Acknowledgement n Some contents on honeypot are from







- Slides: 23

Acknowledgement n Some contents on honeypot are from u http: //staff. washington. edu/dittrich/talks/arohoneynets. ppt 1

What Is a Honeypot? n n Abstract definition: “A honeypot is an information system resource whose value lies in unauthorized or illicit use of that resource. ” (Lance Spitzner) Concrete definition: “A honeypot is a faked vulnerable system used for the purpose of being attacked, probed, exploited and compromised. ” 2

Example of a Simple Honeypot n Install vulnerable OS and software on a machine n Install monitor or IDS software n Connect to the Internet (with global IP) n n Wait & monitor being scanned, attacked, compromised Finish analysis, clean the machine 3

Benefit of Deploying Honeypots n Risk mitigation: u n Lure an attacker away from the real production systems (“easy target“). IDS-like functionality: u Since no legitimate traffic should take place to or from the honeypot, any traffic appearing is evil and can initiate further actions. 4

Benefit of Deploying Honeypots n Attack analysis: Find out reasons, and strategies why and how you are attacked. u Binary and behavior analysis of capture malicious code u n Evidence: u n Once the attacker is identified, all data captured may be used in a legal procedure. Increased knowledge 5

Honeypot Classification n High-interaction honeypots u u A full and working OS is provided for being attacked VMware virtual environment Ø n Low-interaction honeypots u u Only emulate specific network services No real interaction or OS Ø n Several VMware virtual hosts in one physical machine Honeyd Honeynet/honeyfarm u A network of honeypots 6

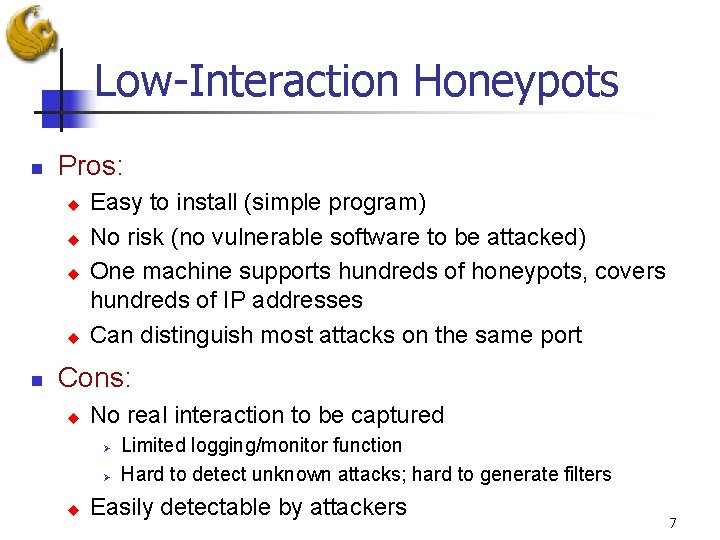
Low-Interaction Honeypots n Pros: u u n Easy to install (simple program) No risk (no vulnerable software to be attacked) One machine supports hundreds of honeypots, covers hundreds of IP addresses Can distinguish most attacks on the same port Cons: u No real interaction to be captured Ø Ø u Limited logging/monitor function Hard to detect unknown attacks; hard to generate filters Easily detectable by attackers 7

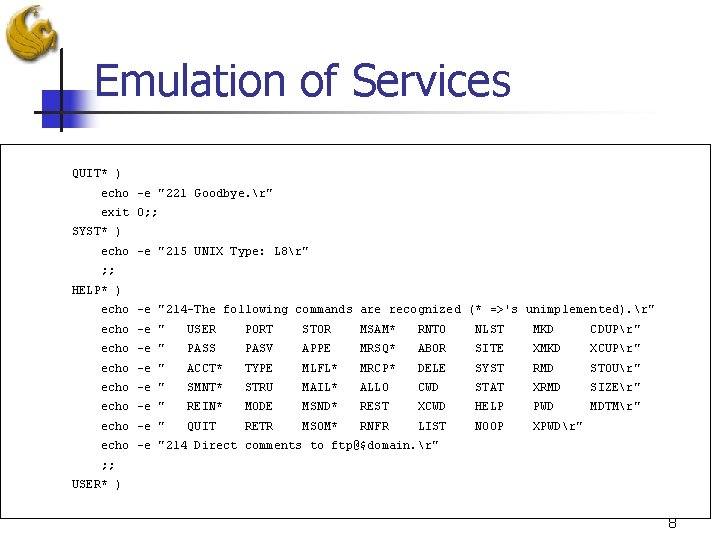
Emulation of Services QUIT* ) echo -e "221 Goodbye. r" exit 0; ; SYST* ) echo -e "215 UNIX Type: L 8r" ; ; HELP* ) echo -e "214 -The following commands are recognized (* =>'s unimplemented). r" echo -e " USER PORT STOR MSAM* RNTO NLST MKD CDUPr" echo -e " PASS PASV APPE MRSQ* ABOR SITE XMKD XCUPr" echo -e " ACCT* TYPE MLFL* MRCP* DELE SYST RMD STOUr" echo -e " SMNT* STRU MAIL* ALLO CWD STAT XRMD SIZEr" echo -e " REIN* MODE MSND* REST XCWD HELP PWD MDTMr" echo -e " QUIT RETR MSOM* RNFR LIST NOOP XPWDr" echo -e "214 Direct comments to ftp@$domain. r" ; ; USER* ) 8

