Telecommunications Project Management Risk Management What is risk






























- Slides: 35

Telecommunications Project Management Risk Management

What is risk? ©“Event that disrupts the execution of a project and reduces its chances of meeting its objectives of quality, cost, or schedule. ” ©Characterized by: ©Root cause ©Probability of occurrence ©Financial consequence (EV & NPV)

Categories of Risk ©Strategic – competitive markets ©Operational – infrastructure upgrade ©Financial – cost benefit analysis ©Regulatory – government standards ©Technological – life cycle management ©Reputational – perceived value

Risk Management Steps 1. Identification of various root causes of risks 2. Risk evaluation to prioritize the treatment of various risks 3. Risk mitigation 4. Financing the residual risks

Risk Identification © Experience based ©Expert assessment of resources needed and consequences of the absence/malfunction of any of these resources ©Project manager or sector-wide benchmarking © Brainstorming-based ©Statistics on exposure to risk scarce ©Innovation is disruptive ©Wired and wireless telephone provide similar service but different risk

Risk Evaluation © Requires: ©Current and anticipated conditions ©Probability of conditions arising ©Likely consequences © Allows prioritization of risks © Can answer questions: ©How likely project completed on time? ©If late, how late? What contingency plans? ©When is the greatest vulnerability to risk?

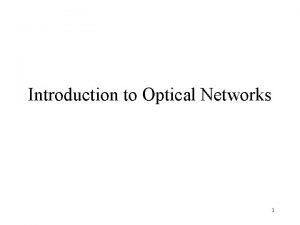
Risk Map ©Figure 10. 1

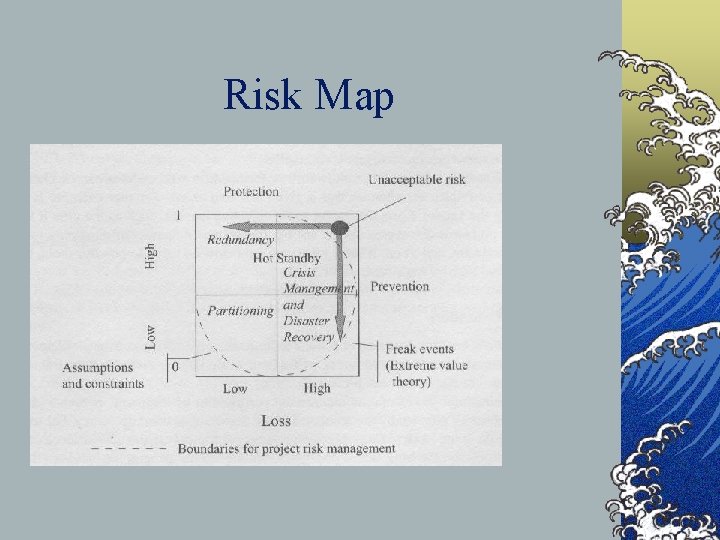
Risk Map ©Table 10. 1

Risk Mitigation © Risk Avoidance ©Prevention to reduce probability of occurrence ©Total avoidance changing project plan ©Probability of risk reduced by modifying scope or implementation © Risk Reduction ©Protection through corrective action to limit the consequences of the problem ©Partitioning of resources so that they are all not affected by the problem and provide redundancy ©UPS/Diesel Generator ©Contingency planning – High loss low probability

Risk Mitigation ©Risk Deflection ©Transfer risk to third party ©Insurance, outsourcing, warranty ©Risk Financing ©Cost/Schedule ©According to plan ©Some risk events occur ©Cost/Delay due to unpredictable events

Known © Known events © Known unknowns ©Identified risks ©Budget padded for contingency © Unknown unknowns ©Unexpected technical difficulties, labor shortages, economic downturns, natural causes, etc. ©Financed with management reserve – in addition to baseline budget and contingencies (not PM control) © http: //www. youtube. com/watch? v=QBb 1 k. Mn. P 8 ek

