European Grid Initiative AAI in EGI Status and



















- Slides: 33

European Grid Initiative AAI in EGI Status and Evolution Peter Solagna Senior Operations Manager peter. solagna@egi. eu 1 www. egi. eu

Outline • Introduction to AAI in a federated environment • EGI services and solutions for AAI • Evolution of AAI in EGI • Summary EGI AAI Webinar 2 www. egi. eu

User authentication in a federated environment • Local environment (e. g. one institution, one cluster) – Users have local accounts, validated often in a F 2 F verification with the system administrator – All the needed information are filled in at the moment of the registration • Federated environment (e. g. distributed infrastructure) – Users do not have local accounts on every service/cluster/centre – Users own credentials that are recognized by all the service providers in the federation – Identity providers and service providers must agree on the: • Information provided to the SP • Level of assurance of the credentials • Operations of the Id. P EGI AAI Webinar 3 www. egi. eu

User’s identity • A user must be able to authenticate with the same identity on the distributed services • From the user’s point of view – Uniform authentication enable cross-site workflows – Use of distributed resources using the same credential • From the service provider’s point of view – Uniform authentication improves security operations in a federated environment – Easier management of users, and their access to resources EGI AAI Webinar 4 www. egi. eu

Delegation • For some workflows and use cases, delegation is an important capability – Applications that in general need to: access data stored by the user and not publicly accessible or to save data in the user’s storage area – Portals and scientific gateways do actions on behalf of the user, like job submission to compute resources. • This is usually implemented by impersonating and delegating – Impersonation: the application/service acts as the user (using user’s temporary credentials). Done at authentication level. – Delegation: the user enables the service to work on his/her behalf. Done at authorization level EGI AAI Webinar 5 www. egi. eu

Level of assurance Not all the credentials are the same! Examples: • Very high level of assurance: e. ID • High level of assurance with ID verification: – X 509 certificates, many institutional Id. P • Social media credentials – Everyone with an email account can have one • Not always the highest Lo. A is required: for some low-risk activities low assurance credentials are usable! • The minimum Lo. A required is determined by the user community and the service provider requirements EGI AAI Webinar 6 www. egi. eu

Authorization in a federated environment • In a federated environment individual user authorization cannot be handled by the service provider – Service provider does not know the user and if him/her should be allowed to perform a specific action • Rules for the authorization must use information associated with the user – Provided by the Id. P – Provided by the research collaboration who grants users access to resources EGI-In. SPIRE RI-261323 7 www. egi. eu

Distribute collaboration management in EGI: Virtual Organization • Virtual Organization: A group of researchers with common interests, requirements and applications, who need to work collaboratively and/or share resources. • Service providers enable users to access services and resources based on the VO membership and additional attributes such as roles within the VO and sub-groups of users within the VO • The VO membership is managed by the VO Manager(s) who is the main contact with EGI and who knows the users and the groups in the collaboration – New users can be added and removed enabling/disabling their access rights, without direct intervention of service providers – VO Manager usually does not manage users credential, a VO is not an Id. P EGI AAI Webinar 8 www. egi. eu

Outline • Introduction to AAI in a federated environment • EGI services and solutions for AAI • Evolution of AAI in EGI • Summary EGI AAI Webinar 9 www. egi. eu

EGI user authentication: X 509 certificates • X 509 certificates are the main authentication technology used in EGI • Trust network of certification authorities (IGTF/EUGrid. PMA) • EGI services are configured to accept certificates released by the Certification Authorities federated within IGTF • You have one IGTF personal certificate you can authenticate wherever in EGI AAI Webinar 10 www. egi. eu

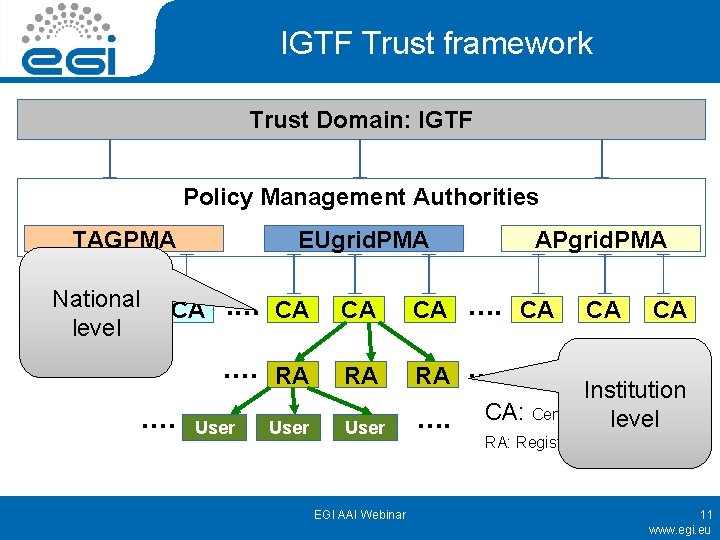
IGTF Trust framework Trust Domain: IGTF Policy Management Authorities TAGPMA National CA CA level EUgrid. PMA CA . . APgrid. PMA . . CA CA CA . . . . RA RA RA . . User EGI AAI Webinar CA CA CA Institution CA: Certificationlevel Authority RA: Registration Authority 11 www. egi. eu

