Encryption methods Symmetric cryptography Sender and receiver know







- Slides: 19

Encryption methods • Symmetric cryptography – Sender and receiver know the secret key (apriori ) • Fast encryption, but key exchange should happen outside the system • Asymmetric cryptography – Each person maintains two keys, public and private • M Private. Key(Public. Key(M)) • M Public. Key (Private. Key(M)) – Public part is available to anyone, private part is only known to the sender – E. g. Pretty Good Privacy (PGP), RSA CSE 542: Operating Systems

My Public Key -----BEGIN PGP PUBLIC KEY BLOCK----Version: PGPfreeware 7. 0. 3 for non-commercial use <http: //www. pgp. com> m. QGi. BDqt. LPw. RBADn. G 0+9 Ik. Dv. I 8 t/3 wd. L 3 CSO 4 Dyt. EH 0 Njr. Nw. AYYIaewp 3 Mklsxk. P p 6 i. Vblwii. CH 4 T 4 Nqkaru+ka. EQ 1 h. STa 7 E/F 9 y. QCWN 5 J 0 u 1 U 7 mtg. TKFyt 7 VG 0 tx. AVx t. V 7 Tuyx. Nog. Jkpm 2 Bqo. Kqq. Ud. Cdbm+Gur. X/G 2 ynb. INj. EOvhcy 0 i 1 ttxgy. Drw. Cg/8 HZ t. M 0 i 06 VVNc. R/QCm. A+Jd. HGw. MEAIj. XLVV 97 hu. Etpu. WDiq 4 J 53 ec. V 3 HXQm 6 Xo. UZq 4 Sc n+nsv. Xe 4 UD+6 ldub/ri. Oq. By 22 f. BBAKh. Us. M 3 l. GFgr 7 h 19 X 3 RGdw/y. BVox+BLajp. W+ F+ddj. JAVSFe. Tv. Nanhn. XL 9 a 3 nw. CThb 4 a. EUTd. D 61 kgo. UWJl 2 Bns. K 1 DUSo 2 X 6 As. ZYo+ Gkn. OA/92 d. UNYUzsp. PLk. Xv. Pj. Oo+u. JEr. ZA 4 a. N+UYs. Jw. D 3 Al. Yug. VLkc 3 n. QBQy. SO 4 b. AR Xitjn. N 0 DA 6 Kz/j 6 e+cq. Re. Cy. Eu. Bn. Pta. Y/Nn/d. An 1 lg. Ul. J/Et. KQ 9 J 4 kr. I 3+Rx. Rmlp. Y Ut. Wy. Taak. V/QCXk. B/y. B 9 i 6 i. Afs. Cprlc. RSpm. ZAGu. NXr+p. HTHB 0 ILQm. U 3 Vy. ZW 5 k. YXIg Q 2 hhbm. Ry. YSA 8 c 3 Vy. ZW 5 k. YXJAY 3 Mud. Wdh. Lm. Vkd. T 6 JAFg. EEBECABg. FAjqt. LPw. ICw. MJ CAc. CAQo. CGQEFGw. MAAAAACgk. Ql. U 7 d. FVWfeisq. TACf. Xx. U 9 a 1 mbou. W 2 nb. Wdx 6 MHat. Q 6 TOg. Ao. M 9 W 1 PBRW 8 Iz 3 BIgcn. Ss. Z 2 UPNJHDu. QINBDqt. LPw. QCAD 2 Qle 3 CH 8 IF 3 Kiutap Qv. MF 6 Pl. TETl. Ptv. Fuu. Us 4 INo. Bp 1 aj. FOm. PQFXz 0 Af. Gy 0 Opl. K 33 TGSGSfg. Mg 71 l 6 Rf. U od. NQ+PVZX 9 x 2 Uk 89 PY 3 bzpnh. V 5 JZzf 24 rn. RPxfx 2 v. IPFRz. Bhznz. JZv 8 V+bv 9 k. V 7 H Aar. TW 56 No. KVy. Ot. Qa 8 L 9 GAFgr 5 f. SI/Vh. OSdv. NILSd 5 JEHNmszb. Dg. NRR 0 Pf. Iiz. HHxb LY 7288 kjw. EPwp. Vs. Yj. Y 67 VYy 4 XTj. TNP 18 F 1 d. Dox 0 Yb. N 4 z. ISy 1 Kv 884 b. Ep. QBg. Rj. Xy. E pwpy 1 ob. EAxn. IByl 6 yp. UM 2 Zafq 9 AKUJs. CRt. MIPWak. XUGfn. Hy 9 i. Usi. GSa 6 q 6 Jew 1 Xp Mgs 7 AAICCACLx. NC 3 Vth 553 Y 90 JCVy. M 9 m. PWzvrkjf. EGf. Bi. CFDZ 0 HONW 81 yw. Uy. V 6 j. T O/1 s. Usg. R 7 j. GB 26 XBsn. IY 96 a 9 WTp. Uo. I+20 Yst. FLRj 8 s. XOVXua. P/YTmg. SLv 82 O 6 SWd Bze 1 S 0 YJc. U 31/zd. Cftsz 67 UWT 8 vg 39 ye. Gy. Q 5 KQP 83 p 9 DKpi 4 Z 5 K 4 M 29 p 8 e. Ct 9 BY+ kid 94 h 9+16 ZT 8 JLF 0 i. Ew. Gap. Zvpa. Tuc. CNo. C 8 t 6 CKPto 0 d. Gpk. Yp 7 u. BYo. Sz. Lg. Nv. Uh 2 n Bj. GVEm. Luioabqb. Oaom. DEr. ITY 2 i. Nc. W 3 CCgjj. Yvgg/Hnu 7 HB 2 x. Kzu. VUN 1 NTGogcu. NI Yx 88 mi+d/Hx. TY 6 YNr 9 x. NW 0 f 0 p. Wk. ZDVB 0 i. QBMBBg. RAg. AMBQI 6 r. Sz 8 BRs. MAAAAAAo. J EJVO 3 RVVn 3 or. Yh. IAo. IQPx. Gv. Hm. X 8 c 6 ka. AZqko 1 z. YCeixc. AJ 9 tp 5 h/KQZr. IN/Bpy. TW 9 Xgv 4 qx. KEA== =Pv 5 O -----END PGP PUBLIC KEY BLOCK----- CSE 542: Operating Systems

