Commercial Drones Peeping Tom or Precision Operator A










- Slides: 13

Commercial Drones: Peeping Tom or Precision Operator? A Governance, Risk and Compliance Framework for a Secure Drone Eco-system Saravanan Thangavelu Lech Janczewski Gabrielle Peko David Sundaram

Main research motivation: Proliferation of commercial drone use without suitable governance, risk management and compliance mechanisms • Expanding types of applications: • From battlefield to entertainment, industry and services • No standardization in hardware and software components especially on security aspects • General capabilities architecture needs to be defined • Addressing cyber-security threats (data protection, privacy, operational security) 2

Examples of issues: Delivering of vital medicine supply to rural areas that have rough terrain and less access to hospital. Drone delivery of blood in 15 mins compared with road 2 hours: Zipline in Rwanda. Source: Zipline, 2020 Could be used for mass delivery of vital items in the case of pandemic like coronavirus disease (COVID-19). But mass use of drones impossible without solving logistic issues like: • Lack of harmonization and standardization. • Regulations and adequate drone framework. 3

Literature analysis • Suggestions on cyber-vulnerabilities unique to drone operations and privacy (Kim & Kim, 2019; Vacek, 2017; Krishna & Murphy, 2017; Vattapparamban et al. , 2016; Bressler & Bressler, 2016). • Performance standards and self-certification (Perritt & Plawinski, 2016). • Societal impacts of civilian drones (Bartsch et al. , 2017; Rao et al. , 2016). • Security and privacy challenges (Lin et al. , 2018; Lv, 2019). • Civil application challenges such as charging, classification, collision avoidance, networking and swarming (Shakhatreh et al. , 2018; Hassanalian & Abdelkefi, 2017). • Industry perspective and recommendations (Molina & Campos (ed. ), 2018). • Integration of drones into the National Airspace System (Dalamagkidis et al. , 2012; Takahashi, 2012). • Counter-drone solutions (Shelley, 2018). • Drone-focused cybersecurity and privacy laws (Urban, 2018). • Regulatory response (Nakamura & Kajikawa, 2018; Clarke, 2016; West, 2015). 4

Standards • The commercial drone market is being monopolized and there is a need for anti-competitive stance that can enable a harmonized consortium to develop secure commercial drone components. • Recent implementation of ISO 21382 (for operational procedures ONLY) is a well–thought approach but it does not clearly identify role of manufacturers and drone components. ISO 21382 reflects more towards drone operators/service providers and not manufacturers responsibilities. Also, secure framework for safety and security measures is yet to be developed. 5

Research and practical problem There is an absence of a dynamic framework and regulatory model. 6

Research objectives • To develop a reliable, inclusive and dynamic framework and relevant artefacts for driving towards a secure drone eco-system. • Existing commercial drone regulations and frameworks will be analyzed for their suitability to the current commercial drone market and threat vectors. • To propose security focused framework and regulatory model that can enable the development of security and privacy-focused drones by default. • To recommend the adoption of a holistic 3 -step approach model to effectively mitigate threats and protect drone operations and critical infrastructures. 7

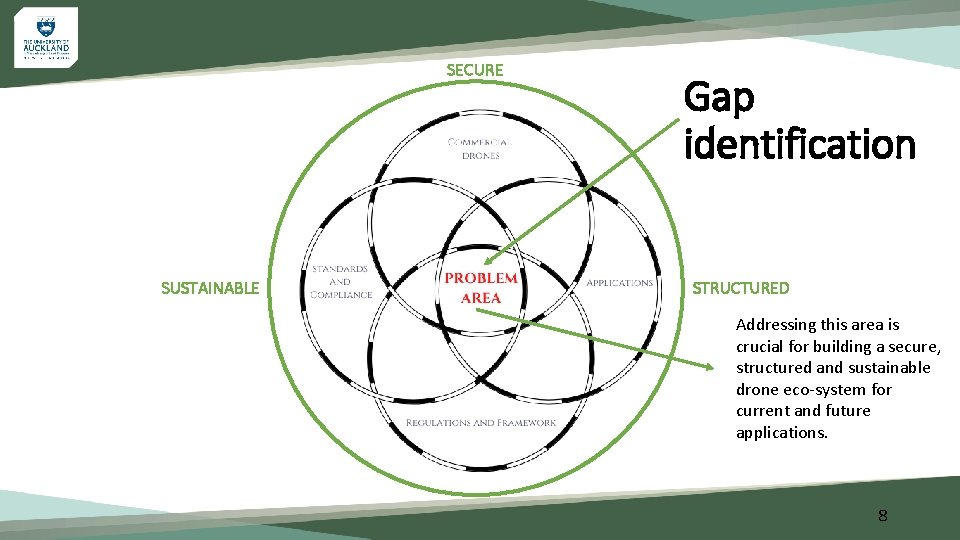
SECURE SUSTAINABLE Gap identification STRUCTURED Addressing this area is crucial for building a secure, structured and sustainable drone eco-system for current and future applications. 8

