ISOIEC 27001 2005 Information security management Part 2












- Slides: 13

ISO/IEC 27001: 2005 Information security management Part 2: Specification for information security management systems Presenter: Joe Otway 1

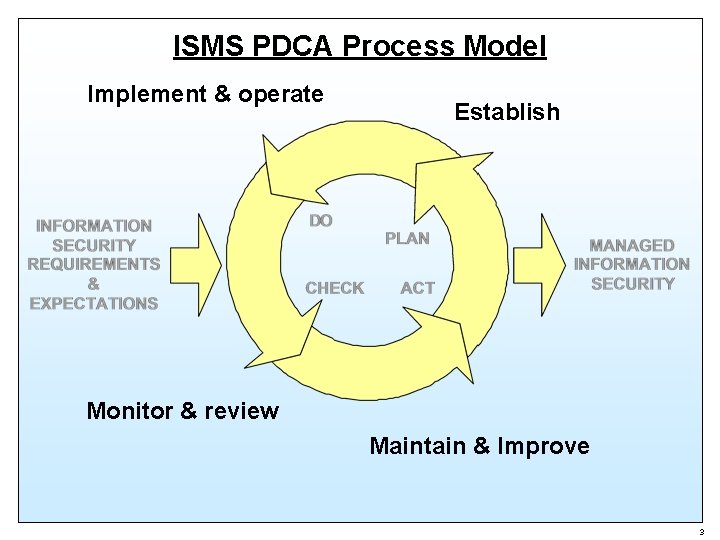
ISO/IEC 27001: 2005 - A Process Approach A process approach encourages its users to emphasize the importance of: • Understanding business information security requirements and the need to establish policy and objectives for information security; • Implementing and operating controls in the context of managing an organization’s overall business risk; • Monitoring and reviewing the performance and effectiveness of the ISMS; • Continual improvement based on objective measurement. 2

ISMS PDCA Process Model Implement & operate Establish Monitor & review Maintain & Improve 3

Plan - Establish the ISMS • Define the scope of the ISMS • Define an ISMS policy • Define a systematic approach to risk assessment • Identify the risks • Assess the risks • Identify & evaluate risk treatment options • Select control objectives & controls • Prepare a “Statement of Applicability” • Obtain management approval 4

Do - Implement & Operate the ISMS • Formulate a risk treatment plan • Implement the risk treatment plan • Implement selected controls • Implement training and awareness programs • Manage operations • Manage resources • Implement procedures and other controls capable of enabling prompt detection of and response to security incidents 5

Check - Monitor & Review the ISMS • Execute monitoring procedures and other controls • Undertake regular reviews of the effectiveness of the ISMS • Review the level of residual risk and acceptable risk • Conduct internal ISMS audits at planned intervals • Undertake a management review of the ISMS at least once a year • Record actions and events that could have an impact on the effectiveness or performance of the ISMS 6

Act - Maintain & Improve the ISMS • Implement the identified improvements in the ISMS • Take appropriate corrective and preventive actions • Communicate the results and actions • Ensure that the improvements achieve their intended objectives 7

Documentation Requirements • Documented statements of the security policy control objectives • The scope of the ISMS and procedures and controls in support of the ISMS • Risk assessment report • Risk treatment plan • Documented procedures & forms needed by the organization to ensure the effective management, operation and maintenance of its information security processes • Records required by ISO/IEC 27001: 2005 • Statement of Applicability 8

Documentation Control A documentation control system is required for the lifecycle control of: • Documents • Records 9

Management Responsibility • Management commitment – Strategic – Operational Resource management – Provision of resources – Training awareness and competency 10

Management Review of the ISMS ISO/IEC 27001: 2005 prescribes requirements for reviews of the ISMS including: • Review input • Review output • Internal ISMS audits 11

ISMS Improvement ISO/IEC 27001: 2005 prescribes requirements for ISMS improvement: • Continual improvement • Corrective action • Preventive action 12

ISO/IEC 27001: 2005 Information security management Part 2: Specification for information Security Management Systems Presenter: Joe Otway 13