INFOCOM 2007 Landmark Selection and Greedy LandmarkDecent Routing

- Slides: 23

INFOCOM 2007 Landmark Selection and Greedy Landmark-Decent Routing for Sensor Network An Nguyen, Nikola Milosavljevic, Qing Fang, Jie Gao, and Leonidas J. Guibas Dept. of Computer Science, Stanford University 산업 및 시스템 공학과 통신시스템 및 인터넷보안연구실 20075273 김효원

Outline § § § Introduction Landmark Selection Landmark Descent – Greedy Rule Simulations Conclusion 2 Telecommunication System & Internet Security Lab.

§ § § Introduction Landmark Selection Landmark Descent – Greedy Rule Simulations Conclusion 3 Telecommunication System & Internet Security Lab.

Introduction § Implementation of scalable point to point routing § Geographic location based method § Greedy routing § Robust to sensor location inaccuracy § Do not guarantee packet delivery rate § Face routing § Overcome problems of greedy routing § Use planar graph but fail in real world deployment § Accurate geographic location information is difficult and expensive to obtain, § Location free routing schemes have been developed 4 Telecommunication System & Internet Security Lab.

Introduction § Implementation of scalable point to point routing § Geographic location free method § Several virtual coordinate system use landmark § GLIDER (Gradient Landmark-based Routing) § BVR (Beacon Vector Routing) § Landmark-based schemes are favored by simplicity and independence of network, § and can be easily extended to sensors deployed in 3 D → In this paper, propose 1. 2. Distributed landmark selection protocol Greedy Landmark Descent Routing (GLDR) 5 Telecommunication System & Internet Security Lab.

§ § § Introduction Landmark Selection Landmark Descent – Greedy Rule Simulations Conclusion 6 Telecommunication System & Internet Security Lab.

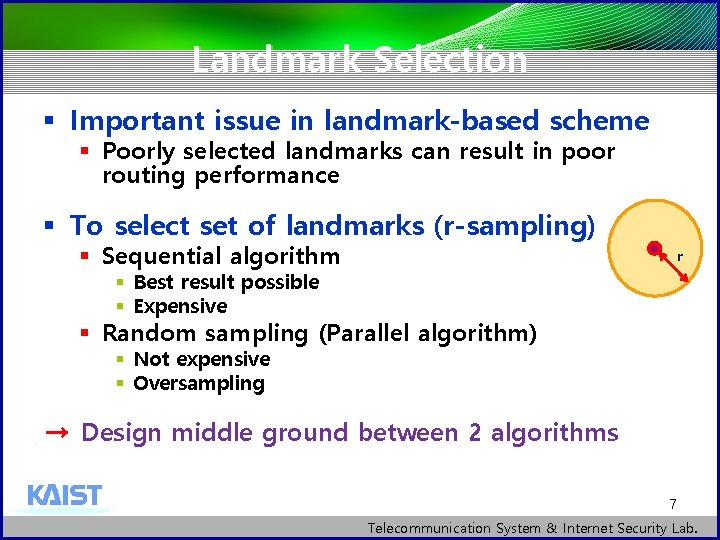
Landmark Selection § Important issue in landmark-based scheme § Poorly selected landmarks can result in poor routing performance § To select set of landmarks (r-sampling) § Sequential algorithm r § Best result possible § Expensive § Random sampling (Parallel algorithm) § Not expensive § Oversampling → Design middle ground between 2 algorithms 7 Telecommunication System & Internet Security Lab.

