EU 28 Cloud Security Conference Reaching the Cloud








- Slides: 15

EU 28 Cloud Security Conference: Reaching the Cloud Era in the European Union Track A: Legal and Compliance - “Cloud Security and the Network and Information Security Directive: the need for Harmonization” Jan Neutze Director, Cybersecurity Policy, EMEA, Microsoft

Aims of a Overview national cybersecurity strategy 1) 1) Emerging Cloud & Cybersecurity Strategies 2) 2) The NIS Directive – opportunities and challenges 3) 3) Case Study: Estonia’s Virtual Data Embassies

Global Landscape Emerging Cloud & Cybersecurity Strategies

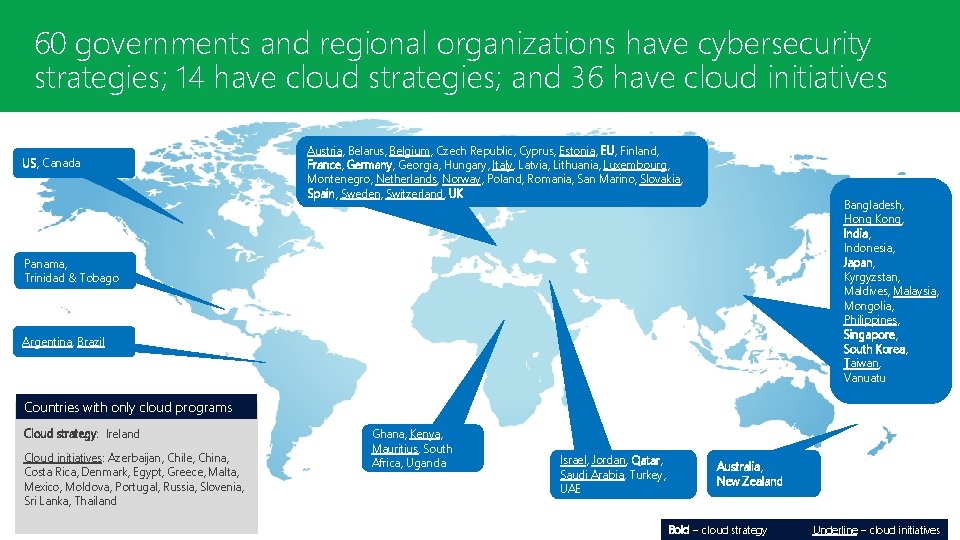
60 governments and regional organizations have cybersecurity strategies; 14 have cloud strategies; and 36 have cloud initiatives US, Canada Austria, Belarus, Belgium, Czech Republic, Cyprus, Estonia, EU, Finland, France, Germany, Georgia, Hungary, Italy, Latvia, Lithuania, Luxembourg, Montenegro, Netherlands, Norway, Poland, Romania, San Marino, Slovakia, Spain, Sweden, Switzerland, UK Bangladesh, Hong Kong, India, Indonesia, Japan, Kyrgyzstan, Maldives, Malaysia, Mongolia, Philippines, Singapore, South Korea, Taiwan, Vanuatu Panama, Trinidad & Tobago Argentina, Brazil Countries with only cloud programs Cloud strategy: Ireland Cloud initiatives: Azerbaijan, Chile, China, Costa Rica, Denmark, Egypt, Greece, Malta, Mexico, Moldova, Portugal, Russia, Slovenia, Sri Lanka, Thailand Ghana, Kenya, Mauritius, South Africa, Uganda Israel, Jordan, Qatar, Saudi Arabia, Turkey, UAE Australia, New Zealand Bold = cloud strategy Underline = cloud initiatives

