Department of Information Engineering University of Padova ITALY





- Slides: 25

Department of Information Engineering University of Padova, ITALY Performance Analysis of Limited– 1 Polling in a Bluetooth Piconet A note on the use of these ppt slides: We’re making these slides freely available to all, hoping they might be of use for researchers and/or students. They’re in Power. Point form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. In return for use, we only ask the following: If you use these slides (e. g. , in a class, presentations, talks and so on) in substantially unaltered form, that you mention their source. If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and put a link to the authors webpage: www. dei. unipd. it/~zanella Thanks and enjoy! CITSA 05, Orlando (Florida), 14 -17 July, 2005

Department of Information Engineering University of Padova, ITALY Special Interest Group on NEtworking & Telecommunications Performance Analysis of Limited– 1 Polling in a Bluetooth Piconet Daniele Miorandi, Andrea Zanella {daniele. miorandi, andrea. zanella}@dei. unipd. it CITSA’ 05, Orlando, 14 -17 July 2005 CITSA 05, Orlando (Florida), 14 -17 July, 2005

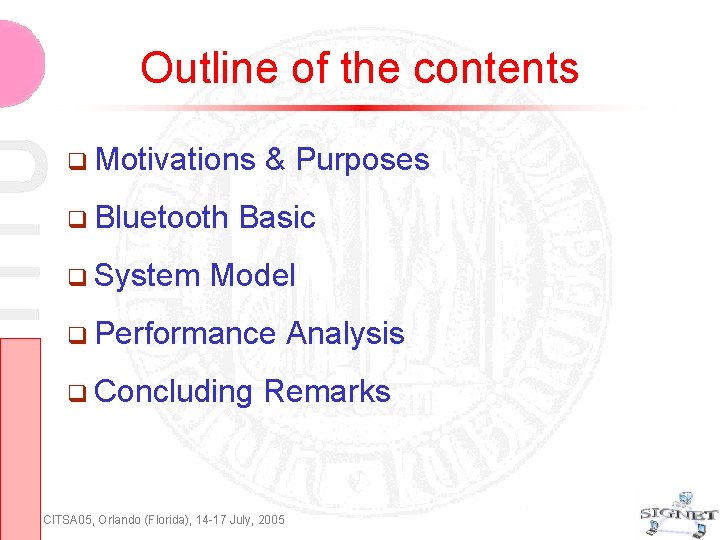
Outline of the contents Motivations Bluetooth System & Purposes Basic Model Performance Concluding Analysis Remarks CITSA 05, Orlando (Florida), 14 -17 July, 2005

What and Why… Motivations & Purposes CITSA 05, Orlando (Florida), 14 -17 July, 2005

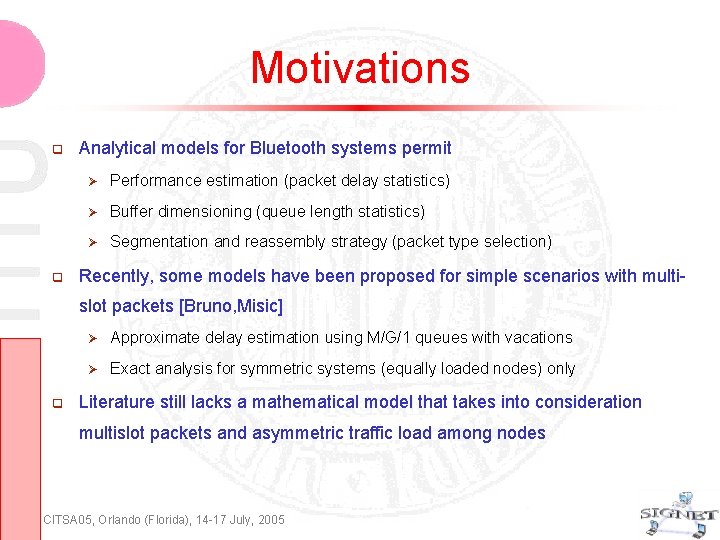
Motivations Analytical models for Bluetooth systems permit Performance estimation (packet delay statistics) Buffer dimensioning (queue length statistics) Segmentation and reassembly strategy (packet type selection) Recently, some models have been proposed for simple scenarios with multislot packets [Bruno, Misic] Approximate delay estimation using M/G/1 queues with vacations Exact analysis for symmetric systems (equally loaded nodes) only Literature still lacks a mathematical model that takes into consideration multislot packets and asymmetric traffic load among nodes CITSA 05, Orlando (Florida), 14 -17 July, 2005

