Analysis of Security Protocols John C Mitchell Stanford

![Recent Language Approach l l [AG 97] Write protocol in process calculus Express security Recent Language Approach l l [AG 97] Write protocol in process calculus Express security](https://slidetodoc.com/presentation_image_h/04292d804e9fce65ca065401dd9ba151/image-4.jpg)



![Observing Probabilistic Process l Observations w Compare |Prob[P “yes”] - Prob[ Q “yes”] | Observing Probabilistic Process l Observations w Compare |Prob[P “yes”] - Prob[ Q “yes”] |](https://slidetodoc.com/presentation_image_h/04292d804e9fce65ca065401dd9ba151/image-13.jpg)


![Protocol P [Diffie, Hellman, El. Gamal] ga mod p A gb mod p B Protocol P [Diffie, Hellman, El. Gamal] ga mod p A gb mod p B](https://slidetodoc.com/presentation_image_h/04292d804e9fce65ca065401dd9ba151/image-16.jpg)
- Slides: 20

Analysis of Security Protocols John C. Mitchell Stanford University (V)

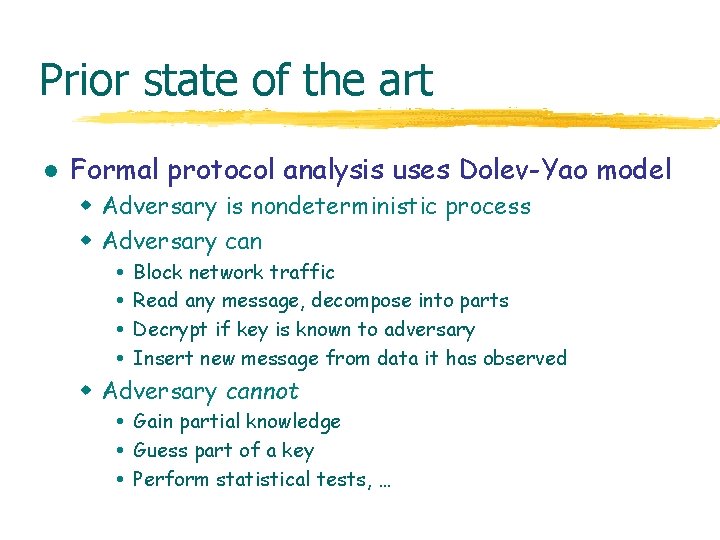
Prior state of the art l Formal protocol analysis uses Dolev-Yao model w Adversary is nondeterministic process w Adversary can Block network traffic Read any message, decompose into parts Decrypt if key is known to adversary Insert new message from data it has observed w Adversary cannot Gain partial knowledge Guess part of a key Perform statistical tests, …

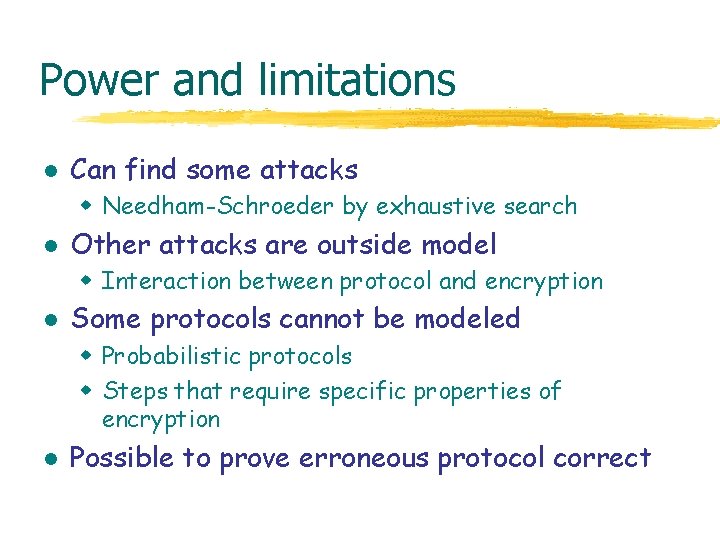
Power and limitations l Can find some attacks w Needham-Schroeder by exhaustive search l Other attacks are outside model w Interaction between protocol and encryption l Some protocols cannot be modeled w Probabilistic protocols w Steps that require specific properties of encryption l Possible to prove erroneous protocol correct
![Recent Language Approach l l AG 97 Write protocol in process calculus Express security Recent Language Approach l l [AG 97] Write protocol in process calculus Express security](https://slidetodoc.com/presentation_image_h/04292d804e9fce65ca065401dd9ba151/image-4.jpg)
Recent Language Approach l l [AG 97] Write protocol in process calculus Express security using observational equivalence w Standard relation from programming language theory P Q iff for all contexts C[ ], same observations about C[P] and C[Q] w Context (environment) represents adversary l Use proof rules for to prove security w Protocol is secure if no adversary can distinguish it from some idealized version of the protocol

