An Intro to Network Analyzers References Introduction to







- Slides: 23

An Intro to Network Analyzers References: • “Introduction to Wiresharkl”, Dr. Farid Farahmand, Fall 2014 • "Packet analyzer", Wikipedia, March 2013. . • “Wireshark User’s Guide”, For Wireshark 1. 99. • “Wireshark Installation & packet Chapter”, August 2011.

Network Analysis & Sniffing • Process of capturing, decoding, & analyzing network traffic – Why is the network slow – What is the network traffic pattern – How is the traffic being shared between nodes • Also known as – traffic analysis, protocol analysis, sniffing, packet analysis, eavesdropping*, etc. *Listen secretly to what is said in private! 2

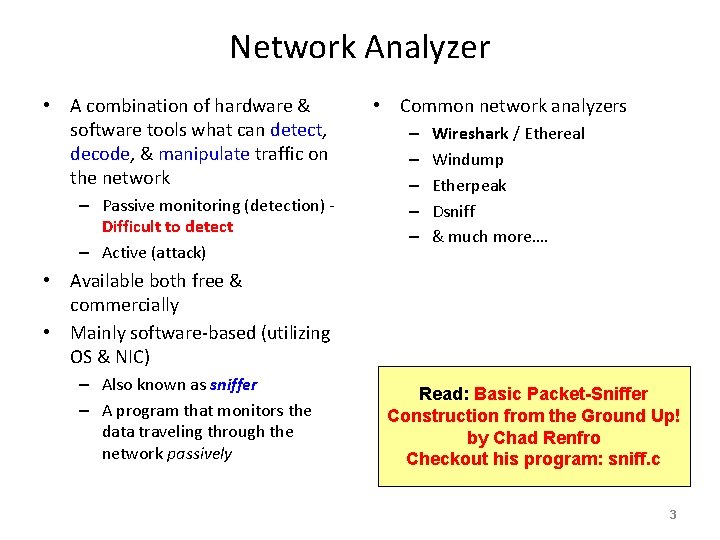
Network Analyzer • A combination of hardware & software tools what can detect, decode, & manipulate traffic on the network – Passive monitoring (detection) Difficult to detect – Active (attack) • Common network analyzers – – – Wireshark / Ethereal Windump Etherpeak Dsniff & much more…. • Available both free & commercially • Mainly software-based (utilizing OS & NIC) – Also known as sniffer – A program that monitors the data traveling through the network passively Read: Basic Packet-Sniffer Construction from the Ground Up! by Chad Renfro Checkout his program: sniff. c 3

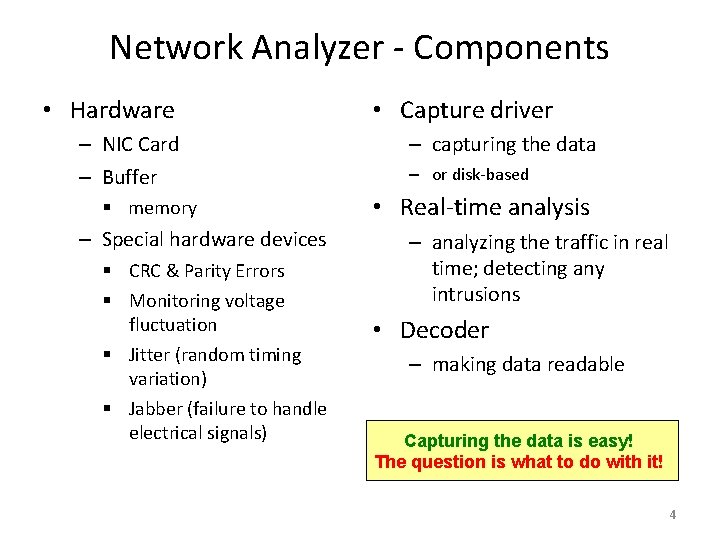
Network Analyzer - Components • Hardware – NIC Card – Buffer § memory – Special hardware devices § CRC & Parity Errors § Monitoring voltage fluctuation § Jitter (random timing variation) § Jabber (failure to handle electrical signals) • Capture driver – capturing the data – or disk-based • Real-time analysis – analyzing the traffic in real time; detecting any intrusions • Decoder – making data readable Capturing the data is easy! The question is what to do with it! 4

