Are Friends of My Friends Too Social Limitations







- Slides: 19

Are Friends of My Friends Too Social? Limitations of Location Privacy in a Socially-Connected World Boris Aronov NYU Alon Efrat University of Arizona Ming Li University of Arizona Jie Gao Stony Brook University Joseph S. B. Mitchell Stony Brook University Valentin Polishchuk Linko ping University Boyang Wang University of Cincinnati Hanyu Quan Xidian University Jiaxin Ding Stony Brook University Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

• In this talk we will first discuss accurate localization first as a positive desired property. • Then will formulate potential privacy bridging, that suggest counter attacks. Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

Our model Mobile agents are moving in an environment. For example • • Vehicles on a road Customers in a mall (eg Bluetooth) Hiker in rain forest Constructions employees. In all cases, agents might receive GPS signal and might publish their locations. Want to be able to know agents’ locations at every time (as accurately as possible) Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

Our model - cont. • Agent ai shares (intentionally or not) lists of his/hers events. All timestamped. • Two types of events 1. (ai , x, y, t). A GPS event – time and location where agent ai received a GPS signal. 2. (aj , ak , t). A Meeting event between agent ai and other agent ak v Easily extendable to be within range of each other. • Also for each agent ai we are given the maximum speed vj he/she might move. (No lower bound). => If agent j was involved in two events, and they have occurred at times t and t’, are geographically at distance ≤|t−t′|vj away from each other. Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

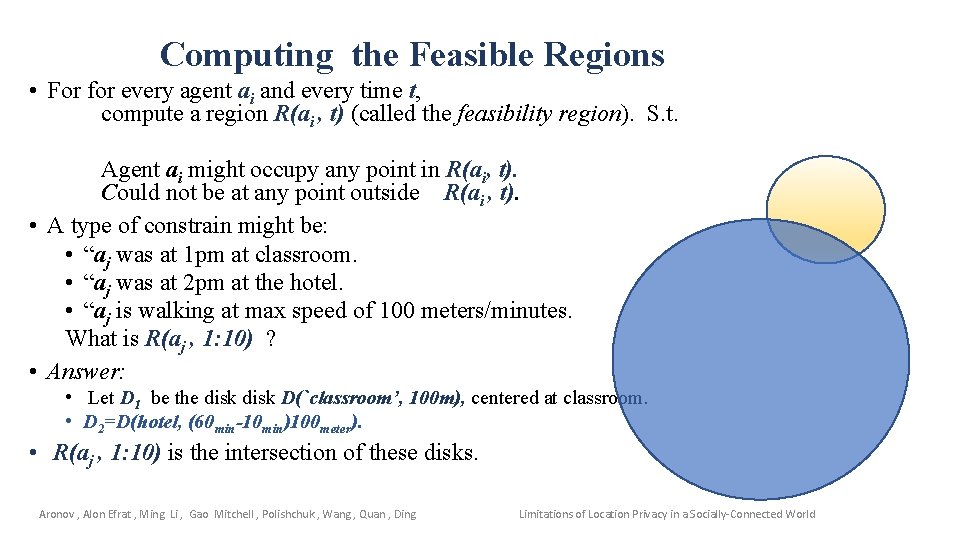
Computing the Feasible Regions • For for every agent ai and every time t, compute a region R(ai , t) (called the feasibility region). S. t. Agent ai might occupy any point in R(ai, t). Could not be at any point outside R(ai , t). • A type of constrain might be: • “aj was at 1 pm at classroom. • “aj was at 2 pm at the hotel. • “aj is walking at max speed of 100 meters/minutes. What is R(aj , 1: 10) ? • Answer: • Let D 1 be the disk D(`classroom’, 100 m), centered at classroom. • D 2=D(hotel, (60 min-10 min)100 meter). • R(aj , 1: 10) is the intersection of these disks. Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

Characterizing R(aj , t)? • If we set variables (xjyj) to every event j • The constrains about maximum distances between events are just upper bounding dist( (xiyi), (xk yk) ). • This is a convex programming problem. • So R(aj , t) is just a projection of the feasible solutions onto 2 D plane. • Conclusion: R(aj , t) is convex Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