How to obtain a certificate Do you own credentials provided by an Id. P federated in one of the national federations part of edu. GAIN? You can most probably access the Terena Certificate Service (TCS) through your NREN, and get an X 509 certificate without the need to contact a registration authority EGI AAI Webinar 12 www. egi. eu

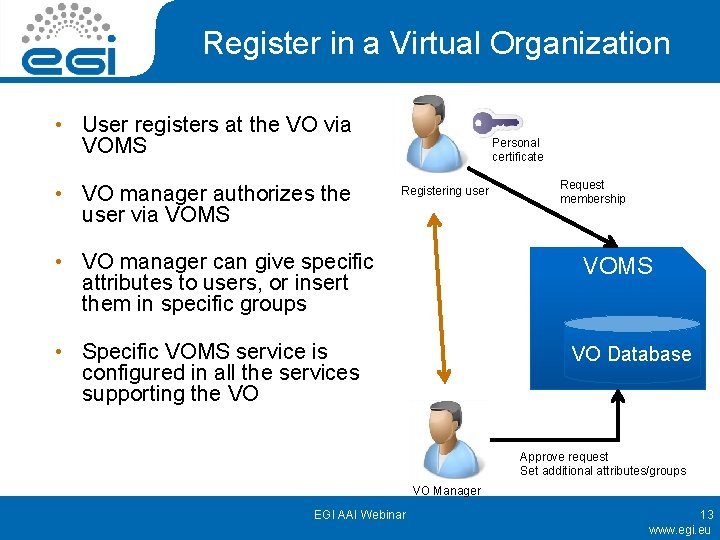
Register in a Virtual Organization • User registers at the VO via VOMS • VO manager authorizes the user via VOMS Personal certificate Registering user • VO manager can give specific attributes to users, or insert them in specific groups Request membership VOMS • Specific VOMS service is configured in all the services supporting the VO VO Database Approve request Set additional attributes/groups VO Manager EGI AAI Webinar 13 www. egi. eu

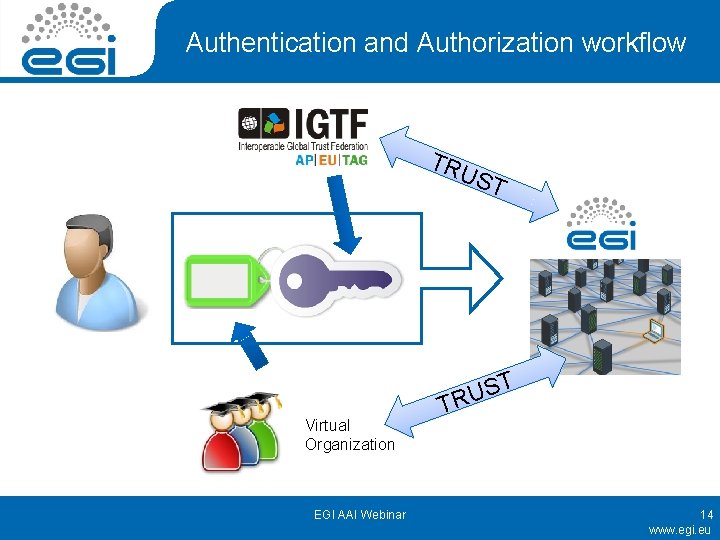
Authentication and Authorization workflow TRU ST Virtual Organization EGI AAI Webinar T S U TR 14 www. egi. eu

The key is: trust & collaboration • Authentication and Authorization workflows scale with the number of service providers and users – User identity is verified by the IGTF Certification Authorities who release the X 509 certificates – The certificate enable uniform authentication of the user across resource centres • User communities have the tools to manage the membership of their users and their structure – Collaborate to the trust chain and to integrate the information provided by the Identity Providers – Authorization is based on the Virtual Organization membership and attributes not on the single user identity – The user capabilities based on groups and roles within the VO are reflected into uniform access rights across the sites that support the VO EGI AAI Webinar 15 www. egi. eu