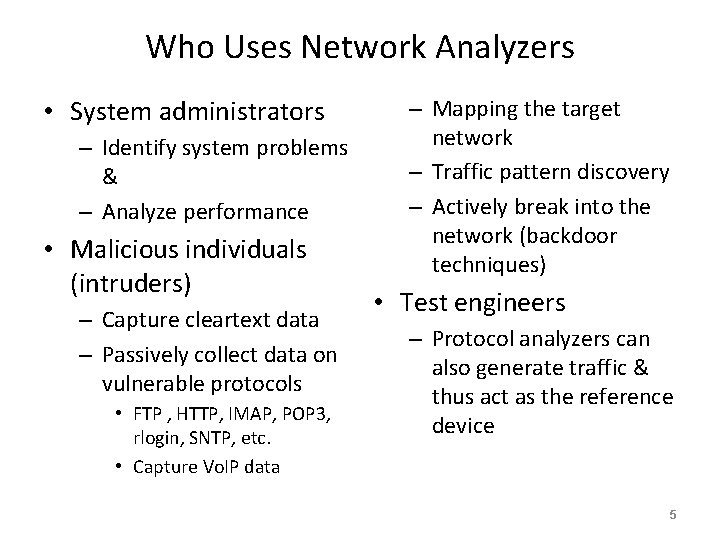
Who Uses Network Analyzers • System administrators – Identify system problems & – Analyze performance • Malicious individuals (intruders) – Capture cleartext data – Passively collect data on vulnerable protocols • FTP , HTTP, IMAP, POP 3, rlogin, SNTP, etc. • Capture Vo. IP data – Mapping the target network – Traffic pattern discovery – Actively break into the network (backdoor techniques) • Test engineers – Protocol analyzers can also generate traffic & thus act as the reference device 5

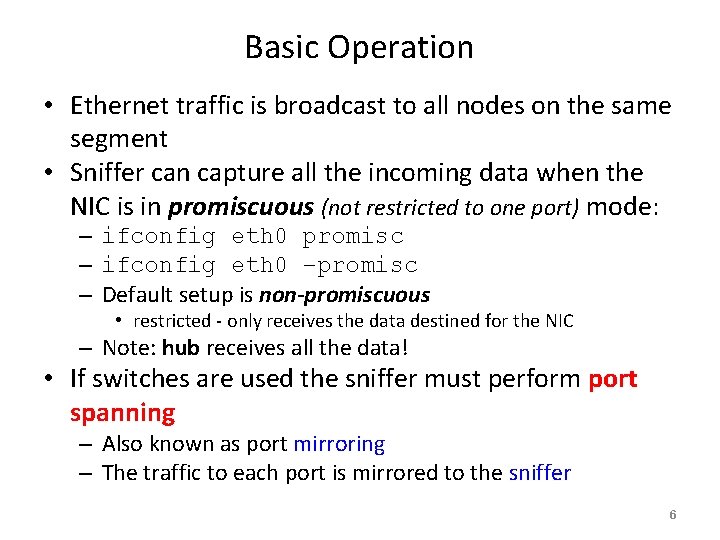
Basic Operation • Ethernet traffic is broadcast to all nodes on the same segment • Sniffer can capture all the incoming data when the NIC is in promiscuous (not restricted to one port) mode: – ifconfig eth 0 promisc – ifconfig eth 0 –promisc – Default setup is non-promiscuous • restricted - only receives the data destined for the NIC – Note: hub receives all the data! • If switches are used the sniffer must perform port spanning – Also known as port mirroring – The traffic to each port is mirrored to the sniffer 6

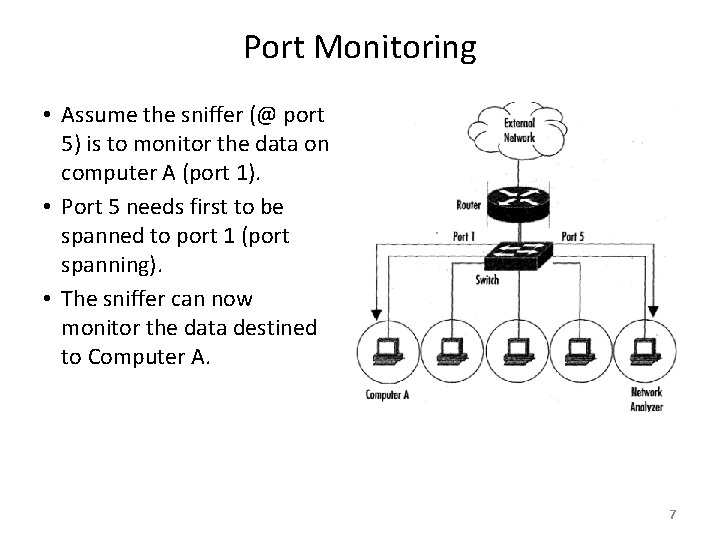
Port Monitoring • Assume the sniffer (@ port 5) is to monitor the data on computer A (port 1). • Port 5 needs first to be spanned to port 1 (port spanning). • The sniffer can now monitor the data destined to Computer A. 7

