Chapter 16 Wireless Mesh networks Overview Introduction Mesh









- Slides: 28

Chapter 16 Wireless Mesh networks

Overview Introduction Mesh network defined Benefits of wireless mesh Current issues and solutions Mesh deployment issues Conclusion

Introduction Used by Municipalities to enterprises Telecom providers Public safety Military Popular do to Ease of deployment Increase in network capacity mobility

Mesh Network Defined A set of fully interconnected network nodes that support traffic flows between any two nodes over one or more paths or routes Wireless provides connectivity while in motion Biggest example is the internet

Benefits of wireless mesh Deployment Each node maintains multiple connectivity Allows for multiple paths Cost Wired networks are more expensive Many nodes use the same access point Continuity of services in case of device failure Users expect this because of the fee they pay Scalability Easy and cost effective to add more capacity

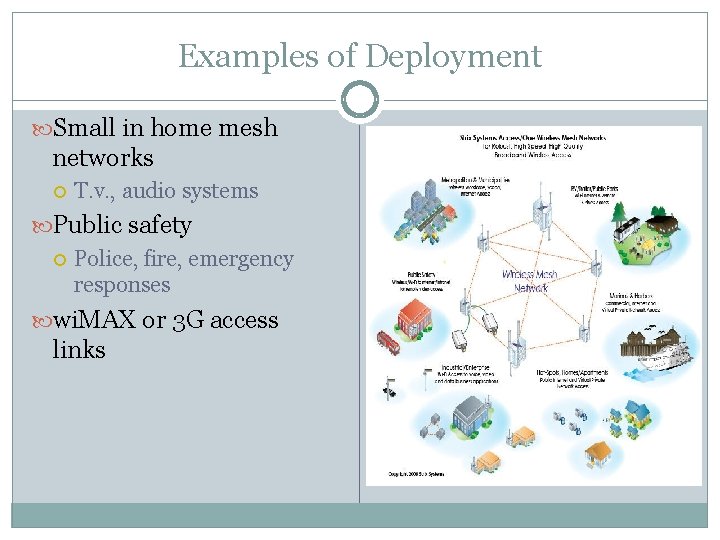
Examples of Deployment Small in home mesh networks T. v. , audio systems Public safety Police, fire, emergency responses wi. MAX or 3 G access links

Current issues and solutions Netowork structure Intra-mesh channel re-use Medium access contention Mesh routing and forwarding Mesh security Congestion control Voice over mesh Mesh network management

Network structure Plays a big role in performance of voice services Determines delay encountered by voice packets Parking lot effect Is a function of the number of hops in a mesh and the peering ratio As seen the hop depth H is 3 and the peering ratio Rp is 2 The load on the portal link is equal to 7 peer links Solutions for the parking lot effect include proper dimensioning of the links of mesh network and/or limiting access to the mesh so as to keep the offered load within the limits imposed by the capacity of the available RF links

Intra-mesh Channel Re-use Links between mesh nodes may use one or more RF channels One RF channel for rapid peer acquisition and mesh formation Re-use worsens parking lot effect May cause interference between links The further from a portal, the more a packet has to compete for the channel In some cases nodes may not see other node transmissions This leads to interference and packet loss

Intra-mesh Channel Re-use Due to exponential back off for MAC in IEEE 802. 11 protocol, packet loss may lead to significant delays per packet per link Solutions require increasing the isolation between links Three dimensions are available: Space(directional antennas) Frequency(multiple RF channels) Coding(using orthogonal codes for mesh links) Which is best depends on requirements and conditions of a given network deployment

Medium Access Contention IEEE 802. 11 MAC is designed for bursty data traffic in unpredictable RF environments Channel state is re-established for every packet Done with listen-before-talk and collision avoidance through use of contention window Medium access is subject to jitter For voice and video services, Qo. S extensions have been added to the standard EDCA is an enhancement of the basic distributed access control mechanism with a priority bias for certain types of traffic like voice, video, and best effort data

Mesh Routing and Forwarding Routing of packets has an important role in the service level offered by a mesh network. Route set-up is based on finding the most efficient path to the portal Once links are formed, path does not change except for node or link failure Mobile mesh networks do not have static links A lot of research efforts have been invested in finding a solution to routing in fixed and mobile mesh networks

Mesh routing and Forwarding Spanning tree routing Networks consisting of wireless bridges naturally form treelike structures Rooted in a portal node May be set up using a combination of parameters Such as hop count and link transit delay Monitor functions which detect link failure and/or portal loss, may be used to trigger link or tree rebuilding These structures can be simple and efficient

