ISO 27001 Information Security Management Standard Experiences of















- Slides: 16

ISO 27001 Information Security Management Standard. Experiences of gaining accreditation Presented to an RSS Social Statistics Section/ASC Meeting, 20 May 2014 Data Privacy. Protecting Participant Identities. Randy Banks (randy@essex. ac. uk) Institute for Social and Economic Research http: //www. iser. essex. ac. uk @iseressex

Outline n n n ISER Description of ISO 27001 Effects of achieving ISO 27001 certification Costs ¨ Benefits ¨ n n Caveats Concluding thoughts RSS/ASS Meeting Data Privacy 20 May 2014 2

Institute for Social and Economic Research n n n Interdisciplinary socio-economic research department at the University of Essex ~80 staff, ~40 Ph. D students Specialise in longitudinal research and methodology Large number and variety of projects ranging from small, ad hoc studies to large, relatively permanent fixtures, e. g. : ¨ British Household Panel Survey ¨ Understanding Society ¨ ESRC Research Centre on Micro-Social Change ¨ EUROMOD Completely dependent on research income from clients and funders. ¨ n ESRC, EC, Government Departments, foundations, commercial and charitable organisations, etc. Certified to ISO 27001 in April 2013 RSS/ASS Meeting Data Privacy 20 May 2014 3

ISO 27001. What is it? n n ISO/IEC 27001. Information technology – Security Techniques – Information security management systems – Requirements. Second Edition. 2013 -10 -01. Information security – ‘preservation of confidentiality, integrity and availability [the CIA] of information’ (ISO 27000) ¨ n Confidentiality important, but not everything An information security management standard, not an information security standard Framework and process for developing an information security management system (ISMS) ¨ Tells you how to go about protecting your information, not what you should do to protect it ¨ Wide applicability ¨ n ISO 27002 provides implementation guidance ¨ BS ISO/IEC 27002: 2013. Information technology. Security techniques. Code of practice for information security controls RSS/ASS Meeting Data Privacy 20 May 2014 4

Structure n n n Preliminary clauses Mandatory clauses Information security controls RSS/ASS Meeting Data Privacy 20 May 2014 5

Mandatory Clauses n n N=7 Common to other ISO management standards Clause Coverage 4 Context of the organisation Understanding the organisation and its context, and Interested parties, defining the ISMS scope 5 Leadership Demonstrate management commitment, create information security policy, determination of roles and responsibilities 6 Planning Requirements for risk assessment and treatment, information security objectives and planning to achieve them 7 Support Resourcing, competence, awareness, documentation and communication 8 Operations, implementation of risk assessment and treatment 9 Performance evaluation Assessing the effectiveness of ISMS, internal audit and management review 10 Improvement Addressing non-conformities, continual improvement RSS/ASS Meeting Data Privacy 20 May 2014 6

Information Security Controls n n n Annex A. Reference control objectives and controls N = 114 grouped into 14 sections Maps to controls and references described in ISO 27002 ¨ n A. 5. * to A. 18. * Selected as a result of the risk assessment process and recorded as applicable or not in Statement of Applicability (SOA) – clause 6. 1. 3 RSS/ASS Meeting Data Privacy 20 May 2014 7

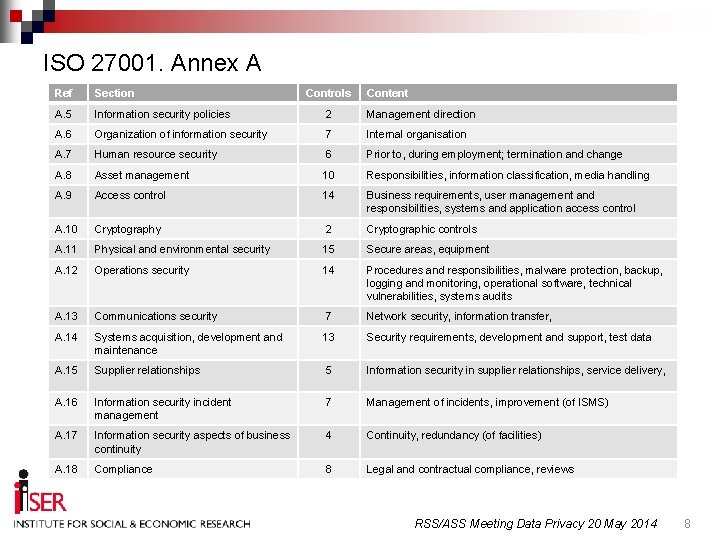
ISO 27001. Annex A Ref Section Controls Content A. 5 Information security policies 2 Management direction A. 6 Organization of information security 7 Internal organisation A. 7 Human resource security 6 Prior to, during employment; termination and change A. 8 Asset management 10 Responsibilities, information classification, media handling A. 9 Access control 14 Business requirements, user management and responsibilities, systems and application access control A. 10 Cryptography 2 Cryptographic controls A. 11 Physical and environmental security 15 Secure areas, equipment A. 12 Operations security 14 Procedures and responsibilities, malware protection, backup, logging and monitoring, operational software, technical vulnerabilities, systems audits A. 13 Communications security 7 Network security, information transfer, A. 14 Systems acquisition, development and maintenance 13 Security requirements, development and support, test data A. 15 Supplier relationships 5 Information security in supplier relationships, service delivery, A. 16 Information security incident management 7 Management of incidents, improvement (of ISMS) A. 17 Information security aspects of business continuity 4 Continuity, redundancy (of facilities) A. 18 Compliance 8 Legal and contractual compliance, reviews RSS/ASS Meeting Data Privacy 20 May 2014 8

