ECE 4371 Fall 2017 Introduction to Telecommunication EngineeringTelecommunication






- Slides: 33

ECE 4371, Fall, 2017 Introduction to Telecommunication Engineering/Telecommunication Laboratory Zhu Han Department of Electrical and Computer Engineering Class 5 Sep. 18 nd, 2017

Overview l Cochannel interference l Analysis of Noise – Math model (good thing, not required) – Noise shape, preemphasis/deemphasis – FM threshold effects l Security basics l Good news: This is the last class for exam 1 l HW 2, 5. 1. 1, 5. 1. 4, 5. 2. 7, 5. 3. 1, 5. 4. 2, 5. 4. 3, due 10/2/17 l Project one due 10/2/17 l Exam time?

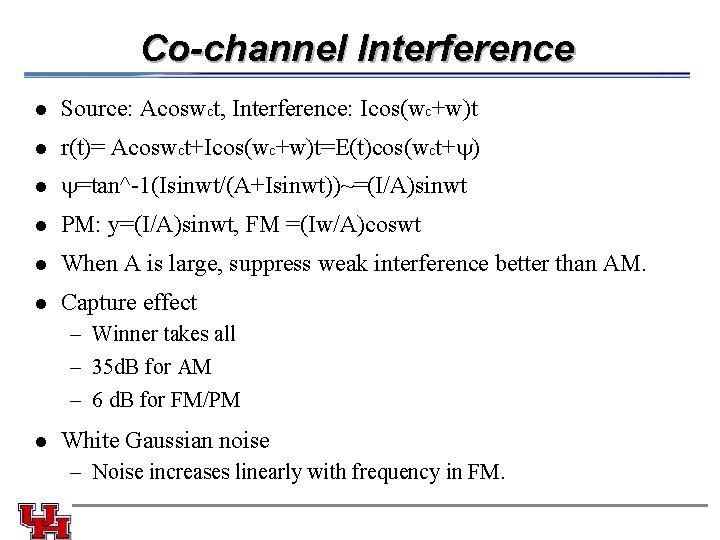
Co-channel Interference l Source: Acoswct, Interference: Icos(wc+w)t l r(t)= Acoswct+Icos(wc+w)t=E(t)cos(wct+ ) l =tan^-1(Isinwt/(A+Isinwt))~=(I/A)sinwt l PM: y=(I/A)sinwt, FM =(Iw/A)coswt l When A is large, suppress weak interference better than AM. l Capture effect – Winner takes all – 35 d. B for AM – 6 d. B for FM/PM l White Gaussian noise – Noise increases linearly with frequency in FM.

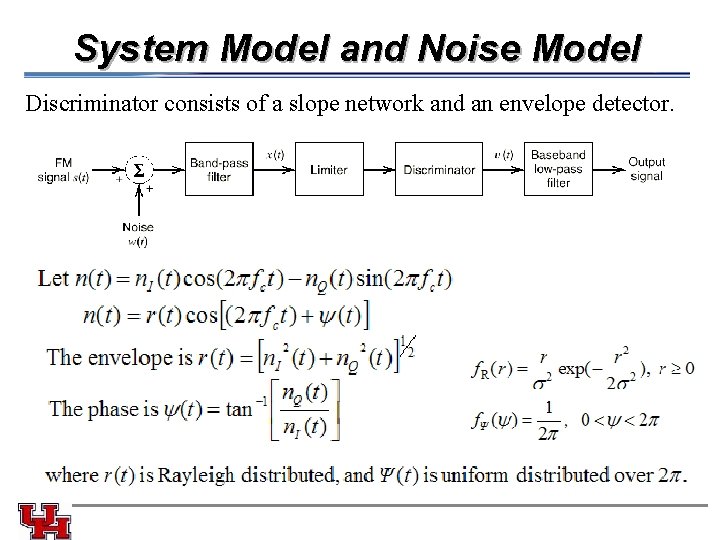
System Model and Noise Model Discriminator consists of a slope network and an envelope detector.

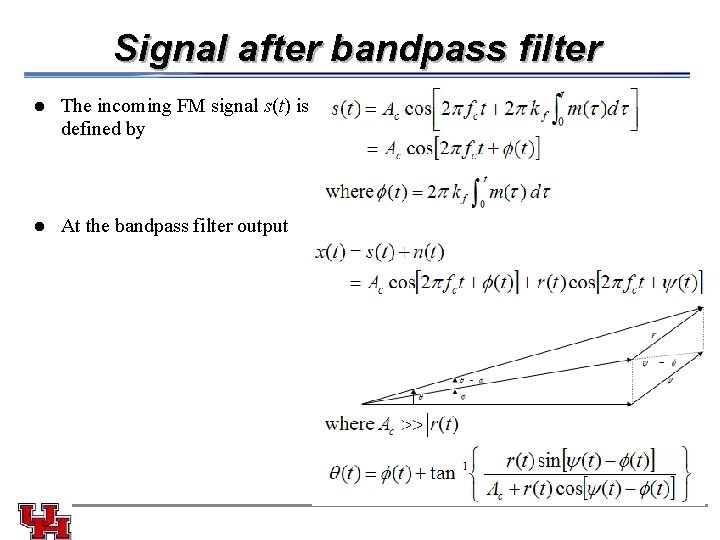
Signal after bandpass filter l The incoming FM signal s(t) is defined by l At the bandpass filter output

