INTRODUCING WINDOWS CARDSPACE James Kovacs James Kovacs com














- Slides: 25

INTRODUCING WINDOWS CARDSPACE James Kovacs James. Kovacs. com jkovacs@post. harvard. edu August 15, 2006

DEVELOPERS – ALWAYS THE LAST TO KNOW WCS Booth at Tech. Ed 2006 in Boston

AGENDA Identity and Access Management Digital Identity The 7 Laws of Identity Vision for an Identity Meta. System Applying theories Identity for Websites Identity for Distributed Applications

IDENTITY ACCESS AND MANAGEMENT � How many digital identities do you have? � Work Domain logon � SQL Server � Oracle � Various internal apps � Partner websites �… � � � Home computer(s) � Internet sites (lots!) � Your website/blog � Bank �… Result? � Weak passwords � Repeated passwords � Passwords in text files or on Post-Its

THREATS TO ONLINE SAFETY The Internet was built without a way to know who and what you are connecting to Internet services have one-off “workarounds” Inadvertently taught people to be phished Greater use and greater value attract professional international criminal fringe Exploit weaknesses in patchwork Phishing and pharming at 1000% annually Missing an “Identity Layer” No simplistic solution is realistic

LESSONS FROM PASSPORT Passport designed to solve two problems Identity provider for MSN 250 M+ users, 1 billion logons per day Identity provider for the Internet Unsuccessful Learning: solution must be different than Passport

THE LAWS OF IDENTITY AN INDUSTRY DIALOG 1. User control and consent 2. Minimal disclosure for a defined use 3. Justifiable parties 4. Directional identity 5. Pluralism of operators and technologies 6. Human integration 7. Consistent experience across contexts From www. identityblog. com

IDENTITY METASYSTEM � We need a unifying “Identity metasystem” � Protect applications from identity complexities � Allow digital identity to be loosely coupled: multiple operators, technologies, and implementations � Not first time we’ve seen this in computing � Emergence of TCP/IP unified Ethernet, Token Ring, Frame Relay, X. 25, even the not-yetinvented wireless protocols

WHAT IS A DIGITAL IDENTITY? A set of claims someone makes about me (the subject) A claim is an assertion of the truth about something A subject is an individual or other entity about which a claim is made Claims are packaged in security token which normally travels over process and machine boundaries

IDENTITY SELECTOR

CARDSPACE CARDS Steven Woodgate’s Card � Self-issued � � � Stored locally on Steven’s computer(s) Assertions about Steven Not corroborated Woodgrove Bank � Managed � � � Provided by banks, governments, clubs, enterprises, etc. Stored by identity provider Metadata only on client

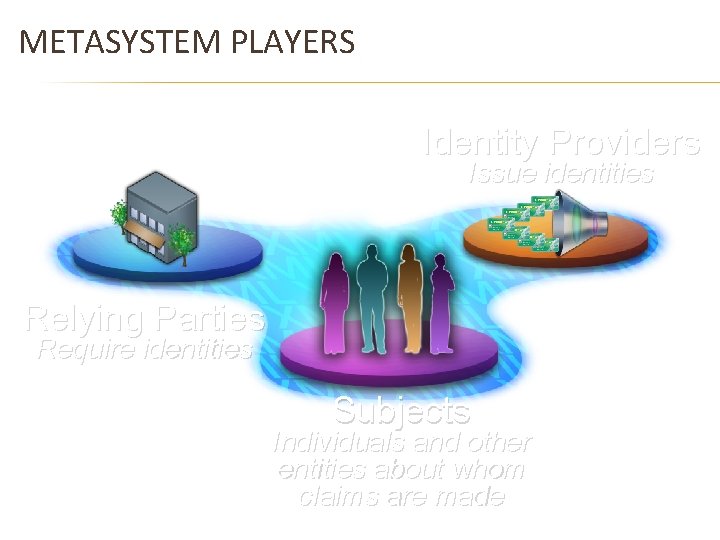
METASYSTEM PLAYERS Identity Providers Issue identities Relying Parties Require identities Subjects Individuals and other entities about whom claims are made

