DOM XSS ADog CONTENT 1 Introduction 2 Riding








- Slides: 25

DOM XSS之殇 报告人: ADog

CONTENT 1. Introduction 2. Riding out DOMsday 3. Defence 4. Conclusion

1. Introduction Description Causes Examples Consequences

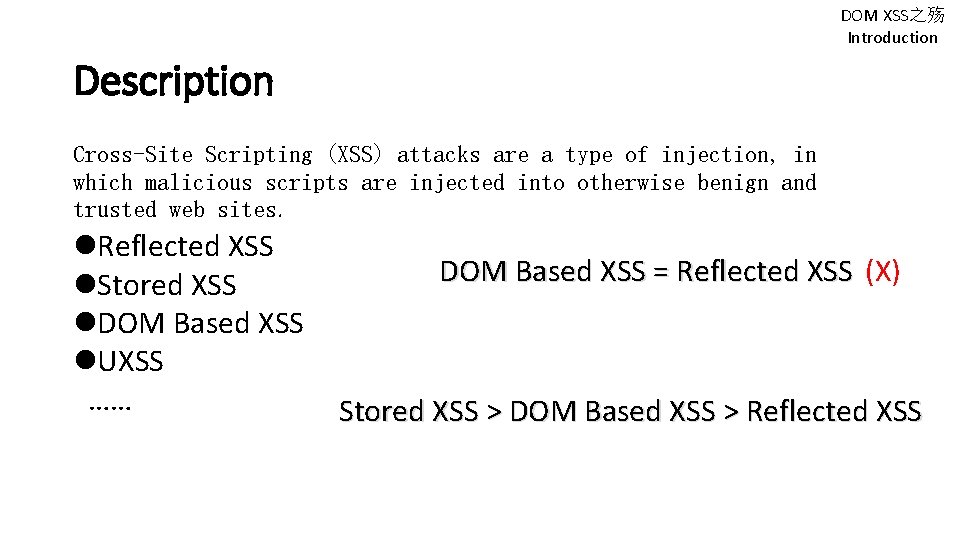
DOM XSS之殇 Introduction Description Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted web sites. Reflected XSS Stored XSS DOM Based XSS UXSS …… DOM Based XSS = Reflected XSS (X) Stored XSS > DOM Based XSS > Reflected XSS

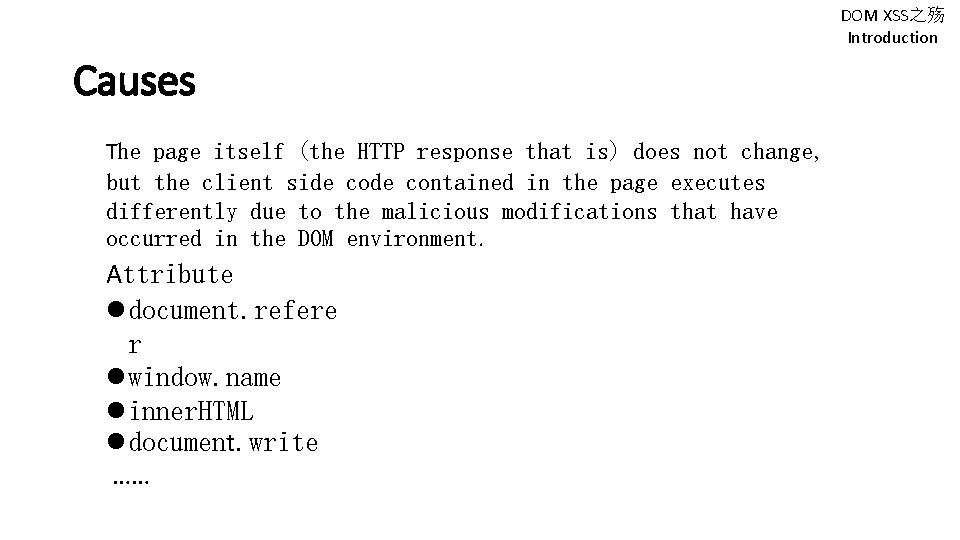
DOM XSS之殇 Introduction Causes The page itself (the HTTP response that is) does not change, but the client side contained in the page executes differently due to the malicious modifications that have occurred in the DOM environment. Attribute document. refere r window. name inner. HTML document. write ……

