Cryptanalysis of the Stream Cipher DECIM Hongjun Wu
















- Slides: 19

Cryptanalysis of the Stream Cipher DECIM Hongjun Wu and Bart Preneel Katholieke Universiteit Leuven ESAT/COSIC KULeuven, ESAT/COSIC

Overview 1. 2. 3. 4. Introduction to DECIM Key Recovery Attack (on Initialization) Distinguishing Attack Conclusion KULeuven, ESAT/COSIC 2

Description of DECIM (1) submission to the e. Stream 80 -bit key, 64 or 80 -bit IV hardware efficient stream cipher (profile II) Main features 1. ABSG decimation algorithm (similar to the self-shrinking generator, 25% more efficient) 2. Buffer for constant output rate KULeuven, ESAT/COSIC 3

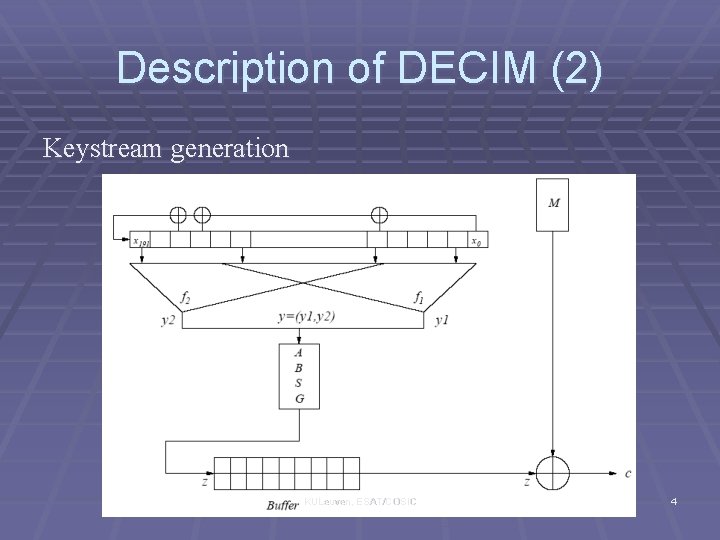
Description of DECIM (2) Keystream generation KULeuven, ESAT/COSIC 4

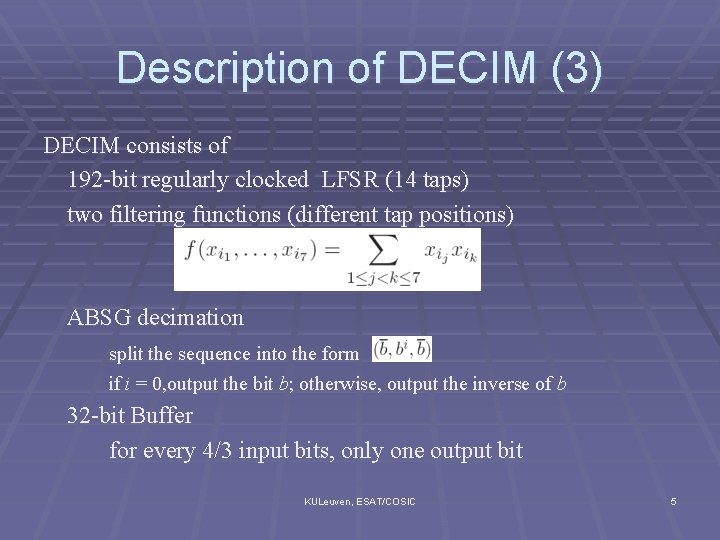
Description of DECIM (3) DECIM consists of 192 -bit regularly clocked LFSR (14 taps) two filtering functions (different tap positions) ABSG decimation split the sequence into the form if i = 0, output the bit b; otherwise, output the inverse of b 32 -bit Buffer for every 4/3 input bits, only one output bit KULeuven, ESAT/COSIC 5