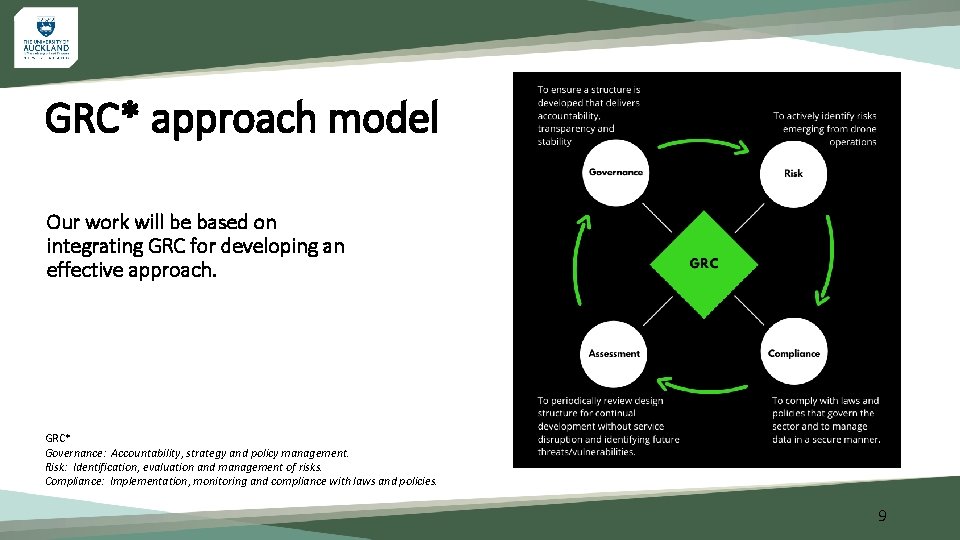
GRC* approach model Our work will be based on integrating GRC for developing an effective approach. GRC* Governance: Accountability, strategy and policy management. Risk: Identification, evaluation and management of risks. Compliance: Implementation, monitoring and compliance with laws and policies. 9

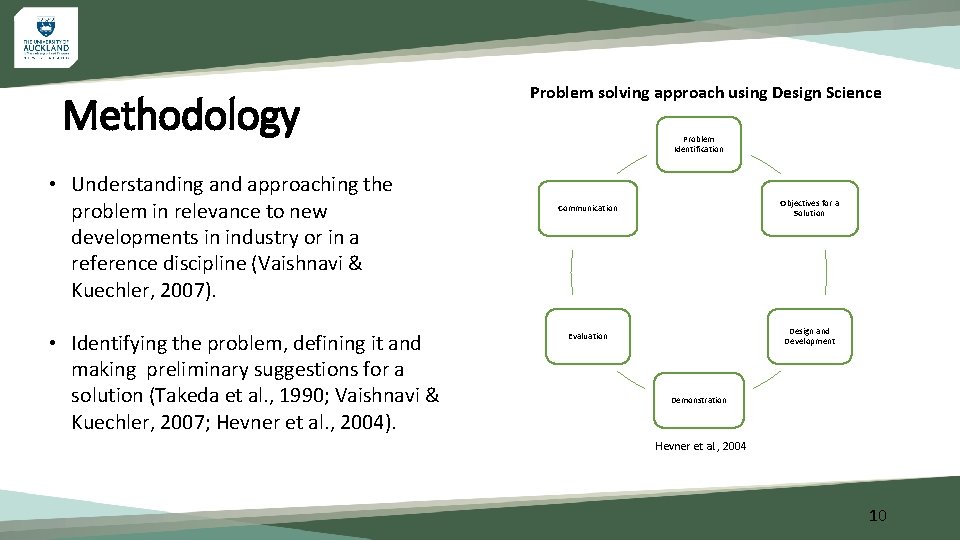
Methodology • Understanding and approaching the problem in relevance to new developments in industry or in a reference discipline (Vaishnavi & Kuechler, 2007). • Identifying the problem, defining it and making preliminary suggestions for a solution (Takeda et al. , 1990; Vaishnavi & Kuechler, 2007; Hevner et al. , 2004). Problem solving approach using Design Science Problem Identification Communication Objectives for a Solution Evaluation Design and Development Demonstration Hevner et al. , 2004 10

Next research steps: • To evaluate the current framework and regulations used in New Zealand. • Interviews/conversations with industry experts and drone manufactures for developing efficient and novel solutions. • To create and recommend a reliable and effective framework and regulatory model. 11

Possible future projects: • Risk analysis of commercial drones available on the market. • Reviewing existing drone manufactures’ security approach. • Mandatory implementation of mitigative measures for reducing threats and vulnerabilities (technical and societal). Project approach method: § Case study § Evaluative § Action research 12

Thank you! Questions?