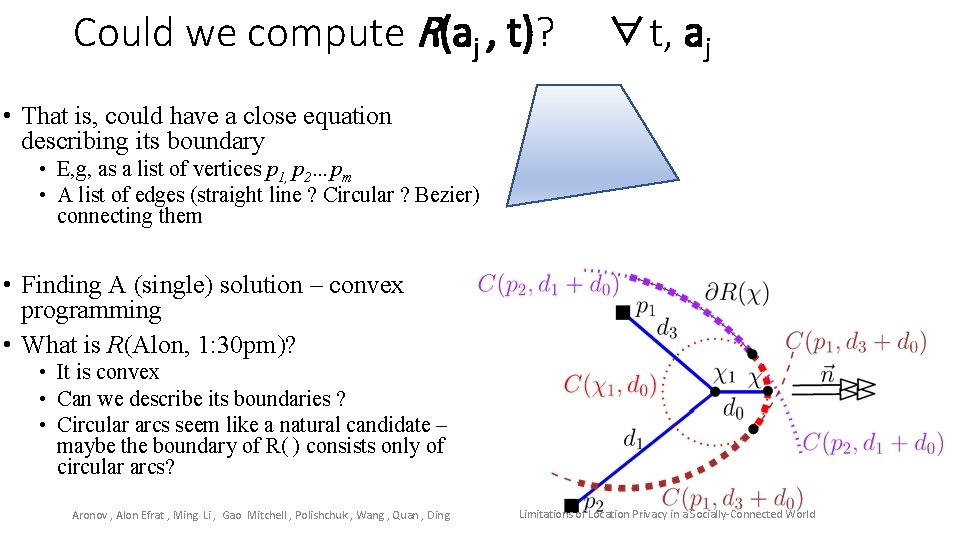
Could we compute R(aj , t)? ∀t, aj • That is, could have a close equation describing its boundary • E, g, as a list of vertices p 1, p 2…pm • A list of edges (straight line ? Circular ? Bezier) connecting them • Finding A (single) solution – convex programming • What is R(Alon, 1: 30 pm)? • It is convex • Can we describe its boundaries ? • Circular arcs seem like a natural candidate – maybe the boundary of R( ) consists only of circular arcs? Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

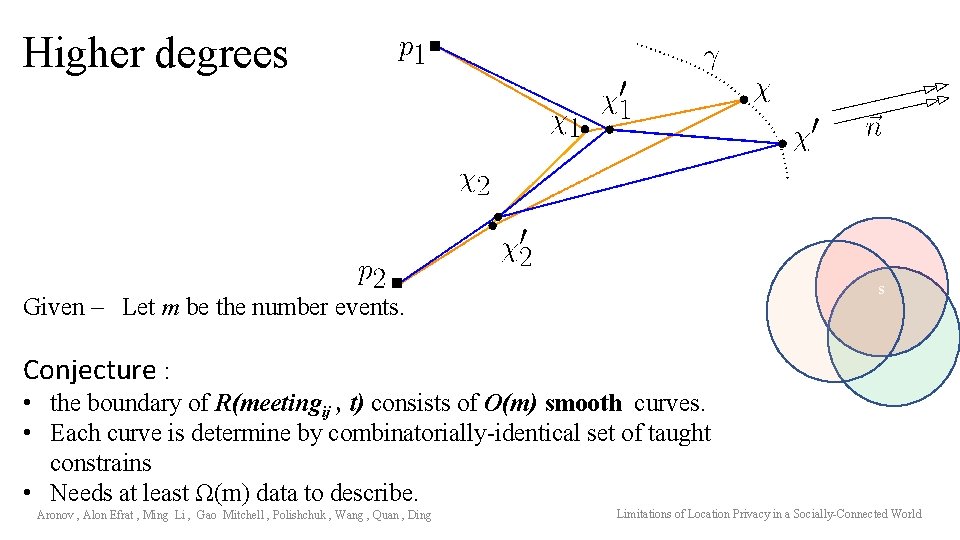
Higher degrees s Given – Let m be the number events. Conjecture : • the boundary of R(meetingij , t) consists of O(m) smooth curves. • Each curve is determine by combinatorially-identical set of taught constrains • Needs at least Ω(m) data to describe. Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