RSA • Named after Rivest, Shamir and Adleman – Only receiver receives message: • Encode message using receivers public key – Only sender could’ve sent the message • Encode message using sender’s private key – Only sender could’ve sent the message and only receiver can read the message • Encode message using receivers public key and then encode using our private key CSE 542: Operating Systems

Strength • Strength of crypto system depends on the strengths of the keys • Computers get faster – keys have to become harder to keep up • If it takes more effort to break a code than is worth, it is okay – Transferring money from my bank to my credit card and Citibank transferring billions of dollars with another bank should not have the same key strength CSE 542: Operating Systems

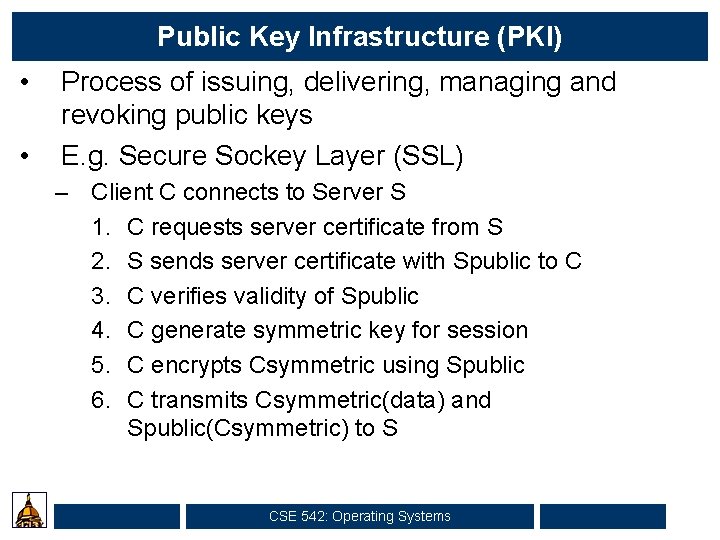
Public Key Infrastructure (PKI) • • Process of issuing, delivering, managing and revoking public keys E. g. Secure Sockey Layer (SSL) – Client C connects to Server S 1. C requests server certificate from S 2. S sends server certificate with Spublic to C 3. C verifies validity of Spublic 4. C generate symmetric key for session 5. C encrypts Csymmetric using Spublic 6. C transmits Csymmetric(data) and Spublic(Csymmetric) to S CSE 542: Operating Systems

Authentication • Identification verification process – E. g. kerberos certificates, digital certificates, smart cards • Used to grant resources to authorized users CSE 542: Operating Systems

Practical Public Key Cryptosystem 1. 2. 3. 4. Decrypt(Encrypt(Message)) = Message Encrypt() and Decrypt() are easy to compute Encrypt() does not reveal Decrypt() Encrypt(Decrypt(Message)) = Message • Function satisfying 1 -3: Trap-door one-way function – One way: easy to compute in one direction, difficult in the other direction – Trap-door: Inverse functions are easy to compute once certain private “trap-door” information is known. • 1 -4: permutation CSE 542: Operating Systems

