CS 501 Software Engineering Fall 2000 Lecture 15


















- Slides: 30

CS 501: Software Engineering Fall 2000 Lecture 15 System Architecture II Distributed and Real Time Systems

Administration Assignment 2: Requirements • • • Grades -- presentation, report, individual Comments at presentation Comments from teaching assistant Assignment 3: Design

Comments on Requirements Report Audience • • Client and design team Will be updated over time Content • • • Level of detail -- will be used to validate the implementation Requirements, not design Precise, but not legalistic

Sequence Diagram: Notation lib. Mem: Library. Member Book. Borrower the. Book: Book the. Copy: Copy borrow(the. Copy) ok. To. Borrow borrow dotted line shows object lifetime rectangle shows focus of control

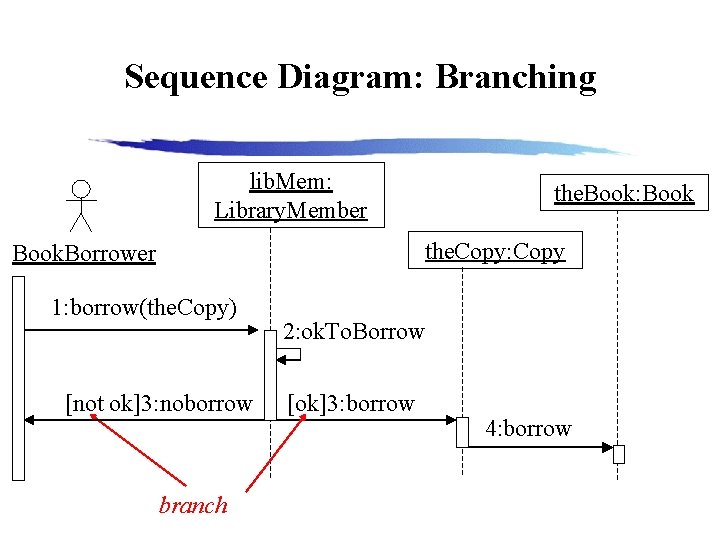
Sequence Diagram: Branching lib. Mem: Library. Member the. Book: Book the. Copy: Copy Book. Borrower 1: borrow(the. Copy) [not ok]3: noborrow branch 2: ok. To. Borrow [ok]3: borrow 4: borrow

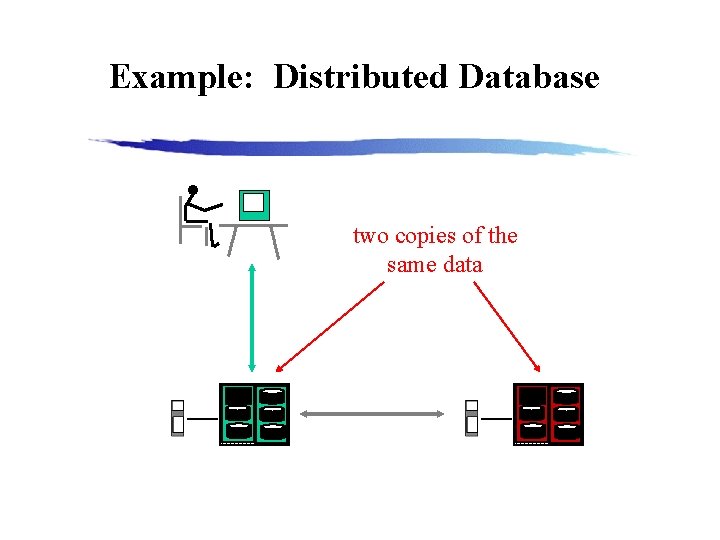
Example: Distributed Database two copies of the same data

Distributed Data and Replication Distributed Data is held on several computer systems. A transaction may need to assemble data from several sources. Replication Several copies of the data are held in different locations. Mirror: Complete data set is replicated Cache: Dynamic set of data is replicated (e. g. , most recently used) With replicated data, the biggest problem is consistency.

