El Gamal Cryptosystem In Practice DiffieHellman El Gamal





- Slides: 9

- El. Gamal Cryptosystem -In Practice - Diffie-Hellman El Gamal and Diffie Hellman CSCI 284, 162 Spring 2008 GWU CS 284 -162/Spring 08/GWU/Vora/Discrete Log

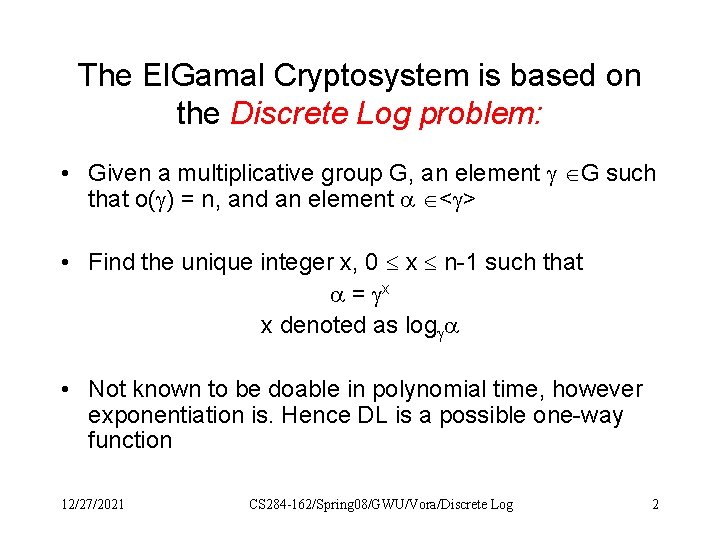
The El. Gamal Cryptosystem is based on the Discrete Log problem: • Given a multiplicative group G, an element G such that o( ) = n, and an element < > • Find the unique integer x, 0 x n-1 such that = x x denoted as log • Not known to be doable in polynomial time, however exponentiation is. Hence DL is a possible one-way function 12/27/2021 CS 284 -162/Spring 08/GWU/Vora/Discrete Log 2

El Gamal Cryptosystem Let p a prime such that DL in Zp* is infeasible Let Zp* be a primitive element P = Zp* C = Zp* X Zp* and K = {(p, , a, ): = a (mod p)} public key = (p, , ) and private key = a For a secret random number k Zp-1 e. K(x, k) = (y 1, y 2) y 1 = k mod p y 1 = x k mod p d. K (y 1, y 2) = y 2( y 1 a)-1 mod p 12/27/2021 CS 284 -162/Spring 08/GWU/Vora/Discrete Log 3

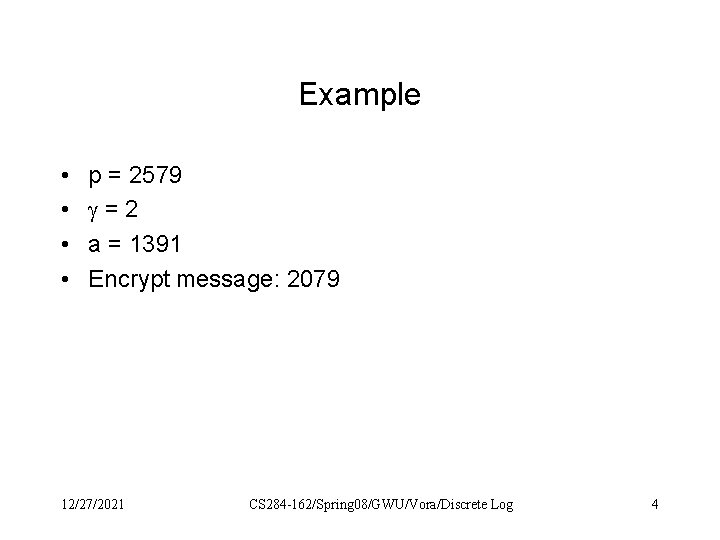
Example • • p = 2579 =2 a = 1391 Encrypt message: 2079 12/27/2021 CS 284 -162/Spring 08/GWU/Vora/Discrete Log 4

Practicalities • More efficient attacks possible unless elliptic curve DL, for which these efficient attacks are not known. • Modulus required for security: – 2160 with elliptic curves – 21880 without • DL over elliptic curves very hot problem. 12/27/2021 CS 284 -162/Spring 08/GWU/Vora/Discrete Log 5