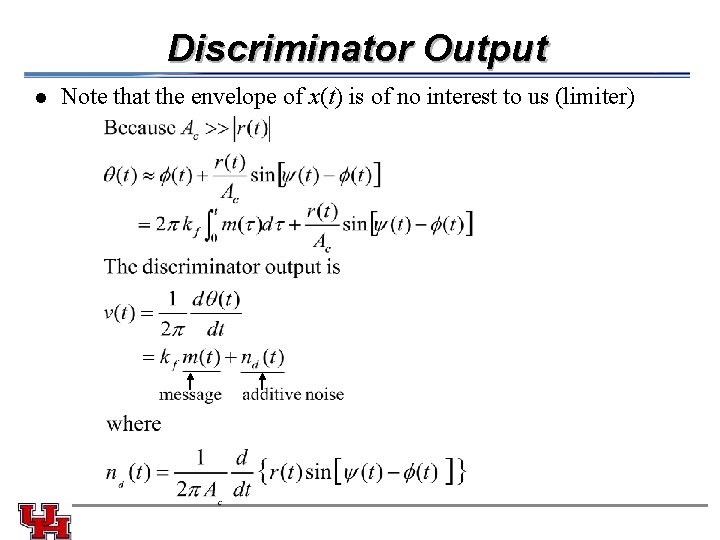
Discriminator Output l Note that the envelope of x(t) is of no interest to us (limiter)

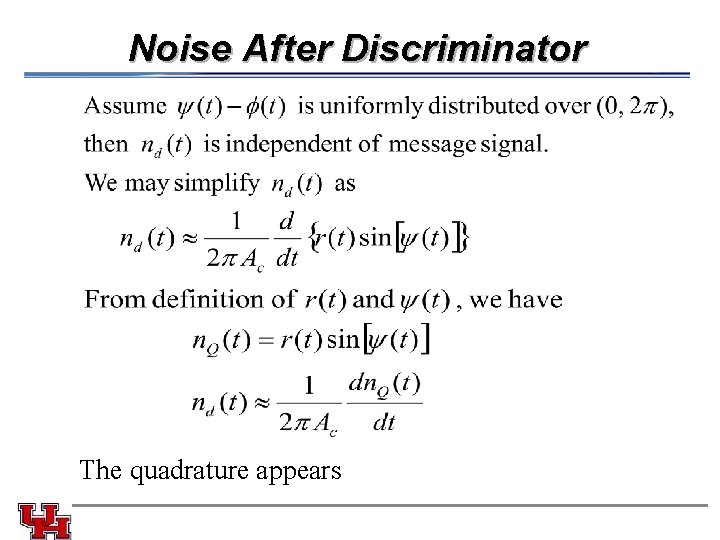
Noise After Discriminator The quadrature appears

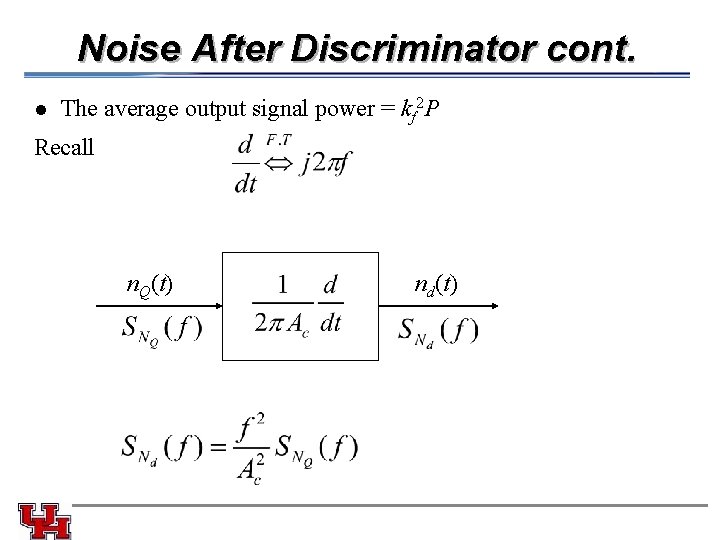
Noise After Discriminator cont. l The average output signal power = kf 2 P Recall n. Q(t) nd(t)