Mesh Routing and Forwarding AODV: Ad-hoc, On-demand Distance Vector protocol Fairly simple, but not as efficient as spanning tree When route is needed or needs repair, its originator floods the network with a request for a destination The latter replies with a unicast that is forwarded back to the originator Loss of a link triggers a route error message up and down the route The cost of flooding in AODV depends on the rate of change of the environment

Mesh Routing and Forwarding OLSR: Optimized Link State Routing protocol Is a pro-active routing protocol that uses the link state as a driving factor and includes a multicast capability A subset of nodes called multi-point relays, provides anchors for neighbor nodes Link state information distribution can remain local and multicasting is supported naturally Although simple, the implementation of OLSR requires many different control messages. More efficient than flooding based parents, overall efficiency is not the best for this protocol

Mesh Routing and Forwarding HWMP: Hybrid Wireless Mesh Protocol In 2005, the IEEE 802. 11 working group started development of the wireless LAN standard with a layer 2 mesh protocol Includes simple tree building protocol to handle static mesh, and AODV elements to support mobile mesh This allows a mesh to use the most efficient routing protocol appropriate for a given deployment or application

Mesh Routing and Forwarding Regardless of the network structure, there will be alternative routes to a given destination and each node has to decide which next hop to send an a given packet to Requires the use of a consistent set of metrics All nodes involved must share the same meaning and measurement of the metrics of a given link or path Path metrics can include Number of hops, airtime needed to reach destination, complex values that bring together a variety of parameters such as hop count, link load, and SNR

Mesh Routing and Forwarding The best metric to use depends on the type of mesh network and the operational conditions Different types of service have different requirements Voice packets are short and must be delivered within certain time constraints In this case link reliability and hop count are important routing metrics Background data service packets may be large and timing is not important In this case a high data rate is more important than link reliability

Mesh Security in wireless mesh is complicated because of absence of human users that can be used as trusted parties during network initialization Security functionality and the storage of cryptographic data cannot be fully relied upon Mesh nodes perform a number of functions, each of which has its own security concerns

Mesh Security Discovery This function serves to detect other mesh nodes that belong to the same owner or administrative domain Security is limited to authentication of the information provided by other nodes Can be provided by means of public key ciphers that allow the verification of digital signatures This is done depending on operational needs, the tolerance for overhead and the available budget In commercial mesh, the discovery function is left unprotected Exposes the network to spoofing and DOS attacks

Mesh Security Peer link establishment This function creates secure links between mesh nodes and in the process it validates the non-protected data that nodes obtain during discovery Secure link establishment requires Nodes are able to identify themselves They can be authenticated They are able to set up a cryptographic session with each other that protects the flow of data and management information between nodes Various means are available to secure link set-up A combination of symmetric key ciphers and asymmetric ciphers are used

Mesh Security Peer link establishment…continued IEEE 802. 11 X protocol Client requests a connection This is done with a security server Validates the ID of a node and generates keys

Mesh Security Routing Form paths through a network that is used to forward data and management information Interfering with route set-up causes loss of connectivity among nodes as well as loss or hiding of data Attacks against routing functions tend to result in DOS like effects Solutions Expanding routing protocols Tesla approach Secure the link before routing is initiated

Mesh Security Forwarding The forwarding function delivers packets to their destination, either directly or via intermediate nodes that lie on a path known to include the destination Confidentiality and integrity are most important Symmetric key cryptography is preferred for efficiency Can either be hop-by-hop or end-to-end between the original node and the end destination If connected to other networks, end-to-end is impractical, therefore higher layer security solutions like IPSEC must be used

Congestion Control Congestion occurs when a source produces more than its sink can handle Each link is a sink and all links that feed it are potential sources Consider each link as potential sink for traffic Each link carries traffic in both directions Must monitor each outgoing link, and using flow control messages

Congestion Control Other forms of congestion control Rate limiting the traffic sources Pro-active form of source flow control Downside isinefficiency

Voice over Mesh Factors that can affect the quality of voice over mesh Choice of codec Different requirements with respect to jitter Choosing a codec dynamically Handover Client link and intra mesh links may change Time depends on a number of factors Other causes of voice quality impairment Radio measurement traffic Location signaling Legacy 802. 11 devices that share the channel Non-802. 11 devices like microwave ovens and cordless phones, bluetooth

Mesh Deployment Issues For fixed mesh networks, deployment can be a complex issue, even though the self organizing capability makes life a bit easier The main factors that drive a fixed mesh deployment are: The service level to be offered in terms of bits per second per user and on which basis, best effort or guaranteed The user density– people per area The available sites for mounting the access transceivers The available favorable sites for mounting intra-network transceivers The available RF frequency band the number of channels, shared or otherwise