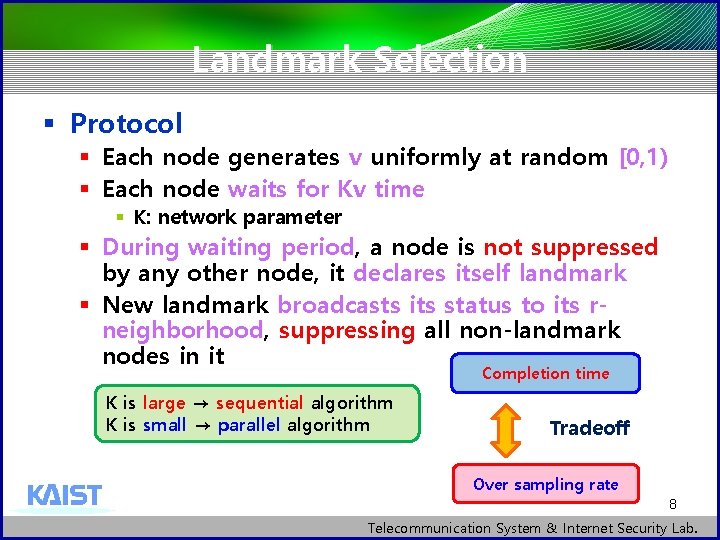
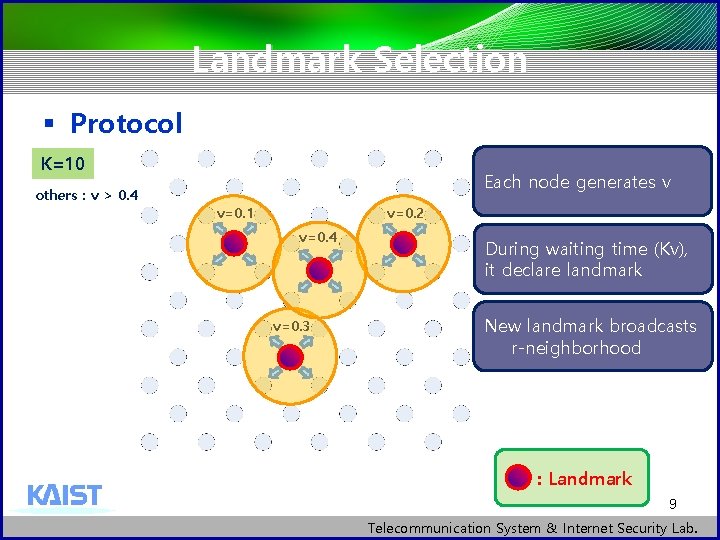
Landmark Selection § Protocol § Each node generates v uniformly at random [0, 1) § Each node waits for Kv time § K: network parameter § During waiting period, a node is not suppressed by any other node, it declares itself landmark § New landmark broadcasts its status to its rneighborhood, suppressing all non-landmark nodes in it Completion time K is large → sequential algorithm K is small → parallel algorithm Tradeoff Over sampling rate 8 Telecommunication System & Internet Security Lab.

Landmark Selection § Protocol K=10 others : v > 0. 4 Each node generates v v=0. 1 v=0. 2 v=0. 4 v=0. 3 During waiting time (Kv), it declare landmark New landmark broadcasts r-neighborhood : Landmark 9 Telecommunication System & Internet Security Lab.

§ Introduction § Landmark Selection § Landmark Descent – Greedy Rule § Process § GLDR in Networks § Handling the Boundary Effect § Simulations § Conclusion 10 Telecommunication System & Internet Security Lab.