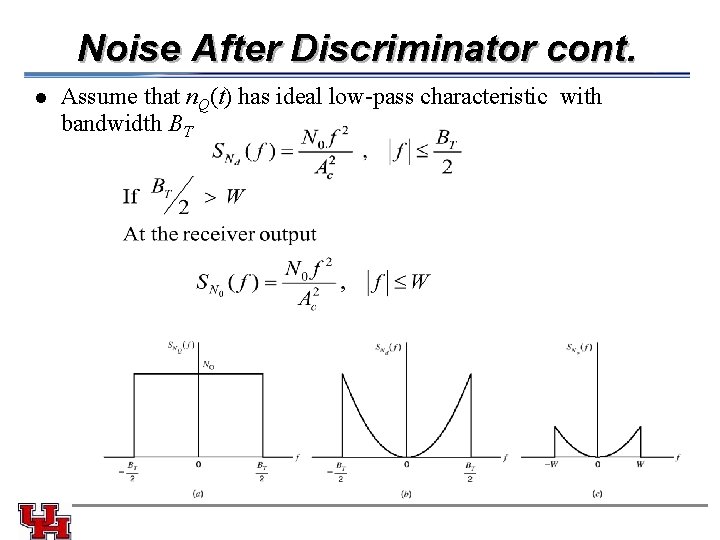
Noise After Discriminator cont. l Assume that n. Q(t) has ideal low-pass characteristic with bandwidth BT

