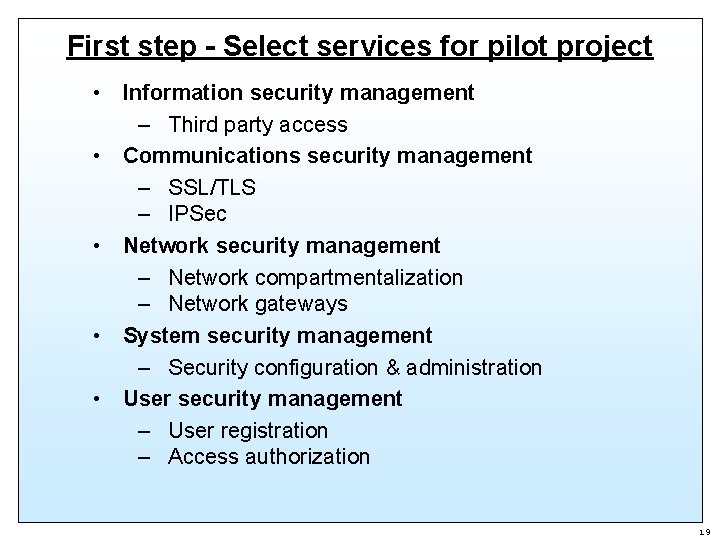
First step - Select services for pilot project • Information security management – Third party access • Communications security management – SSL/TLS – IPSec • Network security management – Network compartmentalization – Network gateways • System security management – Security configuration & administration • User security management – User registration – Access authorization 19

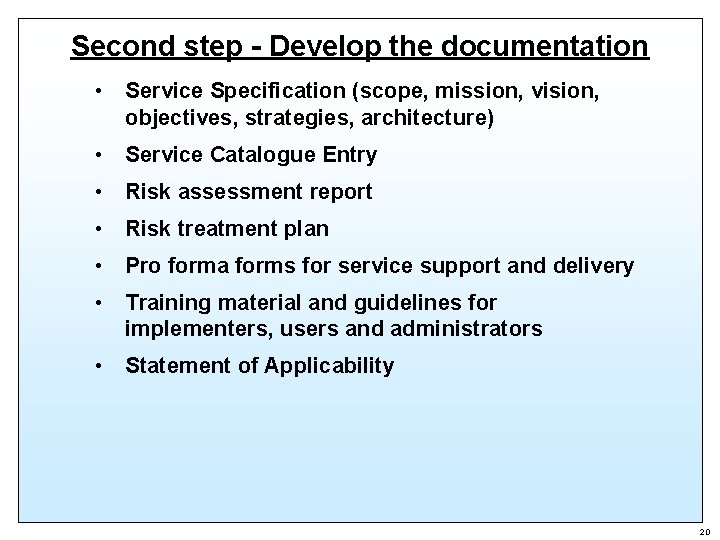
Second step - Develop the documentation • Service Specification (scope, mission, vision, objectives, strategies, architecture) • Service Catalogue Entry • Risk assessment report • Risk treatment plan • Pro forma forms for service support and delivery • Training material and guidelines for implementers, users and administrators • Statement of Applicability 20

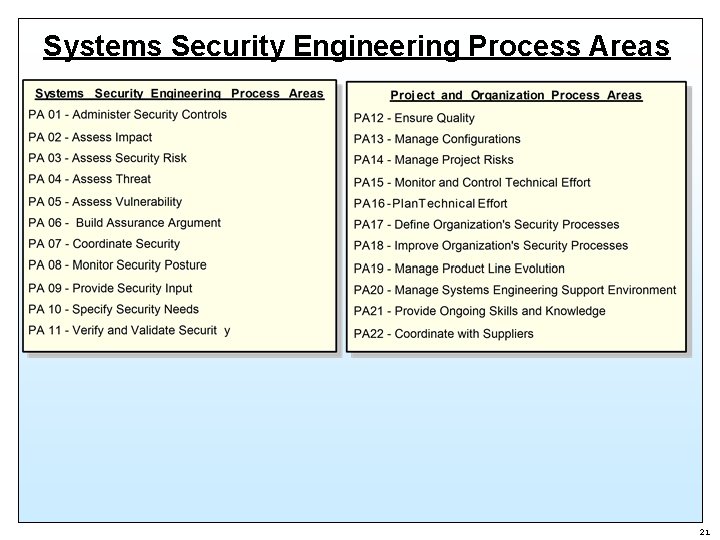
Systems Security Engineering Process Areas 21

COBIT Processes 22

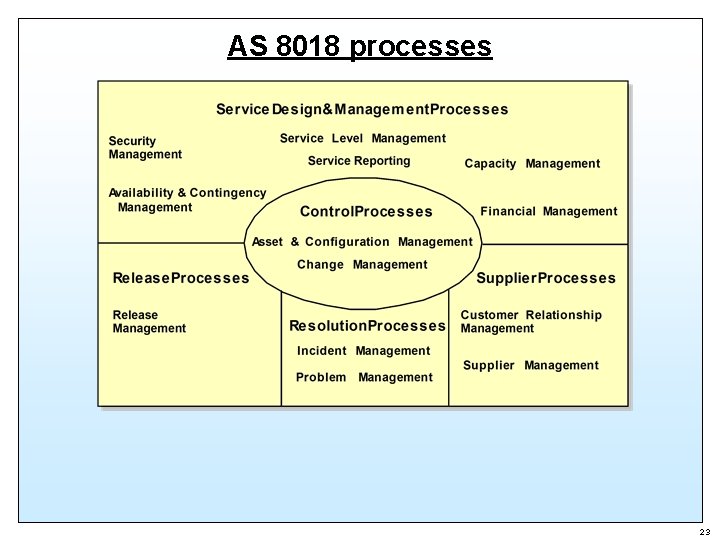
AS 8018 processes 23

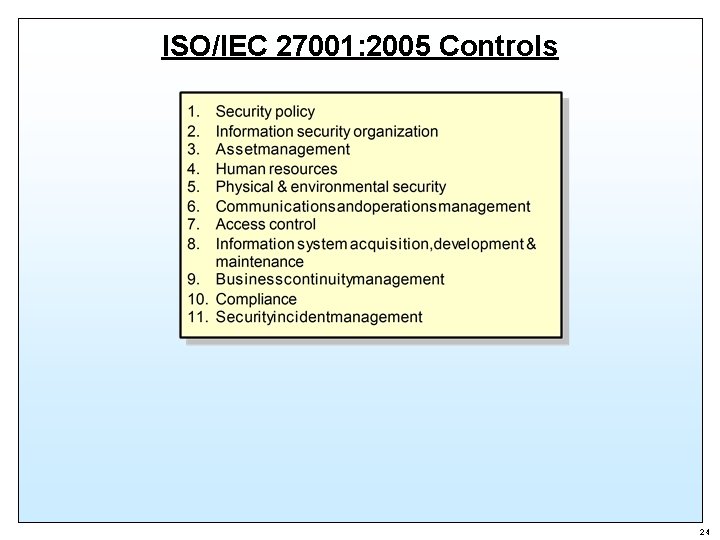
ISO/IEC 27001: 2005 Controls 24

ISO/IEC 27001: 2005 Specification for information Security Management Systems Presenter: Joe Otway 25