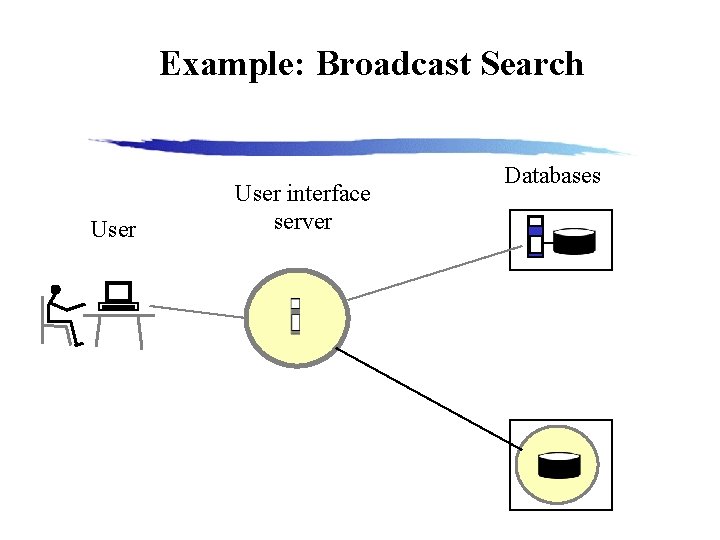
Example: Broadcast Search User interface server Databases

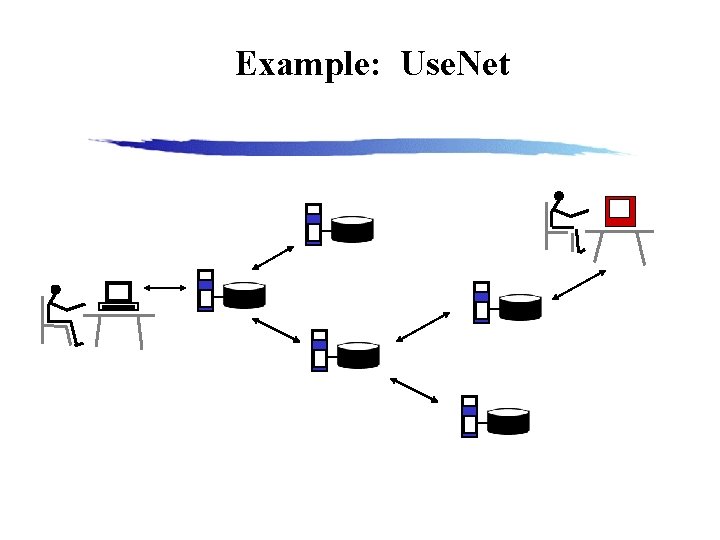
Example: Use. Net

Stateless Protocol v. Stateful Stateless protocol Example: http Open connection Send message Return reply Close connection State in http must be sent with every message (e. g. , as parameter string or in a cookie)

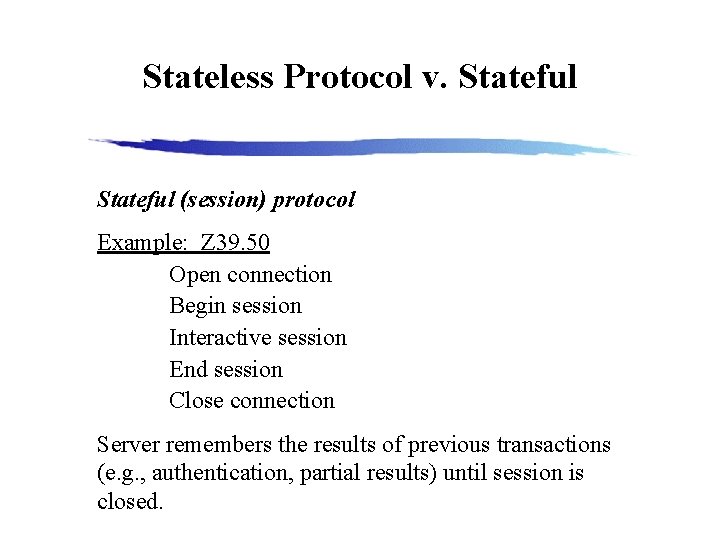
Stateless Protocol v. Stateful (session) protocol Example: Z 39. 50 Open connection Begin session Interactive session End session Close connection Server remembers the results of previous transactions (e. g. , authentication, partial results) until session is closed.