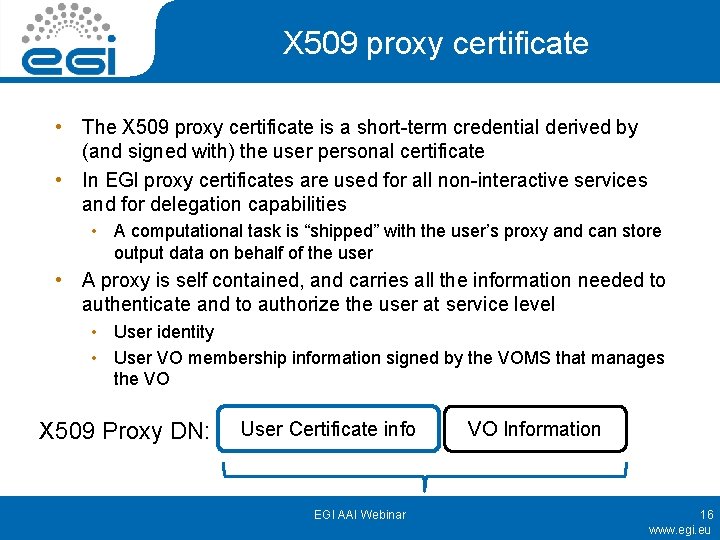
X 509 proxy certificate • The X 509 proxy certificate is a short-term credential derived by (and signed with) the user personal certificate • In EGI proxy certificates are used for all non-interactive services and for delegation capabilities • A computational task is “shipped” with the user’s proxy and can store output data on behalf of the user • A proxy is self contained, and carries all the information needed to authenticate and to authorize the user at service level • User identity • User VO membership information signed by the VOMS that manages the VO X 509 Proxy DN: User Certificate info EGI AAI Webinar VO Information 16 www. egi. eu

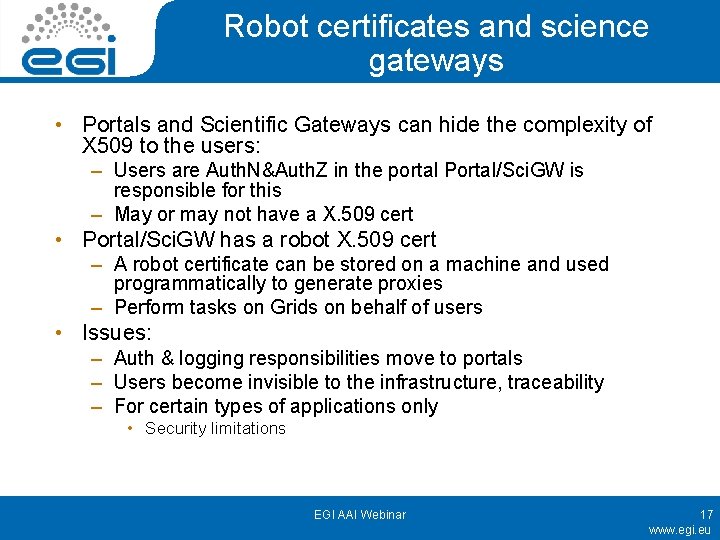
Robot certificates and science gateways • Portals and Scientific Gateways can hide the complexity of X 509 to the users: – Users are Auth. N&Auth. Z in the portal Portal/Sci. GW is responsible for this – May or may not have a X. 509 cert • Portal/Sci. GW has a robot X. 509 cert – A robot certificate can be stored on a machine and used programmatically to generate proxies – Perform tasks on Grids on behalf of users • Issues: – Auth & logging responsibilities move to portals – Users become invisible to the infrastructure, traceability – For certain types of applications only • Security limitations EGI AAI Webinar 17 www. egi. eu

Outline • Introduction to AAI in a federated environment • EGI services and solutions for AAI • Evolution of AAI in EGI • Summary EGI AAI Webinar 18 www. egi. eu

