An introduction to Network Analyzers Dr Farid Farahmand
- Slides: 18

An introduction to Network Analyzers Dr. Farid Farahmand 3/23/2009

Network Analysis and Sniffing n Process of capturing, decoding, and analyzing network traffic q q q n Why is the network slow What is the network traffic pattern How is the traffic being shared between nodes Also known as q traffic analysis, protocol analysis, sniffing, packet analysis, eavesdropping*, etc. *Listen secretly to what is said in private!

Network Analyzer n A combination of hardware and software tools what can detect, decode, and manipulate traffic on the network q q n n Passive monitoring (detection) - Difficult to detect Active (attack) n Common network analyzers q q q Wireshark / Ethereal Windump Etherpeak Dsniff And much more…. Available both free and commercially Mainly software-based (utilizing OS and NIC) q q Also known as sniffer A program that monitors the data traveling through the network passively Read: Basic Packet-Sniffer Construction from the Ground Up! by Chad Renfro Checkout his program: sniff. c

Network Analyzer Components n Hardware q n Special hardware devices n n q Capturing the data is easy! The question is what to do with it! Monitoring voltage fluctuation Jitter (random timing variation) Jabber (failure to handle electrical signals) CRC and Parity Errors NIC Card Capture driver q n Buffer q n memory or disk-based Real-time analysis q n capturing the data analyzing the traffic in real time; detecting any intrusions Decoder q making data readable

Who Uses Network Analyzers n System administrators q n Understand system problems and performance Malicious individuals (intruders) n n Capture cleartext data Passively collect data on vulnerable protocols q q n n n FTP, POP 3, IMAP, SMATP, rlogin, HTTP, etc. Capture Vo. IP data Mapping the target network Traffic pattern discovery Actively break into the network (backdoor techniques)

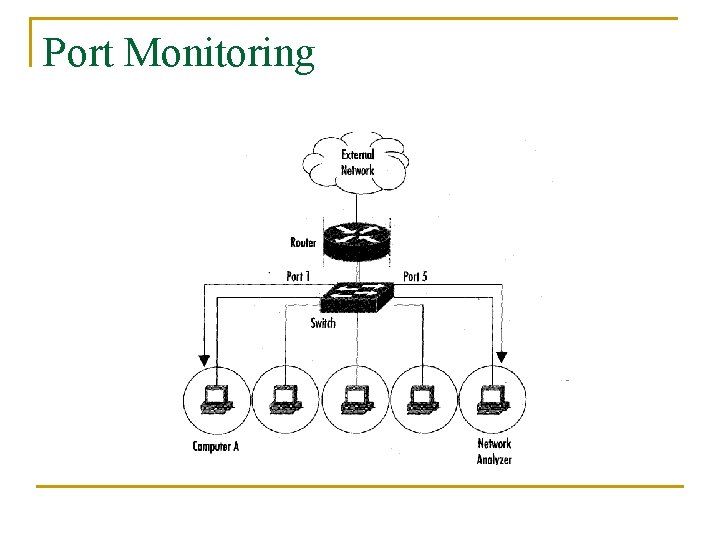
Basic Operation n n Ethernet traffic is broadcasted to all nodes on the same segment Sniffer can capture all the incoming data when the NIC is in promiscuous mode: q q n ifconfig eth 0 promisc ifconfig eth 0 –promisc Default setup is non-promiscuous (only receives the data destined for the NIC) Remember: a hub receives all the data! If switches are used the sniffer must perform port spanning q q Also known as port mirroring The traffic to each port is mirrored to the sniffer

Port Monitoring

Protecting Against Sniffers n Spoofing the MAC is often referred to changing the MAC address (in Linux: ) q q ifconfig eth 0 down ifconfig eth 0 hw ether 00: 01: 02: 03: 04: 05 ifconfig eth 0 up Register the new MAC address by broadcasting it n n ping –c 1 –b 192. 168. 1. 1 To detect a sniffer (Linux) q q q n Remember: 00: 01: 02: 03: 04: 05 MAC address (HWaddr)= Vender Address + Unique NIC # Download Promisc. c) ifconfig -a (search for promisc) ip link (search for promisc) To detect a sniffer (Windows) q Download Promisc. Detect

Protecting Against Sniffers n n Using switches can help Use encryption q q n Remember: Never use unauthorized Sniffers at wok! Making the intercepted data unreadable Note: in many protocols the packet headers are cleartext! VPNn use encryption and authorization for secure communications q VPN Methods n Secure Shell (SSH): headers are not encrypted n Secure Sockets Layer (SSL): high network level packet n security; headers are not encrypted IPsec: Encrypted headers but does not used TCP or UDP

