Modified El Gamal Elliptic Curve Cryptosystem using Hexadecimal

- Slides: 10

Modified El. Gamal Elliptic Curve Cryptosystem using Hexadecimal Representation Author: Ziad E. Dawahdeh, Shahrul N. Yaakob and Ali Makki Sagheer Publisher: Indian Journal of Science and Technology, 2015 Presenter: 柯懷貿 Date: 2019/03/27 Department of Computer Science and Information Engineering National Cheng Kung University, Taiwan R. O. C.

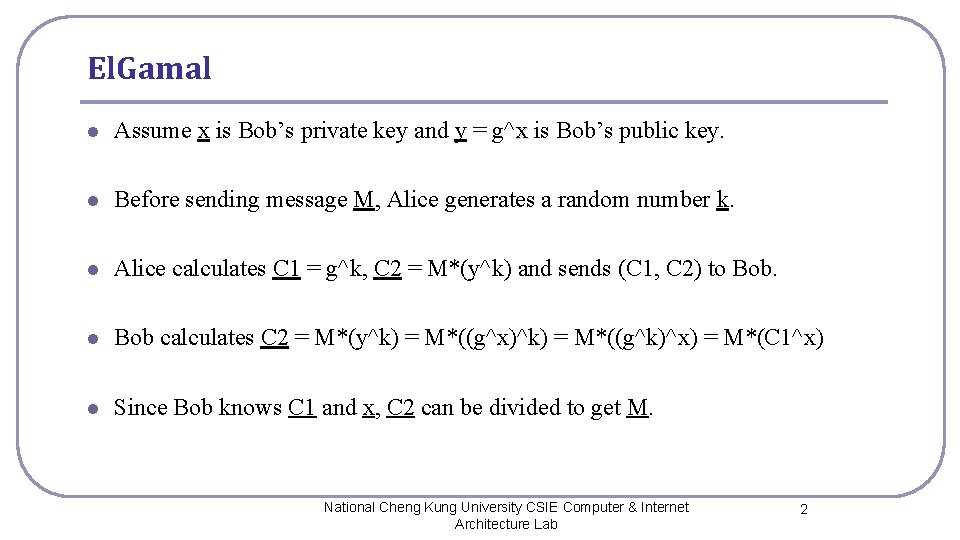
El. Gamal l Assume x is Bob’s private key and y = g^x is Bob’s public key. l Before sending message M, Alice generates a random number k. l Alice calculates C 1 = g^k, C 2 = M*(y^k) and sends (C 1, C 2) to Bob. l Bob calculates C 2 = M*(y^k) = M*((g^x)^k) = M*((g^k)^x) = M*(C 1^x) l Since Bob knows C 1 and x, C 2 can be divided to get M. National Cheng Kung University CSIE Computer & Internet Architecture Lab 2

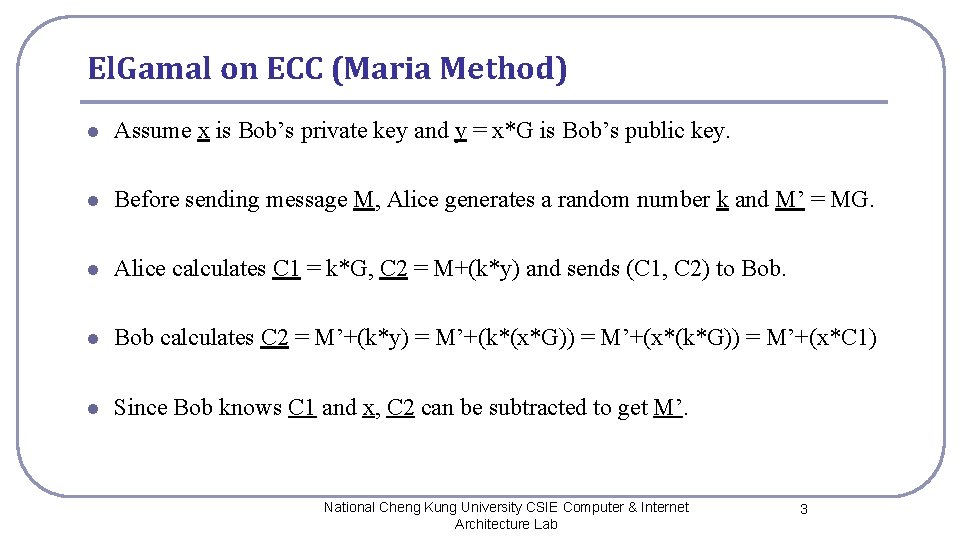
El. Gamal on ECC (Maria Method) l Assume x is Bob’s private key and y = x*G is Bob’s public key. l Before sending message M, Alice generates a random number k and M’ = MG. l Alice calculates C 1 = k*G, C 2 = M+(k*y) and sends (C 1, C 2) to Bob. l Bob calculates C 2 = M’+(k*y) = M’+(k*(x*G)) = M’+(x*(k*G)) = M’+(x*C 1) l Since Bob knows C 1 and x, C 2 can be subtracted to get M’. National Cheng Kung University CSIE Computer & Internet Architecture Lab 3