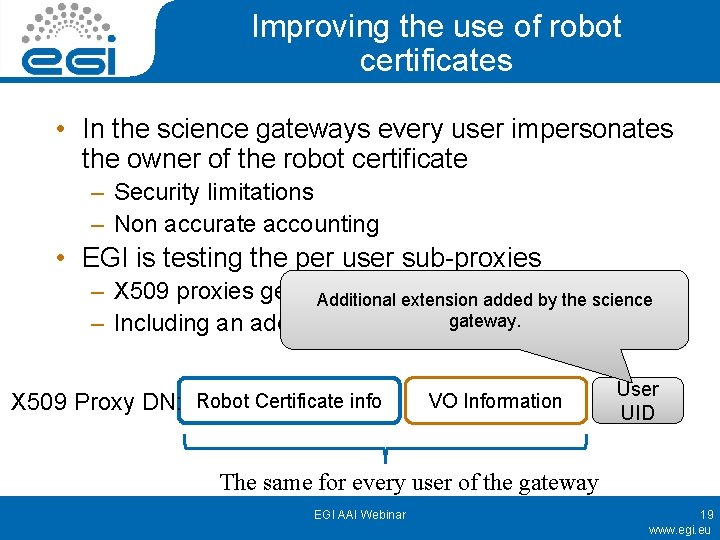
Improving the use of robot certificates • In the science gateways every user impersonates the owner of the robot certificate – Security limitations – Non accurate accounting • EGI is testing the per user sub-proxies – X 509 proxies generated using a robot certificate Additional extension added by the science gateway. – Including an additional extension with the user ID X 509 Proxy DN: Robot Certificate info VO Information User UID The same for every user of the gateway EGI AAI Webinar 19 www. egi. eu

Advantages of the sub proxy • User tracking – Services get “different” credentials for individual users – It’s possible to block one user without blocking all the users using the same robot certificate • Security – Individual users can be isolated, e. g. preventing them to access other users’ workspace • Accounting – Account for individual users’ usage – Report the actual number of real users accessing the infrastructure • Per user sub-proxy tested within the Long tail of Science platform under development Other alternatives: Online CA • It’s an alternative (more elegant? ) solution for the same problem • Not commonly available as the robot-certificates • Robot-certificates at the moment are the quickest solution. EGI AAI Webinar 20 www. egi. eu

Extend the X 509 mechanism • For some users approaching EGI, the X 509 mechanism is a barrier – They do not have easy access to a Certification Authority – They would prefer to continue using their institutional credentials – VOs and Resource Providers implement portals to ease the access to the resources • The most effective solution is to bridge other identity federations (edu. GAIN, institutional Id. P) with the EGI AAI – Technical bridge: credentials translation, support in the middleware for other Auth. N protocols – Policy bridge: build trust between SP and Id. P, enable different level of trust EGI AAI Webinar 21 www. egi. eu

Flexible authentication By extending the current authentication mechanisms we will also enable users with the flexibility they need: • Use lower level of assurance credentials for low-risk activities • Integrate the Id. P currently used by the communities with the EGI services EGI AAI Webinar 22 www. egi. eu

Enable federated Auth. Z • Provide tools to the users to manage their user communities – Distributed Attribute Authorities connected with the user’s Id. Ps – Can be used also within application-specific environments for user authorization • Maintain uniform authorization across multiple service providers – Based on the attributes provided by the user communities • Apply the collaborative trust approach of EGI to new authentication technologies EGI AAI Webinar 23 www. egi. eu

edu. GAIN and EGI • edu. GAIN is the pan-European federation of national Id. P federations – Includes most of the Id. P used by researchers in Europe • Limitations: – Not all the Id. Ps are part of edu. GAIN federations – For many use cases a direct Id. P <-> SP communication (paperwork) is required – Some Id. P • The European-funded AARC project aims – among other things – to overcome part of these limitations EGI AAI Webinar 24 www. egi. eu