Aim of the study Providing an approximate performance analysis in case of Use of multi-slot packets Asymmetric and unbalanced traffic matrix CITSA 05, Orlando (Florida), 14 -17 July, 2005

What the standard says… Bluetooth basic CITSA 05, Orlando (Florida), 14 -17 July, 2005

Bluetooth piconet Two up to eight Bluetooth units sharing the same channel form a piconet In each piconet, a unit acts as master, the others act as slaves Channel access is based on a centralized polling scheme Full-duplex is supported by Time-divisionduplex (TDD), with time slots of T=0. 625 ms CITSA 05, Orlando (Florida), 14 -17 July, 2005

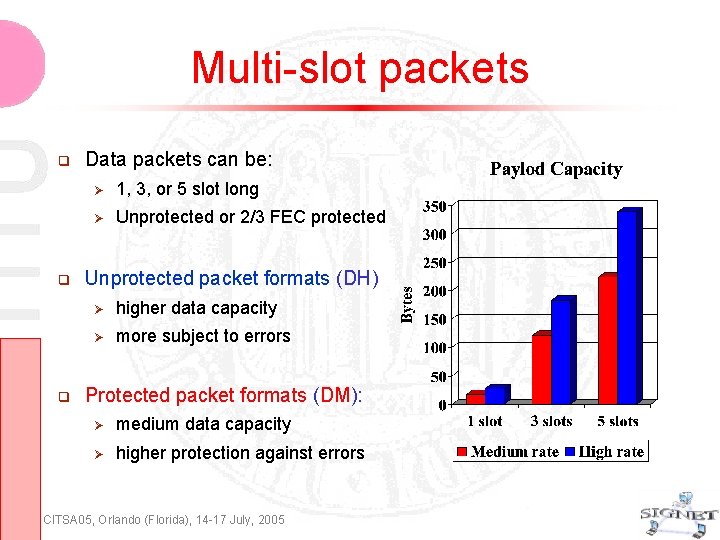
Multi-slot packets Data packets can be: 1, 3, or 5 slot long Unprotected or 2/3 FEC protected Unprotected packet formats (DH) higher data capacity more subject to errors Protected packet formats (DM): medium data capacity higher protection against errors CITSA 05, Orlando (Florida), 14 -17 July, 2005

Mathematical Model System Model for Ideal Channels CITSA 05, Orlando (Florida), 14 -17 July, 2005

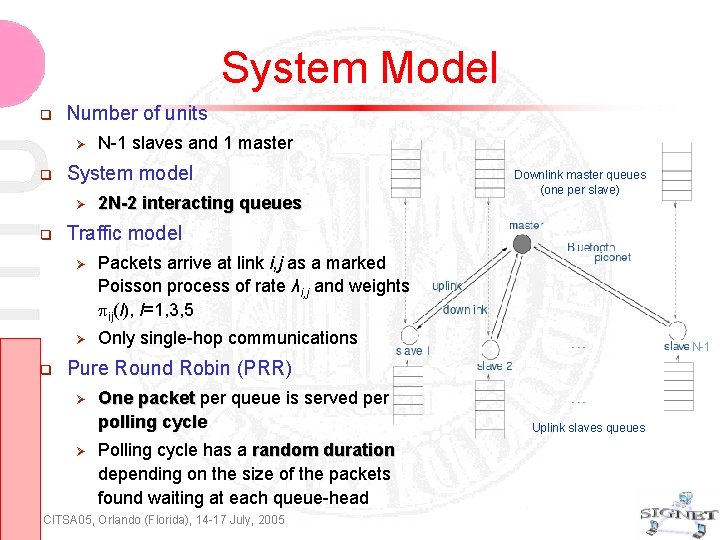
System Model Number of units System model N-1 slaves and 1 master 2 N-2 interacting queues Downlink master queues (one per slave) Traffic model Packets arrive at link i, j as a marked Poisson process of rate λi, j and weights ij(l), l=1, 3, 5 Only single-hop communications N-1 Pure Round Robin (PRR) One packet per queue is served per polling cycle Polling cycle has a random duration depending on the size of the packets found waiting at each queue-head CITSA 05, Orlando (Florida), 14 -17 July, 2005 Uplink slaves queues