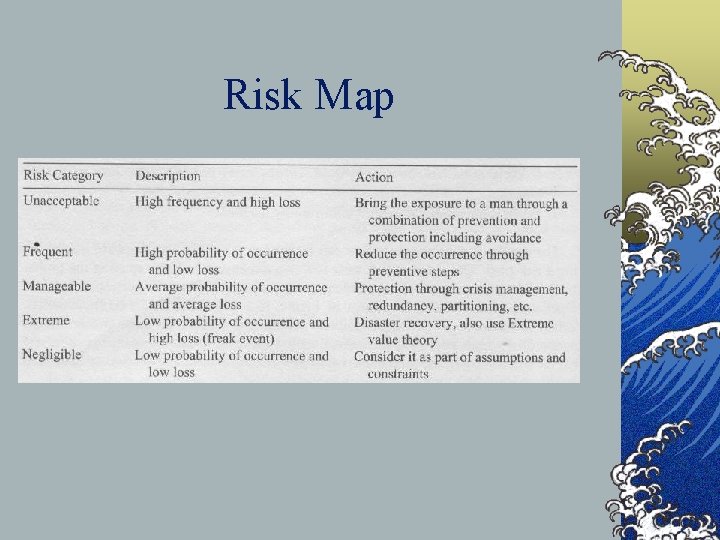
Known Figure ©Figure 10. 3

Telecom Sources of Risk ©Complexity ©Scope ©Requirements on cost, quality, schedule ©Number of interfaces (nonstandard) ©Concurrency of tasks ©Degree of interdependence with other projects

Telecom Sources of Risk © Schedule ©Long schedule ©Unexpected shortage of money ©Change of technology ©Shift in strategy from sponsor, supplier, or customer ©Change in regulations ©Short schedule ©Speed service delivery at expense of long-term quality ©Cause shortcuts with relation to safety, labor laws, or environment

Telecom Sources of Risk ©Novelty ©Type of innovation (incremental, platform, architectural, radical) ©Availability of functional and managerial skills ©Knowledge management

Telecom Sources of Risk © Geography ©New country or region may require additional testing ©Existing infrastructure not adequate ©Infrastructure projects susceptible to delays due to weather ©Holiday schedules different in countries ©Regulations ©Jurisdiction risk ©Geography of the area (900 MHz)

Telecom Sources of Risk © Internal Organization ©Lack of top management support or incompetence ©Lack of resources ©Uncontrolled changes to project scope ©Unresolved conflicts between project and functional organization ©Stakeholders hidden agenda (conflicting agendas) ©Lack of commitment ©Loss of personnel ©Recruitment difficulty, low morale, etc ©Lack of training of the workforce

Telecom Sources of Risk ©Technology ©Unreliable hardware or software ©Insufficient testing ©Lack of expertise with technology ©Lack of interface standards or incorrect standards ©Health risks (cell phones) ©Unknown risks

Telecom Sources of Risk © Supplier ©New vendor ©New connectivity agreement ©Supplier fails to deliver time/quality ©Security not guaranteed © Customer ©Financial viability ©Unreasonable expectations ©Hidden agendas/power struggles ©Level of end-user support (define requirements)

Telecom Risk Mitigation ©Table 10. 2

Innovation Risk ©Incremental Innovation ©Improve efficiency or expand scale ©Based on historical experience ©Familiarity ©AT&T 1994 ©Choose between IS-95, GSM, CDMA ©IS-95 maintain backward compatibility with AMPS © 2000 – Switch to GSM at huge cost ©Acquired by Cingular in 2003

Innovation Risk © Architectural Innovation ©Change in suppliers, markets, customers, etc ©Selling ring tones for wireless phones © New marketing techniques © Profiles of new customers © Unmanaged assumptions may hurt chances of success ©Unintended consequences ©Bluetooth © Wireless capability © Security risk ©Mitigate risk by identifying user needs through prototypes, request help

Innovation Risk © Platform Risk © Based on engineering estimates © Radical Innovation © Steep learning curve 1. 2. 3. 4. 5. 6. R&D needed before service ready? Engineering needed to design network? Certify network elements before deployable? Change to OSSs? Cost of maintaining operation? Training? Change to workflow and WPs? © Communications vital © Phase-gate approach

Expected Value (Quantitative Risk)

