The EGI AAI Check In Service Peter Solagna





- Slides: 19

The EGI AAI “Check. In” Service Peter Solagna - EGI. eu Christos Kanellopoulos - GRNET www. egi. eu EGI-Engage is co-funded by the Horizon 2020 Framework Programme of the European Union under grant number 654142

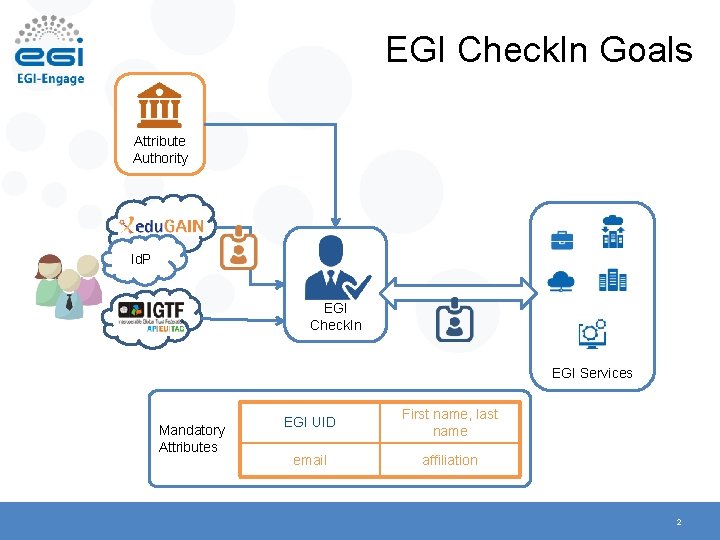
EGI Check. In Goals Attribute Authority Id. P EGI Check. In EGI Services Mandatory Attributes EGI UID First name, last name email affiliation 2

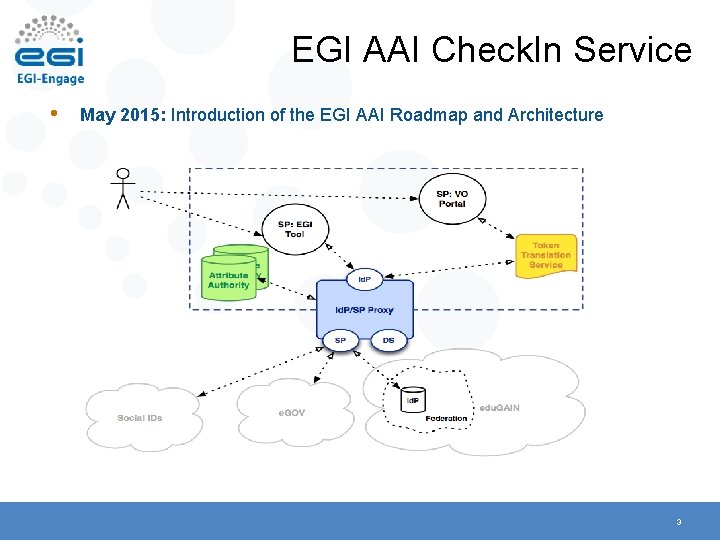
EGI AAI Check. In Service • May 2015: Introduction of the EGI AAI Roadmap and Architecture 3