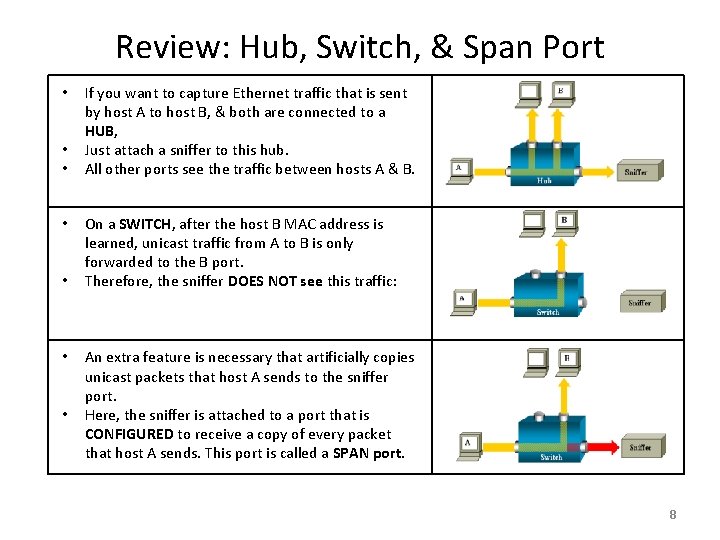
Review: Hub, Switch, & Span Port • • If you want to capture Ethernet traffic that is sent by host A to host B, & both are connected to a HUB, Just attach a sniffer to this hub. All other ports see the traffic between hosts A & B. On a SWITCH, after the host B MAC address is learned, unicast traffic from A to B is only forwarded to the B port. Therefore, the sniffer DOES NOT see this traffic: An extra feature is necessary that artificially copies unicast packets that host A sends to the sniffer port. Here, the sniffer is attached to a port that is CONFIGURED to receive a copy of every packet that host A sends. This port is called a SPAN port. 8

Protecting Against - Sniffers • Spoofing the MAC is often referred to changing the MAC address (in Linux: ) – – ifconfig eth 0 down ifconfig eth 0 hw ether 00: 01: 02: 03: 04: 05 ifconfig eth 0 up Register the new MAC address by broadcasting it • ping –c 1 –b 192. 168. 1. 1 • To detect a sniffer (Linux) – Download Promisc. c) – ifconfig -a (search for promisc) – ip link (search for promisc) • To detect a sniffer (Windows) – Download Promisc. Detect Remember: 00: 01: 02: 03: 04: 05 MAC address (HWaddr)= Vender Address + Unique NIC # 9

Protecting Against Sniffers • Using switches can help • Use encryption Remember: Never use unauthorized Sniffers at work! – Making the intercepted data unreadable – Note: in many protocols the packet headers are clear text! • VPNs use encryption & authorization for secure communications – VPN Methods • Secure Shell (SSH): headers are not encrypted • Secure Sockets Layer (SSL): high network level packet security; headers are not encrypted • IPsec: Encrypted headers but does not use TCP or UDP 10

What is Wireshark? • Formerly called Ethereal • An open source program – free with many features • • Remember: You must have a good understanding of the network before you use Sniffers effectively! Decodes over 750 protocols Compatible with many other sniffers Plenty of online resources are available Supports command-line & graphical user interfaces (CLI, GUI) – TSHARK (CLI) has three components • Editcap – similar to “Save As” to translate the format of captured packets • Mergecap – combines multiple saved captured files • Text 2 pcap – ASCII Hexdump captures & writes the data into a libpcap output file 11

Installing Wireshark • Download the Wireshark program from – www. wireshark. org/download. html , OR – UBUNDU 14. 04 Webpage – Requires to install capture drivers • monitor ports & capture all traveling packets 12