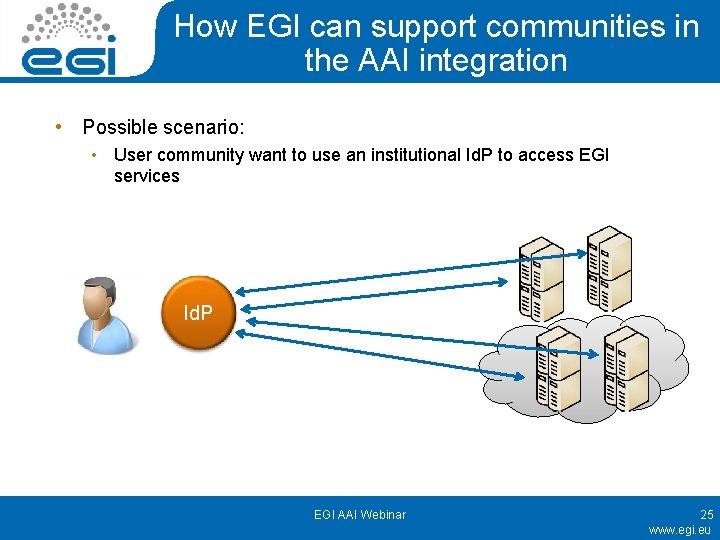
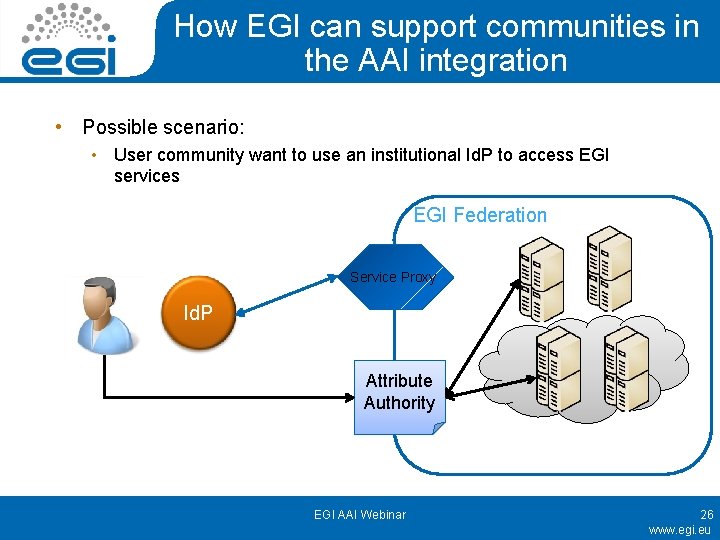
How EGI can support communities in the AAI integration • Possible scenario: • User community want to use an institutional Id. P to access EGI services Id. P EGI AAI Webinar 25 www. egi. eu

How EGI can support communities in the AAI integration • Possible scenario: • User community want to use an institutional Id. P to access EGI services EGI Federation Service Proxy Id. P Attribute Authority EGI AAI Webinar 26 www. egi. eu

AARC Authentication and Authorisation for Research and Collaboration • support the collaboration model across institutional and sector borders • guarantee user privacy and security • build on the existing and evolving components EGI, ESFRI clusters, edu. GAIN, national AAI federations, NGIs, IGTF, SCI, Sir. TFi, … • design, test and pilot any missing components • integrate them with existing working flows • Expected starting date May 1 st EGI AAI Webinar 27 www. egi. eu

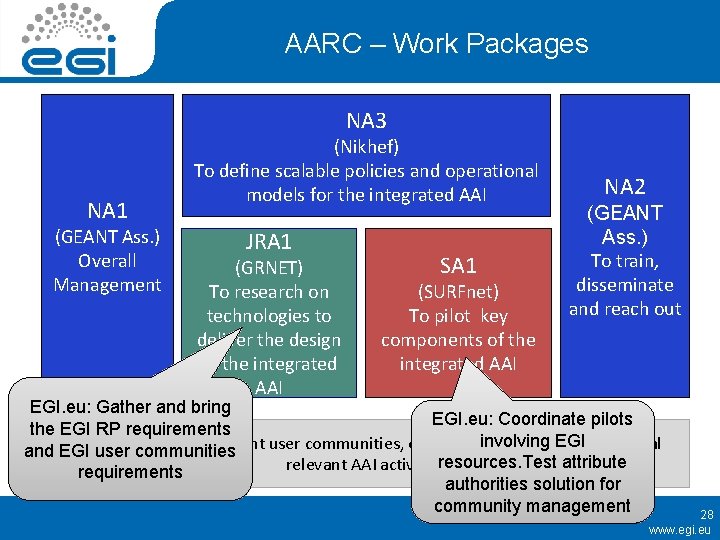
AARC – Work Packages NA 3 NA 1 (GEANT Ass. ) Overall Management (Nikhef) To define scalable policies and operational models for the integrated AAI JRA 1 (GRNET) To research on technologies to deliver the design of the integrated AAI SA 1 (SURFnet) To pilot key components of the integrated AAI NA 2 (GEANT Ass. ) To train, disseminate and reach out EGI. eu: Gather and bring EGI. eu: Coordinate pilots the EGI RP requirements involving Liaison other relevant user communities, e-Infrastructures and. EGI international and EGI userwith communities relevant AAI activitiesresources. Test attribute requirements authorities solution for community management 28 www. egi. eu