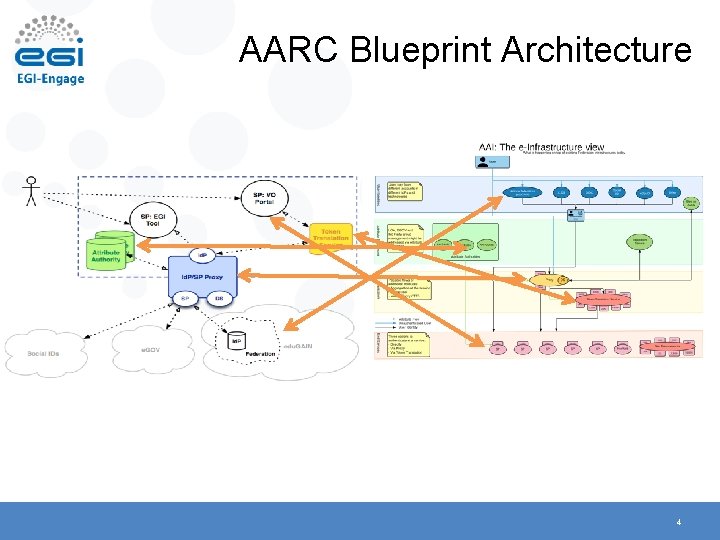
AARC Blueprint Architecture 4

Why Proxy? All EGI SPs can have one statically configured Id. P No need to run an Id. P Discovery Service on each EGI SP Connected SPs get consistent/harmonised user identifiers and accompanying attribute sets from one or more AAs that can be interpreted in a uniform way for auth. Z purposes External Id. Ps only deal with a single EGI SP proxy In a nutshell: EGI services will not have to deal with the complexity of multiple Id. Ps/Federations/Attribute Authorities/technologies. This complexity will be handled centrally by the proxy. 5

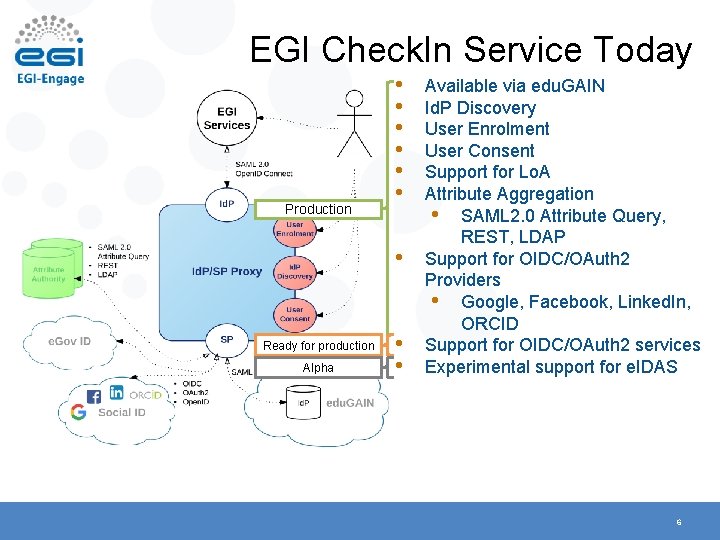
EGI Check. In Service Today Production • • Ready for production Alpha • • Available via edu. GAIN Id. P Discovery User Enrolment User Consent Support for Lo. A Attribute Aggregation • SAML 2. 0 Attribute Query, REST, LDAP Support for OIDC/OAuth 2 Providers • Google, Facebook, Linked. In, ORCID Support for OIDC/OAuth 2 services Experimental support for e. IDAS 6

Levels of Assurance • EGI AAI proposal for 3 levels of assurance. Each level is represented by a URI: • Low: Authentication through a social identity provider → https: //aai. egi. eu/Lo. A#Low • Substantial: Password authentication at the user's home Id. P → https: //aai. egi. eu/Lo. A#Substantial • High: Substantial + multi-factor authn (not yet supported, TBD) → https: //aai. egi. eu/Lo. A#High • TODO: Create an appropriate document for each Lo. A (this may be, but does not have to be, referenced by the URI above). 7