What is Wireshark? Remember: You must have a n n n good understanding of the network before you use Sniffers effectively! Formerly called Ethereal An open source program q free with many features Decodes over 750 protocols Compatible with many other sniffers Plenty of online resources are available Supports command-line and GUI interfaces q TSHARK (offers command line interface) has three components n n n Editcap (similar to Save as. . to translate the format of captured packets) Mergecap (combine multiple saved captured files) Text 2 pcap (ASCII Hexdump captures and write the data into a libpcap output file)

Installing Wireshark n n Download the program from q www. wireshark. org/download. html Requires to install capture drivers (monitor ports and capture all traveling packets) q Linux: libpcap q Windows: winpcap (www. winpcap. org) Typically the file is in TAR format (Linux) To install in Linux q rpm –ivh libpcap-0. 9. 4 -8. 1. i. 386. rpm (install lipcap RPM) q rpm –q libpcap (query lipcap RPM) q tar –zxvf libpcap-0. 9. 5. tar. gz q. /config q make q sudo make install

Installing Wireshark n n Log in as the ‘root’ user Insert Fedora Code 4 Disk #4 Navigate to the following folder in the disk /Fedora/RPMS Locate packages q q n n Copy the above packages to your system Change directory to the packages location q n cd <package_dir> Install Ethereal q n ethereal— 0. 11. -2. i 386. rpm ethereal-gnome-0. 11 -2. i 386. rpm –ivh ethereal— 0. 11. -2. i 386. rpm Install Ethereal GNOME user Interface q rpm –ivh ethereal-gnome-0. 11 -2. i 386. rpm n n Packages that are needed for Installation Ethereal (available in Fedora Core 4 disk #4) q n ethereal— 0. 11. -2. i 386. rpm Ethereal GNOME User Interface q ethereal-gnome-0. 11 -2. i 386. rpm

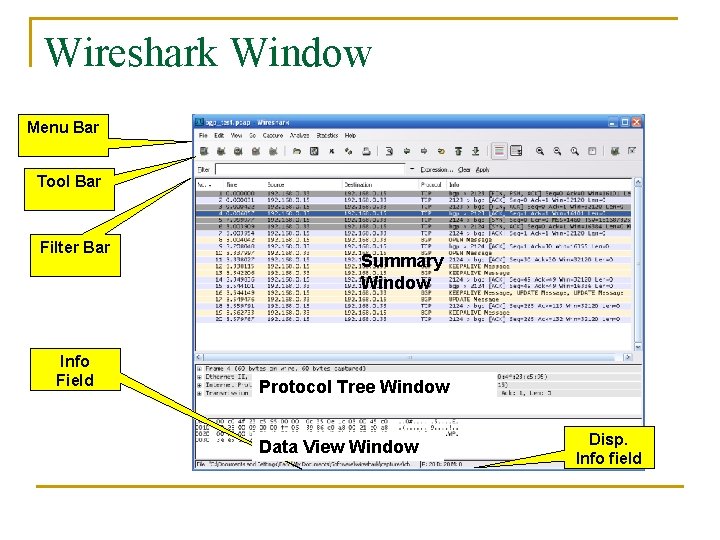
Wireshark Window Menu Bar Tool Bar Filter Bar Info Field Summary Window Protocol Tree Window Data View Window Disp. Info field

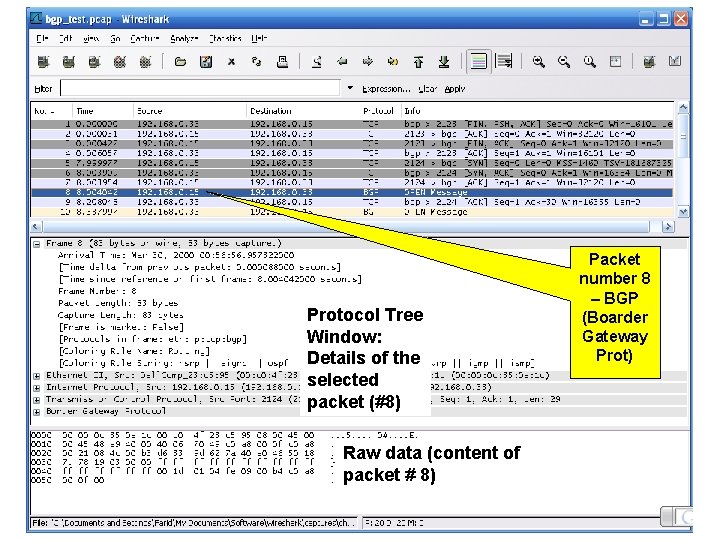
Protocol Tree Window: Details of the selected packet (#8) Raw data (content of packet # 8) Packet number 8 – BGP (Boarder Gateway Prot)