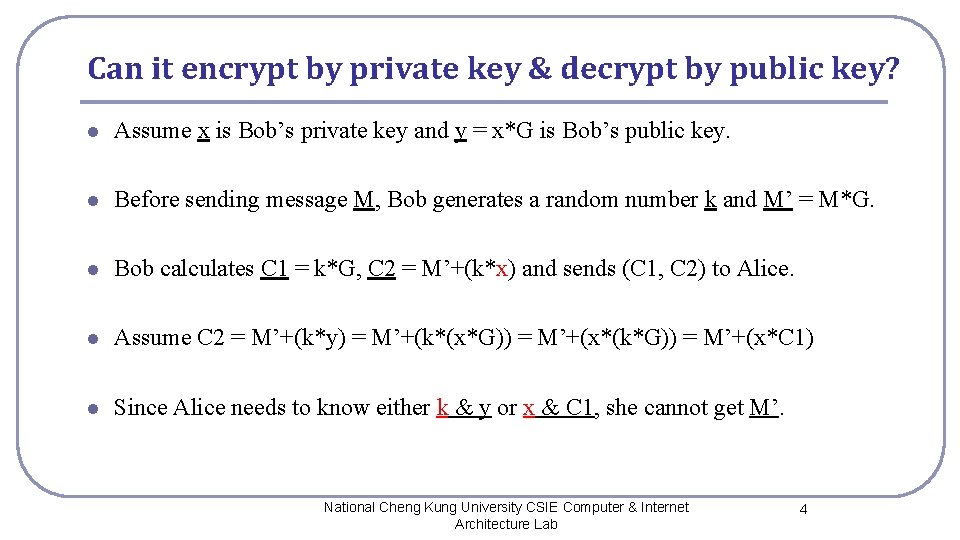
Can it encrypt by private key & decrypt by public key? l Assume x is Bob’s private key and y = x*G is Bob’s public key. l Before sending message M, Bob generates a random number k and M’ = M*G. l Bob calculates C 1 = k*G, C 2 = M’+(k*x) and sends (C 1, C 2) to Alice. l Assume C 2 = M’+(k*y) = M’+(k*(x*G)) = M’+(x*(k*G)) = M’+(x*C 1) l Since Alice needs to know either k & y or x & C 1, she cannot get M’. National Cheng Kung University CSIE Computer & Internet Architecture Lab 4