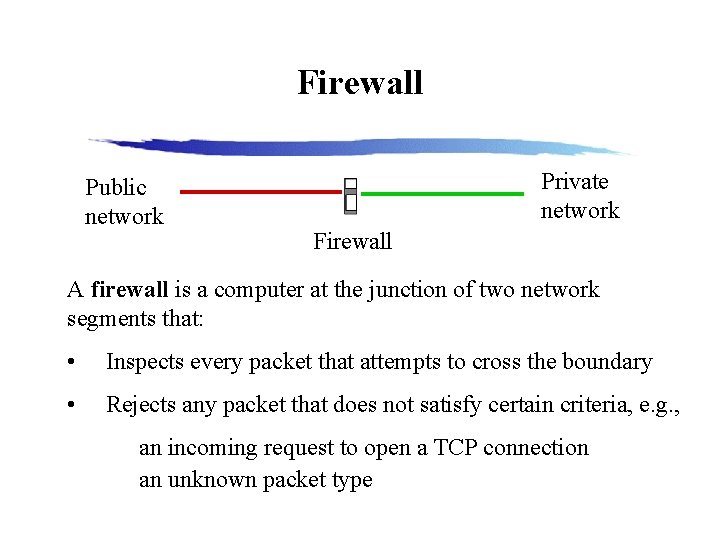
Firewall Public network Private network Firewall A firewall is a computer at the junction of two network segments that: • Inspects every packet that attempts to cross the boundary • Rejects any packet that does not satisfy certain criteria, e. g. , an incoming request to open a TCP connection an unknown packet type

The Domain Name System First attempt to resolve www. cs. cornell. edu server 1 2 3 cornell. edu server cs. cornell. edu server

Discussion of the First Attempt Problems?

The Domain Name System Better method local DNS server 1 almaden. ibm. com cornell. edu Local ece. cmu. edu cache ibm. com acm. org. edu server 2 cornell. edu server 3 cs. cornell. edu server

Real Time System A real time system is a software system whose correct functioning depends upon the results produced and the time at which they are produced. • A soft real time system is degraded if the results are not produced within required time constraints • A hard real time system fails if the results are not produced within required time constraints

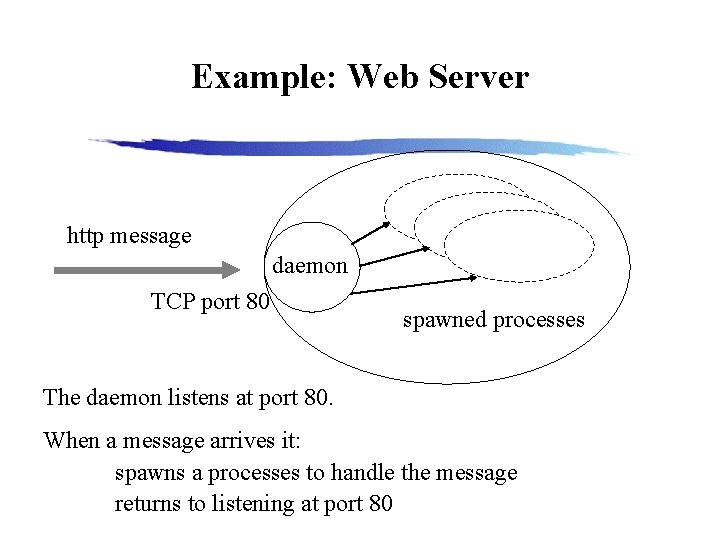
Example: Web Server http message daemon TCP port 80 spawned processes The daemon listens at port 80. When a message arrives it: spawns a processes to handle the message returns to listening at port 80