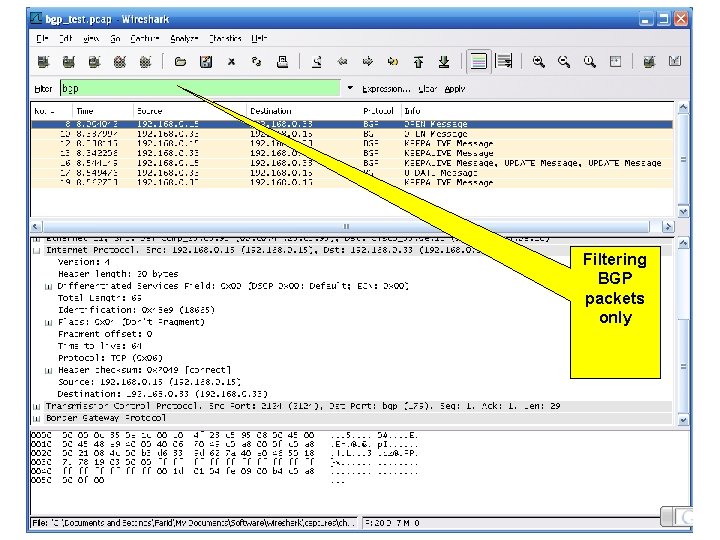
Filtering BGP packets only

We continue in the lab…. n Download the following files and copy them in your HW: q q q bgp_test tcp_stream_analysis follow_tcp_stream

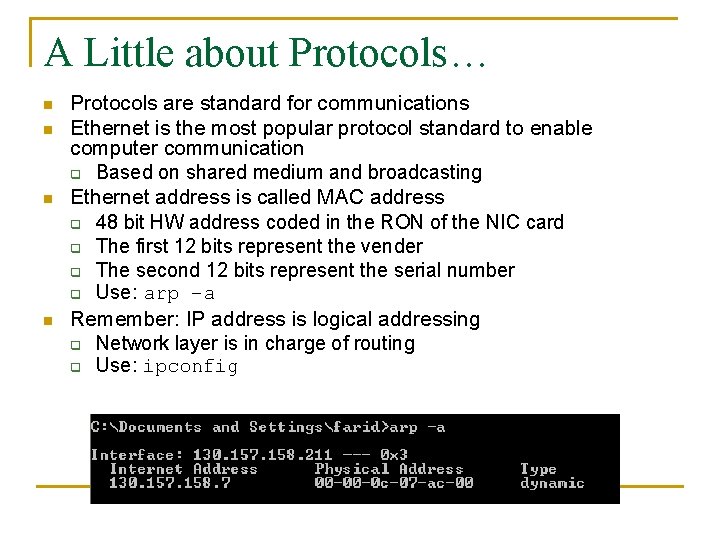
A Little about Protocols… n n Protocols are standard for communications Ethernet is the most popular protocol standard to enable computer communication q Based on shared medium and broadcasting Ethernet address is called MAC address q 48 bit HW address coded in the RON of the NIC card q The first 12 bits represent the vender q The second 12 bits represent the serial number q Use: arp –a Remember: IP address is logical addressing q Network layer is in charge of routing q Use: ipconfig

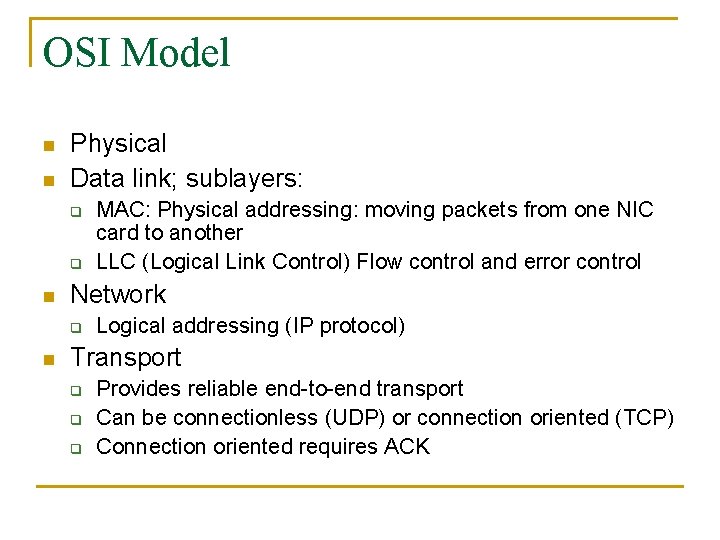
OSI Model n n Physical Data link; sublayers: q q n Network q n MAC: Physical addressing: moving packets from one NIC card to another LLC (Logical Link Control) Flow control and error control Logical addressing (IP protocol) Transport q q q Provides reliable end-to-end transport Can be connectionless (UDP) or connection oriented (TCP) Connection oriented requires ACK