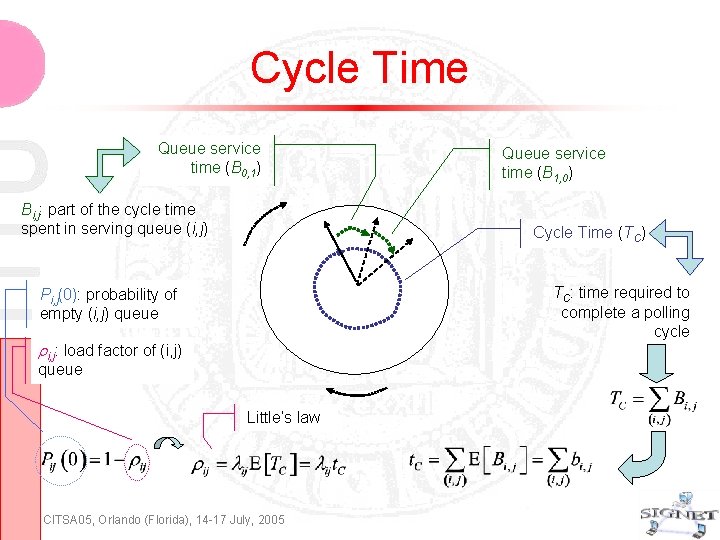
Cycle Time Queue service time (B 0, 1) Bi, j: part of the cycle time spent in serving queue (i, j) Queue service time (B 1, 0) Cycle Time (TC) TC: time required to complete a polling cycle Pi, j(0): probability of empty (i, j) queue i, j: load factor of (i, j) queue Little’s law CITSA 05, Orlando (Florida), 14 -17 July, 2005

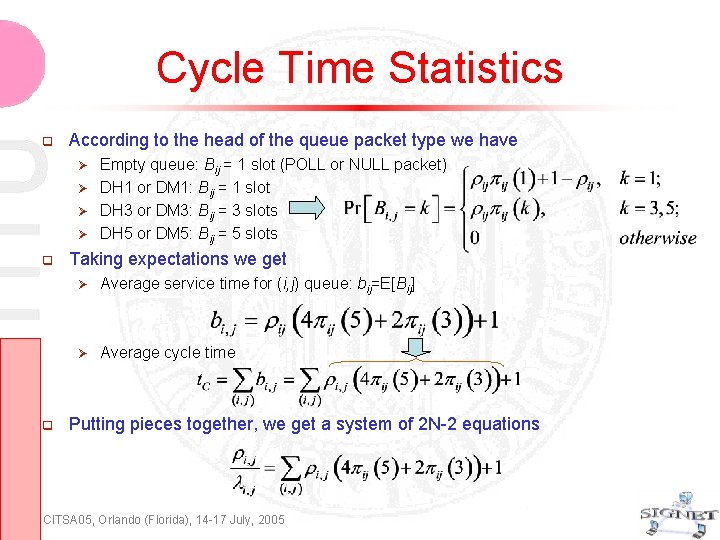
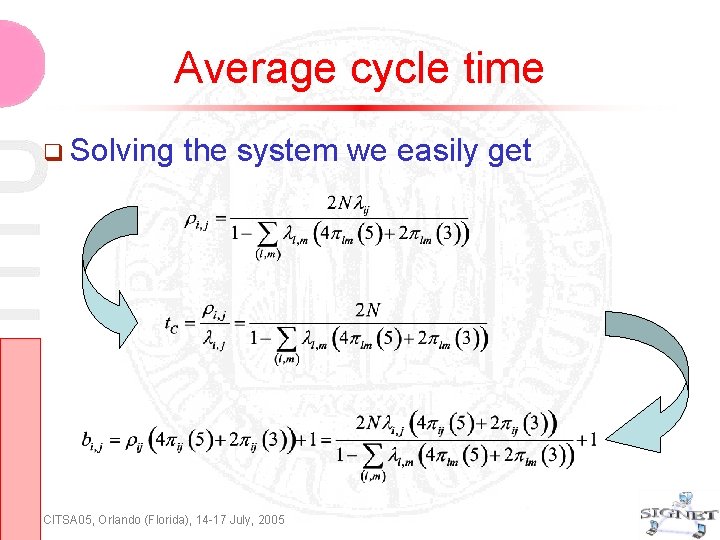
Cycle Time Statistics According to the head of the queue packet type we have Empty queue: Bij = 1 slot (POLL or NULL packet) DH 1 or DM 1: Bij = 1 slot DH 3 or DM 3: Bij = 3 slots DH 5 or DM 5: Bij = 5 slots Taking expectations we get Average service time for (i, j) queue: bij=E[Bij] Average cycle time Putting pieces together, we get a system of 2 N-2 equations CITSA 05, Orlando (Florida), 14 -17 July, 2005