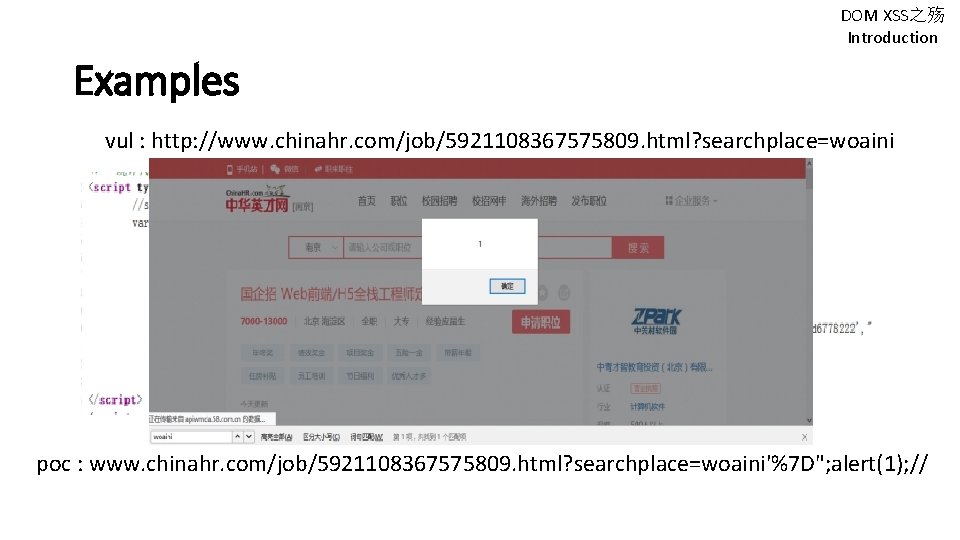
DOM XSS之殇 Introduction Examples vul : http: //www. chinahr. com/job/5921108367575809. html? searchplace=woaini poc : www. chinahr. com/job/5921108367575809. html? searchplace=woaini'%7 D"; alert(1); //

DOM XSS之殇 Introduction Consequences A B Login Cookies Passwords C D Authentications Tokens Url Redirection

2. Riding out DOMsday 1 Methodology 2 Results 3 Limitations 4 Discussion

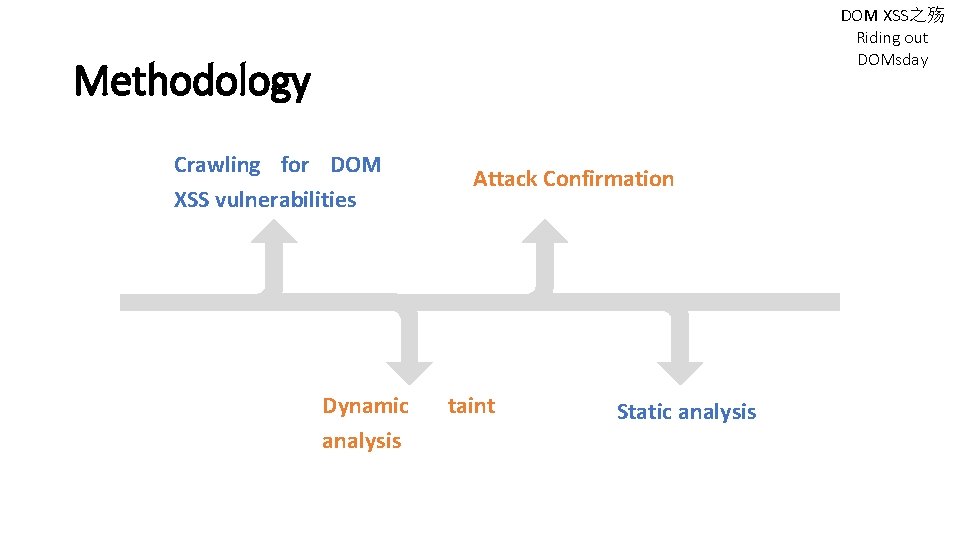
DOM XSS之殇 Riding out DOMsday Methodology Crawling for DOM XSS vulnerabilities Dynamic analysis Attack Confirmation taint Static analysis