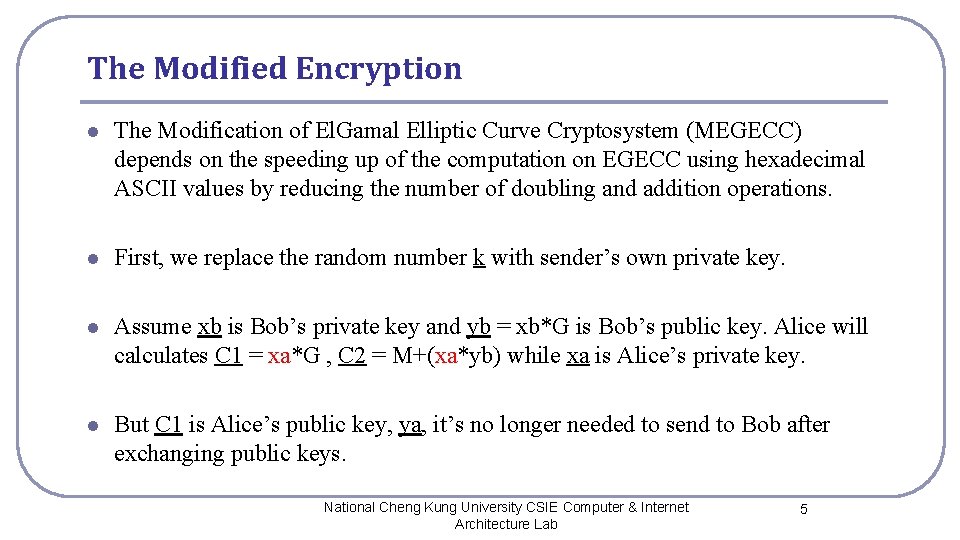
The Modified Encryption l The Modification of El. Gamal Elliptic Curve Cryptosystem (MEGECC) depends on the speeding up of the computation on EGECC using hexadecimal ASCII values by reducing the number of doubling and addition operations. l First, we replace the random number k with sender’s own private key. l Assume xb is Bob’s private key and yb = xb*G is Bob’s public key. Alice will calculates C 1 = xa*G , C 2 = M+(xa*yb) while xa is Alice’s private key. l But C 1 is Alice’s public key, ya, it’s no longer needed to send to Bob after exchanging public keys. National Cheng Kung University CSIE Computer & Internet Architecture Lab 5

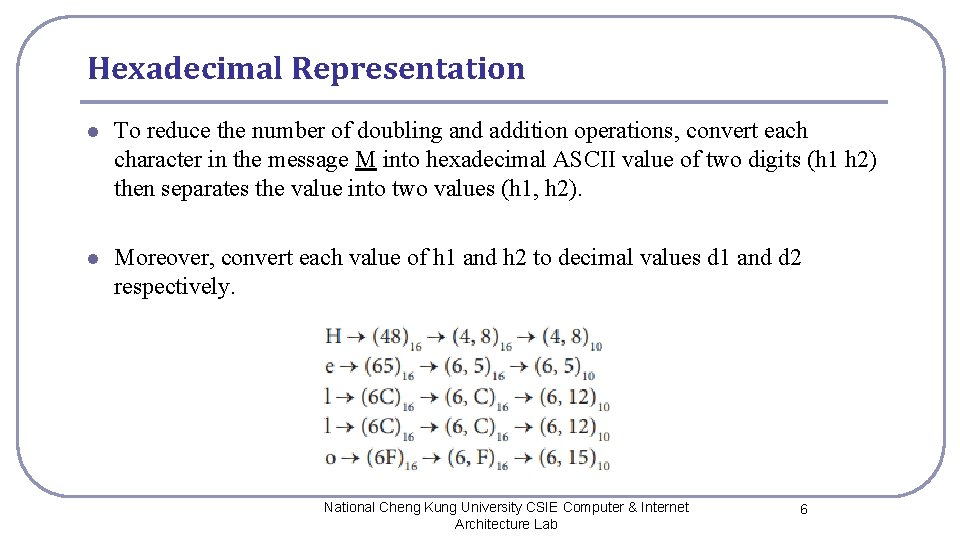
Hexadecimal Representation l To reduce the number of doubling and addition operations, convert each character in the message M into hexadecimal ASCII value of two digits (h 1 h 2) then separates the value into two values (h 1, h 2). l Moreover, convert each value of h 1 and h 2 to decimal values d 1 and d 2 respectively. National Cheng Kung University CSIE Computer & Internet Architecture Lab 6