Average cycle time Solving the system we easily get CITSA 05, Orlando (Florida), 14 -17 July, 2005

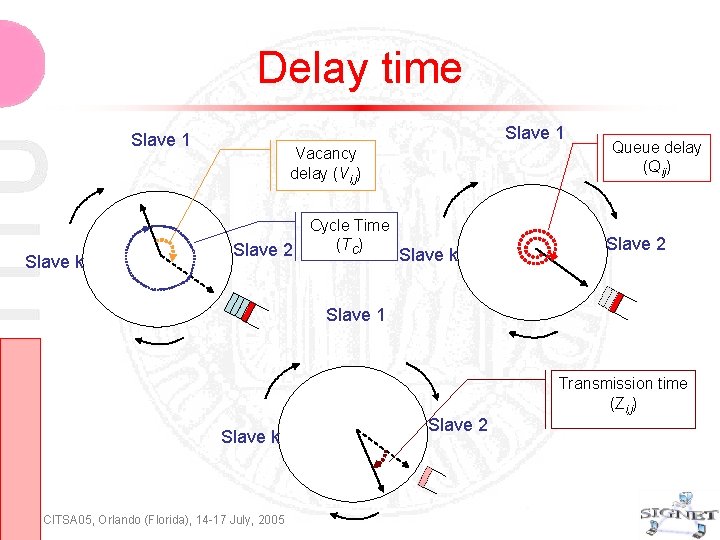
Delay time Slave 1 Slave k Vacancy delay (Vi, j) Slave 2 Cycle Time (TC) Slave k Queue delay (Qij) Slave 2 Slave 1 Transmission time (Zi, j) Slave k CITSA 05, Orlando (Florida), 14 -17 July, 2005 Slave 2

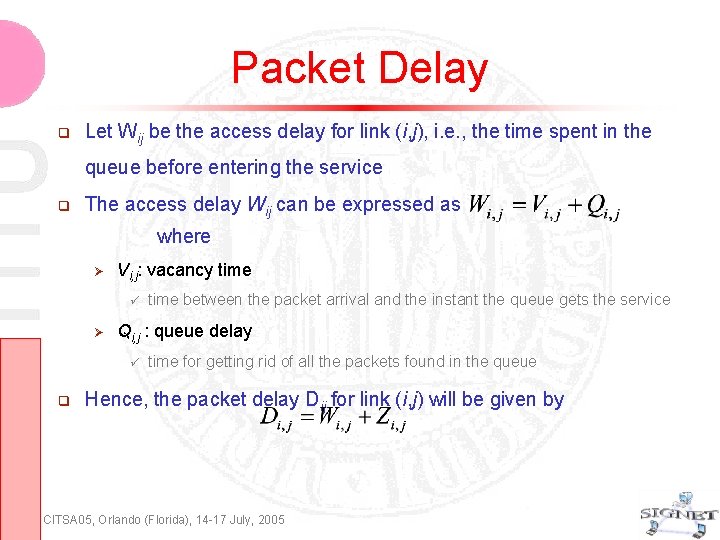
Packet Delay Let Wij be the access delay for link (i, j), i. e. , the time spent in the queue before entering the service The access delay Wij can be expressed as where Vi, j: vacancy time Qi, j : queue delay time between the packet arrival and the instant the queue gets the service time for getting rid of all the packets found in the queue Hence, the packet delay Dij for link (i, j) will be given by CITSA 05, Orlando (Florida), 14 -17 July, 2005