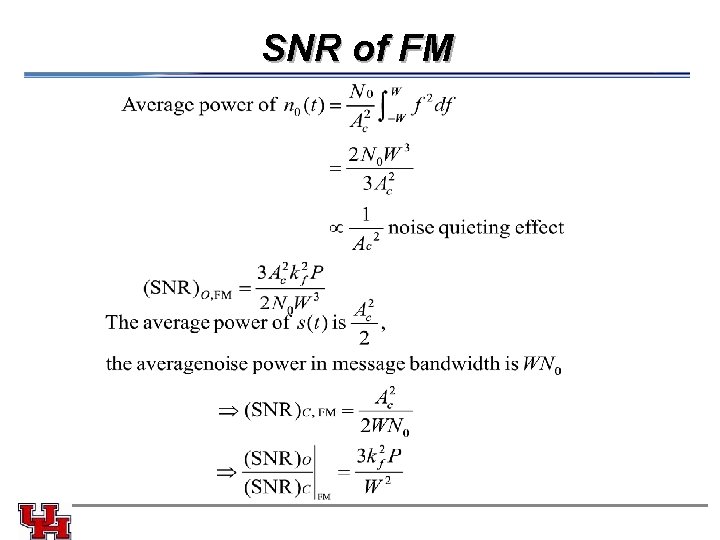
SNR of FM 71

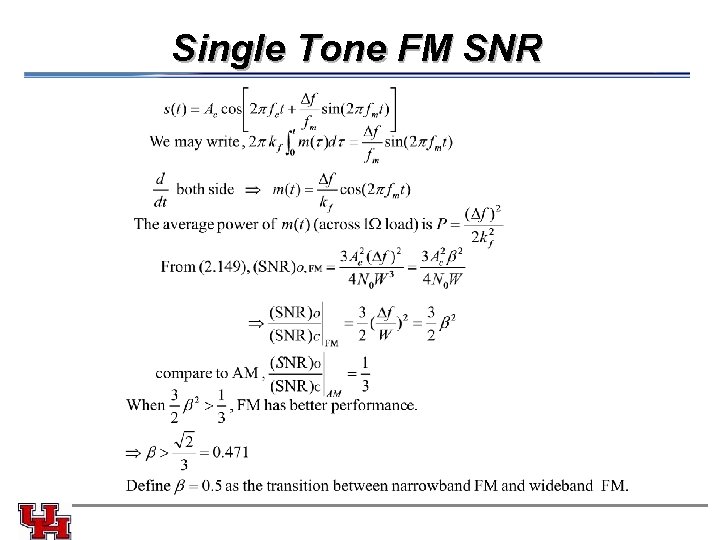
Single Tone FM SNR

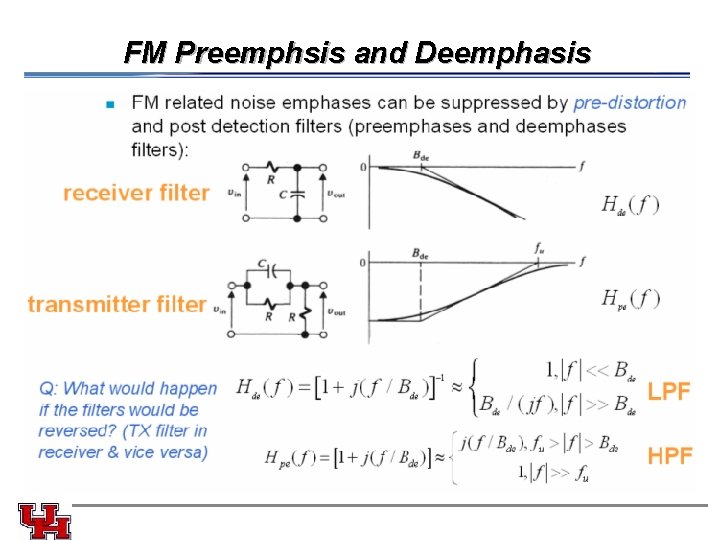
FM Preemphsis and Deemphasis

FM Preemphsis and Deemphasis

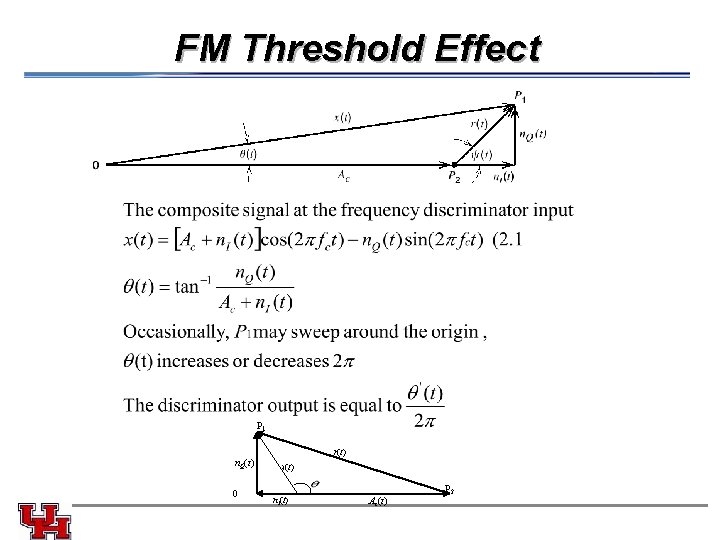
FM Threshold Effect P 1 r(t) n. Q(t) 0 x(t) n. I(t) Ac(t) P 2

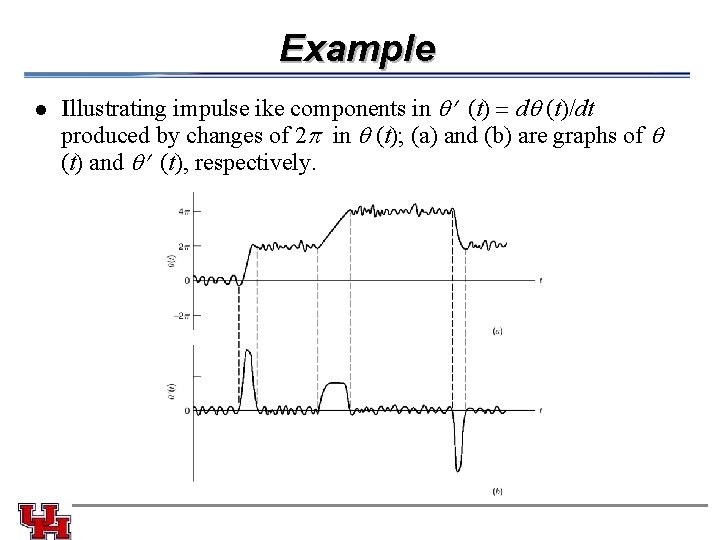
Example l Illustrating impulse ike components in (t) d (t)/dt produced by changes of 2 p in (t); (a) and (b) are graphs of (t) and (t), respectively.

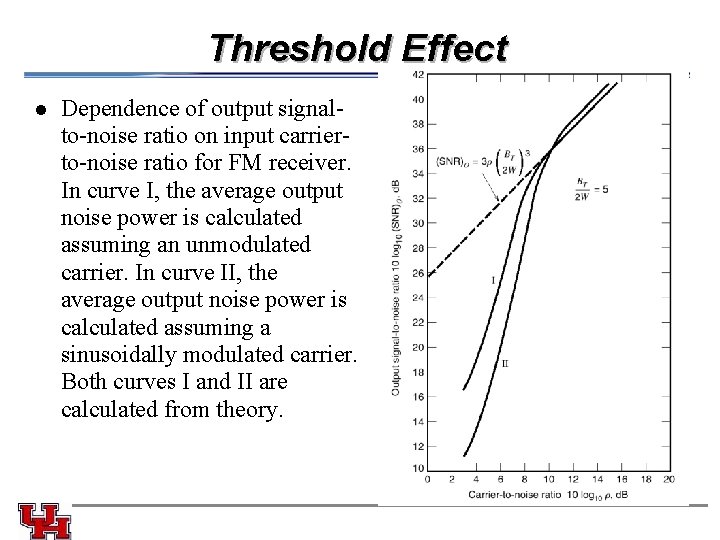
Threshold Effect l Dependence of output signalto-noise ratio on input carrierto-noise ratio for FM receiver. In curve I, the average output noise power is calculated assuming an unmodulated carrier. In curve II, the average output noise power is calculated assuming a sinusoidally modulated carrier. Both curves I and II are calculated from theory.

