CIS 371 Computer Organization and Design Meltdown Spectre







- Slides: 13

CIS 371 Computer Organization and Design Meltdown & Spectre Hardware Vulnerabilities 1

Meltdown & Spectre Bugs Act I: Leaky Caches Act II: Meltdown Act III: Poisoned Branch Predictors Act IV: Spectre Act V: Perspective 2

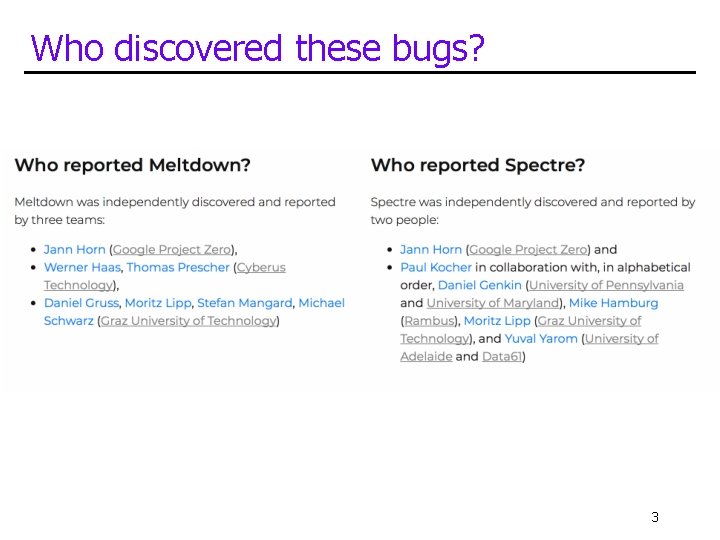
Who discovered these bugs? 3

Act I: Leaky Caches • Goal: leak information via caches without anyone noticing! • Can be used for both: • side channel (unintentional communication) • covert channel (intentional communication) 2005 4

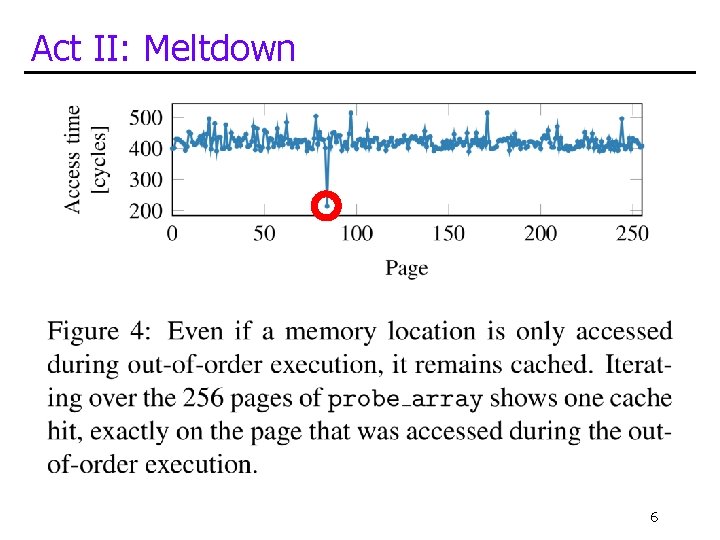
Act II: Meltdown r 0, r 1: temps r 2: kernel address we wish to read r 3: start of probe_array ldr sll add ldr r 0 r 1 <<<<- [r 2] <= but doesn’t this raise an exception? ? !? r 0, #12 r 3, r 0 [r 1] 5

Act II: Meltdown 6

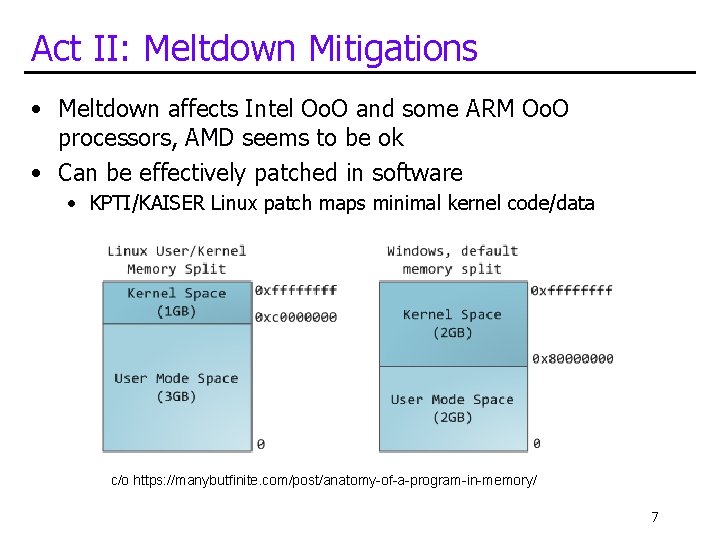
Act II: Meltdown Mitigations • Meltdown affects Intel Oo. O and some ARM Oo. O processors, AMD seems to be ok • Can be effectively patched in software • KPTI/KAISER Linux patch maps minimal kernel code/data c/o https: //manybutfinite. com/post/anatomy-of-a-program-in-memory/ 7

Act III: Poisoned Branch Predictors • Goal: trick another process into leaking information 8

What happens on a Context Switch • Operating system responsible to handle context switching • Hardware support is just a timer interrupt • Each process has an associated data structure which is used to record relevant state such as: • Architected state: PC, registers, Page table pointer • Save and restore them on context switches • Memory state? • Non-architected state: caches, predictor tables, etc. • Ignore or flush • ignoring is key aspect of Spectre/Meltdown vulnerabilities! • OS swaps out values for old process, swaps in values for new process and restarts the system. CIS 371: Comp. Org. | Dr. Joe Devietti | Virtual Memory 9

Act III: Poisoned Branch Predictors • Goal: trick another process into leaking information • Let’s say my sensitive program contains this code: if (x < array 1_size) { y = array 2[array 1[x] * 256]; } 10

Act IV: Spectre • How do I poison the BHT/BTB? • Not hard when the attacker provides their own code • Java. Script, VM on EC 2 • How do I get the victim to run the vulnerable code? • highly victim-specific • easiest in JIT environments, read Chrome state from Java. Script 11

Act IV: Spectre Mitigations • Spectre affects Oo. O chips from everyone! • confirmed on Intel, ARM, AMD • Software patches are incomplete, slow • Reduce use of indirect branches • Disable speculation through special instructions at “critical” code points • Ultimately, Spectre attacks aren’t that easy to pull off 12

Why these names? • Why is it called Meltdown? • “The vulnerability basically melts security boundaries which are normally enforced by the hardware. ” • Why is it called Spectre? • “The name is based on the root cause, speculative execution. As it is not easy to fix, it will haunt us for quite some time. ” • https: //meltdownattack. com/#faq-why-meltdown 13