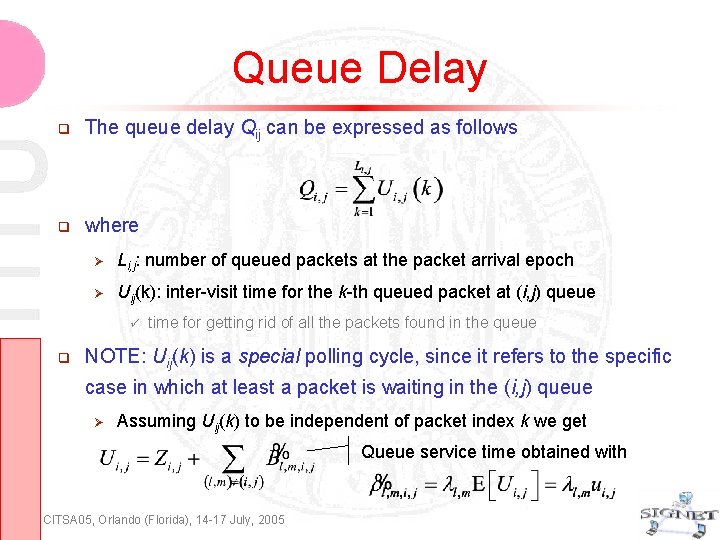
Queue Delay The queue delay Qij can be expressed as follows where Li, j: number of queued packets at the packet arrival epoch Uij(k): inter-visit time for the k-th queued packet at (i, j) queue time for getting rid of all the packets found in the queue NOTE: Uij(k) is a special polling cycle, since it refers to the specific case in which at least a packet is waiting in the (i, j) queue Assuming Uij(k) to be independent of packet index k we get Queue service time obtained with CITSA 05, Orlando (Florida), 14 -17 July, 2005

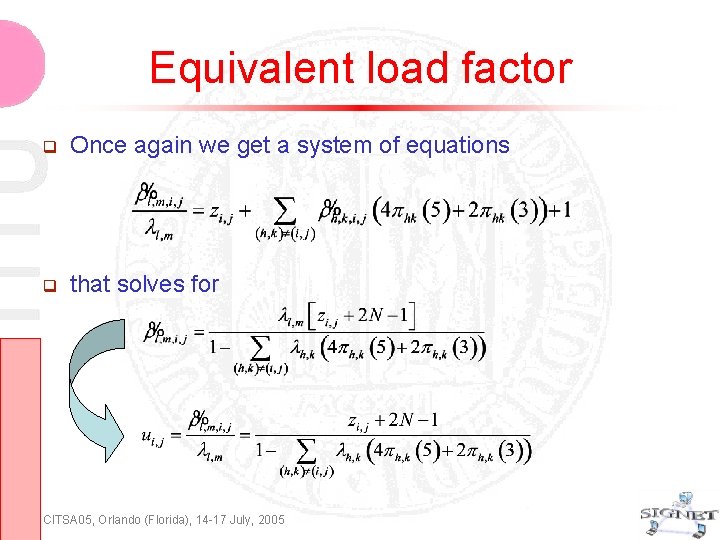
Equivalent load factor Once again we get a system of equations that solves for CITSA 05, Orlando (Florida), 14 -17 July, 2005

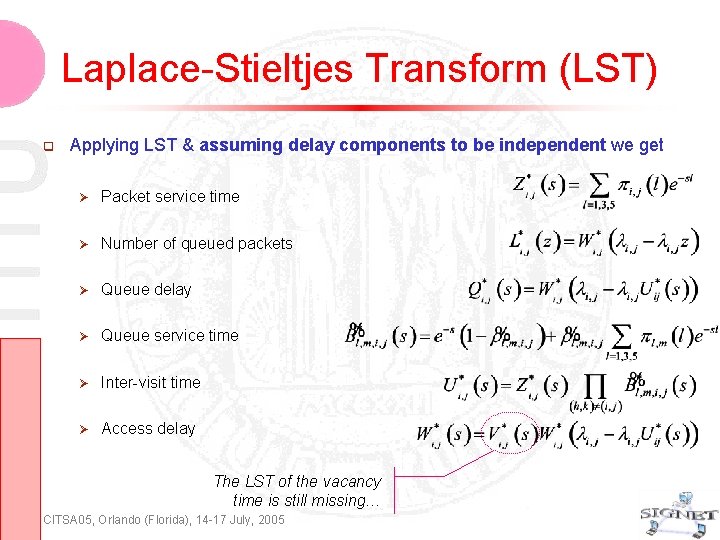
Laplace-Stieltjes Transform (LST) Applying LST & assuming delay components to be independent we get Packet service time Number of queued packets Queue delay Queue service time Inter-visit time Access delay The LST of the vacancy time is still missing… CITSA 05, Orlando (Florida), 14 -17 July, 2005