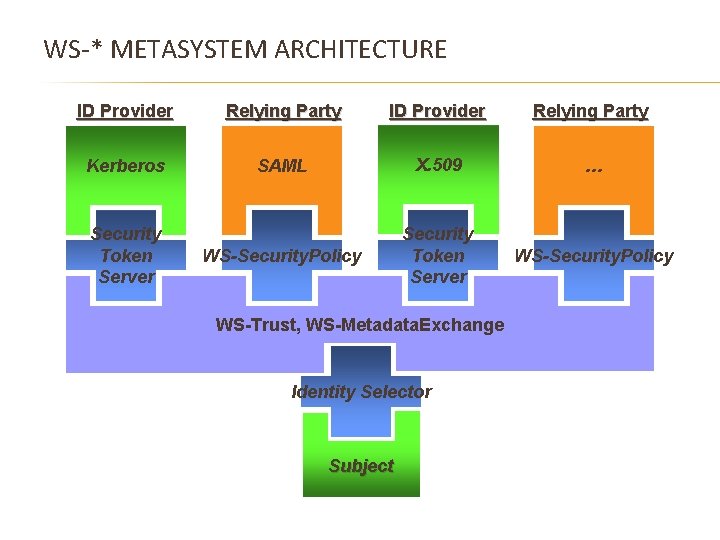
WS-* METASYSTEM ARCHITECTURE ID Provider Relying Party Kerberos SAML X. 509 … WS-Security. Policy Security Token Server WS-Trust, WS-Metadata. Exchange Identity Selector Subject

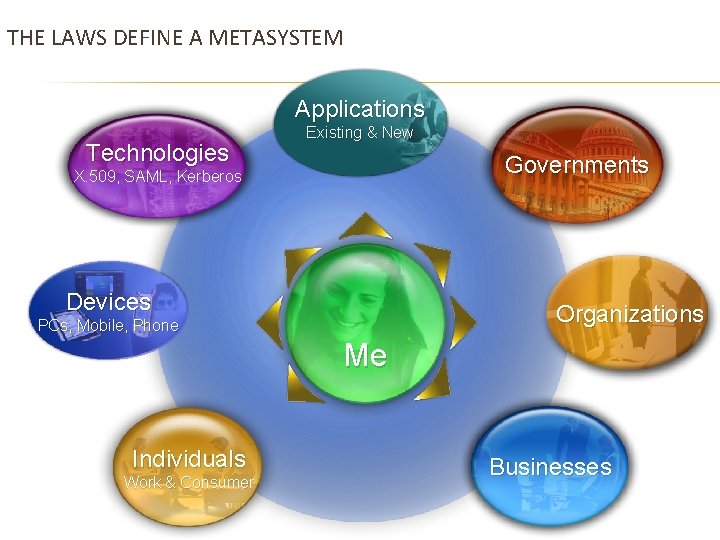
THE LAWS DEFINE A METASYSTEM Applications Technologies Existing & New Governments X. 509, SAML, Kerberos Devices Organizations PCs, Mobile, Phone Me Individuals Work & Consumer Businesses

CARDSPACE OVERVIEW Simple user abstraction for digital identity For managing collections of claims For managing keys for sign-in Grounded in real-world metaphor of physical cards Government ID card, driver’s license, credit card, membership card, etc. Self-issued cards signed by user Managed cards signed by external authority Implemented as secure subsystem Protected UI Anti-spoofing techniques Encrypted storage