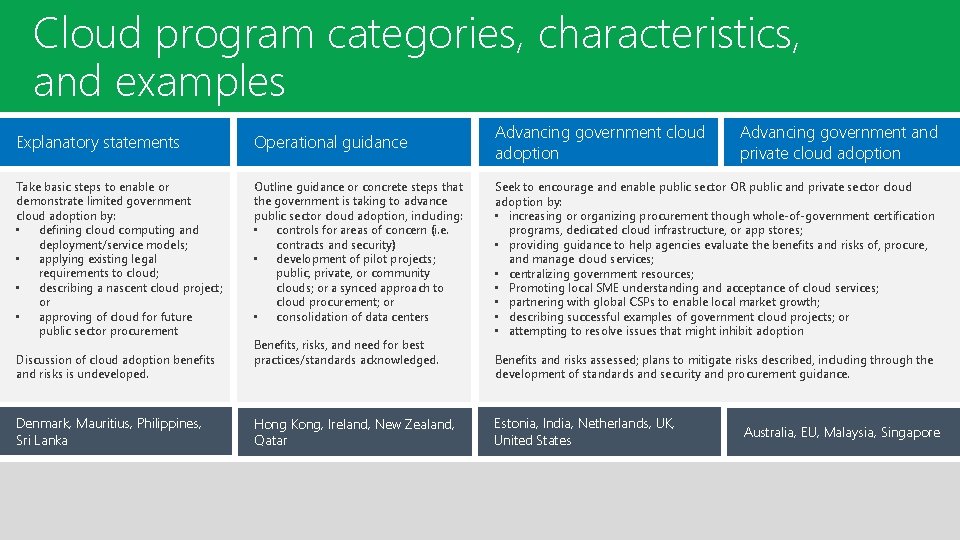
Cloud program categories, characteristics, and examples Trustworthy Cloud Principles Explanatory statements Operational guidance Take basic steps to enable or demonstrate limited government cloud adoption by: • defining cloud computing and deployment/service models; • applying existing legal requirements to cloud; • describing a nascent cloud project; or • approving of cloud for future public sector procurement Outline guidance or concrete steps that the government is taking to advance public sector cloud adoption, including: • controls for areas of concern (i. e. contracts and security) • development of pilot projects; public, private, or community clouds; or a synced approach to cloud procurement; or • consolidation of data centers Discussion of cloud adoption benefits and risks is undeveloped. Denmark, Mauritius, Philippines, Sri Lanka Benefits, risks, and need for best practices/standards acknowledged. Hong Kong, Ireland, New Zealand, Qatar Advancing government cloud adoption Advancing government and private cloud adoption Seek to encourage and enable public sector OR public and private sector cloud adoption by: • increasing or organizing procurement though whole-of-government certification programs, dedicated cloud infrastructure, or app stores; • providing guidance to help agencies evaluate the benefits and risks of, procure, and manage cloud services; • centralizing government resources; • Promoting local SME understanding and acceptance of cloud services; • partnering with global CSPs to enable local market growth; • describing successful examples of government cloud projects; or • attempting to resolve issues that might inhibit adoption Benefits and risks assessed; plans to mitigate risks described, including through the development of standards and security and procurement guidance. Estonia, India, Netherlands, UK, United States Australia, EU, Malaysia, Singapore

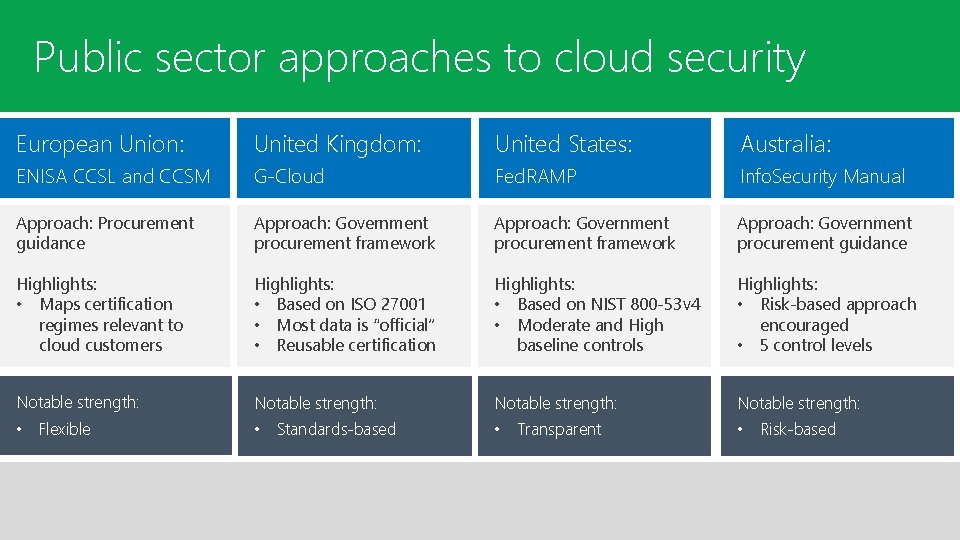
Public sector approaches to cloud security Trustworthy Cloud Principles United Kingdom: United States: European Union: Australia: ENISA CCSL and CCSM G-Cloud Fed. RAMP Info. Security Manual Approach: Procurement guidance Approach: Government procurement framework Approach: Government procurement guidance Highlights: • Maps certification regimes relevant to cloud customers Highlights: • Based on ISO 27001 • Most data is “official” • Reusable certification Highlights: • Based on NIST 800 -53 v 4 • Moderate and High baseline controls Highlights: • Risk-based approach encouraged • 5 control levels Notable strength: • Flexible • Standards-based • Transparent • Risk-based