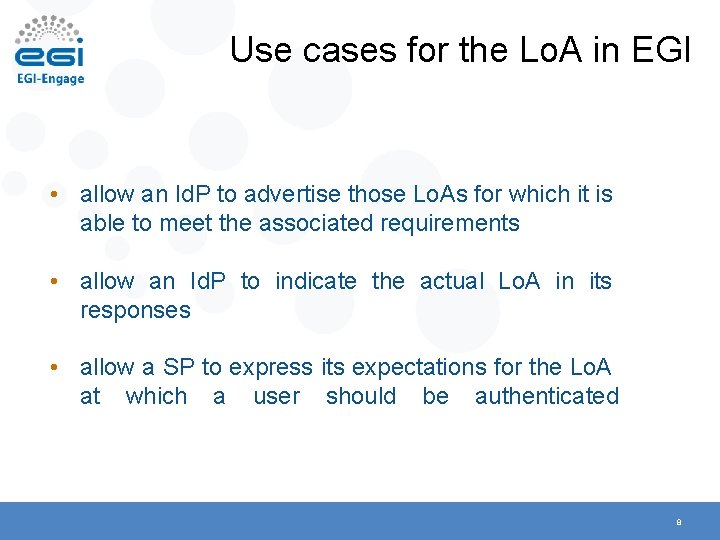
Use cases for the Lo. A in EGI • allow an Id. P to advertise those Lo. As for which it is able to meet the associated requirements • allow an Id. P to indicate the actual Lo. A in its responses • allow a SP to express its expectations for the Lo. A at which a user should be authenticated 8

EGI Unique Identifier requirements EGI User Identifier The EGI User ID should be: • personal - used by a single person • persistent - used for an extended period of time across multiple sessions • non-reassignable - assigned exclusively to a specific person, and never reassigned to another individual • non-targeted - not intended for a specific relying party (or parties), i. e. should be shared • globally unique - unique beyond the namespace of the Id. P and the namespace of the SP(s) with which the ID is shared • opaque - should (by itself) provide no information about the user, i. e. should be privacypreserving 9

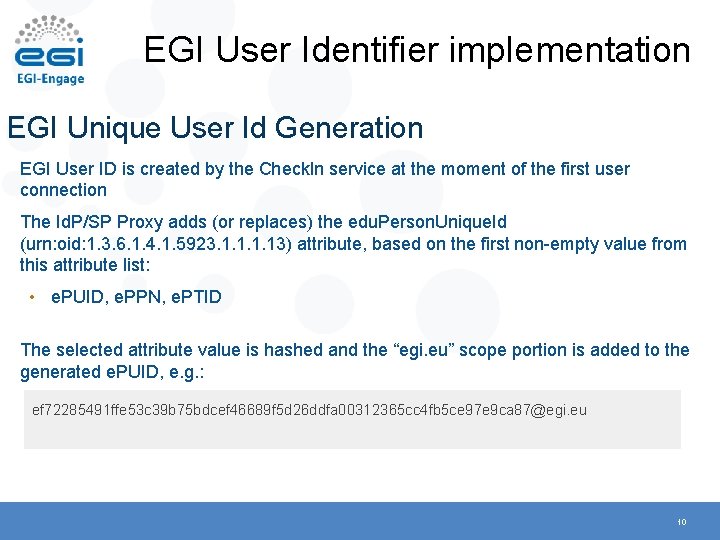
EGI User Identifier implementation EGI Unique User Id Generation EGI User ID is created by the Check. In service at the moment of the first user connection The Id. P/SP Proxy adds (or replaces) the edu. Person. Unique. Id (urn: oid: 1. 3. 6. 1. 4. 1. 5923. 1. 13) attribute, based on the first non-empty value from this attribute list: • e. PUID, e. PPN, e. PTID The selected attribute value is hashed and the “egi. eu” scope portion is added to the generated e. PUID, e. g. : ef 72285491 ffe 53 c 39 b 75 bdcef 46689 f 5 d 26 ddfa 00312365 cc 4 fb 5 ce 97 e 9 ca 87@egi. eu 10