Signature • Encrypt using private key of sender. Anyone can decrypt using the public key of sender to verify signature -----BEGIN PGP SIGNED MESSAGE----Hash: SHA 1 Hello world!! -----BEGIN PGP SIGNATURE----Version: PGPfreeware 7. 0. 3 for non-commercial use <http: //www. pgp. com> i. QA/Aw. UBOq 8 LO 5 VO 3 RVVn 3 or. EQLFZw. Cd. Gi 9 AWvlholla. Ymr 9 TPvtdb. K oe 20 Ao. LLr vb. J 8 Sgk. IZ 73 l. Cy 6 SXDi 91 osd =L 3 Sh -----END PGP SIGNATURE----CSE 542: Operating Systems

Privacy • Encrypt with receivers public key -----BEGIN PGP MESSAGE----Version: PGPfreeware 7. 0. 3 for non-commercial use <http: //www. pgp. com> q. ANQR 1 DBw. U 4 D 30 m 79 rqmj. HMQB/4 q 1 mu 3 IP 8 As. MBYSUW 6 ud. XZn. F 0/LVL 51 e. Yz. Vn. AW Ixgbxh. Hm. Bo. Zf 9 YElto. Xw 82 gkg. Vebz+3 Xfj 6 T 5 m. LNy 5 FA 6 cg. KKw 57 AY 9 Bl 3 a. EKl. JK /n. V 5 q. R 8 E/VZOha. Poog 8 dt. V 1 Hpi 5 Z 0 v. NCI 7 s 5 Ibp 3 C 2 tlrg. Ytvy. Yfe 86 bq. CNe 3 y. AI bt. TUT+b. A 9 HL 3 p. Xqh. Oo. Wl. RB+N 58 T 9 ybn/9 Fyon. YYf. Gu. Pd. MTj+Zci. K 37 R+ez. Wg 5 Ym. Z jd. DMf/Cxgll. MF/Tv 2 j. Q 8 Kgmr. KIyi 6 g. WQm. Et. Wz. FUl. APgdp. OC 7 TQC 3 s. Qq. Vj. K 4 Gy. OY 6 Wnr. Xi. Wq. O 3895 uk. BGy. Hzqyss. UTJFe 5 qnclkrm. Cv. A 3 tph+uc 7 p. CACKr. Ya. GLSWWo. QSB L 6 zch 2 Gnh. G 4+Jp. DCVKF/po. J 1 URk. B 2 Odd 9/OCRe. R 0 s. FXZFv. W 14 IJQznu 3 HOhjt. A+y g 7 Nn 736 fq. MD 9 jp. BZFf. Ut. Kv/v 4 JMy. Wc. Rdp 3 R 3 icm 03 zi 24 n+244 r 1 DQj+c. Vl. FYPfd z. RAGTLORVj. XH 2 am. Gqil. Kyxq. MU 7 ZYXIMI 43 b. FIviu 4 tab. KYn. ZJxp. M 8 ke. UKA 3 u+v. Ps X 9 ks. So. BSi. T 6 Kow 3 Lac 2 t 3 Qo 5 Tim. Yl. S 5 ODFn. C 6 Pp 9 a. RZz. Nc. BOKmi. YO 4 IIbd. FH 2 jta Rbcmes. Ej. H 5 Rpb. DV 4 Bfc. OMdm 2 UGWZe 6 k. Aa. Kk. Sdx. Hl. UVZAJnesb. T+l. Qf 4 AZj. Xkms. OM 8 qn. BKi 5 xy. S/wrh. S 4 zam. V/Mp+5 q. IGNASXUHPsp 3 rukova. ZANd. Z/Y 6 z. NQQVim 0 kphd 5 ECybm. Vr. HQ== =S 9 ph -----END PGP MESSAGE----- CSE 542: Operating Systems

Algorithm • To break their algorithm requires that you factor a large prime – Computationally very hard. Can’t be “proven” yet – With present technology, 512 bit key takes a few months to factor using “super computers”, 1024 takes a long time and 2048 takes a very long time – Takes 2 seconds to generate a 2048 bit key on a 933 Mhz Pentium – Algorithm has remained secure for the past 17 years – One of the most successful public key system CSE 542: Operating Systems