Methodology Crawling for DOM XSS vulnerabilities = How to crwal the websites and which web pages we visited I. Starting by visiting the Alexa Top 10, 000 websites. II. Collecting all the links to other web pages on the home page of each website, and randomly selecting five web pages. Premise : Obey the robots. txt directives DOM XSS之殇 Riding out DOMsday

Methodology Dynamic taint analysis = The specifics of the taint-tracking engine we developed I. Allocating space in Java. Script string primitive. II. Recording which built-in encoding methods have been applied. III. Writing the flow to a log file if an argument contains tainted bytes. IV. Analyzing the logs to determine which flows are vulnerable. DOM XSS之殇 Riding out DOMsday

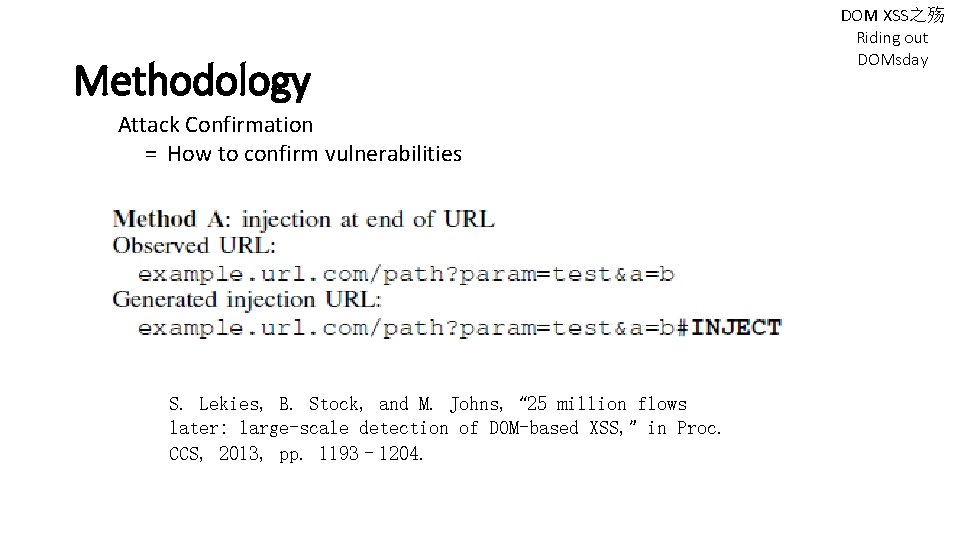
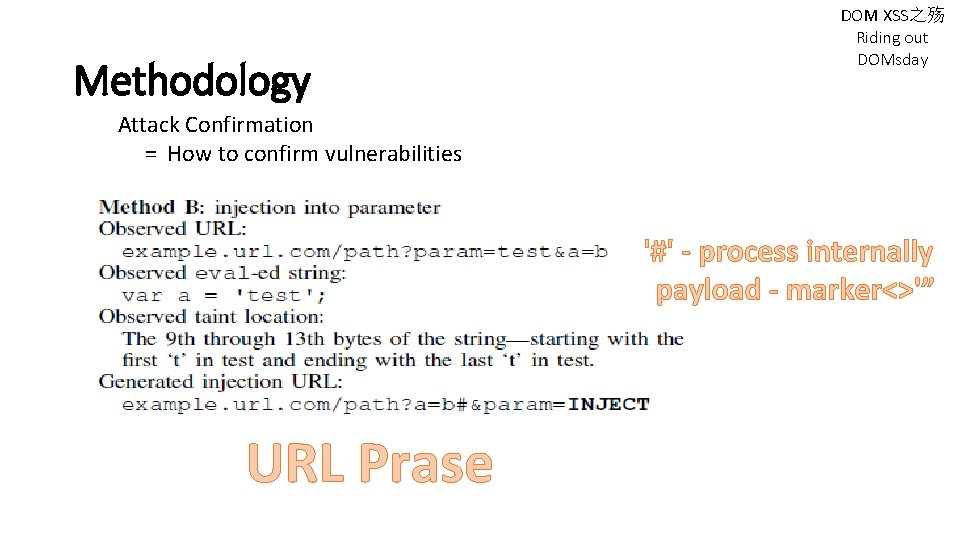
Methodology Attack Confirmation = How to confirm vulnerabilities S. Lekies, B. Stock, and M. Johns, “ 25 million flows later: large-scale detection of DOM-based XSS, ” in Proc. CCS, 2013, pp. 1193– 1204. DOM XSS之殇 Riding out DOMsday