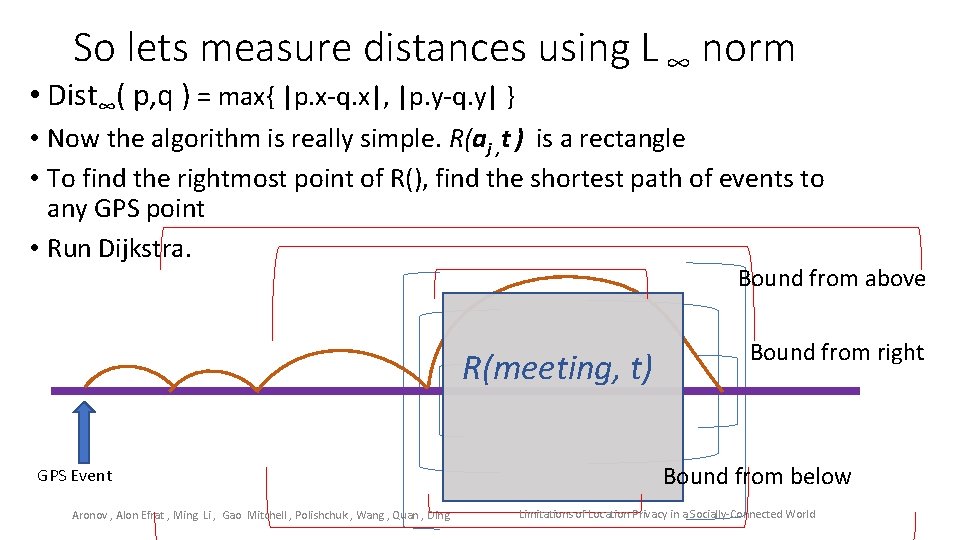
So lets measure distances using L ∞ norm • Dist∞( p, q ) = max{ |p. x-q. x|, |p. y-q. y| } • Now the algorithm is really simple. R(aj , t ) is a rectangle • To find the rightmost point of R(), find the shortest path of events to any GPS point • Run Dijkstra. Bound from above R(meeting, t) GPS Event Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Bound from right Bound from below Limitations of Location Privacy in a Socially-Connected World

…. And this gives a universal solution • Essentially 4 calls to Dijkstra algorithm provides a consistent uncertain regions for all agents, and for all times R(Mark, 1 pm) R(John, 10 am) R(Zod, 2 pm) GPS Event Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

Aronov , Efrat , Li , Gao Mitchell, Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

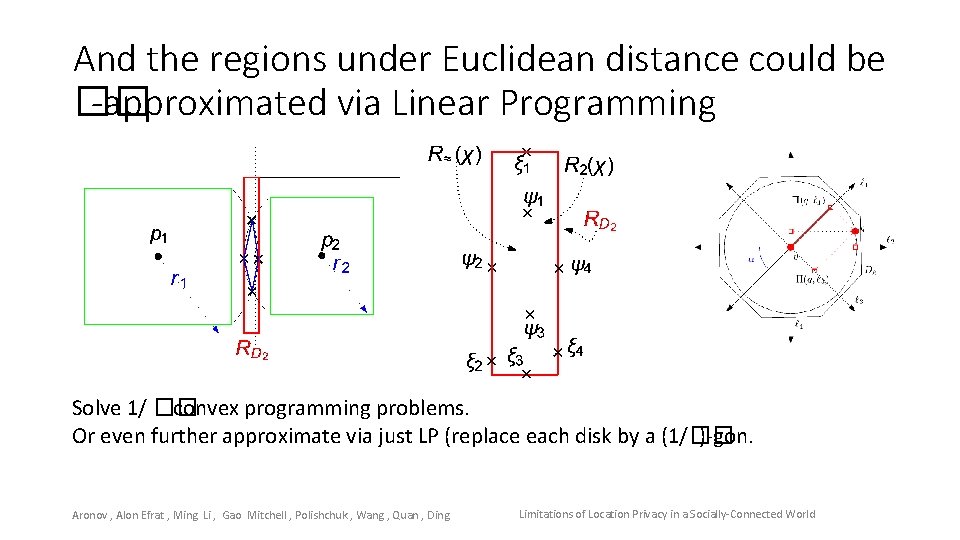
And the regions under Euclidean distance could be �� -approximated via Linear Programming Solve 1/ �� convex programming problems. Or even further approximate via just LP (replace each disk by a (1/�� )-gon. Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