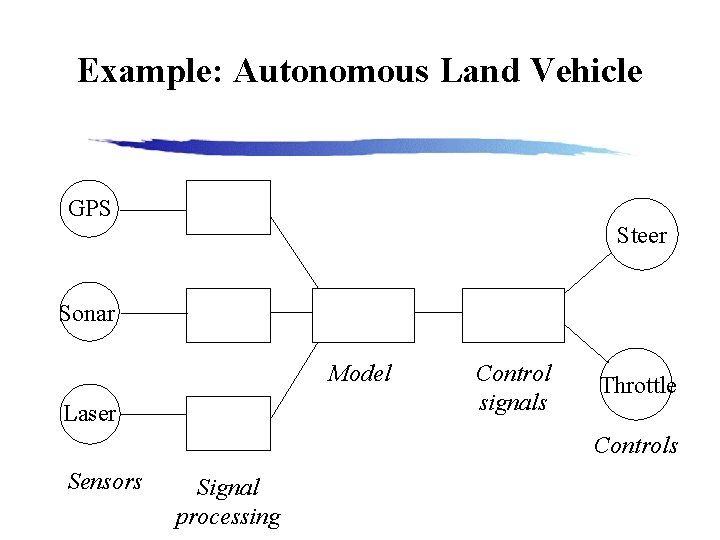
Embedded Systems Software and hardware combined to provide an integrated unit, usually dedicated to a specific task: • Digital telephone • Automobile engine control • GPS • Scientific instruments The software may be embedded in the device in a manner that can not be altered after manufacture.

Example: Autonomous Land Vehicle GPS Steer Sonar Model Laser Control signals Throttle Controls Sensors Signal processing

Other Applications Response critical • • • Network router Telephone switch Seat bag controller Shared systems • • Multi-user data processing Time sharing

Techniques • Special purpose hardware • Multi-threading and multi-tasking • Parallel processing => digital signal processing • Interrupts => levels and priorities

Multi-Threading Several similar threads operating concurrently: • Re-entrant code -- separation of pure code from data for each thread • Testing -- single thread and multi thread May be real time (e. g. , telephone switch) or nontime critical

Real Time Executive Schedules and dispatches tasks in a real time system • Real time clock • Interrupt handler • Scheduler • Resource manager • Dispatcher Must be extremely reliable

Timing mechanisms • Synchronous (clocked) -- periodic stimuli • Asynchronous -- wait for next signal Example: Communications protocols may be synchronous or asynchronous

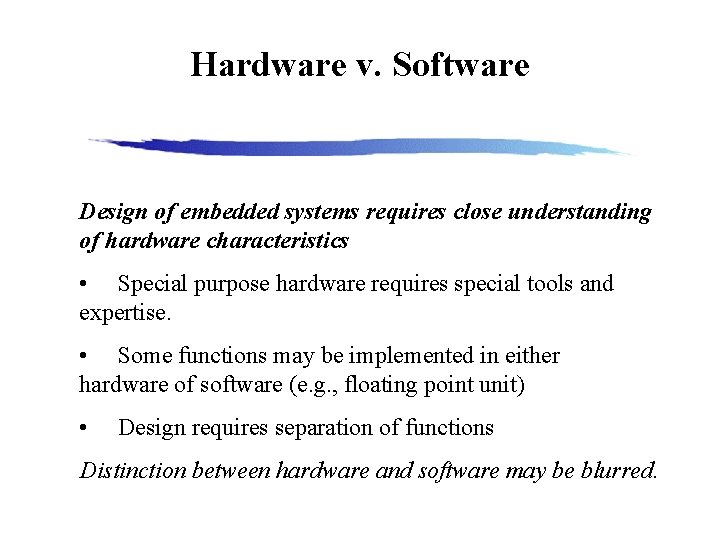
Hardware v. Software Design of embedded systems requires close understanding of hardware characteristics • Special purpose hardware requires special tools and expertise. • Some functions may be implemented in either hardware of software (e. g. , floating point unit) • Design requires separation of functions Distinction between hardware and software may be blurred.