Diffie-Hellman Key Exchange • Protocol for exchanging secret key over public channel. • Select global parameters p, n and . p is prime and is of order n in Zp*. These parameters are public and known to all. 12/27/2021 CS 284 -162/Spring 08/GWU/Vora/Discrete Log 6

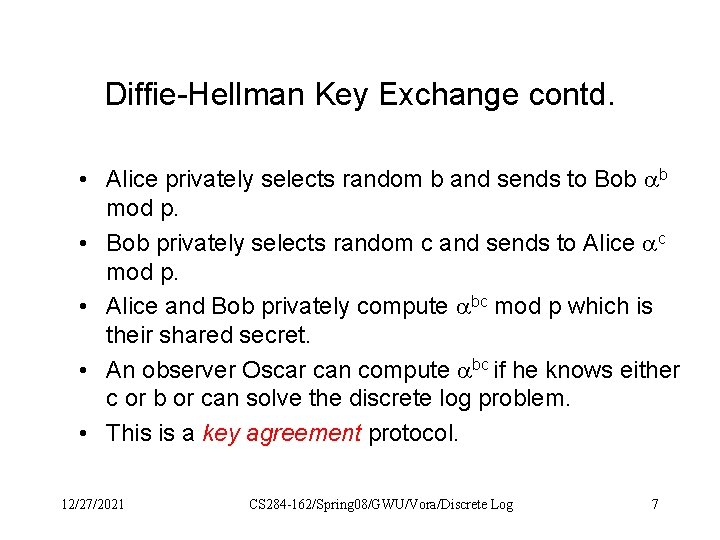
Diffie-Hellman Key Exchange contd. • Alice privately selects random b and sends to Bob b mod p. • Bob privately selects random c and sends to Alice c mod p. • Alice and Bob privately compute bc mod p which is their shared secret. • An observer Oscar can compute bc if he knows either c or b or can solve the discrete log problem. • This is a key agreement protocol. 12/27/2021 CS 284 -162/Spring 08/GWU/Vora/Discrete Log 7

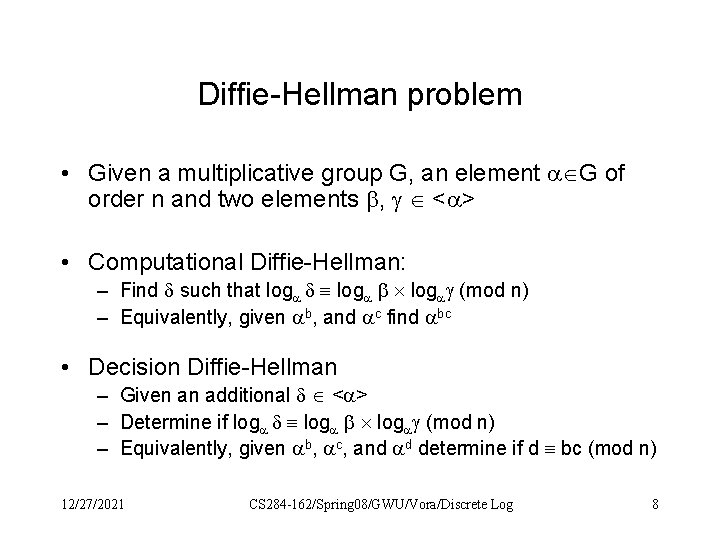
Diffie-Hellman problem • Given a multiplicative group G, an element G of order n and two elements , < > • Computational Diffie-Hellman: – Find such that log log (mod n) – Equivalently, given b, and c find bc • Decision Diffie-Hellman – Given an additional < > – Determine if log log (mod n) – Equivalently, given b, c, and d determine if d bc (mod n) 12/27/2021 CS 284 -162/Spring 08/GWU/Vora/Discrete Log 8

An attack Diffie-Hellman key exchange is susceptible to a man-in-themiddle attack. – Mallory captures b and c in transmission and replaces with own b’ and c’. – Essentially runs two Diffie-Hellman’s. One with Alice and one with Bob. 12/27/2021 CS 284 -162/Spring 08/GWU/Vora/Discrete Log 9