Design Principles Overview Principles Least Privilege FailSafe Defaults




















- Slides: 32

Design Principles Overview Principles Least Privilege Fail-Safe Defaults Economy of Mechanism Complete Mediation Open Design Separation of Privilege Least Common Mechanism Psychological Acceptability

Two Basic Rules Keep It as Simple as po. Ssible (KISS) Restriction

As Simple As Possible Less to go wrong Fewer possible inconsistencies Easy to understand https: //quotefancy. com/media/wallpaper/3840 x 2160/33770 -Albert-Einstein-Quote-Make-everything-as-simple-as-possible-but. jpg

Restriction Minimize access Inhibit communication http: //teamsofdistinction. com/wpcontent/uploads/2015/01/Manager. Keep-their-mouth-shut-1024 x 680. jpeg

Least Privilege A subject should be given only those privileges necessary to complete its task Function, not identity, controls Rights added as needed, discarded after use

Why Least Privilege It’s harder to accidentally compromise what you don’t have access to. Accidental deletions or manipulation is less likely. If you only have access to what you need, anyone that compromises your account will only have access to limited resources. http: //cumbriansystems. co. uk/accesscontrol_cumbria/accesscontrol 7 cumbria. html

Fail-Safe Defaults Unless a subject is given explicit access to an object, it should be denied access to that object; Default action is to deny access; uvalibraryfeb. wordpress. com

Fail-Safe Defaults (cont. ) If action fails, system as secure as when action began; A system's being "fail-safe" means not that failure is impossible or improbable, but rather that the system's design prevents or mitigates unsafe consequences of the system's failure. That is, if and when a "fail-safe" system "fails", it is "safe" or at least no less safe than when it was operating correctly. (Wikipedia. org)

Fail-Safe Defaults (cont. ) www. extremetech. com/extreme/136894 -wi

Fail-Safe Defaults (cont. ) https: //cs. copart. com/v 1/AUTH_svc. pdoc 00001/PIX 87/7 a 7 acef 5 -287 c-48 de-8819 -8 e 6746 e 41254. JPG

Economy of Mechanism Keep it as simple as possible KISS Principle Simpler means less can go wrong And when errors occur, they are easier to understand fix Interfaces and interactions

Economy of Mechanism E = M *C*C

Complete Mediation Check every access to objects to ensure that they are allowed; If the subject needs to access the object again, then check again; https: //www. usenix. org/legacy/publications/library/proceedings/sec 02/full_papers/zhang_html/problem. gif

Complete Mediation

Complete Mediation When a UNIX process tries to read a file, the operating system determines if the process is allowed to read the file. If so, the process receives a file descriptor encoding the allowed access. Whenever the process wants to read the file, it presents the file descriptor to the kernel. The kernel then allows the access. If the owner of the file disallows the process permission to read the file after the file descriptor is issued, the kernel still allows access. https: //www. us-cert. gov/bsi/articles/knowledge/principles/complete-mediation

Complete Mediation The Directory Name Service (DNS) caches information mapping hostnames into IP addresses. If an attacker is able to "poison" the cache by implanting records associating a bogus IP address with a name, the host will route connections to that host incorrectly. https: //www. us-cert. gov/bsi/articles/knowledge/principles/complete-mediation

Open Design Security should not depend on secrecy of design or implementation Popularly misunderstood to mean that source code should be public “Security through obscurity” Does not apply to information such as passwords or cryptographic keys

Open Design Cryptography algorithms: why do we rely its security on passwords but not algorithm design? Design an algorithm takes years, but generating keys only take seconds; Most loopholes can be identified only through public reviews;

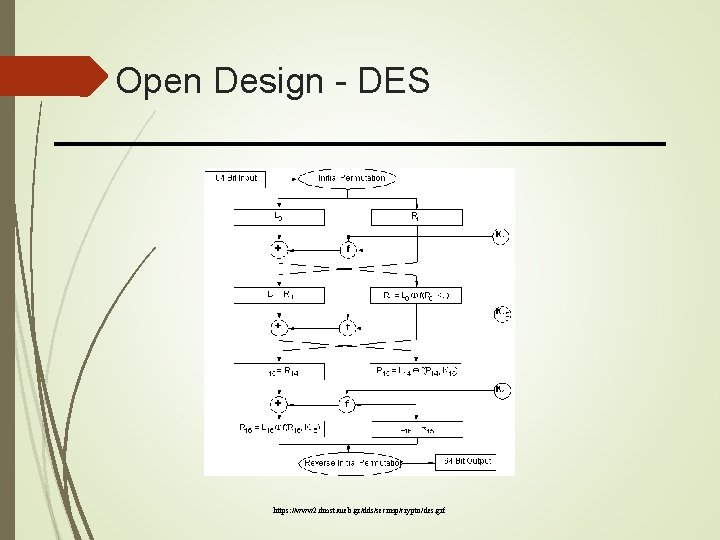
Open Design - DES https: //www 2. dmst. aueb. gr/dds/secimp/crypto/des. gif