Installing Wireshark • If you did not succeed, do the following. • On UBUNTU screen go to the “Dash board” – Search for “Wireshark” & Install, OR – Go to Firefox in UBUNTU & Google “Wireshark for Ubuntu 14. 04” & follow the instruction. • You can also download it using a “Terminal” by command: sudo apt-get install wireshark • If you could not see any interface for capturing, with the current configuration, you need “root” privileges to capture traffic with Wireshark (or dumpcap, for that matter). • Here are the commands sudo -s usermod -a -G wireshark your-username chgrp wireshark /usr/bin/dumpcap chmod 4750 /usr/bin/dumpcap You can safely run Wireshark to inspect, edit or filter packet dumps without root privileges, e. g. , wireshark -i eth 0 -c 5 13

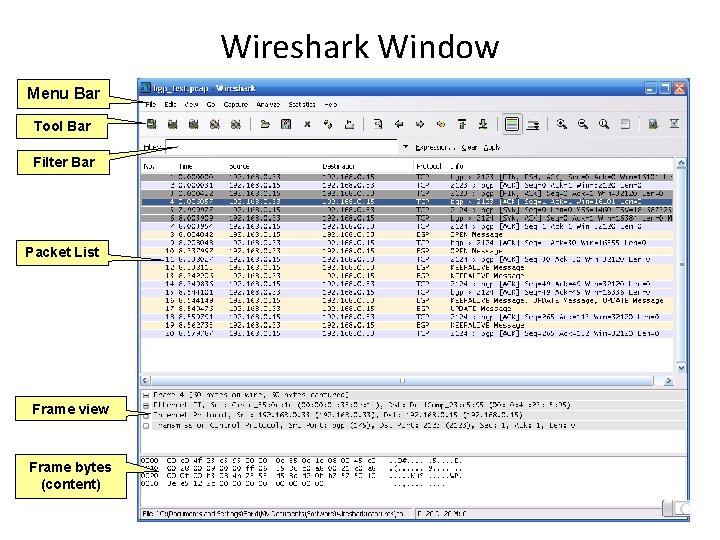
Wireshark Window Menu Bar Tool Bar Filter Bar Packet List Frame view Frame bytes (content) 14

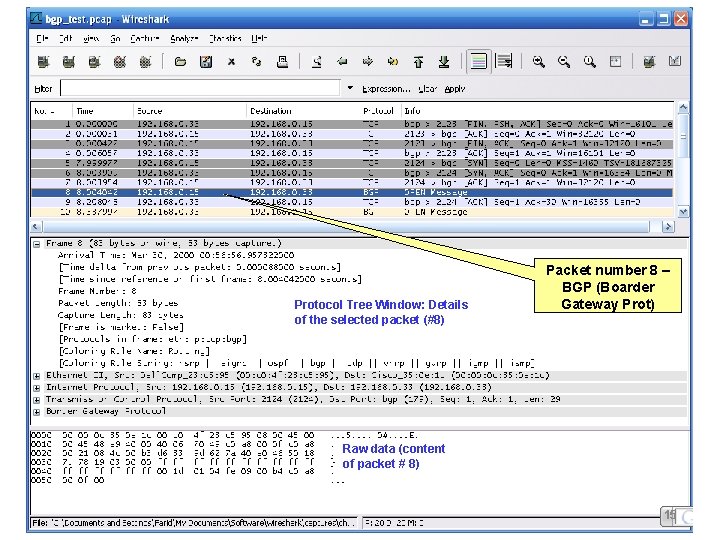
Protocol Tree Window: Details of the selected packet (#8) Packet number 8 – BGP (Boarder Gateway Prot) Raw data (content of packet # 8) 15