Methodology DOM XSS之殇 Riding out DOMsday Attack Confirmation = How to confirm vulnerabilities '#' - process internally payload - marker<>'” URL Prase

Methodology DOM XSS之殇 Riding out DOMsday Static analysis = Detail the methodology for testing static-analysis tools Opensource or inexpensive proprietary tools that statically detect DOM XSS vulnerabilities : I. Scan. JS II. esflow III. Burp Suite Pro

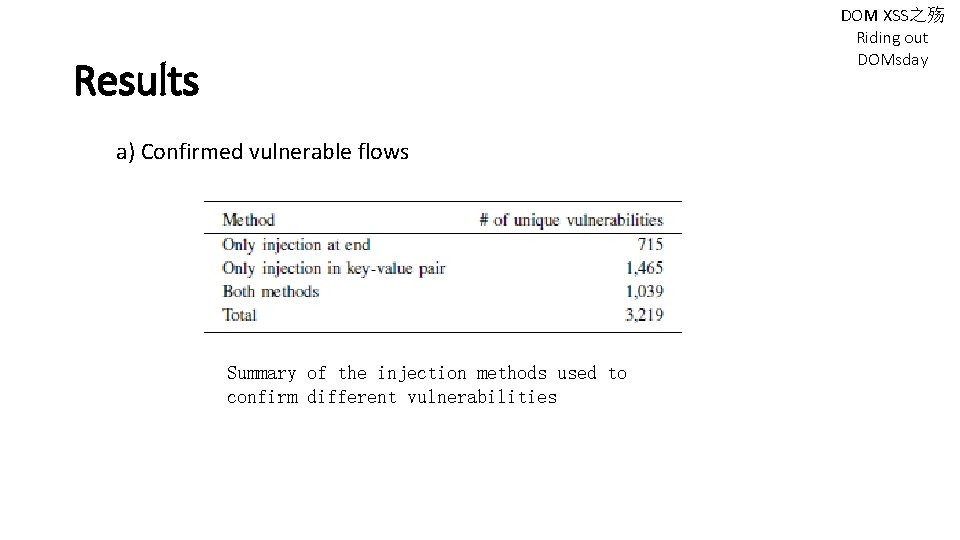
DOM XSS之殇 Riding out DOMsday Results a) Confirmed vulnerable flows Summary of the injection methods used to confirm different vulnerabilities