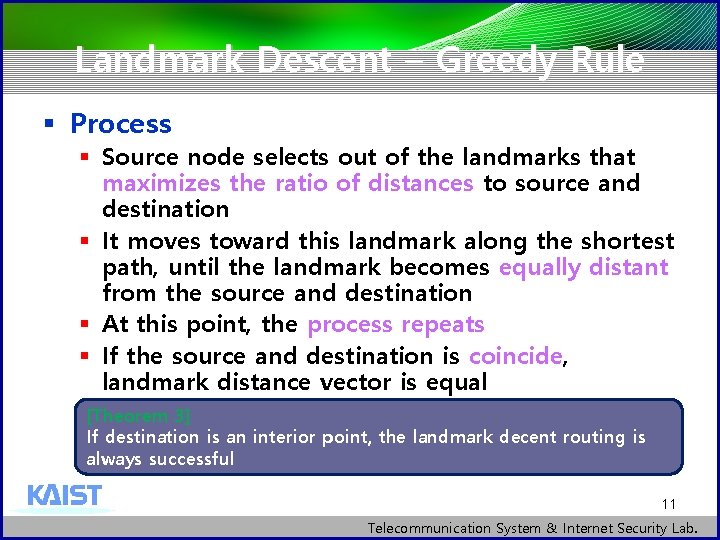
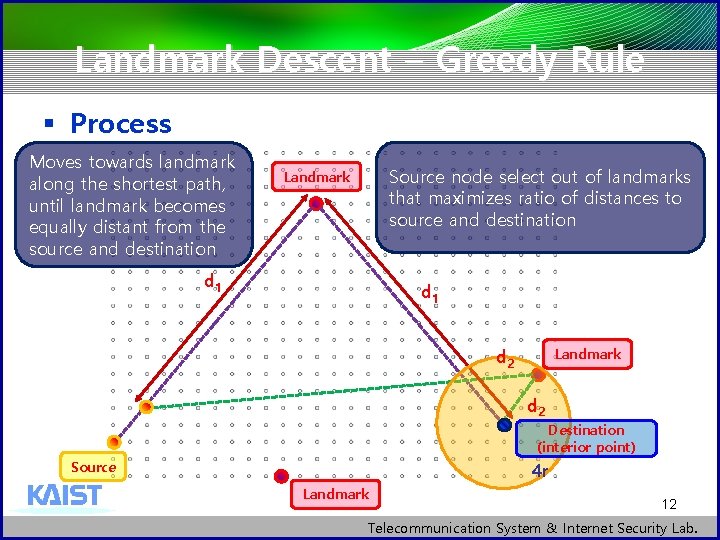
Landmark Descent – Greedy Rule § Process § Source node selects out of the landmarks that maximizes the ratio of distances to source and destination § It moves toward this landmark along the shortest path, until the landmark becomes equally distant from the source and destination § At this point, the process repeats § If the source and destination is coincide, landmark distance vector is equal [Theorem 3] If destination is an interior point, the landmark decent routing is always successful 11 Telecommunication System & Internet Security Lab.

Landmark Descent – Greedy Rule § Process Moves towards landmark along the shortest path, until landmark becomes equally distant from the source and destination Source node select out of landmarks that maximizes ratio of distances to source and destination Landmark d 1 d 2 Landmark d 2 Destination (interior point) Source 4 r Landmark 12 Telecommunication System & Internet Security Lab.

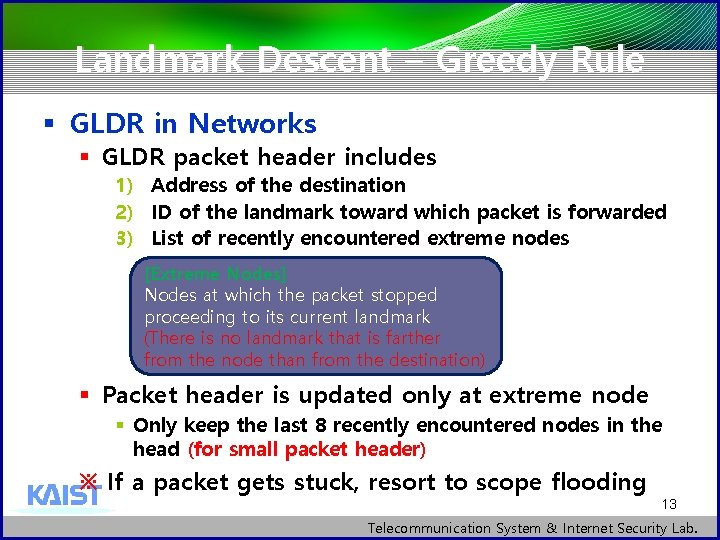
Landmark Descent – Greedy Rule § GLDR in Networks § GLDR packet header includes 1) Address of the destination 2) ID of the landmark toward which packet is forwarded 3) List of recently encountered extreme nodes [Extreme Nodes] Nodes at which the packet stopped proceeding to its current landmark (There is no landmark that is farther from the node than from the destination) § Packet header is updated only at extreme node § Only keep the last 8 recently encountered nodes in the head (for small packet header) ※ If a packet gets stuck, resort to scope flooding 13 Telecommunication System & Internet Security Lab.

