Argus Policies Tutorial Valery Tschopp SWITCH Argus Product


















- Slides: 30

Argus Policies Tutorial Valery Tschopp (SWITCH) – Argus Product Team EGI CF 2013 @ Manchester EMI is partially funded by the European Commission under Grant Agreement RI-261611

Argus Tutorial • Goal of the tutorial – Present the Argus service – Explain the authorization policies • Authorizing VOs, pilot jobs… • Banning users – Job submission through CREAM/g. LExec using Argus authorization – Banning a user payload in a pilot job 11/04/2013 EGI CF 2013, Manchester 2 EMI INFSO-RI-261611 • Demo

Authorization 11/04/2013 EGI CF 2013, Manchester 3 EMI INFSO-RI-261611 What is authorization?

Authorization 11/04/2013 EGI CF 2013, Manchester 4 EMI INFSO-RI-261611 Can user X perform action Y on resource Z ?

Authorization Examples • Can user X… – execute on this worker node (WN) ? – submit a job to this CREAM CE ? – access this storage area ? – submit a job to this WMS instance ? • User X is banned ! 11/04/2013 EGI CF 2013, Manchester 5 EMI INFSO-RI-261611 – Is not allowed to do anything on any resource!

Motivations for Argus • Each Grid service has its own authorization mechanism – Administrators need to know them all – Authorization rules at a site become difficult to understand manage • No global banning mechanism – Urgent ban of malicious users cannot be easily and timely enforced on distributed sites – Hard to change policies without reconfiguring services • Monitoring authorization decisions is hard 11/04/2013 EGI CF 2013, Manchester 6 EMI INFSO-RI-261611 • Authorization policies are static

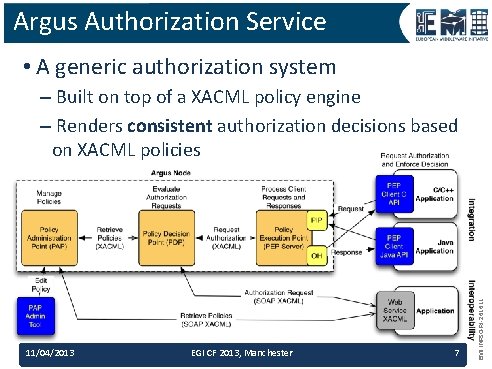
Argus Authorization Service • A generic authorization system 11/04/2013 EGI CF 2013, Manchester 7 EMI INFSO-RI-261611 – Built on top of a XACML policy engine – Renders consistent authorization decisions based on XACML policies

Argus Components • Argus PAP: Policy Administration Point 11/04/2013 EGI CF 2013, Manchester 8 EMI INFSO-RI-261611 – Provides administrators with the tools to author policies (pap-admin) – Stores and manages authored XACML policies – Provides managed authorization policies to other authorization service components (other PAPs or PDP)

Argus Components • Argus PDP: Policy Decision Point 11/04/2013 EGI CF 2013, Manchester 9 EMI INFSO-RI-261611 – Policy evaluation engine – Receives authorization requests from the PEP – Evaluates the authorization requests against the XACML policies retrieved from the PAP – Renders the authorization decision

Argus Components • Argus PEP: Policy Execution Point • Transforms lightweight internal request into XACML • Applies a configurable set of filters (PIPs) to the incoming requests • Asks the PDP to render an authorization decision • If requested by the policy, applies the obligation handler (OH) to determine the user mapping 11/04/2013 EGI CF 2013, Manchester 10 EMI INFSO-RI-261611 – Client/Server architecture – Lightweight PEP client libraries (C and Java) – PEP Server receives the authorization requests from the PEP clients

Authorization Policies Argus is designed to answer the questions: –Can user X performs action Y on resource Z? –Is user X banned? • PERMIT decision –Allow to authorize users to perform an action on a resource • DENY decision • Both can be expressed with XACML policies 11/04/2013 EGI CF 2013, Manchester 11 EMI INFSO-RI-261611 –Allow to ban users