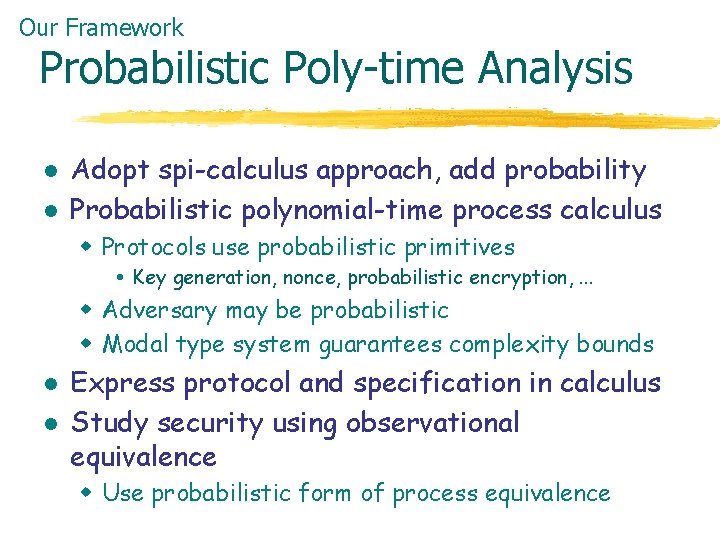
Our Framework Probabilistic Poly-time Analysis l l Adopt spi-calculus approach, add probability Probabilistic polynomial-time process calculus w Protocols use probabilistic primitives Key generation, nonce, probabilistic encryption, . . . w Adversary may be probabilistic w Modal type system guarantees complexity bounds l l Express protocol and specification in calculus Study security using observational equivalence w Use probabilistic form of process equivalence

Technical Challenges l Language for prob. poly-time functions w Extend Hofmann language with rand l Replace nondeterminism with probability w Otherwise adversary is too strong. . . l Define probabilistic equivalence w Related to poly-time statistical tests. . . l Develop specification by equivalence w Several examples carried out l Proof systems for probabilistic equivalence w Goal for the future

Example protocol in process calc l “Notation found in the literature” A B: { m } K B A: { m+1 } l K Process calculus with cryptographic primitives output on port AB let k = new_key(n) in let m = pick_a_number(n) in AB encrypt(k, m) | AB(x). BA encrypt(k, decrypt(k, x)+1) end not m This form makes assumptions and response explicit

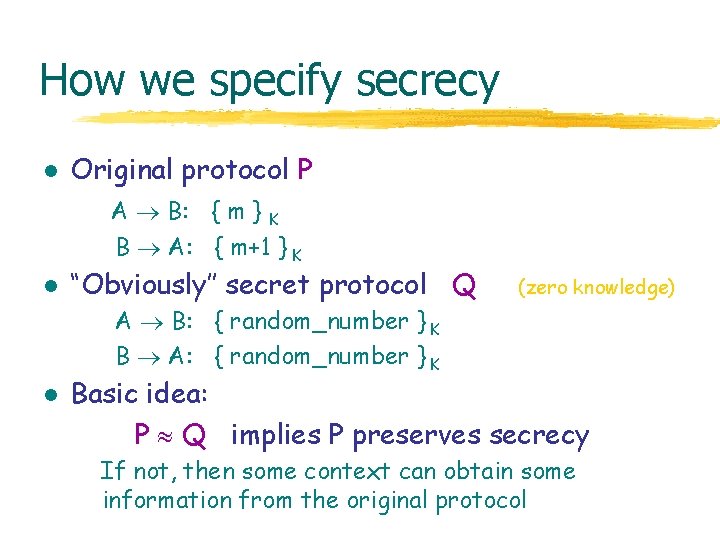
How we specify secrecy l Original protocol P A B: { m } K B A: { m+1 } K l “Obviously’’ secret protocol Q (zero knowledge) A B: { random_number } K B A: { random_number } K l Basic idea: P Q implies P preserves secrecy If not, then some context can obtain some information from the original protocol