ISO 27001. Costs n The standard(s) 27001 is crucial, but also 27002 and others in 27* series ¨ From British Standards Institute (50% discount for members) ¨ n n n Personnel ¨ Designated person with overall IS responsibilities and other personnel with newly defined responsibilities ¨ Additional meetings, e. g. regular management review, internal/external audits ¨ Regular access/operational reviews, risk assessments ¨ Training ¨ New procedures created/some procedures now more formalised - more time consuming Consultants (Continued re-) Certification ¨ (re) Certification Audit(s) ¨ Certificate(s) ¨ Surveillance audits RSS/ASS Meeting Data Privacy 20 May 2014 9

ISO 27001. Benefits n n n Competitive advantage ¨ ISO 27001 certification is increasingly required or positively encouraged by potential clients ¨ Assists in establishing compliance with other standards and requirements, e. g. HMG Security Policy Framework Culture change ¨ Increasing awareness of importance of information security in an interconnected world ¨ Expenditure on information security increasingly seen as business investment and enabler rather than technical overhead that inhibits achievement of business goals ¨ Information security management increasingly seen as everyone’s responsibility and not solely within the purview of the IT department More confidence that we are meeting our ethical, legal and contractual responsibilities RSS/ASS Meeting Data Privacy 20 May 2014 10

ISO 27001. Benefits (continued) n Improved – and continually improving - business and technical processes ¨ n Forced into better understanding of organisational functions and operations Impossible not to improve – 27001 forces you to continually reassess and requires you to demonstrate improvement RSS/ASS Meeting Data Privacy 20 May 2014 11

ISO 27001. What are the costs? n Can’t completely distinguish marginal costs of achieving ISO 27001 certification from: Costs of achieving good information security practice and contribution of 27001 certification to that end ¨ Efficiency gains from the formalisation and regular review of procedures ¨ Costs of implementing contractual requirements (other than 27001 certification) that would otherwise be required ¨ RSS/ASS Meeting Data Privacy 20 May 2014 12

Caveats n When speaking to suppliers ¨ ISO 27001 is not last word in information security n n n ¨ Beware of compliance claims not backed up by (plans for) certification n n Certification verifies compliance with the standard, not with specific measures that you might feel necessary Scope and SOA are critical Beware of excessive claims by suppliers about the relevance of ISO 27001 certification Certification is marginal cost after achieving compliance and When working towards certification ¨ Beware of template solutions and consultants who offer them n ¨ Don’t aim for perfection n ¨ Leads to unnecessary and irrelevant documentation ISO 27001 expects continual improvement Certification is long-term commitment n n Initial certification is followed by (bi)annual surveillance audits and recertification every 3 years Losing certification will cost a lot more than acquiring it in the first place RSS/ASS Meeting Data Privacy 20 May 2014 13

Concluding Thoughts 1. Jump before you’re pushed RSS/ASS Meeting Data Privacy 20 May 2014 14

Getting Help n n Online resources ¨ BSI – ISO/IEC 27001 Information Security resources (http: //www. bsigroup. com/en-GB/iso-27001 -informationsecurity/Resources-for-ISO-27001/) ¨ ECSC – ISO 27001 Executive Brief and email briefings (http: //www. ecsc. co. uk/papers. cgi? id=3) ¨ Information Security Standards (http: //www. iso 27001 security. com/) ¨ And others … Training ¨ BSI (http: //www. bsigroup. com/) ¨ SGS (http: //www. sgs. co. uk/) ¨ And others … RSS/ASS Meeting Data Privacy 20 May 2014 15

Thank you for listening. RSS/ASS Meeting Data Privacy 20 May 2014 16