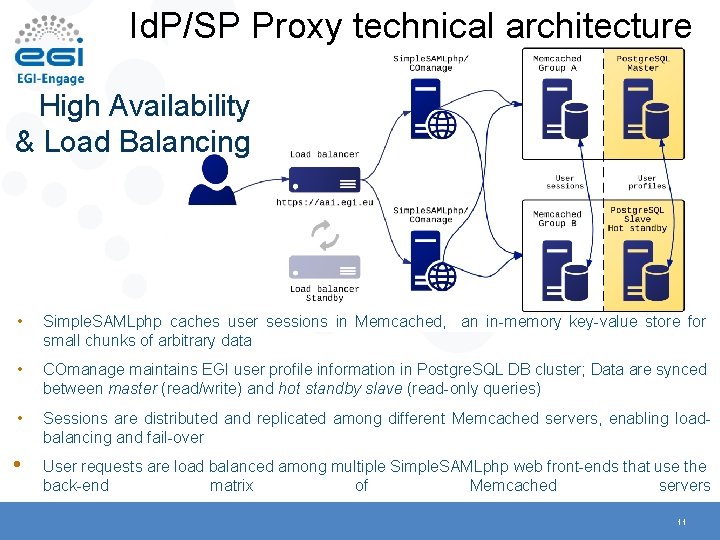
Id. P/SP Proxy technical architecture High Availability & Load Balancing • Simple. SAMLphp caches user sessions in Memcached, an in-memory key-value store for small chunks of arbitrary data • COmanage maintains EGI user profile information in Postgre. SQL DB cluster; Data are synced between master (read/write) and hot standby slave (read-only queries) • Sessions are distributed and replicated among different Memcached servers, enabling loadbalancing and fail-over • User requests are load balanced among multiple Simple. SAMLphp web front-ends that use the back-end matrix of Memcached servers 11

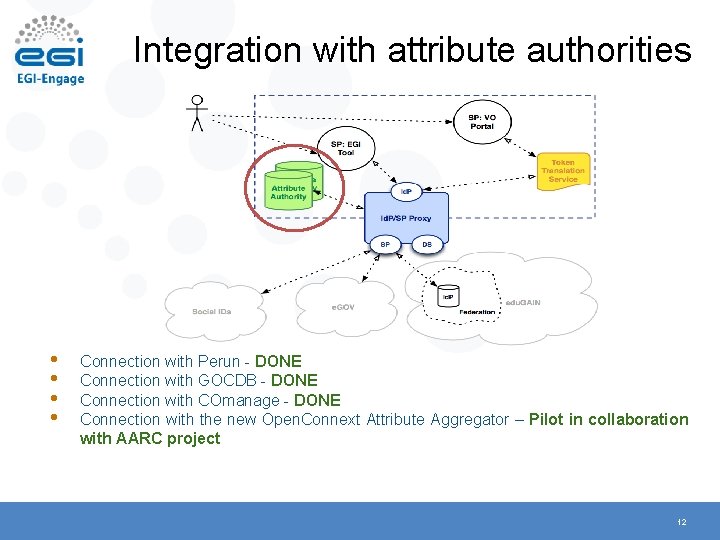
Integration with attribute authorities • • Connection with Perun - DONE Connection with GOCDB - DONE Connection with COmanage - DONE Connection with the new Open. Connext Attribute Aggregator – Pilot in collaboration with AARC project 12