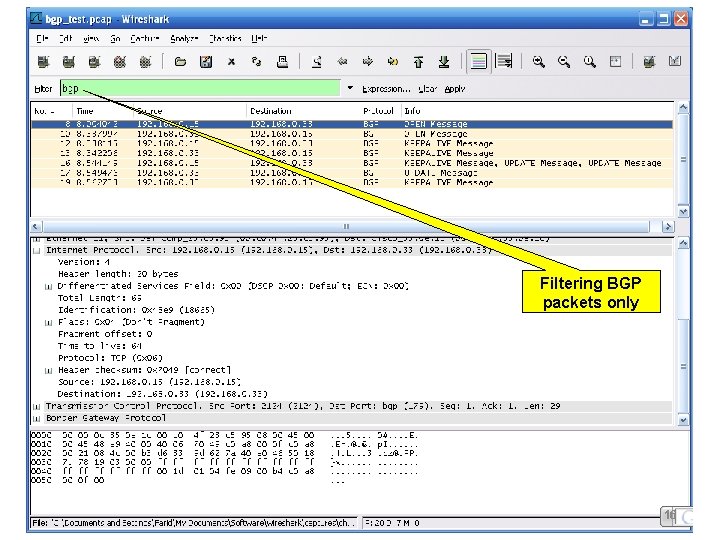
Filtering BGP packets only 16

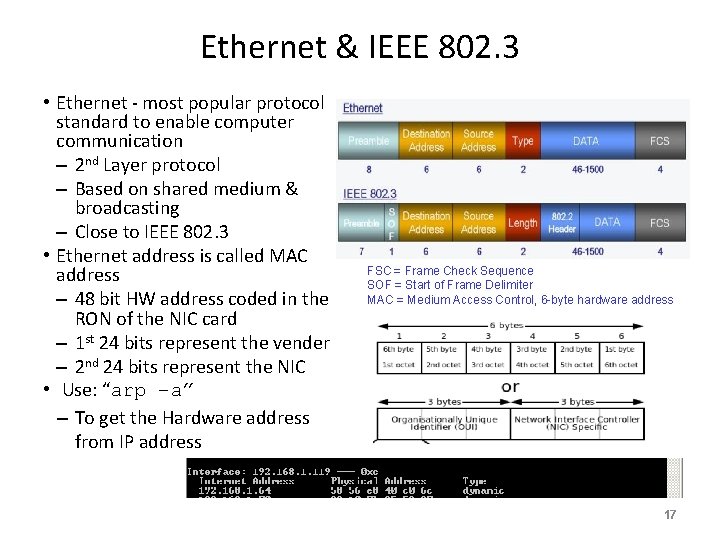
Ethernet & IEEE 802. 3 • Ethernet - most popular protocol standard to enable computer communication – 2 nd Layer protocol – Based on shared medium & broadcasting – Close to IEEE 802. 3 • Ethernet address is called MAC address – 48 bit HW address coded in the RON of the NIC card – 1 st 24 bits represent the vender – 2 nd 24 bits represent the NIC • Use: “arp –a” – To get the Hardware address from IP address FSC = Frame Check Sequence SOF = Start of Frame Delimiter MAC = Medium Access Control, 6 -byte hardware address 17

Appendixes 18

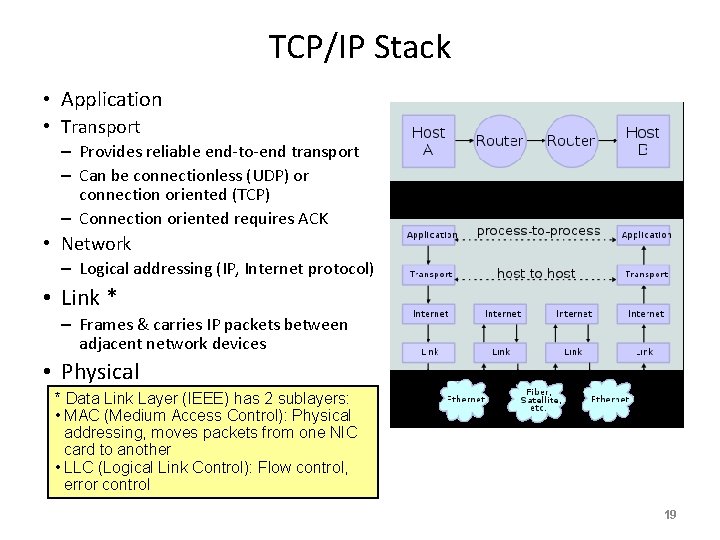
TCP/IP Stack • Application • Transport – Provides reliable end-to-end transport – Can be connectionless (UDP) or connection oriented (TCP) – Connection oriented requires ACK • Network – Logical addressing (IP, Internet protocol) • Link * – Frames & carries IP packets between adjacent network devices • Physical * Data Link Layer (IEEE) has 2 sublayers: • MAC (Medium Access Control): Physical addressing, moves packets from one NIC card to another • LLC (Logical Link Control): Flow control, error control 19