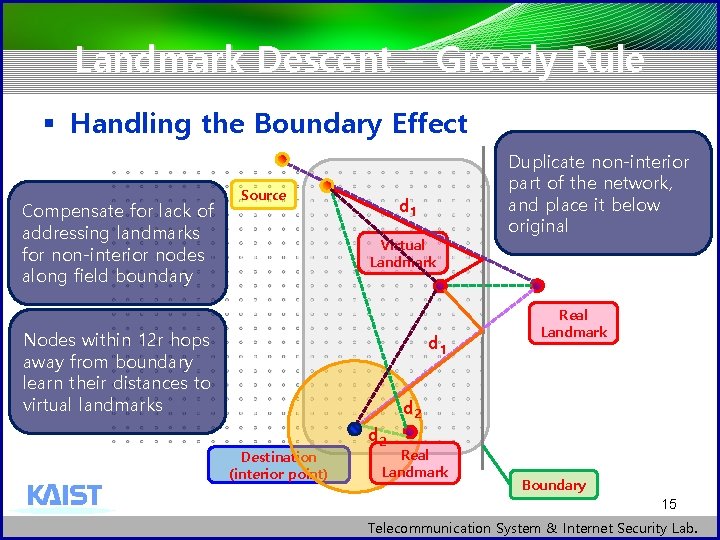
Landmark Descent – Greedy Rule § Handling the Boundary Effect § Routing to destinations near the boundaries is difficult because there are less and/or only onesided reference point § To alleviate boundary effect, virtually expand the sensor field § Reason for using virtual landmarks is to compensate for the lack of addressing landmarks for non-interior nodes along the field boundary 14 Telecommunication System & Internet Security Lab.

Landmark Descent – Greedy Rule § Handling the Boundary Effect Compensate for lack of addressing landmarks for non-interior nodes along field boundary Source d 1 Virtual Landmark Nodes within 12 r hops away from boundary learn their distances to virtual landmarks d 1 Duplicate non-interior part of the network, and place it below original Real Landmark d 2 Destination (interior point) d 2 Real Landmark Boundary 15 Telecommunication System & Internet Security Lab.

§ § Introduction Landmark Selection Landmark Descent – Greedy Rule Simulations § § § Default Simulation Setup Successful Delivery Rate Remaining Path and Stretch Factor Landmark Selection Improving BVR with r-sampling LM selection Improving routing performance using Virtual LM § Conclusion 16 Telecommunication System & Internet Security Lab.

Simulations § Default setup § § § Generate 3200 nodes Communication radius : 10 node degree Landmark generation : 10 -sampling (r=10) K = 1200 Run landmark selection schemes : 100 times When routing, use distance to the nearest 10 LMs § Simulation results § Average 28. 2 landmarks § Success rate of proposed routing : 90. 9% (without flooding) § When failed, hop distance from terminated source to destination : avg = 4. 47, σ = 2. 34 17 Telecommunication System & Internet Security Lab.

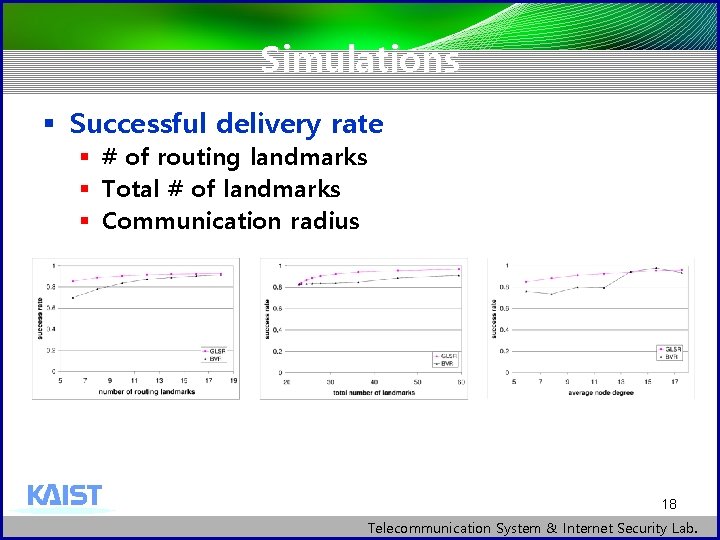
Simulations § Successful delivery rate § # of routing landmarks § Total # of landmarks § Communication radius 18 Telecommunication System & Internet Security Lab.