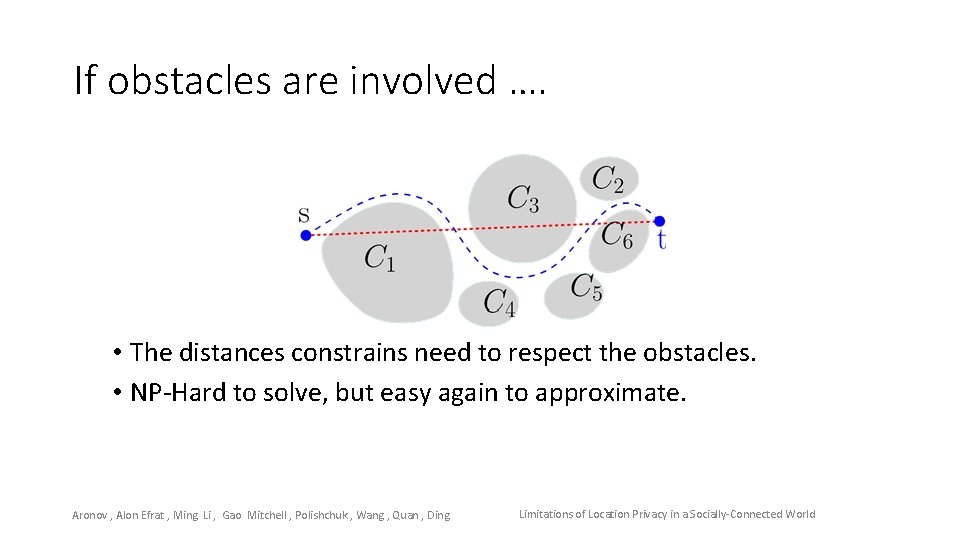
If obstacles are involved …. • The distances constrains need to respect the obstacles. • NP-Hard to solve, but easy again to approximate. Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

Good news: We could find locations efficiently Bad news: We could find locations efficiently • Data could be collected and leaked from Smart building, smart city, Location-Based services… • an increasing number of wireless devices, both static and mobile, populating the physical space. • Location and trajectory data can reveal personally sensitive information: • Frequently visited locations: home or work addresses. • Unique signatures: 4 spatial temporal data points can be used to identify a user from a database of 1. 3 million users. [Krumm. 2007] Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

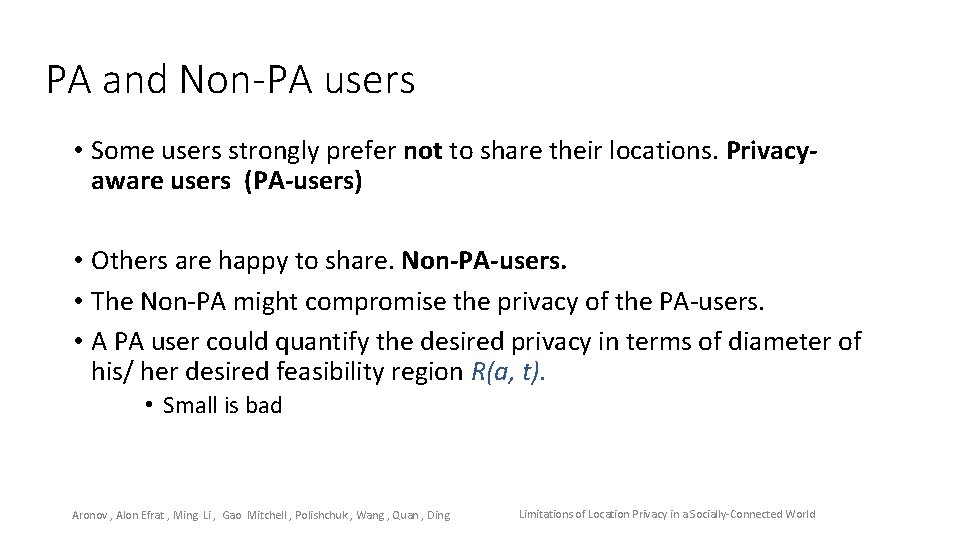
PA and Non-PA users • Some users strongly prefer not to share their locations. Privacyaware users (PA-users) • Others are happy to share. Non-PA-users. • The Non-PA might compromise the privacy of the PA-users. • A PA user could quantify the desired privacy in terms of diameter of his/ her desired feasibility region R(a, t). • Small is bad Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