Case study: Multics • Goal: Develop a convenient, interactive, useable time shared computer system that could support many users. – Bell Labs and GE in 1965 joined an effort underway at MIT (CTSS) on Multics (Multiplexed Information and Computing Service) mainframe timesharing system. • Multics was designed to the swiss army knife of OS • Multics achieved most of these goals, but it took a long time – One of the negative contribution was the development of simple yet powerful abstractions (UNIX) CSE 542: Operating Systems

Multics: Designed to be the ultimate OS • “One of the overall design goals is to create a computing system which is capable of meeting almost all of the present and near-future requirements of a large computer utility. Such systems must run continuously and reliably 7 days a week, 24 hours a day in a way similar to telephone or power systems, and must be capable of meeting wide service demands: from multiple man-machine interaction to the sequential processing of absentee-user jobs; from the use of the system with dedicated languages and subsystems to the programming of the system itself; and from centralized bulk card, tape, and printer facilities to remotely located terminals. Such information processing and communication systems are believed to be essential for the future growth of computer use in business, in industry, in government and in scientific laboratories as well as stimulating applications which would be otherwise undone. ” CSE 542: Operating Systems

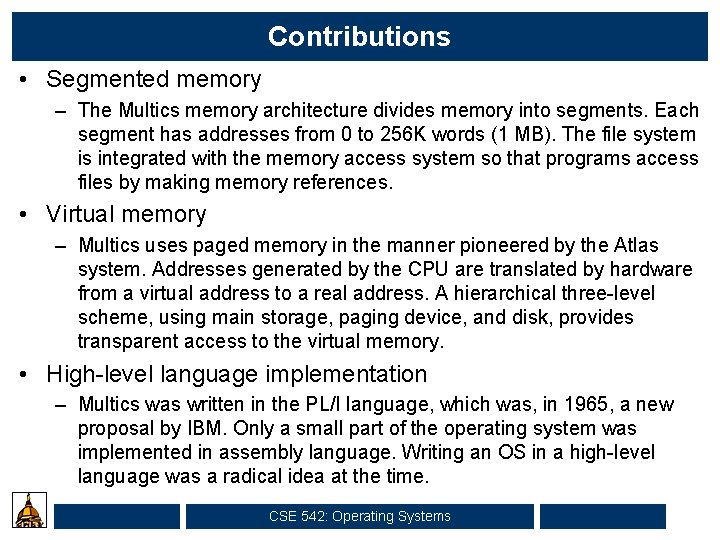
Contributions • Segmented memory – The Multics memory architecture divides memory into segments. Each segment has addresses from 0 to 256 K words (1 MB). The file system is integrated with the memory access system so that programs access files by making memory references. • Virtual memory – Multics uses paged memory in the manner pioneered by the Atlas system. Addresses generated by the CPU are translated by hardware from a virtual address to a real address. A hierarchical three-level scheme, using main storage, paging device, and disk, provides transparent access to the virtual memory. • High-level language implementation – Multics was written in the PL/I language, which was, in 1965, a new proposal by IBM. Only a small part of the operating system was implemented in assembly language. Writing an OS in a high-level language was a radical idea at the time. CSE 542: Operating Systems

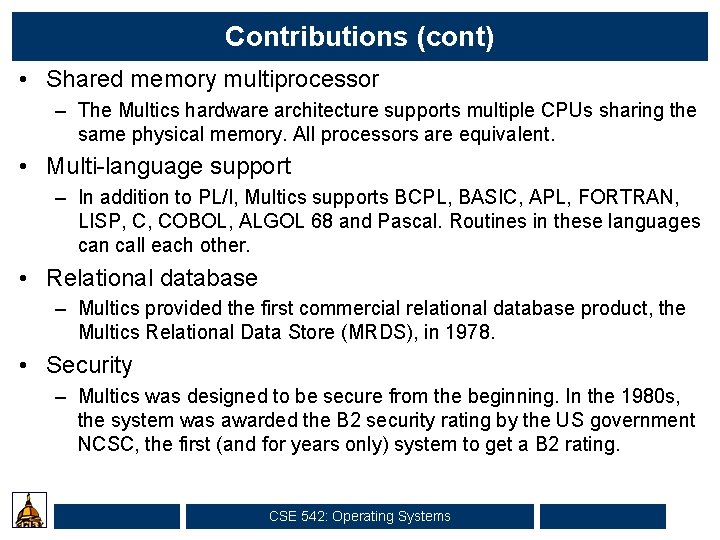
Contributions (cont) • Shared memory multiprocessor – The Multics hardware architecture supports multiple CPUs sharing the same physical memory. All processors are equivalent. • Multi-language support – In addition to PL/I, Multics supports BCPL, BASIC, APL, FORTRAN, LISP, C, COBOL, ALGOL 68 and Pascal. Routines in these languages can call each other. • Relational database – Multics provided the first commercial relational database product, the Multics Relational Data Store (MRDS), in 1978. • Security – Multics was designed to be secure from the beginning. In the 1980 s, the system was awarded the B 2 security rating by the US government NCSC, the first (and for years only) system to get a B 2 rating. CSE 542: Operating Systems