Nondeterminism is traditional, but. . . l Nondeterminism is a useful idealization w Classical disguised as a computational primitive w Expresses extreme “good luck” or “bad luck” Nondeterministic algorithm for traveling salesman • “Guess” a path and check that it is correct Nondeterministic semantics for parallel composition • Treat any possible interleaving as significantly possible • Appropriate for “worst case” correctness l Not an intrinsic property of system itself

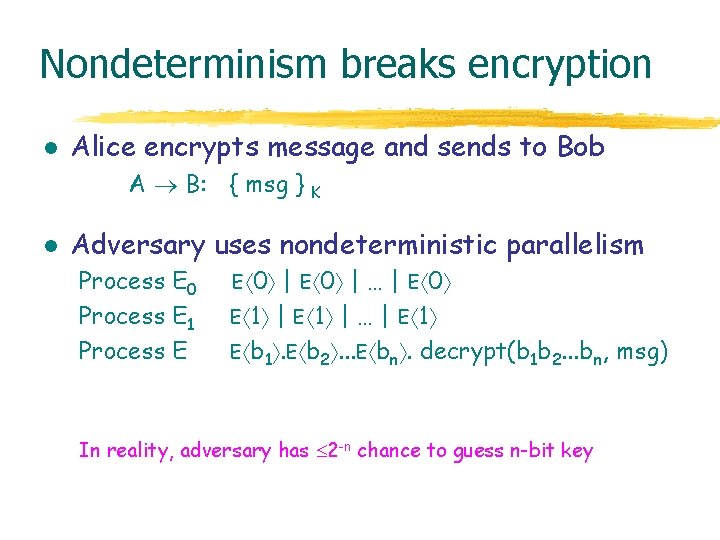
Nondeterminism breaks encryption l Alice encrypts message and sends to Bob A B: { msg } l K Adversary uses nondeterministic parallelism Process E 0 Process E 1 Process E | E 0 | … | E 0 E 1 | … | E 1 E b 1. E b 2. . . E bn. decrypt(b 1 b 2. . . bn, msg) E 0 In reality, adversary has 2 -n chance to guess n-bit key

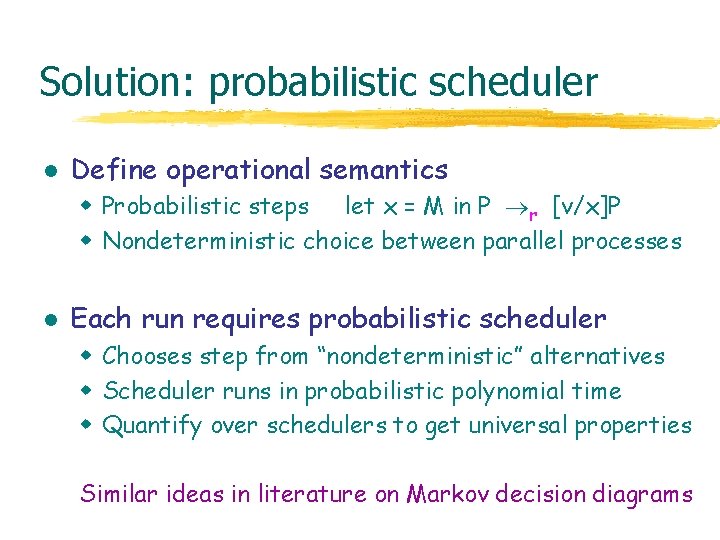
Solution: probabilistic scheduler l Define operational semantics w Probabilistic steps let x = M in P r [v/x]P w Nondeterministic choice between parallel processes l Each run requires probabilistic scheduler w Chooses step from “nondeterministic” alternatives w Scheduler runs in probabilistic polynomial time w Quantify over schedulers to get universal properties Similar ideas in literature on Markov decision diagrams