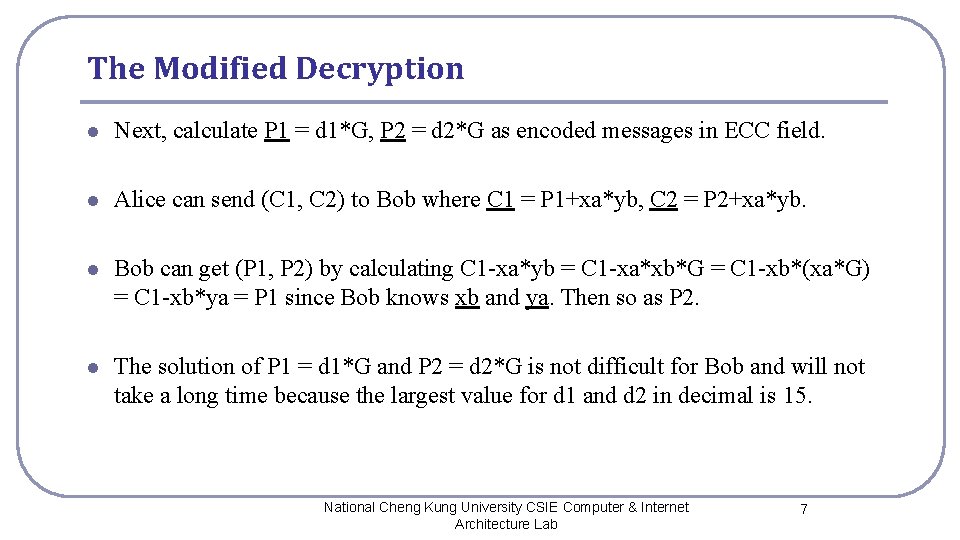
The Modified Decryption l Next, calculate P 1 = d 1*G, P 2 = d 2*G as encoded messages in ECC field. l Alice can send (C 1, C 2) to Bob where C 1 = P 1+xa*yb, C 2 = P 2+xa*yb. l Bob can get (P 1, P 2) by calculating C 1 -xa*yb = C 1 -xa*xb*G = C 1 -xb*(xa*G) = C 1 -xb*ya = P 1 since Bob knows xb and ya. Then so as P 2. l The solution of P 1 = d 1*G and P 2 = d 2*G is not difficult for Bob and will not take a long time because the largest value for d 1 and d 2 in decimal is 15. National Cheng Kung University CSIE Computer & Internet Architecture Lab 7

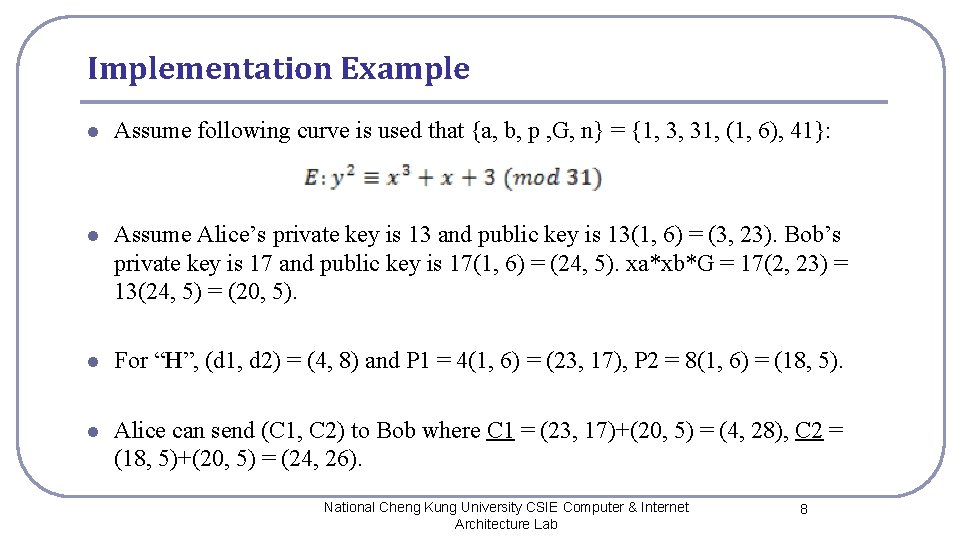
Implementation Example l Assume following curve is used that {a, b, p , G, n} = {1, 3, 31, (1, 6), 41}: l Assume Alice’s private key is 13 and public key is 13(1, 6) = (3, 23). Bob’s private key is 17 and public key is 17(1, 6) = (24, 5). xa*xb*G = 17(2, 23) = 13(24, 5) = (20, 5). l For “H”, (d 1, d 2) = (4, 8) and P 1 = 4(1, 6) = (23, 17), P 2 = 8(1, 6) = (18, 5). l Alice can send (C 1, C 2) to Bob where C 1 = (23, 17)+(20, 5) = (4, 28), C 2 = (18, 5)+(20, 5) = (24, 26). National Cheng Kung University CSIE Computer & Internet Architecture Lab 8