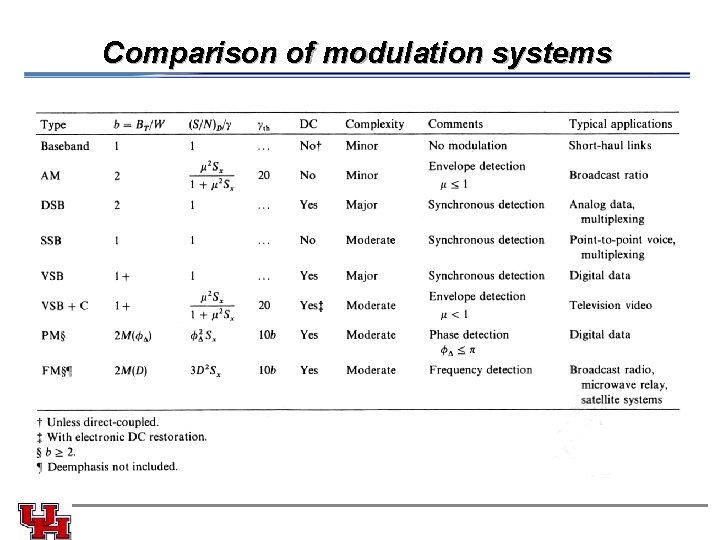
Comparison of modulation systems

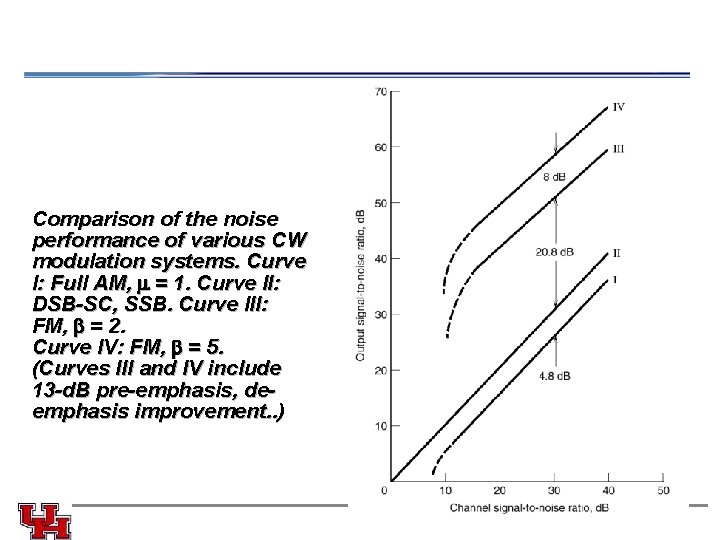
Comparison of the noise performance of various CW modulation systems. Curve I: Full AM, m = 1. Curve II: DSB-SC, SSB. Curve III: FM, b = 2. Curve IV: FM, b = 5. (Curves III and IV include 13 -d. B pre-emphasis, deemphasis improvement. . )

Encryption is a translation of data into a secret code. Encryption is the most effective way to achieve data security. To read an encrypted file, you must have access to a secret key that enables you to decrypt it. Unencrypted data is called plain text; encrypted data is referred to as cipher (text). l Encryption can be used to ensure secrecy, but other techniques are still needed to make communications secure: authentication, authorization, and message integrity. – Message integrity - both parties will always wish to be confident that a message has not been altered during transmission. The encryption makes it difficult for a third party to read a message, but that third party may still be able to alter it in a useful way. – Authentication is a way to ensure users are who they say they are that the user who attempts to perform functions in a system is in fact the user who is authorized to do so. – Authorization protects computer resources (data, files, programs, devices) by allowing those resources to be used by resource consumers having been granted authority to use them. – Digital rights management etc. l

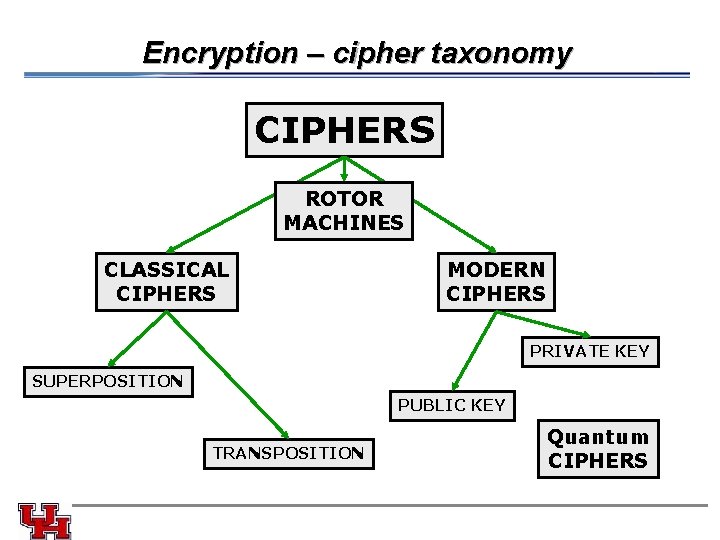
Encryption – cipher taxonomy CIPHERS ROTOR MACHINES CLASSICAL CIPHERS MODERN CIPHERS PRIVATE KEY SUPERPOSITION PUBLIC KEY TRANSPOSITION Quantum CIPHERS