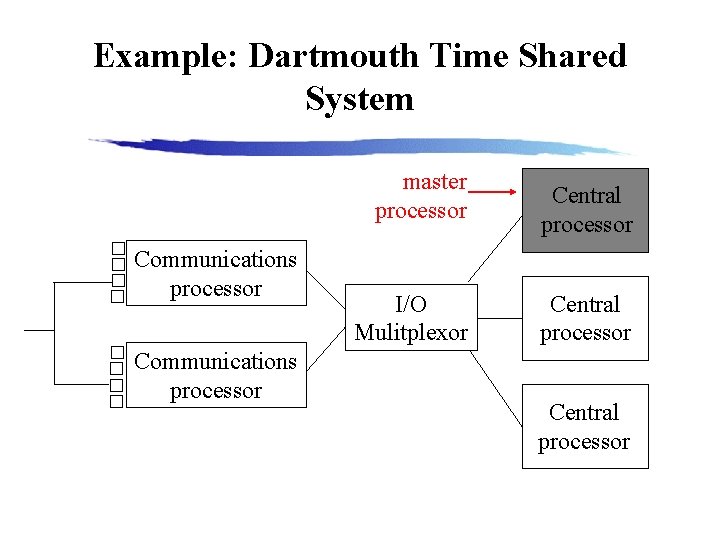
Example: Dartmouth Time Shared System master processor Communications processor I/O Mulitplexor Central processor

Software Considerations Resource considerations may dictate software design and implementation: • Low level language (e. g. , C) where programmer has close link to machine • Inter-process communication may be too slow (e. g. , C fork). • May implement special buffering, etc. , to control timings

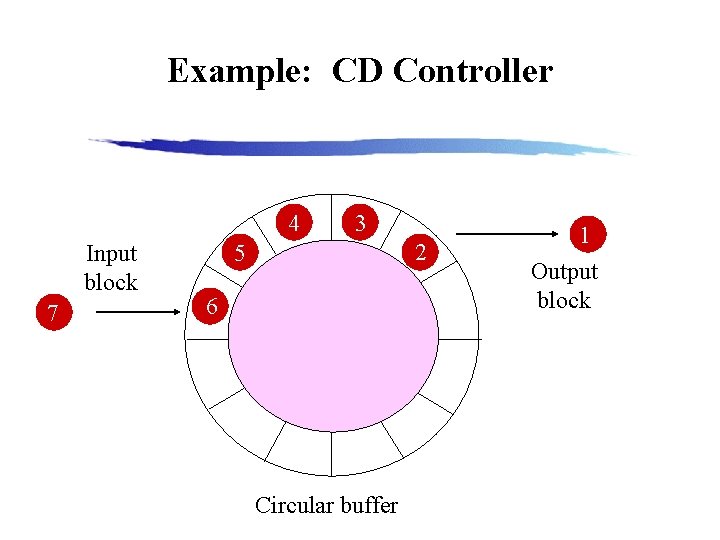
Example: CD Controller 4 Input block 7 3 2 5 6 Circular buffer 1 Output block

Continuous Operation Many systems must operate continuously • Software update while operating • Hardware monitoring and repair • Alternative power supplies, networks, etc. • Remote operation These functions must be designed into the fundamental architecture.

Routers and Other Network Computing • Interoperation with third party devices • Support for several versions of protocols • Restart after total failure • Defensive programming -- must survive => erroneous or malicious messages => extreme loads Time outs, dropped packets, etc. Evolution of network systems • •