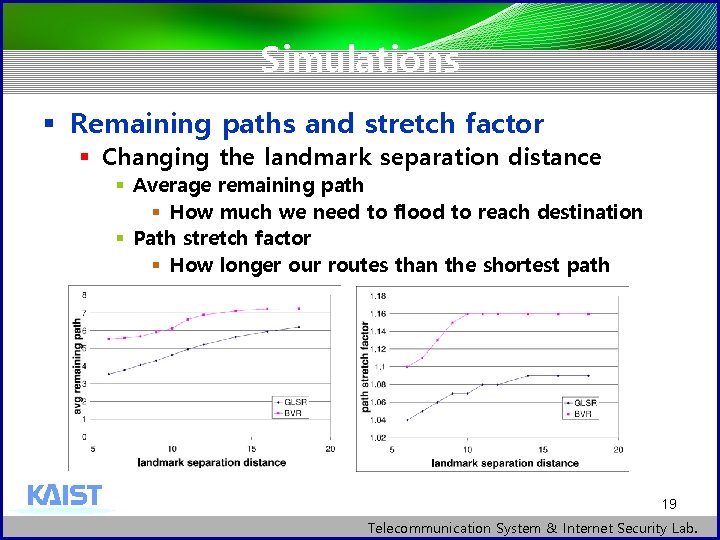
Simulations § Remaining paths and stretch factor § Changing the landmark separation distance § Average remaining path § How much we need to flood to reach destination § Path stretch factor § How longer our routes than the shortest path 19 Telecommunication System & Internet Security Lab.

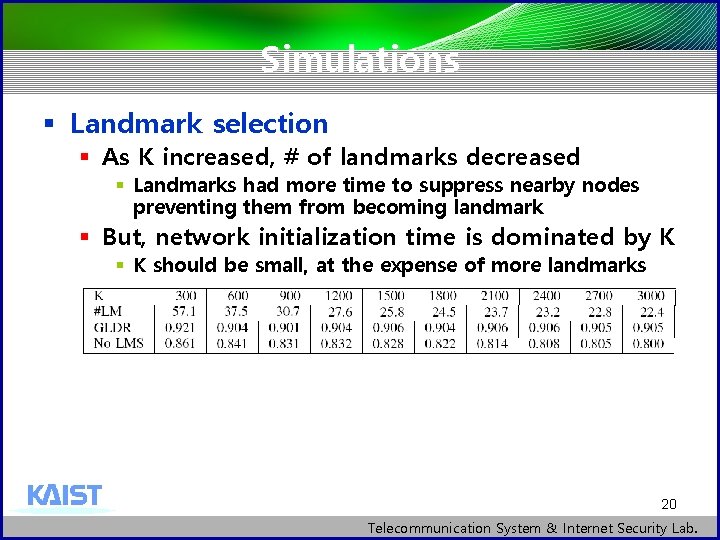
Simulations § Landmark selection § As K increased, # of landmarks decreased § Landmarks had more time to suppress nearby nodes preventing them from becoming landmark § But, network initialization time is dominated by K § K should be small, at the expense of more landmarks 20 Telecommunication System & Internet Security Lab.

Simulations § Improving BCR with r-sampling landmark selection § Proposed LM selection scheme improve BVR § Improving routing performance using virtual landmarks § Virtual LMs improve routing quality 21 Telecommunication System & Internet Security Lab.

§ § § Introduction Landmark Selection Landmark Descent – Greedy Rule Simulations Conclusion 22 Telecommunication System & Internet Security Lab.

Conclusion § For good routing performance, authors propose § Practical landmark selection protocol § Uniformly samples a network of sensors § Beneficial to some other landmark based routing § BVR’s performance improves significantly § Simple greedy routing (GLDR) § Based on distances to landmark § Lower routing overhead compared to BVR 23 Telecommunication System & Internet Security Lab.