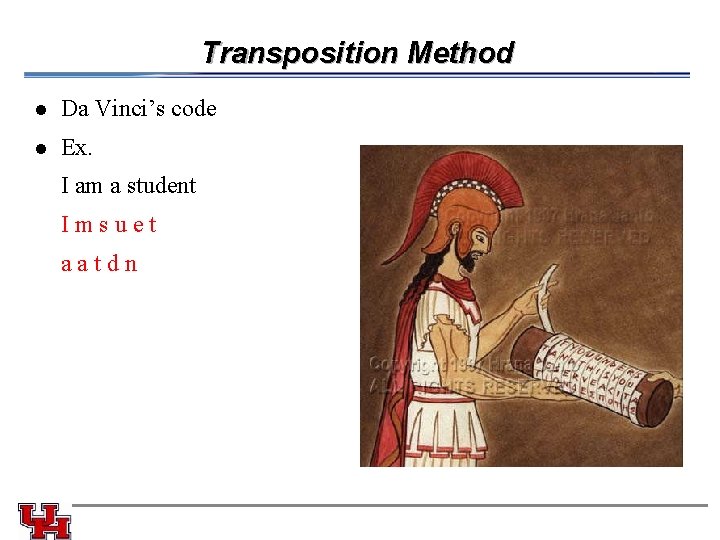
Transposition Method l Da Vinci’s code l Ex. I am a student Imsuet aatdn

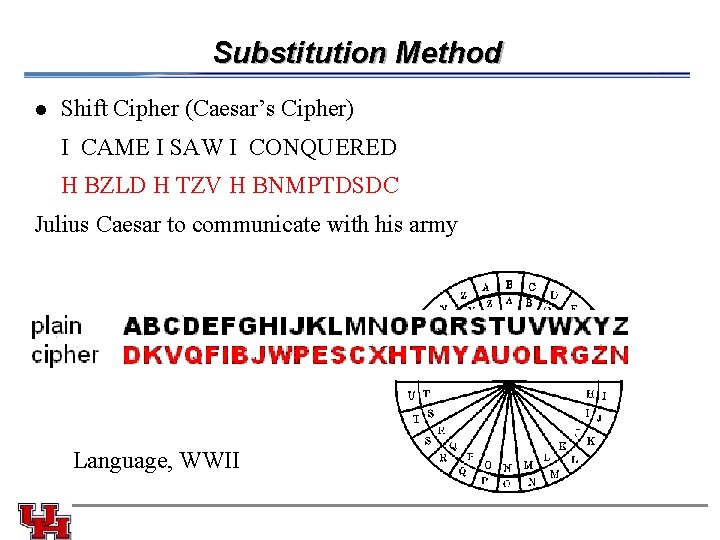
Substitution Method l Shift Cipher (Caesar’s Cipher) I CAME I SAW I CONQUERED H BZLD H TZV H BNMPTDSDC Julius Caesar to communicate with his army Language, WWII

Rotor Machine l The primary component is a set of rotors, also termed wheels or drums, which are rotating disks with an array of electrical contacts on either side. The wiring between the contacts implements a fixed substitution of letters, scrambling them in some complex fashion. On its own, this would offer little security; however, after encrypting each letter, the rotors advance positions, changing the substitution. By this means, a rotor machine produces a complex polyalphabetic substitution cipher. l German Enigma machine used during World War II for submarine. Movie U 571, Italian Job

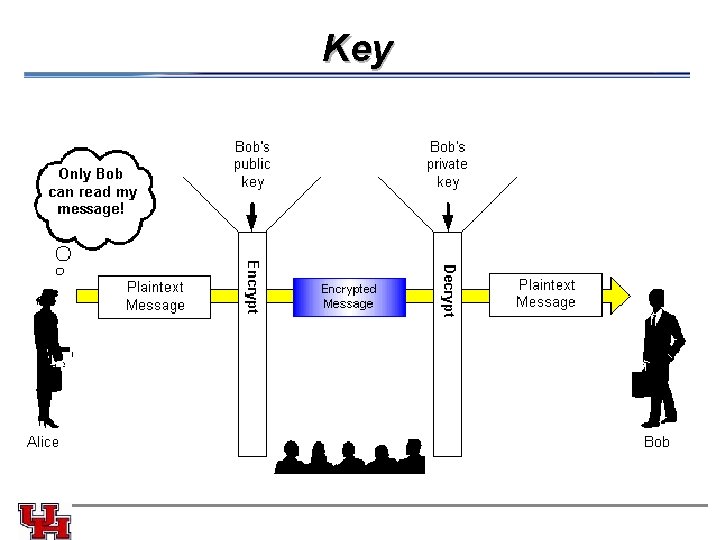
Key

Public Key System - RSA l Named after its inventors Ron Rivest, Adi Shamir and Len Adleman l Base on Number Theory y=ex (mod N) => x=? ? l If the size of N is 100, it takes 100 billion years to decipher with 1 GHz computer. l Applications – – l Digital Signatures Digital Cash: Movie, swordfish Timestamping Services: Movie, entrapment Election Snowden