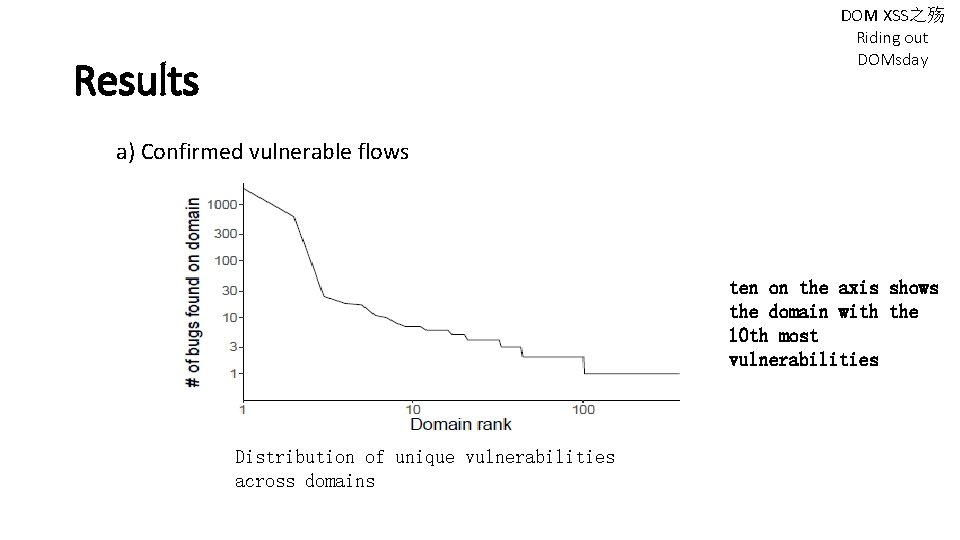
DOM XSS之殇 Riding out DOMsday Results a) Confirmed vulnerable flows ten on the axis shows the domain with the 10 th most vulnerabilities Distribution of unique vulnerabilities across domains

DOM XSS之殇 Riding out DOMsday Results b) Vulnerability attribution by domain and domain category Categories of top level domains that contain an iframe with a DOM XSS vulnerability

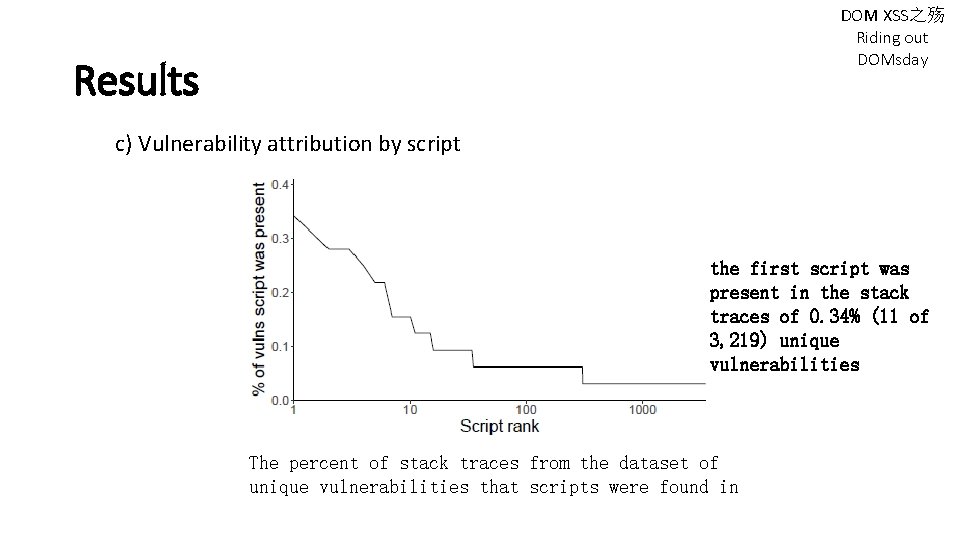
DOM XSS之殇 Riding out DOMsday Results c) Vulnerability attribution by script the first script was present in the stack traces of 0. 34% (11 of 3, 219) unique vulnerabilities The percent of stack traces from the dataset of unique vulnerabilities that scripts were found in