<xacml: Policy. Set xmlns: xacml="urn: oasis: names: tc: xacml: 2. 0: policy: schema: os”Policy. Combining. Alg. Id="urn: oasis: names: tc: xacml: 1. 0: policy-combiningalgorithm: first-applicable" Policy. Set. Id="9784 d 9 ce-16 a 9 -41 b 9 -9 d 26 -b 81 a 97 f 93616" Version="1"> <xacml: Target> <xacml: Resources> <xacml: Resource. Match. Id="urn: oasis: names: tc: xacml: 1. 0: function: string-regexp-match"> <xacml: Attribute. Value Data. Type="http: //www. w 3. org/2001/XMLSchema#string">. *</xacml: Attribute. Value> <xacml: Resource. Attribute. Designator Attribute. Id="urn: oasis: names: tc: xacml: 1. 0: resource-id" Data. Type="http: //www. w 3. org/2001/XMLSchema#string" Must. Be. Present="false"/> </xacml: Resource. Match> </xacml: Resources> </xacml: Target> <xacml: Policy. Id. Reference>public_2 d 8346 b 8 -5 cd 2 -44 ad-9 ad 1 -0 eff 5 d 8 a 6 ef 1</ xacml: Policy. Id. Reference> </xacml: Policy. Set> <xacml: Policy xmlns: xacml="urn: oasis: names: tc: xacml: 2. 0: policy: schema: os” Policy. Id="public_2 d 8346 b 8 -5 cd 2 -44 ad-9 ad 1 -0 eff 5 d 8 a 6 ef 1 ” Rule. Combining. Alg. Id="urn: oasis: names: tc: xacml: 1. 0: rule-combining-algorithm: first-applicable" Version="1"> <xacml: Target> <xacml: Actions> <xacml: Action. Match. Id="urn: oasis: names: tc: xacml: 1. 0: function: string-regexp-match"> <xacml: Attribute. Value Data. Type="http: //www. w 3. org/2001/XMLSchema#string">. *</xacml: Attribute. Value> <xacml: Action. Attribute. Designator Attribute. Id="urn: oasis: names: tc: xacml: 1. 0: action-id" Data. Type="http: //www. w 3. org/2001/XMLSchema#string" Must. Be. Present="false"/> </xacml: Action. Match> </xacml: Actions> </xacml: Target> <xacml: Rule Effect="Deny" Rule. Id="43 c 15124 -6635 -47 ee-b 13 c-53 f 672 d 0 de 77">. . . 11/04/2013 EGI CF 2013, Manchester 12 EMI INFSO-RI-261611 Authorization Policies (XACML)

Authorization Policies • Problem? –XACML not easy to read and/or understand –XACML not easy to write, prone to error • Solution • pap-admin to create, edit, delete permit/deny policy rules 11/04/2013 EGI CF 2013, Manchester 13 EMI INFSO-RI-261611 –Hide the XACML language complexity –Introduce a Simplified Policy Language (SPL) –Provide administrators with simple tool to manage the policies

Simplified Policy Language (SPL) • Deny (ban) a particular user by DN resource ". *" { action ". *" { rule deny { subject=”CN=Valery Tschopp, O=SWITCH, C=CH" } } } resource "http: //grid. switch. ch/wn" { action "http: //glite. org/xacml/action/execute" { rule permit { vo=“atlas" } } } 11/04/2013 EGI CF 2013, Manchester 14 EMI INFSO-RI-261611 • Permit ATLAS users (VO) to execute a job on a worker node (WN)

Identifying Resources and Actions • Actions and Resources are identified by unique ID or “names”, that are assigned to them –Typically URIs, but any string will work • Resource ID example: http: //emitestbed. cnaf. infn. it/ce http: //glite. org/action/submit-job http: //glite. org/action/execute 11/04/2013 EGI CF 2013, Manchester 15 EMI INFSO-RI-261611 • Action ID examples:

Identifying Subjects Subject in a policy can be identified via the following attributes: subject X 509 certificate DN (RFC 2253 format): subject="CN=Valery Tschopp, O=SWITCH, C=CH” ca the CA certificate DN (RFC 2253 format): ca="CN=INFN CA, O=INFN, C=IT” vo the name of the Virtual Organization: vo=”cms” fqan=”/atlas/analysis” 11/04/2013 EGI CF 2013, Manchester 16 EMI INFSO-RI-261611 fqan a VOMS fully qualified attribute name:

Tool pap-admin • Administrator tool to manage the PAP –Policies management –PAP server management –PAP authorization management 11/04/2013 EGI CF 2013, Manchester 20 EMI INFSO-RI-261611 • Simple way to ban user • Simple way to create, edit and delete authorization policies