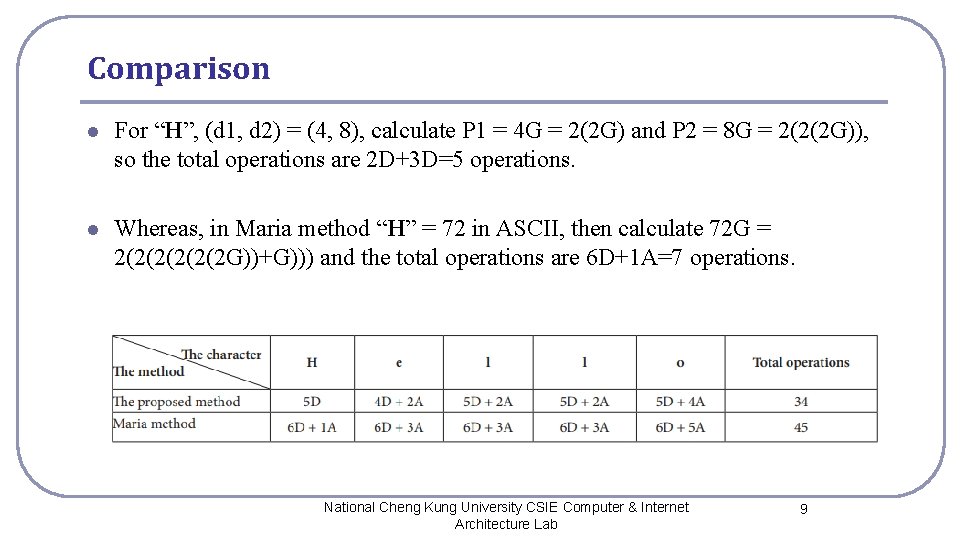
Comparison l For “H”, (d 1, d 2) = (4, 8), calculate P 1 = 4 G = 2(2 G) and P 2 = 8 G = 2(2(2 G)), so the total operations are 2 D+3 D=5 operations. l Whereas, in Maria method “H” = 72 in ASCII, then calculate 72 G = 2(2(2(2 G))+G))) and the total operations are 6 D+1 A=7 operations. National Cheng Kung University CSIE Computer & Internet Architecture Lab 9

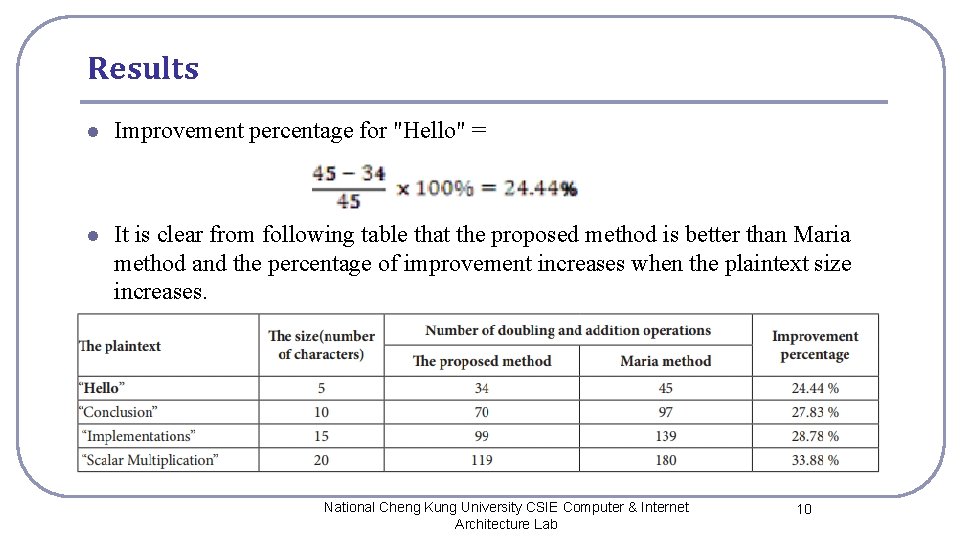
Results l Improvement percentage for "Hello" = l It is clear from following table that the proposed method is better than Maria method and the percentage of improvement increases when the plaintext size increases. National Cheng Kung University CSIE Computer & Internet Architecture Lab 10