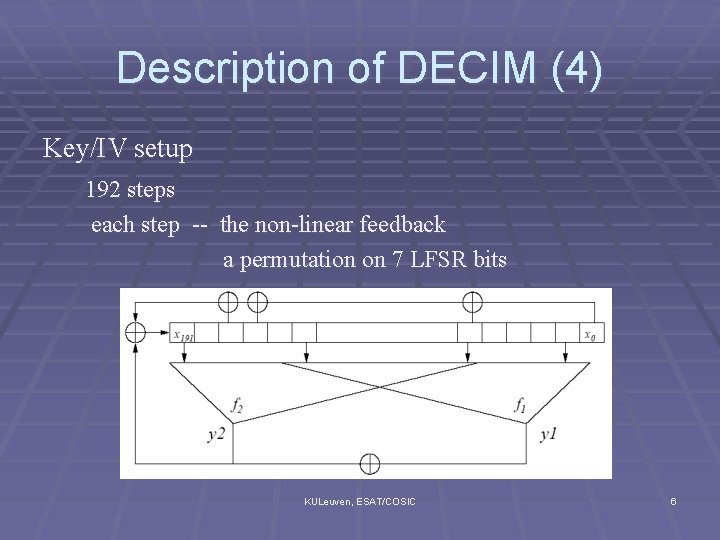
Description of DECIM (4) Key/IV setup 192 steps each step -- the non-linear feedback a permutation on 7 LFSR bits KULeuven, ESAT/COSIC 6

Key Recovery Attack (1) Overview of the Attack The permutations are used to update the LFSR => 54. 5 bits in the LFSR are not updated during the key/IV setup => key recovered with 220 random IVs, the first 2 keystream bytes, negligible computations KULeuven, ESAT/COSIC 7

Key Recovery Attack (2) Two permutations operate on 7 elements (st+5, st+31, st+59, st+100, st+144, st+177, st+186) If the output of ABSG is 1, the first permutation is used; otherwise, the second is used KULeuven, ESAT/COSIC 8

Key Recovery Attack (3) Using permutation to update FSR is bad If no permutation, then every bit in the FSR is updated once every 192 steps But with the permutation on the FSR, the bit positions are changed, some bits would be updated more than once while some bits not updated! => no matter how to design the permutation the updating would not be uniform for all the bits KULeuven, ESAT/COSIC 9

Key Recovery Attack (4) The key-dependent selection of permutations does not hide the intrinsic weakness of the permutation =>in average 54. 5 bits in the LFSR are not updated KULeuven, ESAT/COSIC 10

Key Recovery Attack (5) To recover the key, we need to trace each key bit to see how that key bit is updated during those 192 steps in the initialization => very tedious use computer program to trace those key bits KULeuven, ESAT/COSIC 11

Key Recovery Attack (6) One example – recovering K 21 s 21 = K 21 / IV 21 s 21 is not updated and it becomes s 192+6 with prob 1/27 s 192+6 used in the generation of the first keystream bit z 0 if s 192+6 is 0, then z 0=0 with prob. 56/128 if s 192+6 is 1, then z 0=0 with prob. 72/128 if K 21 = 1, the distribution of z 0 independent of IV 21 if K 21 = 0, the distribution of z 0 affected by IV 21 => Being used to identify K 21 with about 218. 5 random IVs KULeuven, ESAT/COSIC 12

Distinguishing Attack (1) Overview of the Attack The filtering functions are not 1 -resilient ABSG could not hide the non-randomness => any two adjacent bits are equal with 0. 5+2 -9 message being recovered if encrypted 218 times KULeuven, ESAT/COSIC 13

Distinguishing Attack (2) Bias from the filtering function If two inputs share one common bit, the two outputs bits are equal with prob. 65/128 KULeuven, ESAT/COSIC 14

Distinguishing Attack (3) Bias passing through the ABSG decimation and buffer Deal with the bits with relations not affected significantly by the ABSG decimation algorithm i. e. , the bits with small distance For these three pairs of bits, passing through the ABSG decimation and buffer does not reduce the bias too much (about 8 to 32 times) But the analysis is too complicated (details ignored here) KULeuven, ESAT/COSIC 15

Distinguishing Attack (4) Any two adjacent keystream bits are equal with probability 0. 5+2 -9 The bias is large enough for the broadcast attack If a message if encrypted by DECIM for 218 times, then the message could be recovered KULeuven, ESAT/COSIC 16

DECIM v 2 Initialization Permutation removed 768 steps Keystream generation one LFSR + one filtering function + ABSG + buffer 1 -resillient filtering function Greatly simplified comparing to the original version KULeuven, ESAT/COSIC 17

Conclusion Using permutation to update FSR is undesirable Try to design Boolean function conservatively (high resilience, …. ) KULeuven, ESAT/COSIC 18

Thank you! Q&A KULeuven, ESAT/COSIC 19