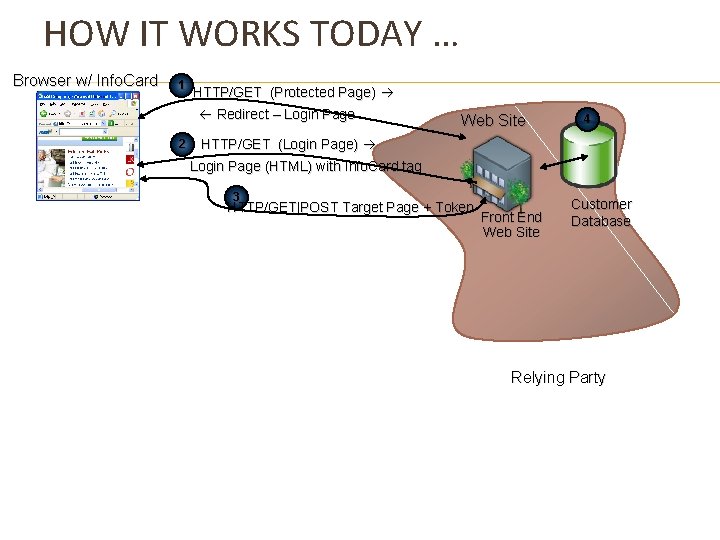
HOW IT WORKS TODAY … Browser w/ Info. Card 1 HTTP/GET (Protected Page) Redirect – Login Page 2 Web Site 4 HTTP/GET (Login Page) Login Page (HTML) with Info. Card tag 3 HTTP/GET|POST Target Page + Token Front End Web Site Customer Database Relying Party

IDENTITY SELECTOR - A SECOND LOOK

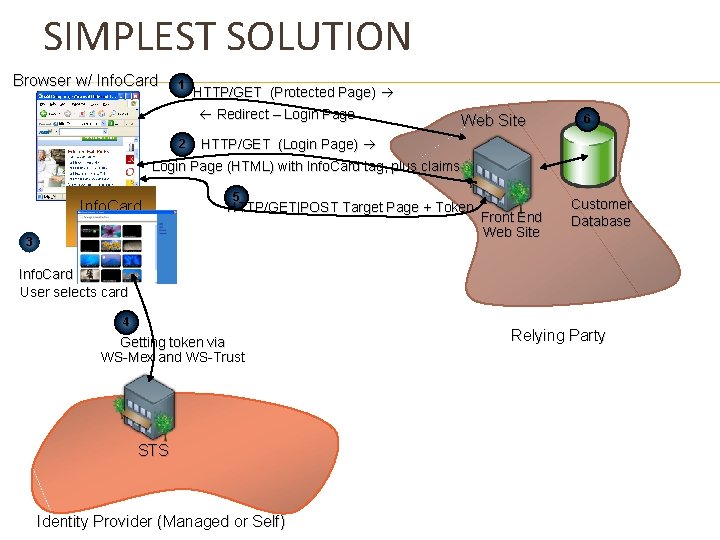
SIMPLEST SOLUTION Browser w/ Info. Card 1 HTTP/GET (Protected Page) Redirect – Login Page 2 Web Site 6 HTTP/GET (Login Page) Login Page (HTML) with Info. Card tag, plus claims Info. Card Service 5 HTTP/GET|POST Target Page + Token 3 Front End Web Site Customer Database Info. Card lights up User selects card 4 Getting token via WS-Mex and WS-Trust STS Identity Provider (Managed or Self) Relying Party

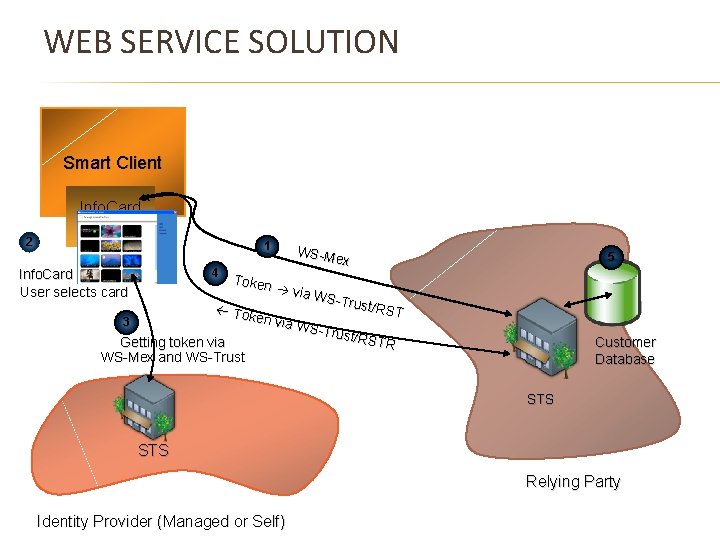
WEB SERVICE SOLUTION Smart Client 2 Info. Card Service 1 4 Info. Card lights up User selects card WS-M ex 5 Token via WS-T rust/R Tok ST en via 3 WS-T rust/R STR Getting token via WS-Mex and WS-Trust Customer Database STS Relying Party Identity Provider (Managed or Self)