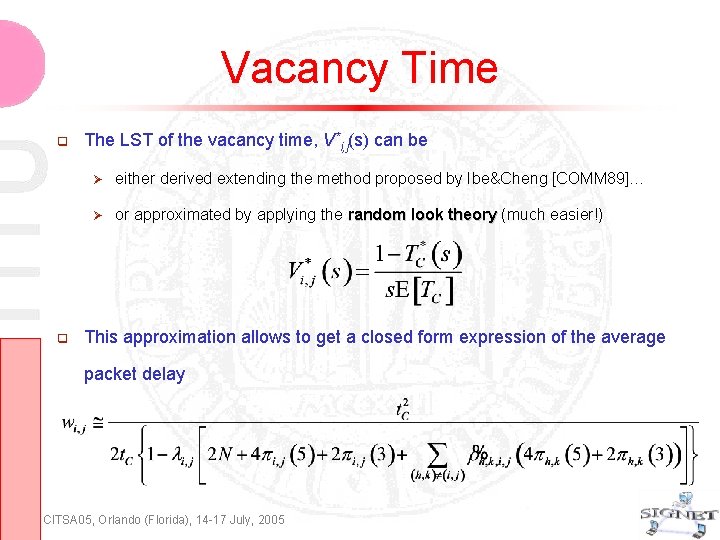
Vacancy Time The LST of the vacancy time, V*i, j(s) can be either derived extending the method proposed by Ibe&Cheng [COMM 89]… or approximated by applying the random look theory (much easier!) This approximation allows to get a closed form expression of the average packet delay CITSA 05, Orlando (Florida), 14 -17 July, 2005

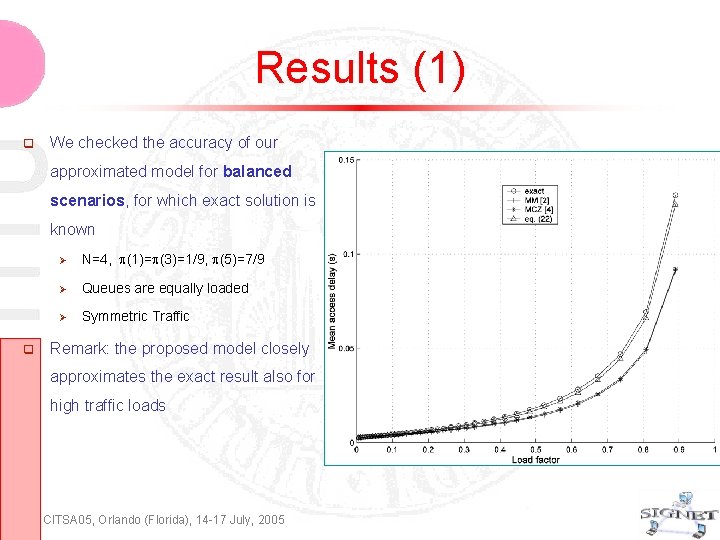
Results (1) We checked the accuracy of our approximated model for balanced scenarios, for which exact solution is known N=4, (1)= (3)=1/9, (5)=7/9 Queues are equally loaded Symmetric Traffic Remark: the proposed model closely approximates the exact result also for high traffic loads CITSA 05, Orlando (Florida), 14 -17 July, 2005

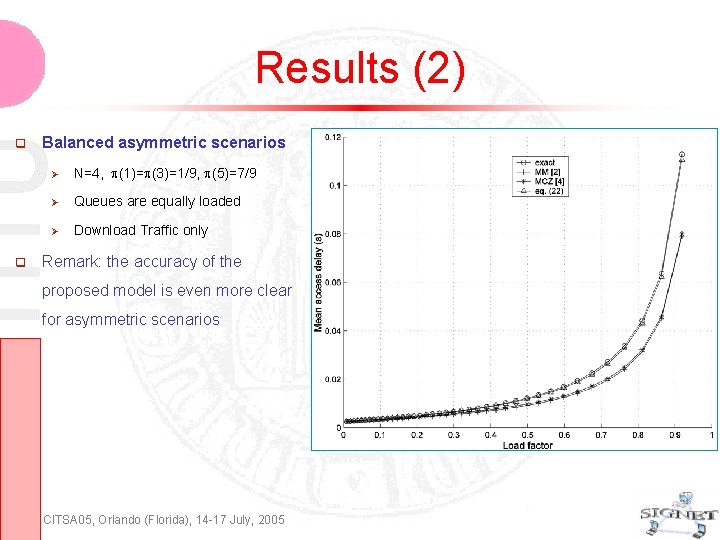
Results (2) Balanced asymmetric scenarios N=4, (1)= (3)=1/9, (5)=7/9 Queues are equally loaded Download Traffic only Remark: the accuracy of the proposed model is even more clear for asymmetric scenarios CITSA 05, Orlando (Florida), 14 -17 July, 2005