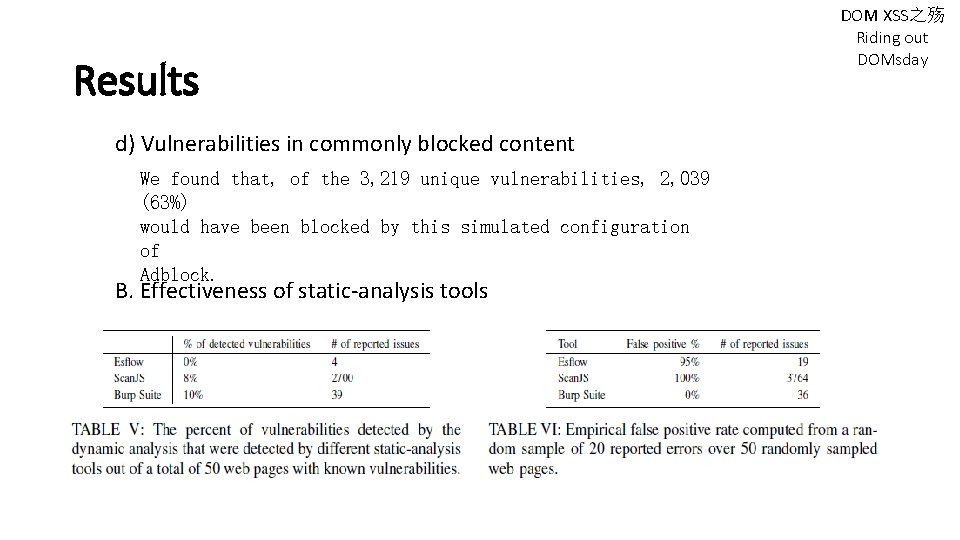
Results d) Vulnerabilities in commonly blocked content We found that, of the 3, 219 unique vulnerabilities, 2, 039 (63%) would have been blocked by this simulated configuration of Adblock. B. Effectiveness of static-analysis tools DOM XSS之殇 Riding out DOMsday

Limitations 01 Only URL to HTML and Java. Script flows 02 Lack of much dynamic functionality 03 Comparsion to previous work may not be perfectly accurate DOM XSS之殇 Riding out DOMsday

DOM XSS之殇 Riding out DOMsday Confusion Inject Payload Encoding and (marker<>'”) Decoding 01 02 Bypass 03

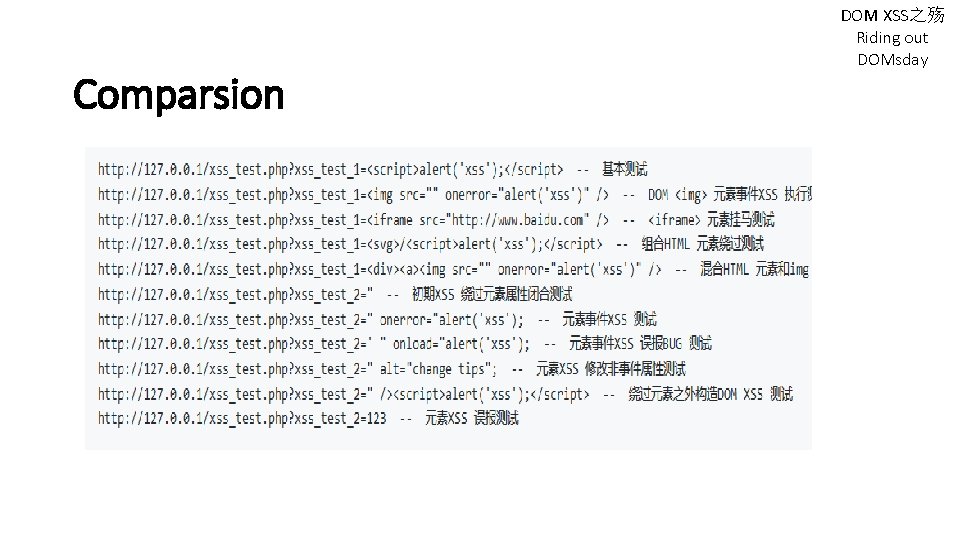
Comparsion LCatro 之前做过一个DOM XSS 检测 具, 原理是解析URL 参数再通过document. body. query. Selector. All 来 查询URL 参数中的特征是不是已经在HTML 中被渲 染过了, 这个方法对反射XSS 有效 Github: https: //github. com/lcatro/XSShunter DOM XSS之殇 Riding out DOMsday

3. Defence CSP(Content Security Policy) http: //foreversong. cn/archives/760 Dynamic analysis(WAF) Secure Coding(encode. URIComponent) Static analysis

4. Conclusion 1 2 Riding out DOMsday Introduction • • Description Causes Examples Consequences 3 • • Methodology Results Limitations Discussion Defence • CSP • WAF

Thank you