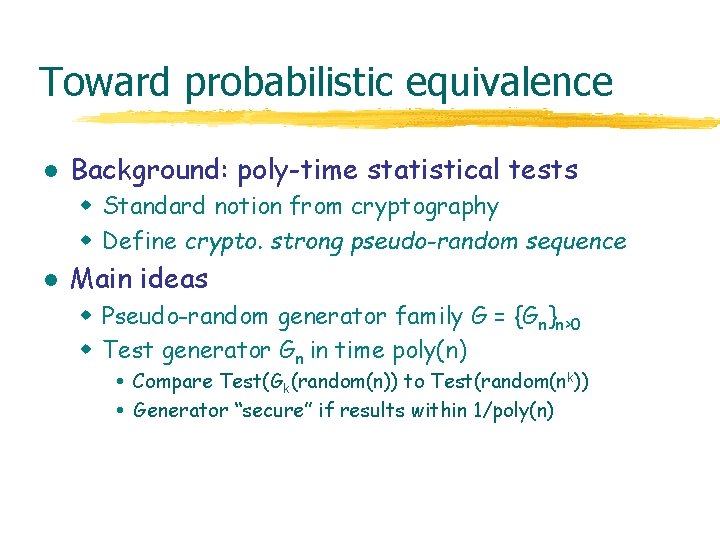
Toward probabilistic equivalence l Background: poly-time statistical tests w Standard notion from cryptography w Define crypto. strong pseudo-random sequence l Main ideas w Pseudo-random generator family G = {Gn}n>0 w Test generator Gn in time poly(n) Compare Test(Gk(random(n)) to Test(random(nk)) Generator “secure” if results within 1/poly(n)
![Observing Probabilistic Process l Observations w Compare ProbP yes Prob Q yes Observing Probabilistic Process l Observations w Compare |Prob[P “yes”] - Prob[ Q “yes”] |](https://slidetodoc.com/presentation_image_h/04292d804e9fce65ca065401dd9ba151/image-13.jpg)
Observing Probabilistic Process l Observations w Compare |Prob[P “yes”] - Prob[ Q “yes”] | < w How small is small ? Less than 1/2, 1/4, … ? (not equiv relation for fixed ) Vanishingly small ? How fast should 0 ? As a function of what? l Cryptographic protocols w Use encryption keys of a certain length Protocol is family { Pn } n>0 indexed by key length w Increasing key length increasing security

Probabilistic Observational Equiv l Processes P, Q are -indistinguishable P Q if contexts C[ ]. observations v. |Prob[C[P] v] - Prob[C[Q] v] | < l Asymptotically within f Process, context families { Pn } n>0 { Qn } n>0 { Cn } n>0 P f Q if contexts C[ ]. obs v. n 0. n> n 0. | Prob[Cn[Pn] v] - Prob[Cn[Qn] v] | < f(n) l Asymptotically polynomially indistinguishable P Q if P f Q for every polynomial f(n) = 1/p(n) Final def’n gives robust equivalence

Basic example l Sequence generated from random seed Pn: let b = nk-bit sequence generated from n random bits in PUBLIC b end l Truly random sequence Qn: let b = sequence of nk random bits in PUBLIC b end l P is crypto strong pseudo-random generator P Q
![Protocol P Diffie Hellman El Gamal ga mod p A gb mod p B Protocol P [Diffie, Hellman, El. Gamal] ga mod p A gb mod p B](https://slidetodoc.com/presentation_image_h/04292d804e9fce65ca065401dd9ba151/image-16.jpg)
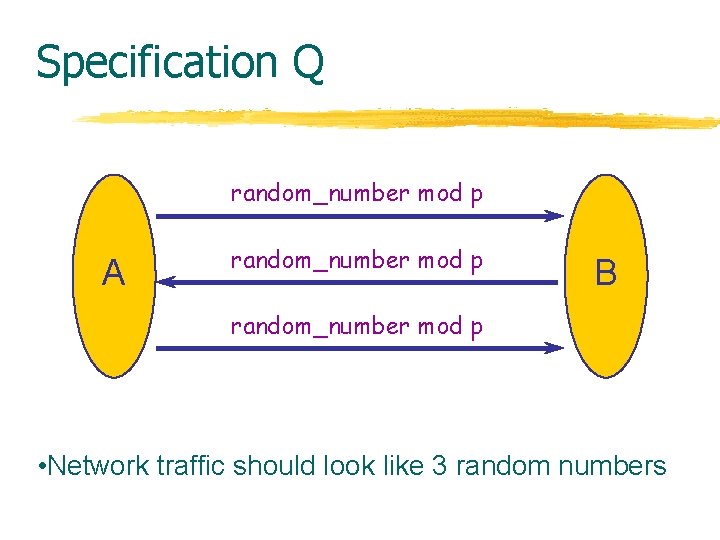
Protocol P [Diffie, Hellman, El. Gamal] ga mod p A gb mod p B msg * gab mod p • Prime p and generator g of Zp are public • Passive eavesdropper has small chance at msg

Specification Q random_number mod p A random_number mod p B random_number mod p • Network traffic should look like 3 random numbers