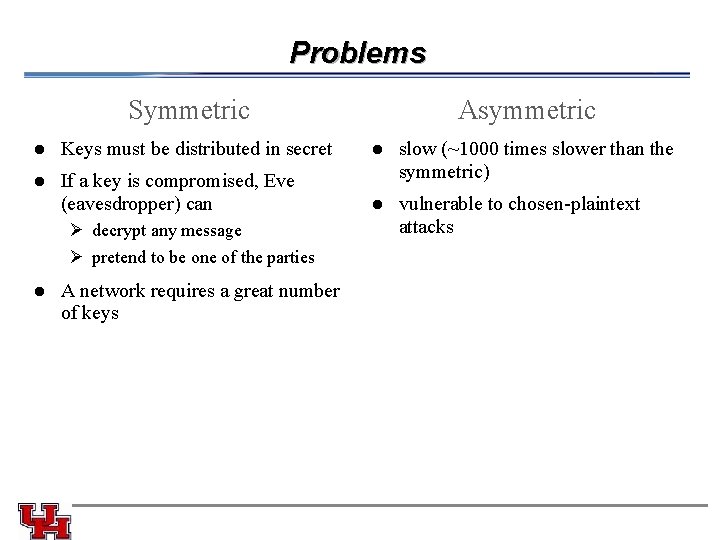
Two kinds of Cryptography Symmetric Asymmetric 1) Alice and Bob agree on a cryptosystem 1) Alice and Bob agree on a public -key cryptosystem 2) Alice and Bob agree on a key 2) Bob sends Alice his public key 3) Alice encrypts her message using Bob’s public key and sends it to Bob 4) Bob decrypts Alice’s message using his private key Alice takes her plaintext message and encrypts it using the encryption algorithm and the key. This creates a ciphertext message 3) 4) Alice sends the ciphertext message to Bob 5) Bob decrypts the ciphertext message with the same algorithm and key and reads it

Problems Symmetric Asymmetric l Keys must be distributed in secret l l If a key is compromised, Eve (eavesdropper) can slow (~1000 times slower than the symmetric) l vulnerable to chosen-plaintext attacks Ø decrypt any message Ø pretend to be one of the parties A network requires a great number of keys l

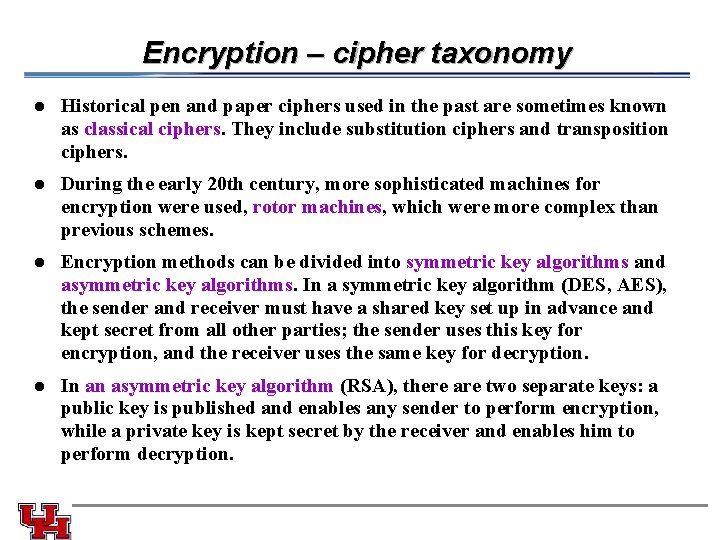
Encryption – cipher taxonomy l Historical pen and paper ciphers used in the past are sometimes known as classical ciphers. They include substitution ciphers and transposition ciphers. l During the early 20 th century, more sophisticated machines for encryption were used, rotor machines, which were more complex than previous schemes. Encryption methods can be divided into symmetric key algorithms and asymmetric key algorithms. In a symmetric key algorithm (DES, AES), the sender and receiver must have a shared key set up in advance and kept secret from all other parties; the sender uses this key for encryption, and the receiver uses the same key for decryption. l l In an asymmetric key algorithm (RSA), there are two separate keys: a public key is published and enables any sender to perform encryption, while a private key is kept secret by the receiver and enables him to perform decryption.

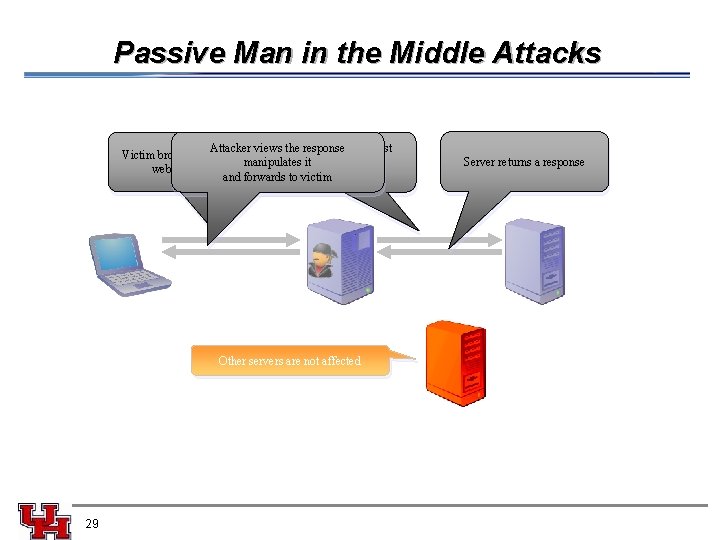
Passive Man in the Middle Attacks Attacker views Attacker the response views the request Victim browses to a manipulates it it website and forwards andtoforwards victim to server Other servers are not affected 29 Server returns a response