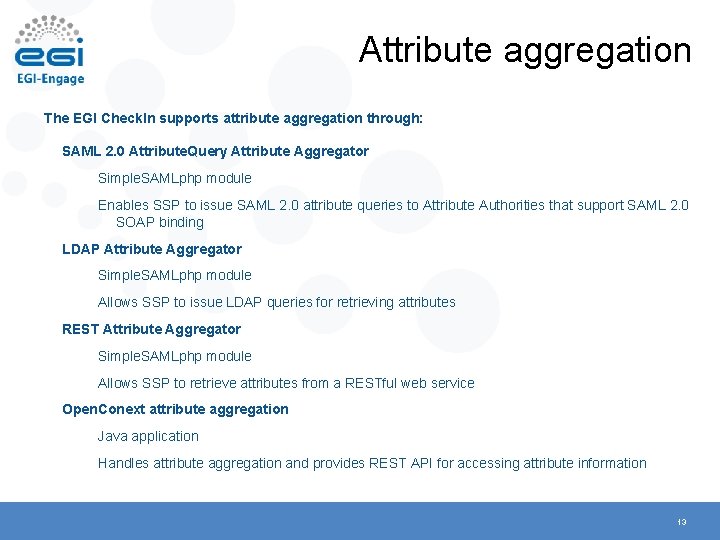
Attribute aggregation The EGI Check. In supports attribute aggregation through: SAML 2. 0 Attribute. Query Attribute Aggregator Simple. SAMLphp module Enables SSP to issue SAML 2. 0 attribute queries to Attribute Authorities that support SAML 2. 0 SOAP binding LDAP Attribute Aggregator Simple. SAMLphp module Allows SSP to issue LDAP queries for retrieving attributes REST Attribute Aggregator Simple. SAMLphp module Allows SSP to retrieve attributes from a RESTful web service Open. Conext attribute aggregation Java application Handles attribute aggregation and provides REST API for accessing attribute information 13

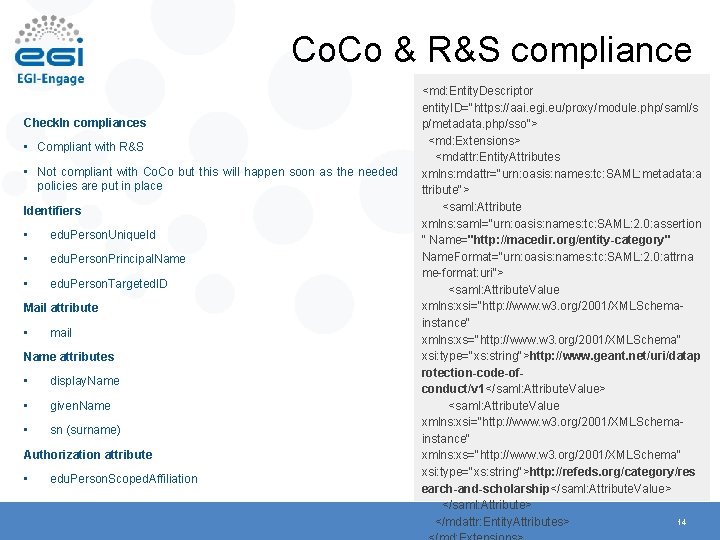
Co. Co & R&S compliance Check. In compliances • Compliant with R&S • Not compliant with Co. Co but this will happen soon as the needed policies are put in place Identifiers • edu. Person. Unique. Id • edu. Person. Principal. Name • edu. Person. Targeted. ID Mail attribute • mail Name attributes • display. Name • given. Name • sn (surname) Authorization attribute • edu. Person. Scoped. Affiliation <md: Entity. Descriptor entity. ID="https: //aai. egi. eu/proxy/module. php/saml/s p/metadata. php/sso"> <md: Extensions> <mdattr: Entity. Attributes xmlns: mdattr="urn: oasis: names: tc: SAML: metadata: a ttribute"> <saml: Attribute xmlns: saml="urn: oasis: names: tc: SAML: 2. 0: assertion " Name="http: //macedir. org/entity-category" Name. Format="urn: oasis: names: tc: SAML: 2. 0: attrna me-format: uri"> <saml: Attribute. Value xmlns: xsi="http: //www. w 3. org/2001/XMLSchemainstance" xmlns: xs="http: //www. w 3. org/2001/XMLSchema" xsi: type="xs: string">http: //www. geant. net/uri/datap rotection-code-ofconduct/v 1</saml: Attribute. Value> <saml: Attribute. Value xmlns: xsi="http: //www. w 3. org/2001/XMLSchemainstance" xmlns: xs="http: //www. w 3. org/2001/XMLSchema" xsi: type="xs: string">http: //refeds. org/category/res earch-and-scholarship</saml: Attribute. Value> </saml: Attribute> 14 </mdattr: Entity. Attributes>