The Digital Single Market Strategy Trustworthy Cloud Principles European Commission Digital Single Market Strategy (May 2015) - The Communication on a Digital Single Market Strategy includes an upcoming European “Free flow of data” initiative, which will build on the “Trusted Cloud Europe” vision and subsequent consultations. This initiative will address the emerging issues of ownership, interoperability, usability and access to data. - In the 2 nd Quarter of 2015, the Commission is expected to launch a Public consultation on a Green Paper on Trust & cloud computing in Europe. - In 2016, the Commission is planning to launch a European Cloud initiative which will include cloud services certification, contracts and switching of cloud services providers. Some of the elements stem from the work carried out by the industry working groups (C-SIGs) on the EU Cloud Computing Strategy. - The Commission is currently still assessing whether to opt for full, co- or self-regulatory actions.

The NIS Directive - opportunities Trustworthy Cloud Principles Proposal for a Directive on Network and Information Security (February 2013) - The Directive aims to raise the level of network and information security across European critical operators. - The Directive is a first step towards building more common approaches to cybersecurity. This can result in a more integrated operational picture, sharing of strategic assessments from reported incidents and enhanced publicprivate cooperation. - Cybersecurity baseline: the Directive should result in processes and capabilities to pro-actively prevent serious cybersecurity incidents as well as the ability to isolate and quickly recover from any incident. - Directive is likely to be adopted in the Second half of 2015 and Member States will get 18 -24 months for transposition in national law.

The NIS Directive – Challenges Scope -> Latvian Presidency has proposed separate Annex & approach for IEs -> details remain unclear Reporting obligations -> to whom do pan-EU operators report? -> how would internet enablers determine impact on customer side? -> how is customer confidentiality ensured? Security Baselines & Audit requirements -> Which security standards would be applied by which NCA? -> Which NCA would receive audits? New audit powers vs. sharing existing audit results? Lack of EU Harmonization: Major Challenges around Jurisdiction/Applicable Law Cybersecurity Patchwork: Could end up with 28 entirely different regimes


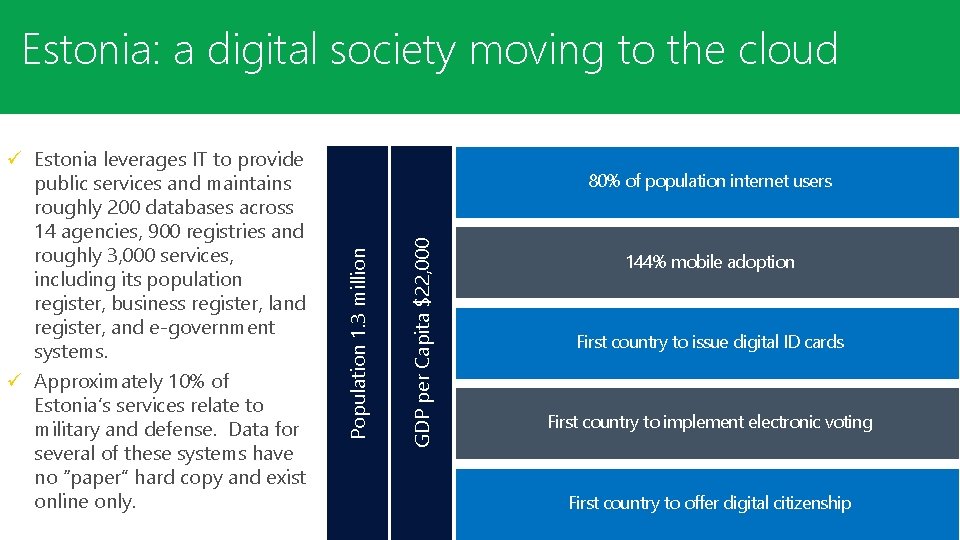
Estonia: aa digital to to thethe cloud Estonia: digitalsocietymoving cloud GDP per Capita $22, 000 80% of population internet users Population 1. 3 million ü Estonia leverages IT to provide public services and maintains roughly 200 databases across 14 agencies, 900 registries and roughly 3, 000 services, including its population register, business register, land register, and e-government systems. ü Approximately 10% of Estonia’s services relate to military and defense. Data for several of these systems have no “paper” hard copy and exist online only. 144% mobile adoption First country to issue digital ID cards First country to implement electronic voting First country to offer digital citizenship