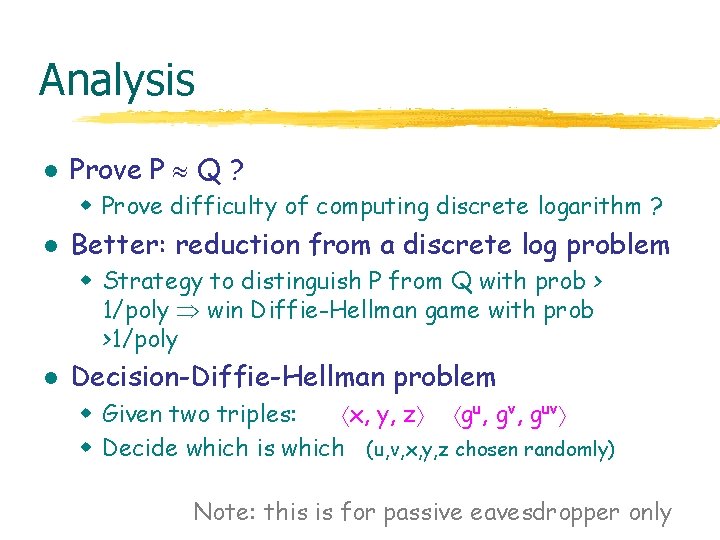
Analysis l Prove P Q ? w Prove difficulty of computing discrete logarithm ? l Better: reduction from a discrete log problem w Strategy to distinguish P from Q with prob > 1/poly win Diffie-Hellman game with prob >1/poly l Decision-Diffie-Hellman problem w Given two triples: x, y, z gu, gv, guv w Decide which is which (u, v, x, y, z chosen randomly) Note: this is for passive eavesdropper only

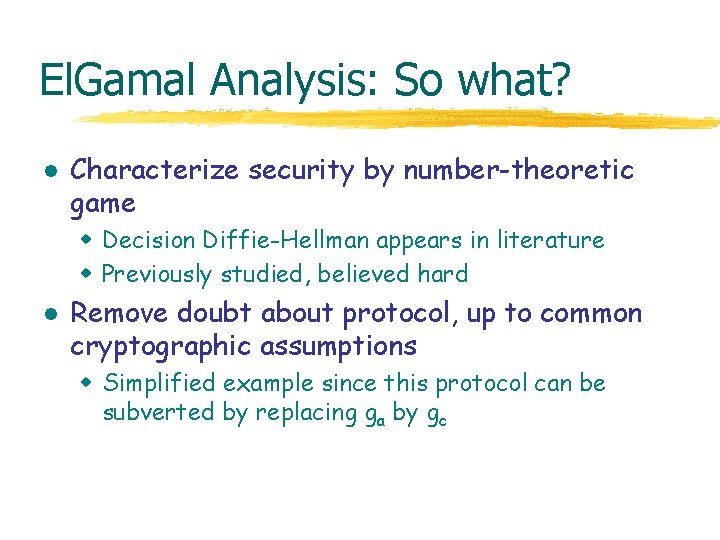
El. Gamal Analysis: So what? l Characterize security by number-theoretic game w Decision Diffie-Hellman appears in literature w Previously studied, believed hard l Remove doubt about protocol, up to common cryptographic assumptions w Simplified example since this protocol can be subverted by replacing ga by gc

Current state of project l Better foundations for protocol analysis ? w Determine crypto requirements of protocols ! l Probabilistic ptime language w Extended Hofmann language with rand l Probabilistic process framework w replaced nondeterminism with rand w equivalence based on ptime statistical tests l l l Specifications of secrecy, authenticity Simple examples Work in progress. . .
 John mitchell stanford
John mitchell stanford John mitchell stanford
John mitchell stanford John mitchell stanford
John mitchell stanford Privatesecurity
Privatesecurity Network security protocols
Network security protocols Network security protocols
Network security protocols The most complex part of tls is the
The most complex part of tls is the Mitchell centre for social network analysis
Mitchell centre for social network analysis Stanford web security
Stanford web security Stanford computer security
Stanford computer security Stanford security awareness
Stanford security awareness Turbine banki-mitchell ou crossflow
Turbine banki-mitchell ou crossflow Nickole mitchell
Nickole mitchell Basil mitchell parable of the partisan
Basil mitchell parable of the partisan Social crm mitchell1
Social crm mitchell1 Retinopatia hipertensiva kwb
Retinopatia hipertensiva kwb Clasificacion de wong mitchell
Clasificacion de wong mitchell Classification de mitchell ostéonécrose
Classification de mitchell ostéonécrose Mitchell daysh
Mitchell daysh 4 table mitchell movement
4 table mitchell movement Mitchell on demand pro
Mitchell on demand pro