2010 Worldwide Security Conference Security Functional Management Security



- Slides: 5

2010 Worldwide Security Conference Security Functional Management

Security Functional Management Security Resource Management • Management Decision Package (MDEP) GPSI - Personnel Security Investigations (PSI) projections and billing validation - Army Central Clearance Facility (A/CCF) operations - Army Investigative Enterprise Solution (AIES) resource implementation • Management Decision Package (MDEP) QSEC - Security specialist civ-pay (not exclusive to all 0080 s) - Training / Travel - Operational Equipment • Building the Program Objective Memorandum (POM) - Initial Programming - Command Participation - Program Evaluation Groups (PEGs) - POM - OSD Review - Program Decision Memorandums (PDMs)

Security Functional Management Security Manpower Model • Decision Point 91 / 59 - ACOMs, ASCCs, and DRUs will independently manage and execute their security programs - IMCOM will provide internal security support and will not be a service provider to Commands unless specifically delineated in MOAs/MOUs § Model Development - Security Manpower Model will allow re-alignment of security resources (Table of Distribution and Allowances (TDA)) in order for commands to execute mission and provide a validated manpower model to use for security resourcing - Installation support and resources remain in place until TDA re-alignment

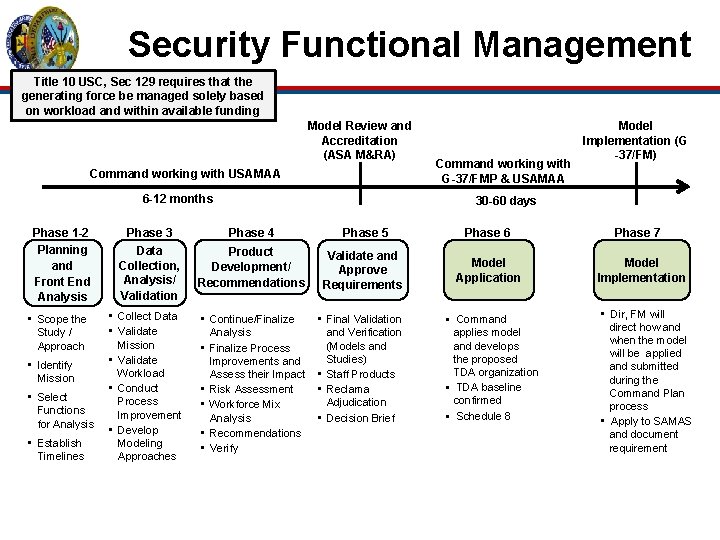
Security Functional Management Title 10 USC, Sec 129 requires that the generating force be managed solely based on workload and within available funding Model Review and Accreditation (ASA M&RA) Command working with USAMAA 6 -12 months Phase 1 -2 Planning and Front End Analysis • Scope the Study / Approach • Identify Mission • Select Functions for Analysis • Establish Timelines Command working with G-37/FMP & USAMAA Model Implementation (G -37/FM) 30 -60 days Phase 3 Phase 4 Phase 5 Phase 6 Data Collection, Analysis/ Validation Product Development/ Recommendations Validate and Approve Requirements Model Application • Collect Data • Validate Mission • Validate Workload • Conduct Process Improvement • Develop Modeling Approaches • Continue/Finalize Analysis • Finalize Process Improvements and Assess their Impact • Risk Assessment • Workforce Mix Analysis • Recommendations • Verify • Final Validation and Verification (Models and Studies) • Staff Products • Reclama Adjudication • Decision Brief § Command applies model and develops the proposed TDA organization § TDA baseline confirmed § Schedule 8 Phase 7 Model Implementation • Dir, FM will direct how and when the model will be applied and submitted during the Command Plan process • Apply to SAMAS and document requirement

Security Functional Management Mr. Andrew (Drew) Mc. Call Security Functional Manager HQDA, ODCS, G-2 Andrew. Mc. Call@us. army. mil 703 -695 -2569