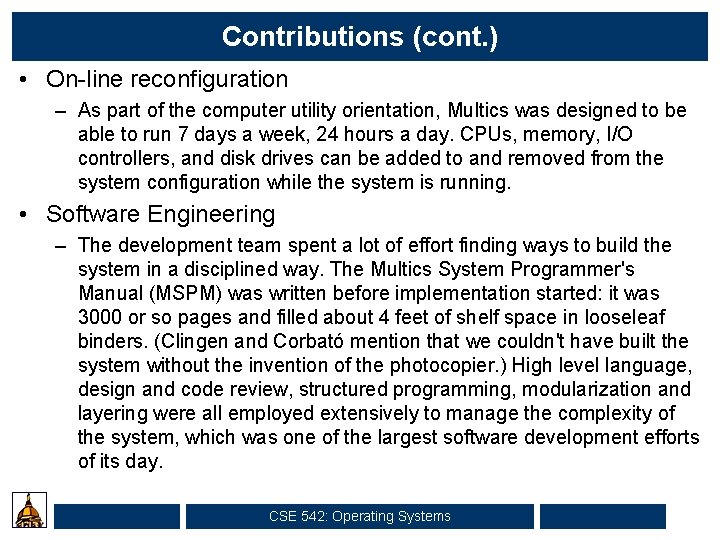
Contributions (cont. ) • On-line reconfiguration – As part of the computer utility orientation, Multics was designed to be able to run 7 days a week, 24 hours a day. CPUs, memory, I/O controllers, and disk drives can be added to and removed from the system configuration while the system is running. • Software Engineering – The development team spent a lot of effort finding ways to build the system in a disciplined way. The Multics System Programmer's Manual (MSPM) was written before implementation started: it was 3000 or so pages and filled about 4 feet of shelf space in looseleaf binders. (Clingen and Corbató mention that we couldn't have built the system without the invention of the photocopier. ) High level language, design and code review, structured programming, modularization and layering were all employed extensively to manage the complexity of the system, which was one of the largest software development efforts of its day. CSE 542: Operating Systems

Multics to UNIX • the group effort initially failed to produce an economically useful system. – Bell Labs withdrew from the effort in 1969 – Bell Labs Computing Science Research Center in Murray Hill -- Ken Thompson, Dennis Ritchie, Doug Mc. Ilroy, and J. F. Ossanna -- went on to develop UNIX (note pun) CSE 542: Operating Systems

Legacy - Positive and negative • UNIX: – Ken Thompson and Dennis Ritchie, the inventors of UNIX, worked on Multics until Bell Labs dropped out of the Multics development effort in 1969. The UNIX system's name is a pun on Multics attributed to Brian Kernighan. Some ideas in Multics were developed further in UNIX. • GCOS 6 – Honeywell's GCOS 6 operating system for the Level 6 minicomputers was strongly influenced by Multics. • Primos – Prime's Primos operating system shows a strong Multics influence. Bill Poduska worked on Multics at MIT before founding Prime, and several other senior Multicians worked at Prime. Poduska referred to Primos as "Multics in a shoebox. " CSE 542: Operating Systems

Legacy • VOS – Stratus's VOS operating system shows a strong Multics influence. Bob Freiburghouse, former Multics languages manager, was one of the founders of Stratus; many Multicians are still Stratus employees. • Apollo Domain – Bill Poduska went on from Prime to help found Apollo, and Domain was known as "Multics in a Matchbox. " Apollo's OS shows strong Multics influence. For instance, the basic access to stuff on disk is via a single-level store directly based on Multics. Supposedly some of the motivation for the object-store style of file system came from Multics too. (Info from Frederick Roeber) [Jerry Saltzer adds: ] In addition, it uses a shared memory model, despite being distributed across a network • NTT DIPS – NTT undertook a massive effort to clone Multics, which led to their DIPS (Denden Information Processing System) series of mainframes. DIPS machines are still in widespread use in Japan today by NTT, but everyone agrees that they are going away. I believe that Intermetrics developed the DIPS PL/I compiler for NTT. CSE 542: Operating Systems

Legacy • Amber • IBM System 360 • Tenex, TOPS 20, GCOS etc • Most of the project members were influential in shaping the computer industry and they took Multics ideas with them • Monolithic vs microkernel debate CSE 542: Operating Systems