Outline • Introduction to AAI in a federated environment • EGI services and solutions for AAI • Evolution of AAI in EGI • Summary EGI AAI Webinar 29 www. egi. eu

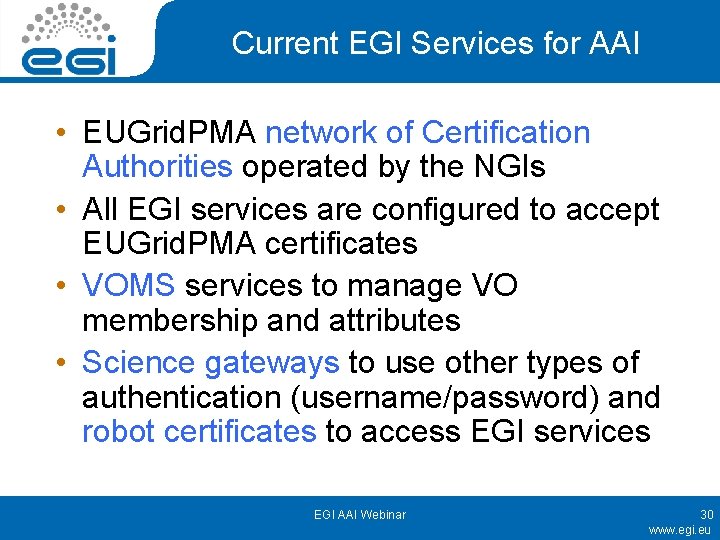
Current EGI Services for AAI • EUGrid. PMA network of Certification Authorities operated by the NGIs • All EGI services are configured to accept EUGrid. PMA certificates • VOMS services to manage VO membership and attributes • Science gateways to use other types of authentication (username/password) and robot certificates to access EGI services EGI AAI Webinar 30 www. egi. eu

Possible future EGI services for EGI Based on the requirements and use cases • Integration with federations and individual Id. Ps • Service proxy to easily integrate new Id. Ps • Attribute authorities network to manage user membership and regulate authorization • Credential translation services to integrate the Authentication technologies used by the user community with the existing services EGI AAI Webinar 31 www. egi. eu

Better support for collaborations • The current trust architecture has proven to be scalable and to work: – Empower the user communities to regulate the access to the resources for their users – Build trust between user communities, service providers and identity providers • Extend this approach by integrating other Auth. N technologies in EGI – Provide tools to manage attributes using non X. 509 credentials – Link the attribute authorities with edu. GAIN and other Id. Ps – Where necessary bridge diverse Auth. N technologies using credential translation services • Bring the requirements from the CCs and in general the user communities to the European level, and ensure interoperability with other e-infrastructures through the AARC project EGI AAI Webinar 32 www. egi. eu

Thanks for your attention Questions? EGI AAI Webinar 33 www. egi. eu
 European cloud initiative
European cloud initiative European capacity building initiative
European capacity building initiative European capacity building initiative
European capacity building initiative European capacity building initiative
European capacity building initiative Reglas de los terminos del silogismo
Reglas de los terminos del silogismo Aai pacing
Aai pacing Jari sinkkonen vastaanotto
Jari sinkkonen vastaanotto Ess portal aai.aero
Ess portal aai.aero Godiva infn
Godiva infn Infn aai login
Infn aai login Aai student portal
Aai student portal Onap aai architecture
Onap aai architecture Aai aspire
Aai aspire Egi etv
Egi etv Wyoming egi
Wyoming egi Mint forró sóhaj elhaló bús jaj
Mint forró sóhaj elhaló bús jaj Egi applications
Egi applications Egi property link
Egi property link Emi accounting
Emi accounting Pin grid array vs land grid array
Pin grid array vs land grid array European grid infrastructure
European grid infrastructure Edcdp
Edcdp Global initiative on food loss and waste reduction
Global initiative on food loss and waste reduction Doctoral initiative on minority attrition and completion
Doctoral initiative on minority attrition and completion National math and science initiative ap biology
National math and science initiative ap biology Ap psychology unit 9
Ap psychology unit 9 Cardiogenic shock
Cardiogenic shock The cyberspace learning initiative
The cyberspace learning initiative What is sdmi
What is sdmi Pharmaceutical supply chain initiative psci
Pharmaceutical supply chain initiative psci Northern waterfront economic development initiative
Northern waterfront economic development initiative Louisiana optical network initiative
Louisiana optical network initiative Safi furniture
Safi furniture Inidicia
Inidicia