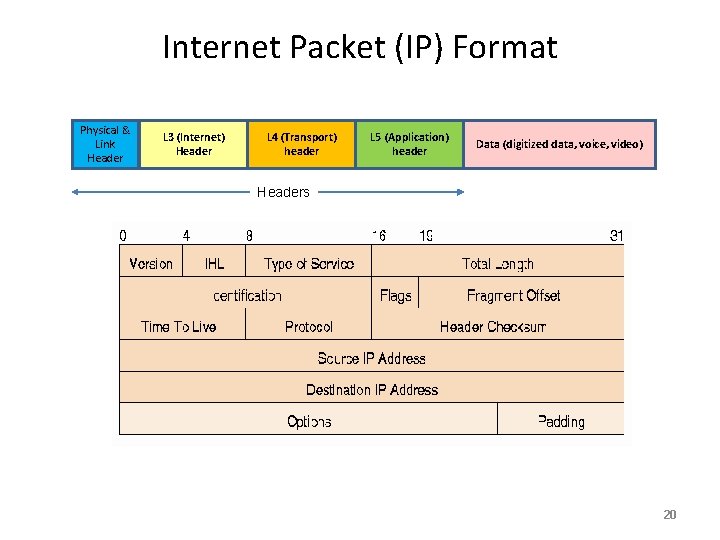
Internet Packet (IP) Format Physical & Link Header L 3 (Internet) Header L 4 (Transport) header L 5 (Application) header Data (digitized data, voice, video) Headers 20

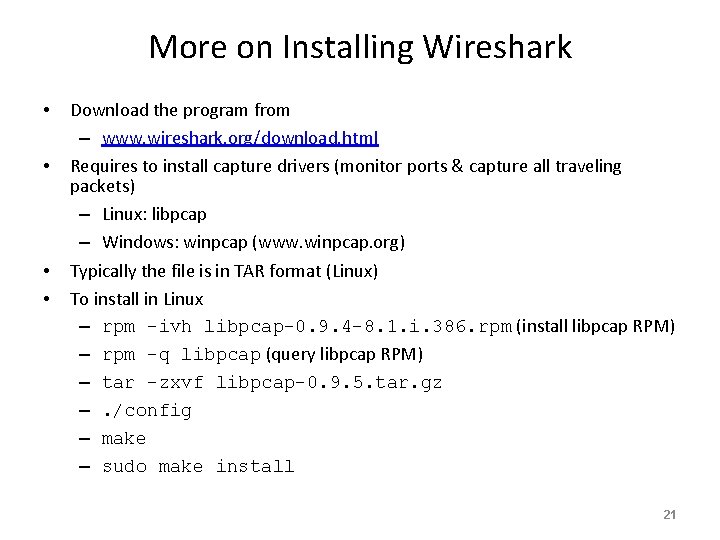
More on Installing Wireshark • • Download the program from – www. wireshark. org/download. html Requires to install capture drivers (monitor ports & capture all traveling packets) – Linux: libpcap – Windows: winpcap (www. winpcap. org) Typically the file is in TAR format (Linux) To install in Linux – rpm –ivh libpcap-0. 9. 4 -8. 1. i. 386. rpm (install libpcap RPM) – rpm –q libpcap (query libpcap RPM) – tar –zxvf libpcap-0. 9. 5. tar. gz –. /config – make – sudo make install 21

Appendix - Installing Wireshark • • Log in as the ‘root’ user Insert Fedora Code 4 Disk #4 Navigate to the following folder in the disk /Fedora/RPMS Locate packages – ethereal— 0. 11. -2. i 386. rpm – ethereal-gnome-0. 11 -2. i 386. rpm • • Copy the above packages to your system Change directory to the packages location – cd <package_dir> • Install Ethereal – rpm –ivh ethereal— 0. 11. -2. i 386. rpm • Install Ethereal GNOME user Interface – rpm –ivh ethereal-gnome-0. 11 -2. i 386. rpm • Packages that are needed for Installation • Ethereal (available in Fedora Core 4 disk #4) – ethereal— 0. 11. -2. i 386. rpm • Ethereal GNOME User Interface – ethereal-gnome-0. 11 -2. i 386. rpm 22

Appendix: Some Helpful References • Wireshark capture – https: //wiki. wireshark. org/Capture. Filters • Wireshark screenshots – https: //www. google. com/search? q=display+wireshark+screenshots&biw=1234&bih=92 0&tbm=isch&tbo=u&source=univ&sa=X&ved=0 CBw. Qs. ARq. FQo. TCLPO 5 u. KGm. Mg. CFd. I 7 i. A odb. Y 0 ABw#imgrc=LTv 96 BTj 4 FEl. YM%3 A • Wireshark for TCP – https: //wiki. wireshark. org/Transmission_Control_Protocol • Wireshark for TCP – https: //www. wireshark. org/docs/wsug_html_chunked/Chapter. Work. html • Wireshark for TCP & UDP – https: //en. wikiversity. org/wiki/Wireshark/UDP • Wireshark You. Tube on filter – https: //www. youtube. com/watch? v=__SR 6 JO 6 l-A 23