Tool pap-admin (cont. ) • List currently active policies: pap-admin list-policies • Ban/unban users: pap-admin ban subject “/C=org/O=ACME/CN=John Doe” pap-admin ban subject “CN=John Doe, O=ACME, C=org” pap-admin un-ban vo ”atlas“ • Add a generic permit policy: • And a lot more functionalites… 11/04/2013 EGI CF 2013, Manchester 21 EMI INFSO-RI-261611 pap-admin add-policy --resource “http: //grid. switch. ch/ce_1” --action “. *” permit fqan=”/atlas/production”

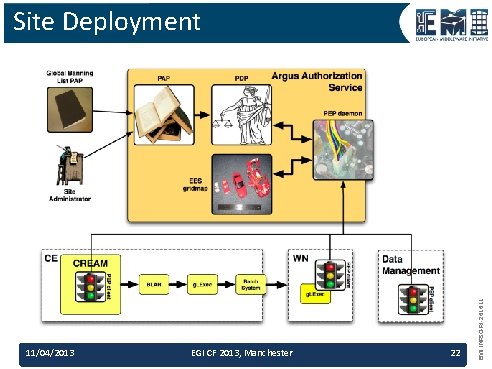
11/04/2013 EGI CF 2013, Manchester 22 EMI INFSO-RI-261611 Site Deployment

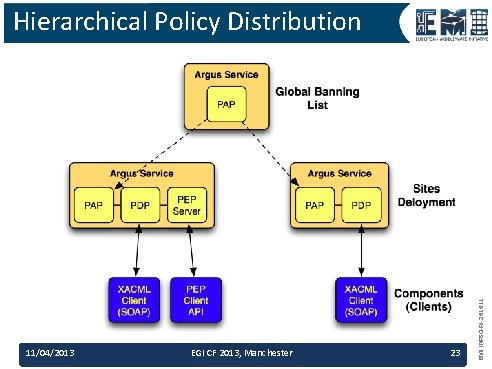
11/04/2013 EGI CF 2013, Manchester 23 EMI INFSO-RI-261611 Hierarchical Policy Distribution

Hierarchical Policy Distribution • Top PAP – Manages global banning list – Have to be trusted by site • Site PAP 11/04/2013 EGI CF 2013, Manchester 24 EMI INFSO-RI-261611 – Retrieves global banning list from top PAP – Merges it on top of local policies – FIRST MATCH rules applies in local PDP

Enable WLCG Global Banning • Add the WLCG PAP pap-admin apap WLCG argus. cern. ch "/DC=ch/DC=cern/OU=computers/CN=argus. cern. ch” • Set PAP order (top banning) pap-admin spo WLCG default • Enable the banning WLCG PAP pap-admin epap WLCG pap-admin lp -all 11/04/2013 EGI CF 2013, Manchester 25 EMI INFSO-RI-261611 • List all policies (WLCG and local ones)

• General documentation https: //twiki. cern. ch/twiki/bin/view/EGEE/Authoriz ation. Framework • PAP admin CLIhttps: //twiki. cern. ch/twiki/bin/view/EGEE/Auth. Z PAPCLI • Simplified Policy Language https: //twiki. cern. ch/twiki/bin/view/EGEE/Simplifie d. Policy. Language • Service Reference Card https: //twiki. cern. ch/twiki/bin/view/EMI/Argus. SRC 11/04/2013 EGI CF 2013, Manchester 26 EMI INFSO-RI-261611 Documentation

11/04/2013 EGI CF 2013, Manchester 28 EMI INFSO-RI-261611 DEMO

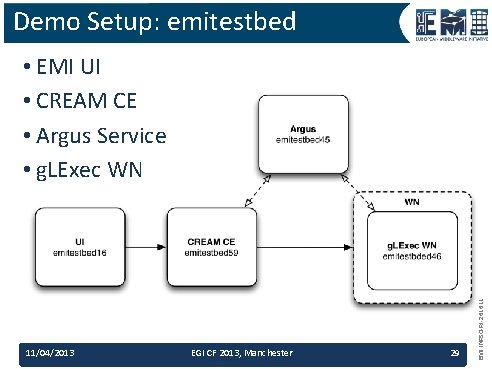
Demo Setup: emitestbed 11/04/2013 EGI CF 2013, Manchester 29 EMI INFSO-RI-261611 • EMI UI • CREAM CE • Argus Service • g. LExec WN