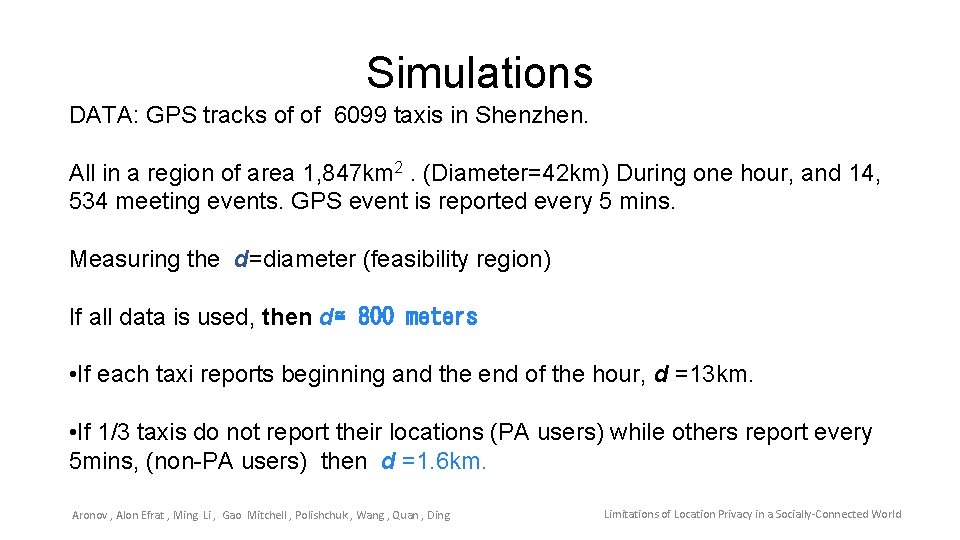
Simulations DATA: GPS tracks of of 6099 taxis in Shenzhen. All in a region of area 1, 847 km 2. (Diameter=42 km) During one hour, and 14, 534 meeting events. GPS event is reported every 5 mins. Measuring the d=diameter (feasibility region) If all data is used, then d≅ 800 meters • If each taxi reports beginning and the end of the hour, d =13 km. • If 1/3 taxis do not report their locations (PA users) while others report every 5 mins, (non-PA users) then d =1. 6 km. Aronov , Alon Efrat , Ming Li , Gao Mitchell , Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

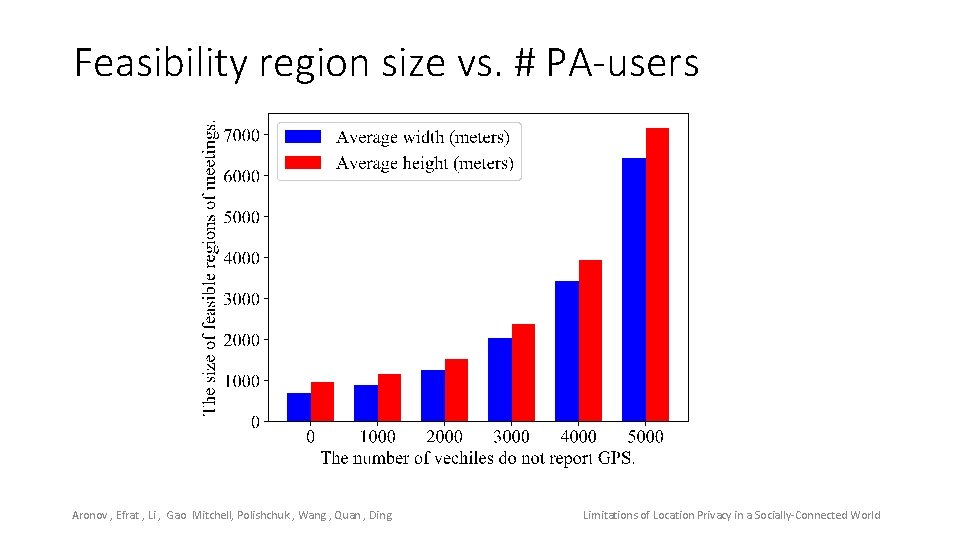
Feasibility region size vs. # PA-users Aronov , Efrat , Li , Gao Mitchell, Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

