Figure 1 17 Security Management n Security is







- Slides: 10

Figure 1 -17: Security Management n Security is a Primarily a Management Issue, not a Technology Issue n Top-to-Bottom Commitment ¡ Top-management commitment ¡ Operational execution ¡ Enforcement 1

Figure 1 -17: Security Management n Comprehensive Security ¡ Closing all avenues of attack ¡ Asymmetrical warfare n Attacker only has to find one opening ¡ Defense in depth n Attacker must get past several defenses to succeed ¡ Security audits n Run attacks against your own network 2

Figure 1 -17: Security Management n General Security Goals (CIA) ¡ Confidentiality n Attackers cannot read messages if they intercept them ¡ Integrity n If attackers change messages, this will be detected ¡ Availability n System is able to server users 3

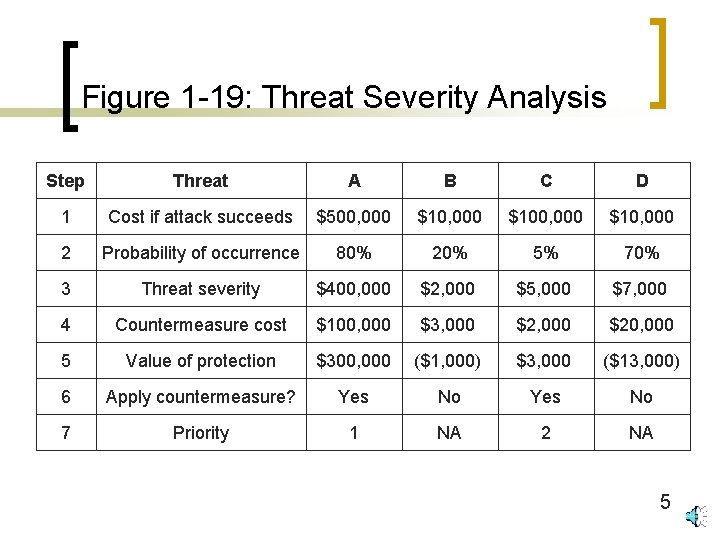
Figure 1 -18: The Plan—Protect— Respond Cycle n Planning ¡ Need for comprehensive security (no gaps) ¡ Risk analysis (see Figure 1 -19) n Enumerating threats n Threat severity = estimated cost of attack X probability of attack n Value of protection = threat severity – cost of countermeasure n Prioritize countermeasures by value of prioritization 4

Figure 1 -19: Threat Severity Analysis Step Threat A B C D 1 Cost if attack succeeds $500, 000 $100, 000 $10, 000 2 Probability of occurrence 80% 20% 5% 70% 3 Threat severity $400, 000 $2, 000 $5, 000 $7, 000 4 Countermeasure cost $100, 000 $3, 000 $20, 000 5 Value of protection $300, 000 ($1, 000) $3, 000 ($13, 000) 6 Apply countermeasure? Yes No 7 Priority 1 NA 2 NA 5

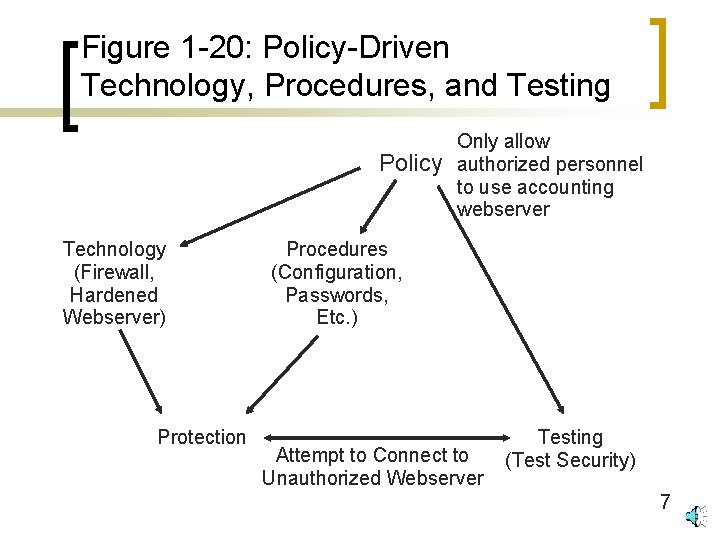
Figure 1 -18: The Plan—Protect— Respond Cycle n Planning ¡ Security policies drive subsequent specific actions (see Figure 1 -20) n Selecting technology n Procedures to make technology effective n The testing of technology and procedures 6

Figure 1 -20: Policy-Driven Technology, Procedures, and Testing Policy Technology (Firewall, Hardened Webserver) Protection Only allow authorized personnel to use accounting webserver Procedures (Configuration, Passwords, Etc. ) Attempt to Connect to Unauthorized Webserver Testing (Test Security) 7

Figure 1 -18: The Plan—Protect— Respond Cycle n Protecting ¡ Installing protections: firewalls, IDSs, host hardening, etc. ¡ Updating protections as the threat environment changes ¡ Testing protections: security audits 8

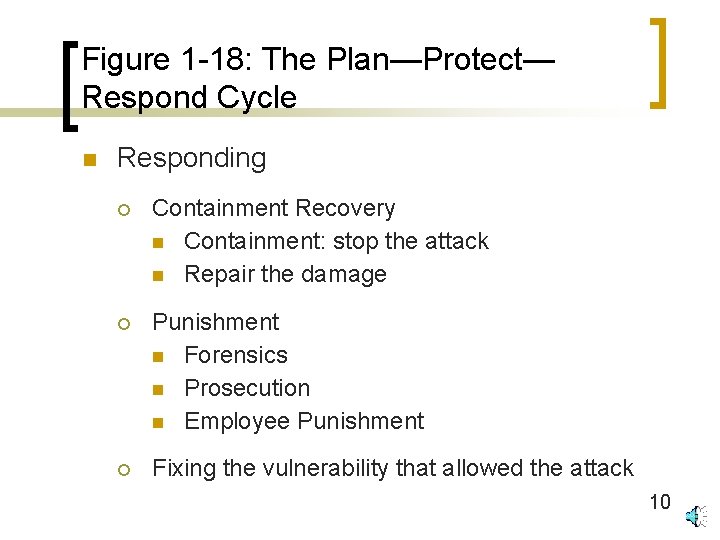
Figure 1 -18: The Plan—Protect— Respond Cycle n Responding ¡ Planning for response (Computer Emergency Response Team) ¡ Incident detection and determination n Procedures for reporting suspicious situations n Determination that an attack really is occurring n Description of the attack to guide subsequent actions 9

Figure 1 -18: The Plan—Protect— Respond Cycle n Responding ¡ Containment Recovery n Containment: stop the attack n Repair the damage ¡ Punishment n Forensics n Prosecution n Employee Punishment ¡ Fixing the vulnerability that allowed the attack 10