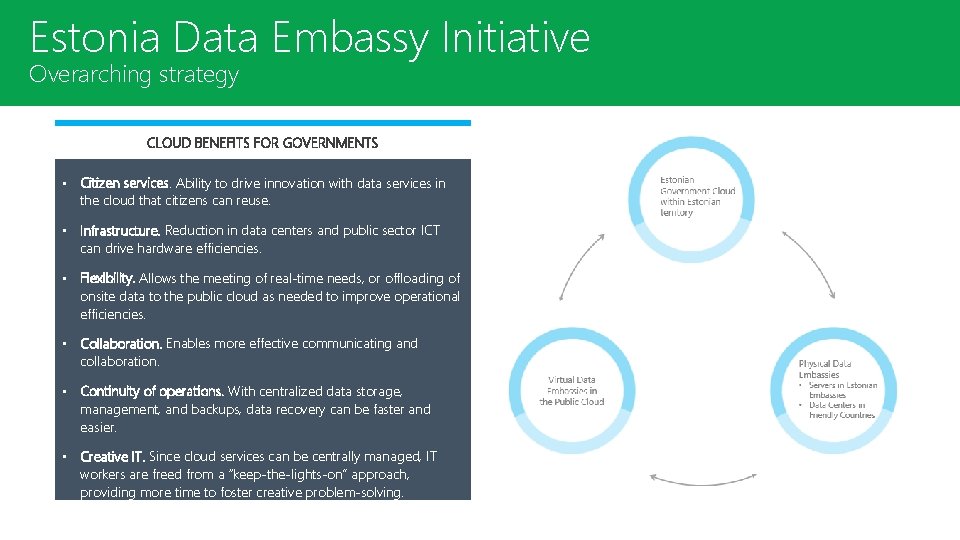
Estonian. Data Embassy Initiative Estonia Initiative Overarching strategy CLOUD BENEFITS FOR GOVERNMENTS • Citizen services. Ability to drive innovation with data services in the cloud that citizens can reuse. • Infrastructure. Reduction in data centers and public sector ICT can drive hardware efficiencies. • Flexibility. Allows the meeting of real-time needs, or offloading of onsite data to the public cloud as needed to improve operational efficiencies. • Collaboration. Enables more effective communicating and collaboration. • Continuity of operations. With centralized data storage, management, and backups, data recovery can be faster and easier. • Creative IT. Since cloud services can be centrally managed, IT workers are freed from a “keep-the-lights-on” approach, providing more time to foster creative problem-solving.

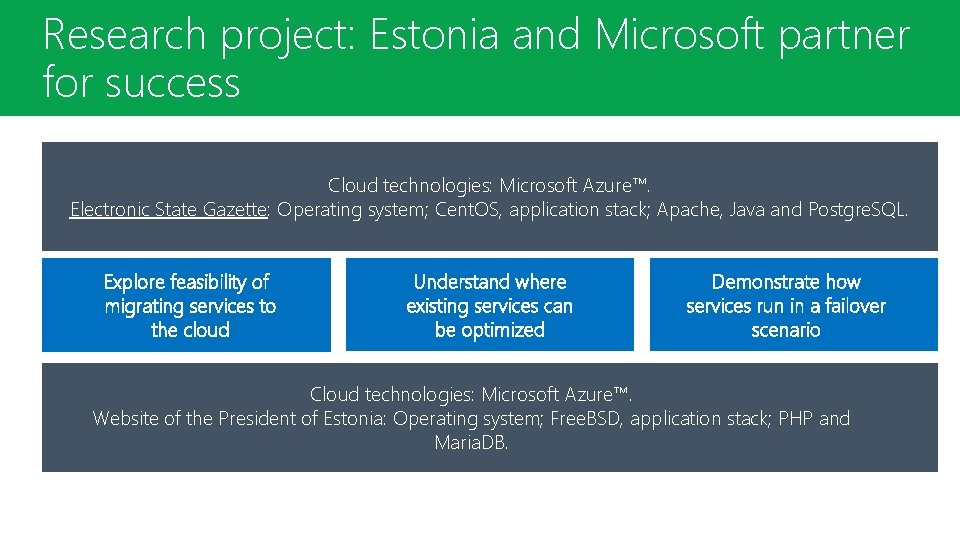
Research. Project: project: Estonia Microsoft partner Research Estonia andand Microsoft partner forsuccess Cloud technologies: Microsoft Azure™. Electronic State Gazette: Operating system; Cent. OS, application stack; Apache, Java and Postgre. SQL. Explore feasibility of migrating services to the cloud Understand where existing services can be optimized Demonstrate how services run in a failover scenario Cloud technologies: Microsoft Azure™. Website of the President of Estonia: Operating system; Free. BSD, application stack; PHP and Maria. DB.

15