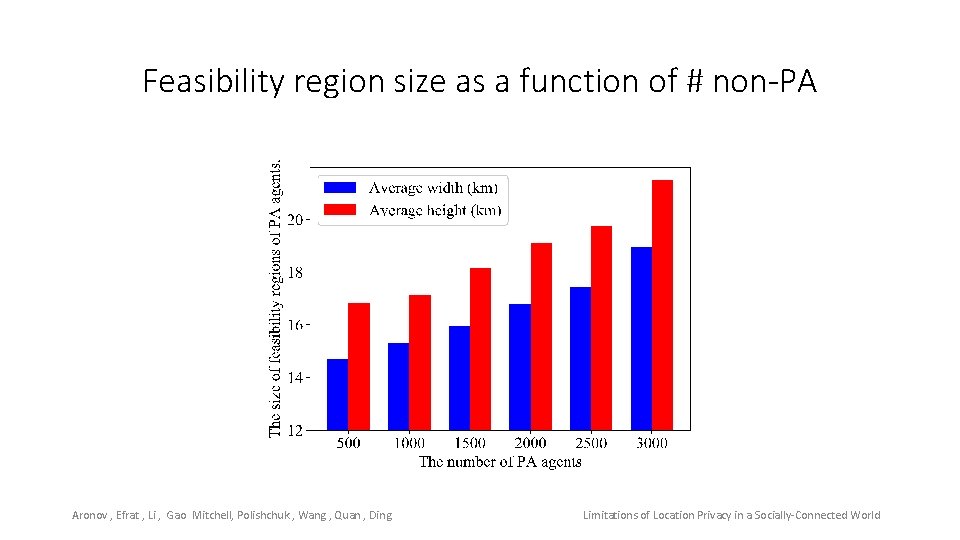
Feasibility region size as a function of # non-PA Aronov , Efrat , Li , Gao Mitchell, Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World

Feasibility region of PA-only Aronov , Efrat , Li , Gao Mitchell, Polishchuk , Wang , Quan , Ding Limitations of Location Privacy in a Socially-Connected World
 Insidan region jh
Insidan region jh Kahoot quantifiers
Kahoot quantifiers Too broad and too narrow examples
Too broad and too narrow examples Too broad too narrow
Too broad too narrow Broad and specific topic examples
Broad and specific topic examples Högkonjuktur inflation
Högkonjuktur inflation Too broad and too narrow examples
Too broad and too narrow examples Too big too small just right
Too big too small just right Too foreign for home too foreign for here
Too foreign for home too foreign for here Too blessed to be stressed too anointed to be disappointed
Too blessed to be stressed too anointed to be disappointed Little friends may prove great friends
Little friends may prove great friends Pigou condition of maximum social advantage
Pigou condition of maximum social advantage Social thinking adalah
Social thinking adalah Social thinking social influence social relations
Social thinking social influence social relations Quirk vs kachru
Quirk vs kachru Limitations of the beer lambert law
Limitations of the beer lambert law Limitations of remote sensing
Limitations of remote sensing Auxochrome
Auxochrome Hydraulic conductivity of soil formula
Hydraulic conductivity of soil formula Limitations of ict
Limitations of ict