Separation of Privilege Require multiple conditions to grant privilege Separation of duty Defense in depth

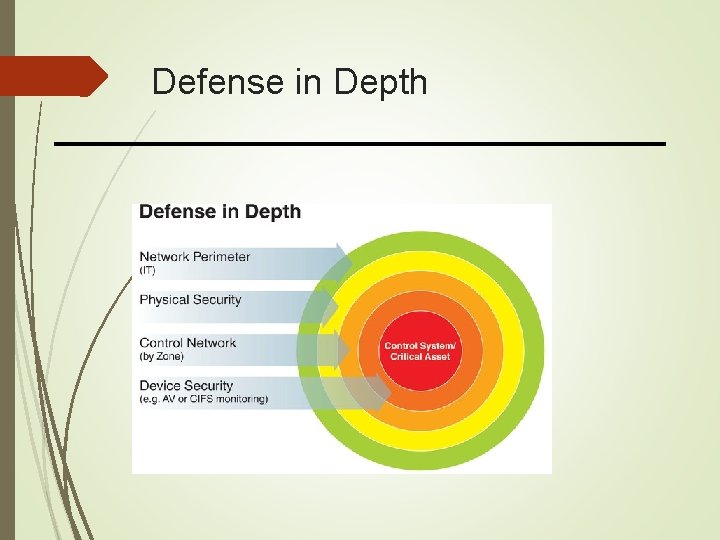
Defense in Depth

Defense in Depth http: //www. huaxia. com/zt/zhwh/05 -082/images/ldy 131508501. jpg

Defense in Depth

Separation of Privilege www. rdsons. com/prods/main_prods/water_dispenser/mini-magic-plus-r-voltas-water-dispe

Separation of Privilege doolancallaghan. com. au

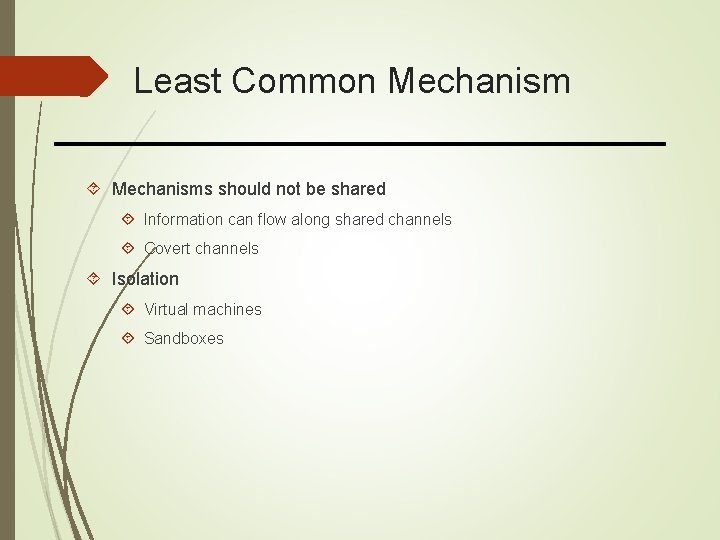
Least Common Mechanisms should not be shared Information can flow along shared channels Covert channels Isolation Virtual machines Sandboxes

Least Common Mechanism

Least Common Mechanism

Psychological Acceptability Security mechanisms should not add to difficulty of accessing resource Hide complexity introduced by security mechanisms Ease of installation, configuration, use Human factors critical here

Psychological Acceptability

Psychological Acceptability

Psychological Acceptability https: //4 brf 13430 svm 3 bnu 053 zbxvg-wpengine. netdna-ssl. com/wp-content/uploads/2016/05/Global-Entry. Program. jpg