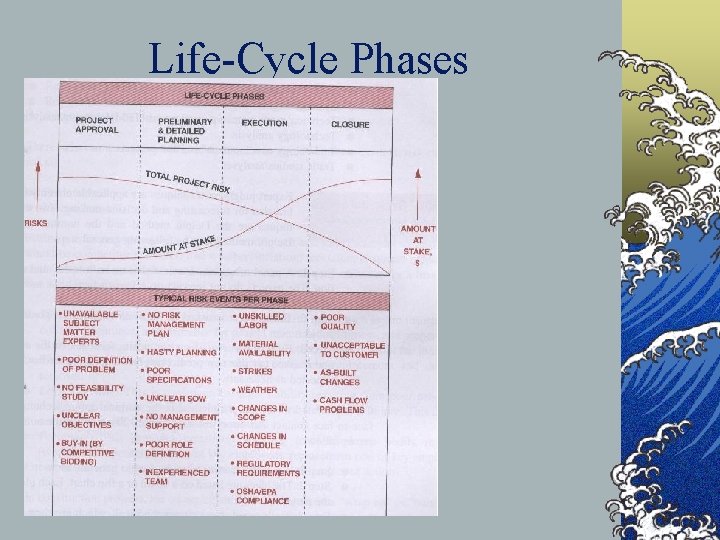
Life-Cycle Phases ©P. 723

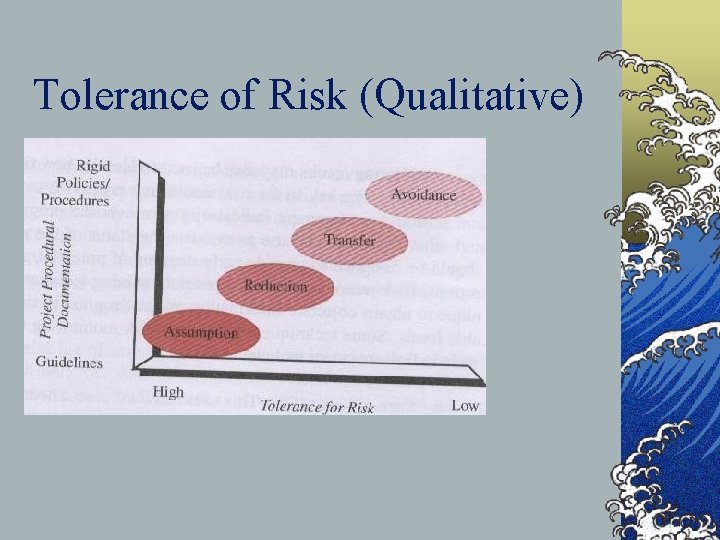
Tolerance of Risk (Qualitative) ©P. 747

©“Most of the things worth doing in the world had been declared impossible before they were done. ” Louis Brandeis

Review © “To minimize the possibility of confusion, good project managers resist defining strict boundaries around kinds of work they are willing or not willing to do. They avoid bright yellow lines between project management tasks and the project itself. Adherence to checklists implies that there is a definitive process that guarantees a particular outcome, which is never the case. In reality there always just three things: a goal, a pile of work, and a bunch of people. ”

©Manage the team, not the checklists. ©Stay engaged with the team. ©Mantra – “Make good stuff happen. ”

©It is only when the details are written down, with people’s names next to them, that real calculations can be made and assumptions examined. There is a psychological power in a schedule that externalizes and amplifies the commitment that is being made.

Snowball Effect Weak or no vision document X Poorly written or no specs X Poor or aggressive work estimates X No budget for integration X No budget for user interface iterations = Prayer of a schedule

©Design skills do not equal implementation skills. ©Business, technology, and customer perspective can not exist without each other. Success in project planning occurs at the intersection of these viewpoints.

5 Qualities of Good Visions ©Simple ©Intentional (goal-driven) ©Consolidated ©Inspirational ©Memorable


Requirements © Preparation minimizes work. © What do we do? © How do we do it? © Good requirements are easy to understand hard to misinterpret.
 Project management telecommunications
Project management telecommunications Tmn function block:
Tmn function block: Market risk credit risk operational risk
Market risk credit risk operational risk Importance of software project management
Importance of software project management A pioneer in the field of telecommunications
A pioneer in the field of telecommunications Advantages of star topology
Advantages of star topology Osha telecommunications standards
Osha telecommunications standards Sierra leone telecommunications company
Sierra leone telecommunications company Telecommunications act of 1996
Telecommunications act of 1996 Venture capital telecommunications
Venture capital telecommunications In a telecommunications network architecture, a protocol is
In a telecommunications network architecture, a protocol is Telecommunications infrastructure standard for data centers
Telecommunications infrastructure standard for data centers Electronics and telecommunications research institute
Electronics and telecommunications research institute Telecommunications, the internet, and wireless technology
Telecommunications, the internet, and wireless technology Telecommunication for dummies
Telecommunication for dummies Telecommunications, the internet, and wireless technology
Telecommunications, the internet, and wireless technology Disaster recovery telecommunications
Disaster recovery telecommunications Rfp for telecommunications services
Rfp for telecommunications services Government emergency telecommunications service
Government emergency telecommunications service Telecommunications engineering
Telecommunications engineering Telecommunications for dummies
Telecommunications for dummies Department of telecommunications
Department of telecommunications Department of telecommunications
Department of telecommunications French telecommunications equipment company
French telecommunications equipment company Digital telecommunications
Digital telecommunications Iu telecommunications
Iu telecommunications European telecommunications standards institute
European telecommunications standards institute Ee3801
Ee3801 Pts
Pts Networks and telecommunications presentation
Networks and telecommunications presentation International telecommunications society
International telecommunications society Wireless telecommunications industry analysis
Wireless telecommunications industry analysis Gts telecommunications
Gts telecommunications Fiduciary investment risk management association
Fiduciary investment risk management association Risk map risk management
Risk map risk management What is risk in software project management
What is risk in software project management