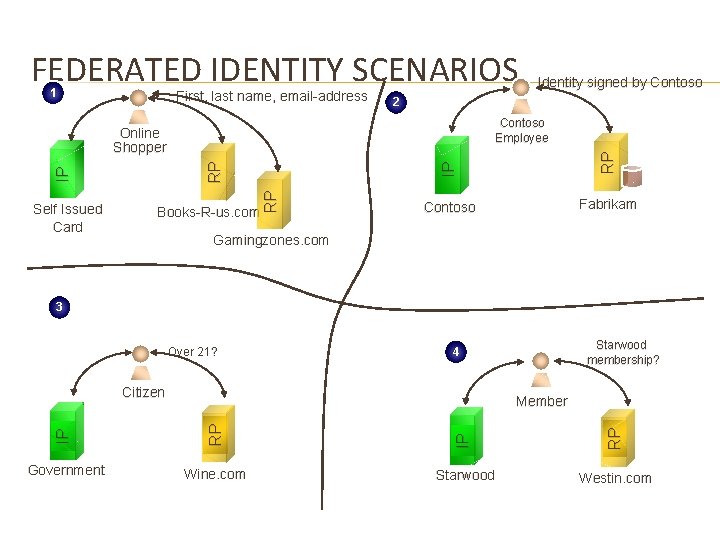
FEDERATED IDENTITY SCENARIOS 1 First, last name, email-address 2 Contoso Employee IP RP Books-R-us. com RP IP RP Online Shopper Self Issued Card Identity signed by Contoso Fabrikam Gamingzones. com 3 Over 21? Starwood membership? 4 Citizen IP RP Member Government Wine. com Starwood Westin. com

MICROSOFT’S IMPLEMENTATION � Component of. NET Framework 3. 0 � � Shipping in Vista and down-level for Windows XP SP 2 and Windows Server 2003 SP 1 Card. Space identity selector Usable by any application � Hardened against tampering and spoofing � � Card. Space simple identity provider Self-issued identity for individuals running on PCs � Uses strong public key-based authentication – user does not disclose passwords to relying parties � � Active Directory managed identity provider � � Plugs Active Directory users into the metasystem Full set of policy controls to manage use of simple identities and Active Directory identities

DEVELOPING FOR CARDSPACE

SUMMARY Laws of Identity define an identity metasystem � WS-* makes possible an identity metasystem using widely-accepted, published protocols � Microsoft implementing full support for an open identity metasystem in Windows � Microsoft not launching Son of Passport � “Now, with the debut of the Info Card identity management system, Microsoft is leading a network wide effort to address the issue. To those of us long skeptical of the technology giant's intentions, the plan seems too good to be true. Yet the solution is not only right, it could be the most important contribution to Internet security since cryptography. ” Lawrence Lessig, Wired Magazine, March 2006.

RESOURCES Windows Card. Space http: //wcs. netfx 3. com/ http: //sandbox. netfx 3. com/ Whitepapers Microsoft’s Vision for an Identity System (http: //tinyurl. com/p 2 moq) http: //www. identityblog. com/stories/2005/07/05/Identity. Metasystem. htm Laws of Identity (http: //tinyurl. com/cuhb 2) http: //www. identityblog. com/stories/2004/12/09/thelaws. html Identity Blogs Kim Cameron http: //www. identityblog. com Andy Harjanto http: //blogs. msdn. com/andyhar

QUESTIONS James. Kovacs. com jkovacs@post. harvard. edu