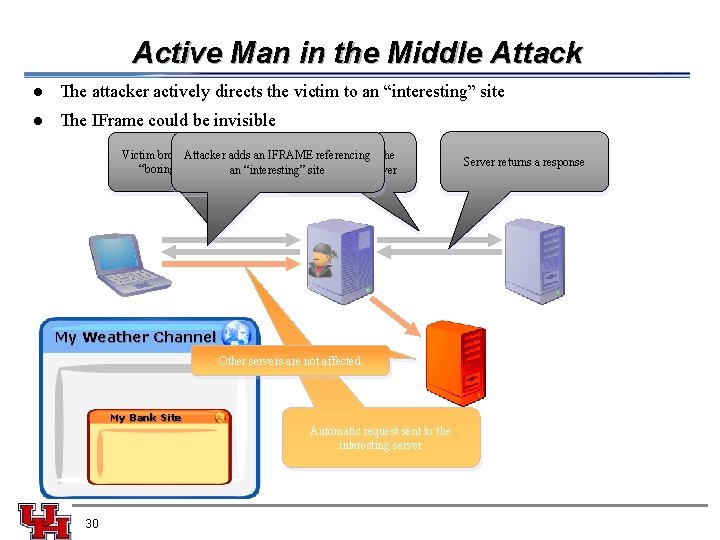
Active Man in the Middle Attack l The attacker actively directs the victim to an “interesting” site l The IFrame could be invisible Victim browses to a adds an IFRAME Attacker Attack referencing transfers the “boring” site an “interesting”request site to the server My Weather Channel Other servers are not affected My Bank Site Automatic request sent to the interesting server 30 Server returns a response

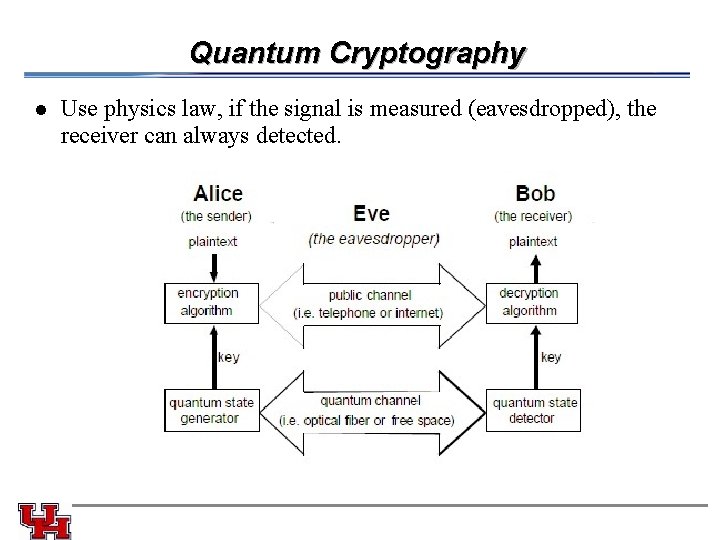
Quantum Cryptography l Use physics law, if the signal is measured (eavesdropped), the receiver can always detected.

Mission is really impossible When you see it, the information has been already changed

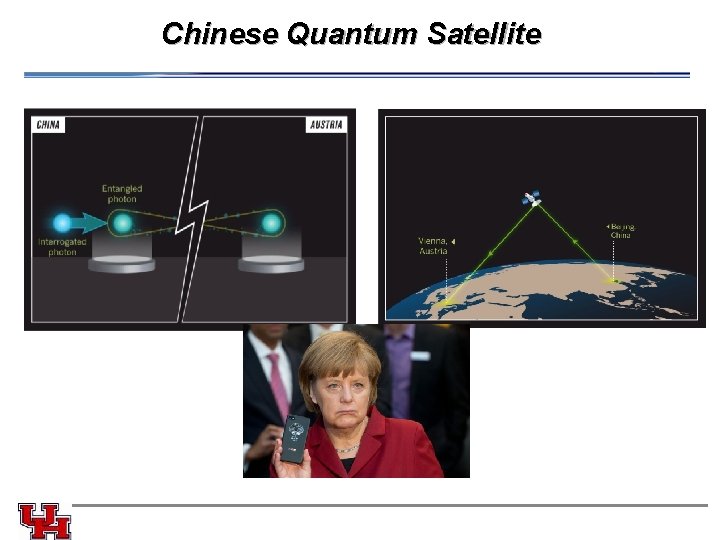
Chinese Quantum Satellite