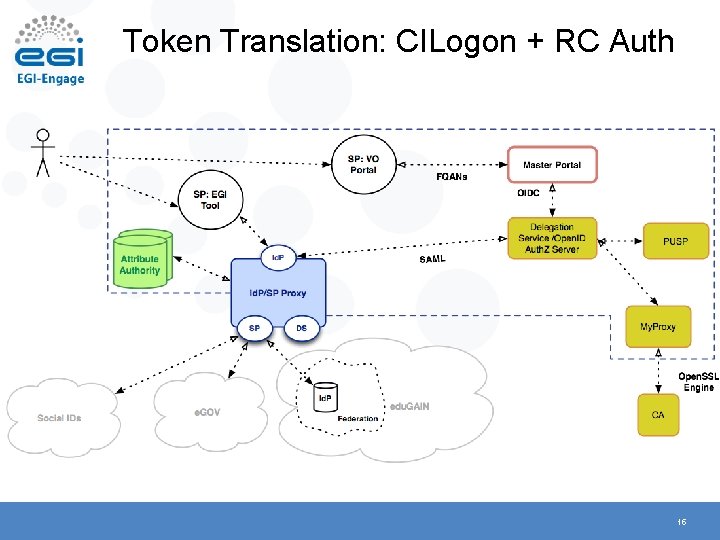
Token Translation: CILogon + RC Auth 15

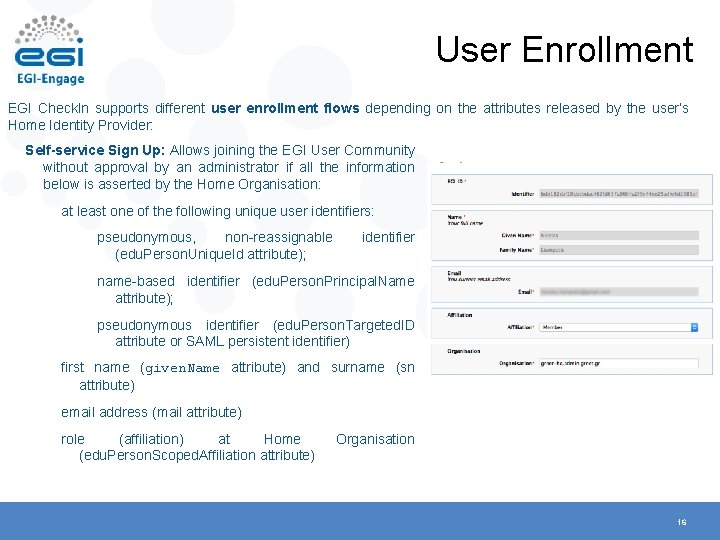
User Enrollment EGI Check. In supports different user enrollment flows depending on the attributes released by the user’s Home Identity Provider: Self-service Sign Up: Allows joining the EGI User Community without approval by an administrator if all the information below is asserted by the Home Organisation: at least one of the following unique user identifiers: pseudonymous, non-reassignable (edu. Person. Unique. Id attribute); identifier name-based identifier (edu. Person. Principal. Name attribute); pseudonymous identifier (edu. Person. Targeted. ID attribute or SAML persistent identifier) first name (given. Name attribute) and surname (sn attribute) email address (mail attribute) role (affiliation) at Home (edu. Person. Scoped. Affiliation attribute) Organisation 16