Demo Setup: Policies • Policies authorized jobs on CREAM CE and for g. LExec on the WN for a VO resource "http: //emitestbed. cnaf. infn. it/wn" { obligation "http: //glite. org/xacml/obligation/local-environment-map" {} action ". *" { rule permit { vo="testers. eu-emi. eu" } } } 11/04/2013 EGI CF 2013, Manchester 30 EMI INFSO-RI-261611 resource "http: //emitestbed. cnaf. infn. it/ce" { obligation "http: //glite. org/xacml/obligation/local-environment-map" {} action ". *" { rule permit { vo="testers. eu-emi. eu" } } }

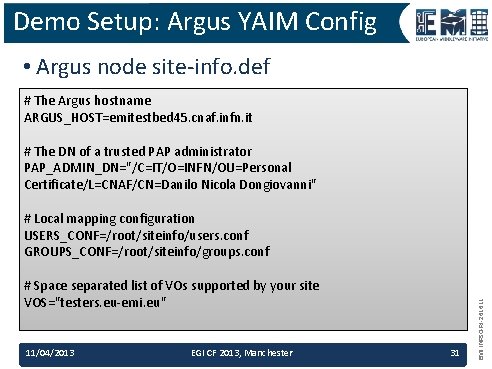
Demo Setup: Argus YAIM Config • Argus node site-info. def # The Argus hostname ARGUS_HOST=emitestbed 45. cnaf. infn. it # The DN of a trusted PAP administrator PAP_ADMIN_DN="/C=IT/O=INFN/OU=Personal Certificate/L=CNAF/CN=Danilo Nicola Dongiovanni" # Space separated list of VOs supported by your site VOS="testers. eu-emi. eu" 11/04/2013 EGI CF 2013, Manchester 31 EMI INFSO-RI-261611 # Local mapping configuration USERS_CONF=/root/siteinfo/users. conf GROUPS_CONF=/root/siteinfo/groups. conf

Demo Setup: CREAM YAIM Config • CREAM CE site-info. def • Enables Argus authorizations 11/04/2013 EGI CF 2013, Manchester 32 EMI INFSO-RI-261611 CEMON_HOST=emitestbed 59. cnaf. infn. it CREAM_DB_USER=tester CREAM_DB_PASSWORD=**** BLPARSER_HOST=emitestbed 59. cnaf. infn. it. . . USE_ARGUS=yes ARGUS_PEPD_ENDPOINTS=https: //emitestbed 45. cnaf. infn. it: 8154/authz CREAM_PEPC_RESOURCEID=http: //emitestbed. cnaf. infn. it/ce

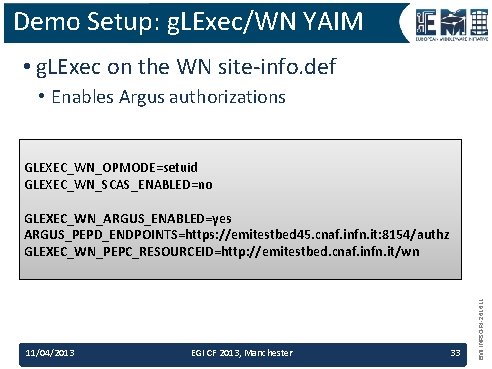
Demo Setup: g. LExec/WN YAIM • g. LExec on the WN site-info. def • Enables Argus authorizations GLEXEC_WN_OPMODE=setuid GLEXEC_WN_SCAS_ENABLED=no 11/04/2013 EGI CF 2013, Manchester 33 EMI INFSO-RI-261611 GLEXEC_WN_ARGUS_ENABLED=yes ARGUS_PEPD_ENDPOINTS=https: //emitestbed 45. cnaf. infn. it: 8154/authz GLEXEC_WN_PEPC_RESOURCEID=http: //emitestbed. cnaf. infn. it/wn

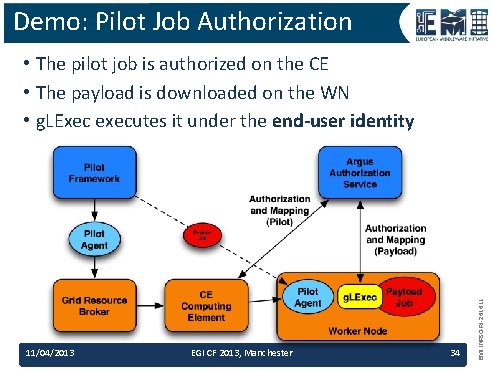
Demo: Pilot Job Authorization 11/04/2013 EGI CF 2013, Manchester 34 EMI INFSO-RI-261611 • The pilot job is authorized on the CE • The payload is downloaded on the WN • g. LExec executes it under the end-user identity