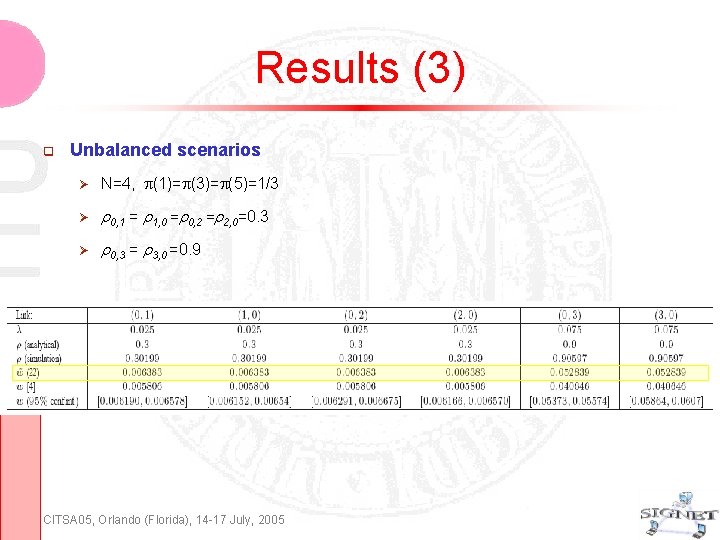
Results (3) Unbalanced scenarios N=4, (1)= (3)= (5)=1/3 0, 1 = 1, 0 = 0, 2 = 2, 0=0. 3 0, 3 = 3, 0 =0. 9 CITSA 05, Orlando (Florida), 14 -17 July, 2005

Conclusions & Future work Summary Simple mathematical model for ideal Bluetooth links with unbalanced load has been presented Average packet delay estimations given by the model closely approximates the exact results in balanced scenario, largely improving the models previously presented in the literature The model seems to offer rather good performance estimation also in unbalanced scenarios CITSA 05, Orlando (Florida), 14 -17 July, 2005 Next steps Model can be extended to error-prone links A fading channel model might be considered Remark: this might exacerbate the interdependency among the queues, making the model less accurate

That’s all! Thanks for your attention! CITSA 05, Orlando (Florida), 14 -17 July, 2005
 Department of information engineering university of padova
Department of information engineering university of padova Department of information engineering university of padova
Department of information engineering university of padova Narrativistic
Narrativistic Information engineering padova
Information engineering padova University of sargodha engineering department
University of sargodha engineering department University of salerno province
University of salerno province Pegaso telematic university
Pegaso telematic university Brescia university italy
Brescia university italy Istituto comprensivo donatello roma
Istituto comprensivo donatello roma Organigramma comune di padova
Organigramma comune di padova Scuola forense padova
Scuola forense padova Via pettinati 46 padova
Via pettinati 46 padova Struttura del vangelo di luca
Struttura del vangelo di luca Scuola pascoli padova
Scuola pascoli padova Iniziazione cristiana padova
Iniziazione cristiana padova Servizi scolastici padova
Servizi scolastici padova Clinica neurologica padova
Clinica neurologica padova Dai ragazzi padova
Dai ragazzi padova Dai ragazzi padova
Dai ragazzi padova Clinica ginecologica padova
Clinica ginecologica padova Scienze psicologiche cognitive e psicobiologiche sbocchi
Scienze psicologiche cognitive e psicobiologiche sbocchi Infn padova
Infn padova Amici dei popoli padova
Amici dei popoli padova Psicologia del lavoro padova
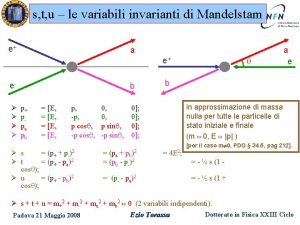
Psicologia del lavoro padova Invarianti di mandelstam
Invarianti di mandelstam Zanardo pediatra padova
Zanardo pediatra padova