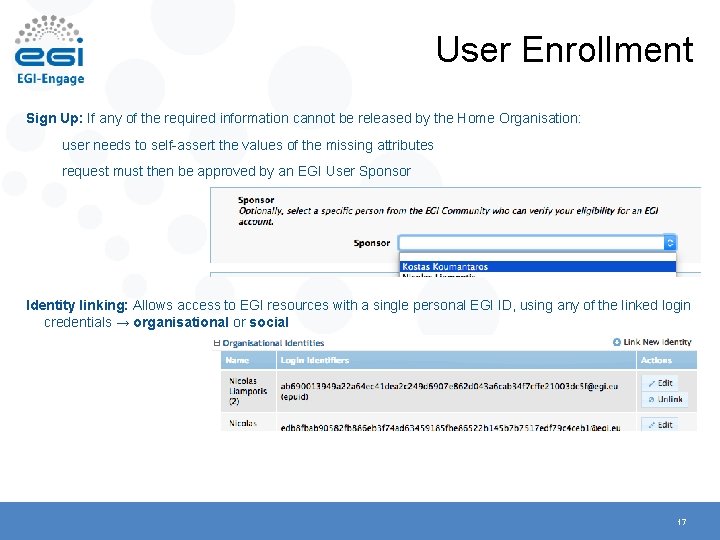
User Enrollment Sign Up: If any of the required information cannot be released by the Home Organisation: user needs to self-assert the values of the missing attributes request must then be approved by an EGI User Sponsor Identity linking: Allows access to EGI resources with a single personal EGI ID, using any of the linked login credentials → organisational or social 17

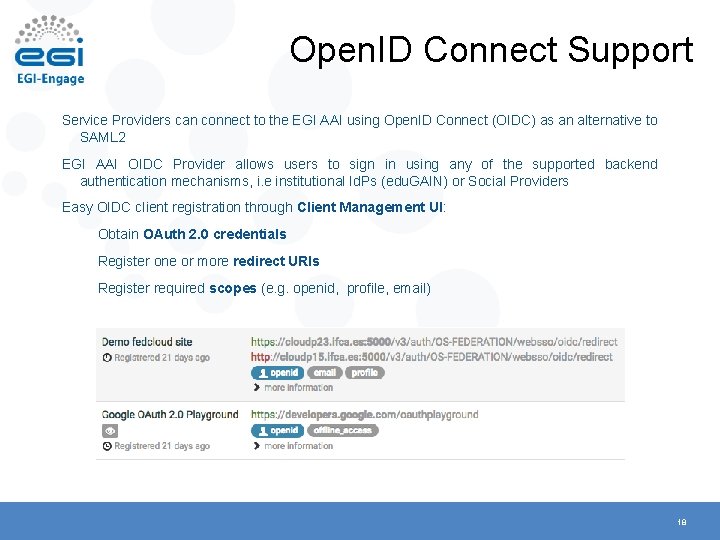
Open. ID Connect Support Service Providers can connect to the EGI AAI using Open. ID Connect (OIDC) as an alternative to SAML 2 EGI AAI OIDC Provider allows users to sign in using any of the supported backend authentication mechanisms, i. e institutional Id. Ps (edu. GAIN) or Social Providers Easy OIDC client registration through Client Management UI: Obtain OAuth 2. 0 credentials Register one or more redirect URIs Register required scopes (e. g. openid, profile, email) 18

Thank you for your attention. Questions? www. egi. eu This work by Parties of the EGI-Engage Consortium is licensed under a Creative Commons Attribution 4. 0 International License.
 Silogismo aee
Silogismo aee Aai pacing
Aai pacing Kiintymysmallit
Kiintymysmallit Ess portal aai
Ess portal aai Aai infn
Aai infn Dael maselli
Dael maselli Samlphp
Samlphp Onap aai architecture
Onap aai architecture Aai aspire
Aai aspire Egi etv
Egi etv Wyoming egi
Wyoming egi Harmatozzatok égi magasok
Harmatozzatok égi magasok Egi database
Egi database Egi property link
Egi property link Emi accounting
Emi accounting Behavior check in check out sheet
Behavior check in check out sheet Behavior check in check out sheet
Behavior check in check out sheet Check in check out behavior intervention
Check in check out behavior intervention Check in check out system
Check in check out system Cashiers check bank of america
Cashiers check bank of america