Clientside vs Serverside Security 1 Outline Intro Clientside










- Slides: 15

Client-side vs Serverside Security 1

Outline ◦ ◦ Intro Client-side security Server-side security Complete security ? 2

Intro. ◦ The security of a web-based information system requires security controls at each tier (client, web server, database server, …). browser web server application/database server HTTP/HTTPS application protocol(s) or HTTP/HTTPS Figure 11. 1 ◦ A web client can become an easy target. ◦ The servers are prime targets to the hackers. ◦ The communication links must be secured as well. 3

Client-side security A challenge to provide total security to clients 1. Client devices tend to be handled by end users with varying levels of expertise. 2. There exist multiple types of client devices. 3. Various executables and/or email attachments may be downloaded to a networked client device. 4. There exist various client applications, each of which requires different configurations, updates, etc. 5. Less physical security 4

Challenges User awareness Client configurations/updates ◦ anti-malware applications ◦ Web browsers ◦ Email client applications How far and how long would sensitive data need to be protected? ◦ Encryption? (key management, …) ◦ MAC? ◦ Period of protection? 5

Server-side security What need to be secured? ◦ The server itself (physical, applications, data) ◦ The connections to the clients ◦ The connected clients A centralized location to enable security controls 6

Server-side security Challenges? 1. A rewarding target (web presence, precious data) 2. Various server-side technologies CGI scripts Server APIs Server-side includes ASP JSP/Servlets Ph. P 7

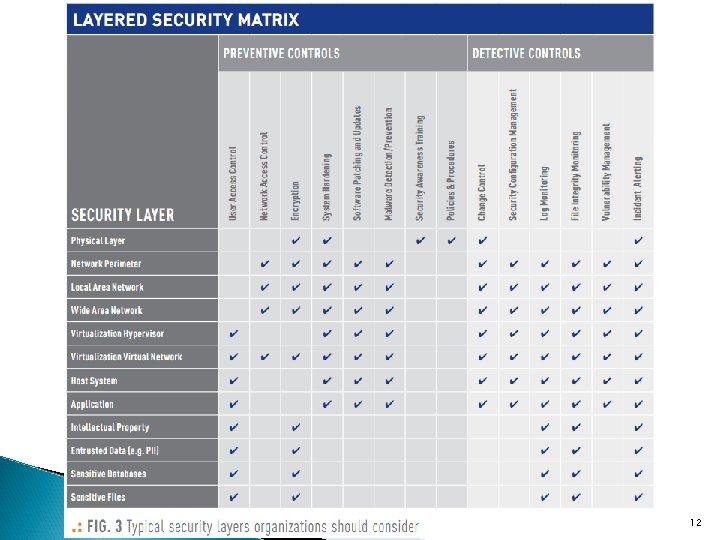
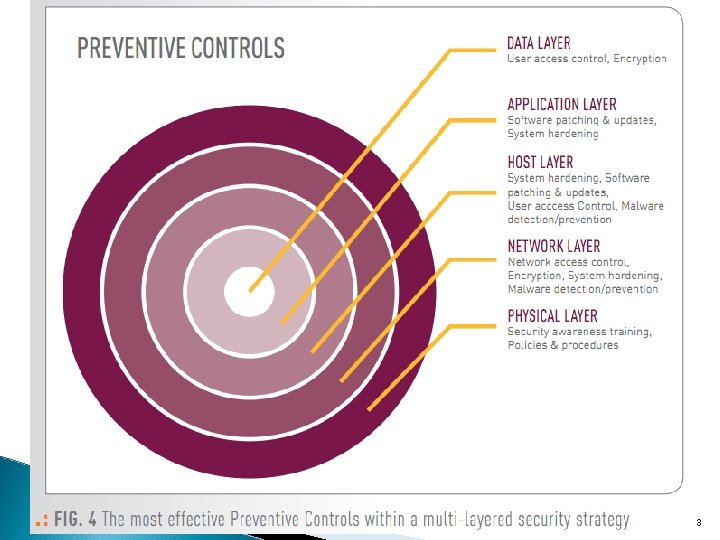
Server-side security Challenges? (cont. ) 3. Possibly high workload (many connections) 4. Need for layered security (application layer vs network or lower layer) 5. Configurations and updates 8

Is “complete” security possible? That’s the goal. Requires the cooperation of all participants, the security of all devices and communication links. ◦ Data security: When and where do sensitive data need to be protected? Laws require corporations and organizations to implement proper measures to protect the data they process. 9

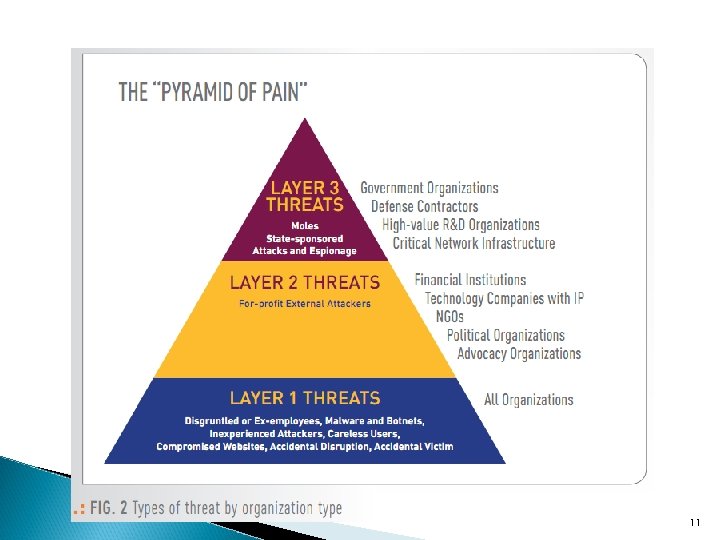
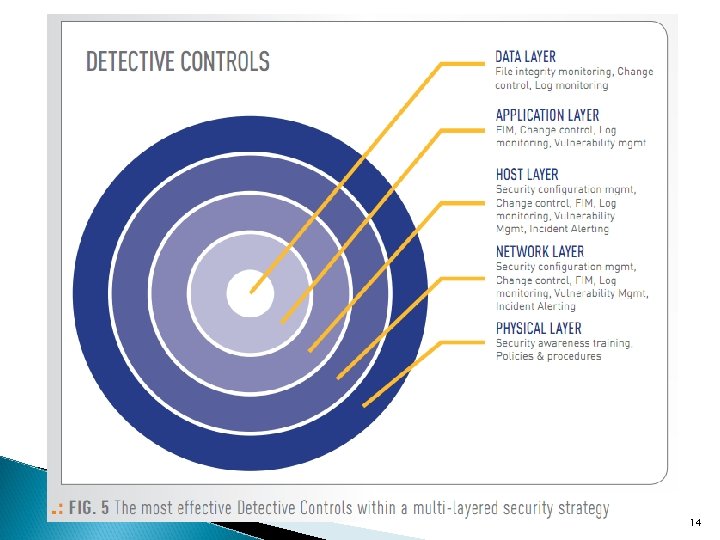
Layered Security: Protecting Your Data in Today's Threat Landscape, Tripwire white paper, 2011. 10

11

12

13

14

Points of discussions: - a better solution to client/end security? Thin clients + cloud computing ? - Is multi-layer security a complete solution? 15