High-Interaction Honeypots n Pros: Real OS, capture all attack traffic/actions u Can discover unknown attacks/vulnerabilites u Can capture and anlayze code behavior u n Cons: Time-consuming to build/maintain u Time-consuming to analysis attack u Risk of being used as stepping stone u High computer resource requirement u 9

Honeynet n n A network of honeypots High-interaction honeynet u n A distributed network composing many honeypots Low-interaction honeynet u u Emulate a virtual network in one physical machine Example: honeyd 10

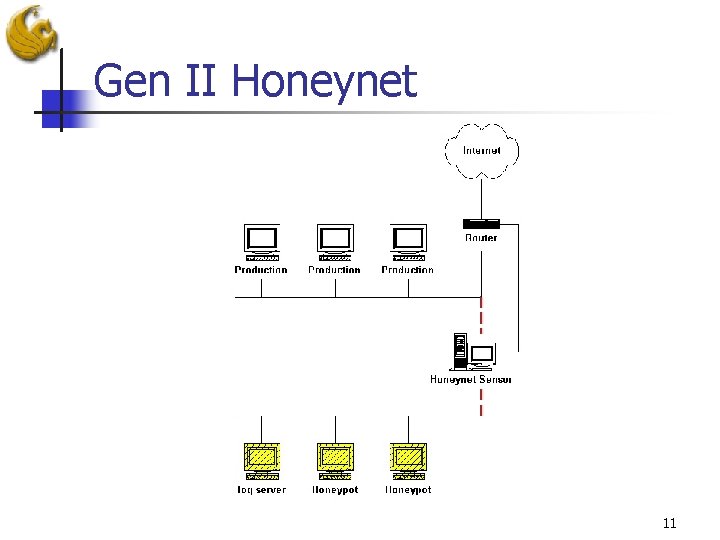
Gen II Honeynet 11

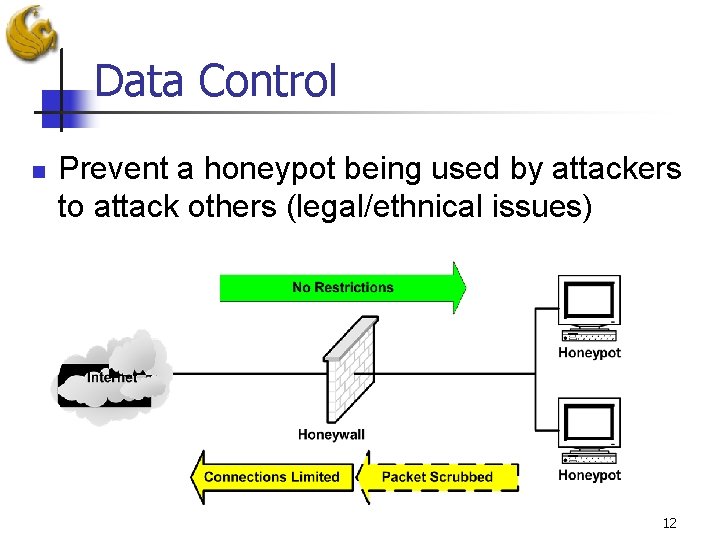
Data Control n Prevent a honeypot being used by attackers to attack others (legal/ethnical issues) 12

The Evolution of Malware n n Malware, including spyware, adware and viruses want to be hard to detect and/or hard to remove Rootkits are a fast evolving technology to achieve these goals u u u n Cloaking technology applied to malware Not malware by itself Example rootkit-based viruses: W 32. Maslan. A@mm, W 32. Opasa@mm Rootkit history u Appeared as stealth viruses Ø u One of the first known PC viruses, Brain, was stealth First “rootkit” appeared on Sun. OS in 1994 Ø Replacement of core system utilities (ls, ps, etc. ) to hide malware processes

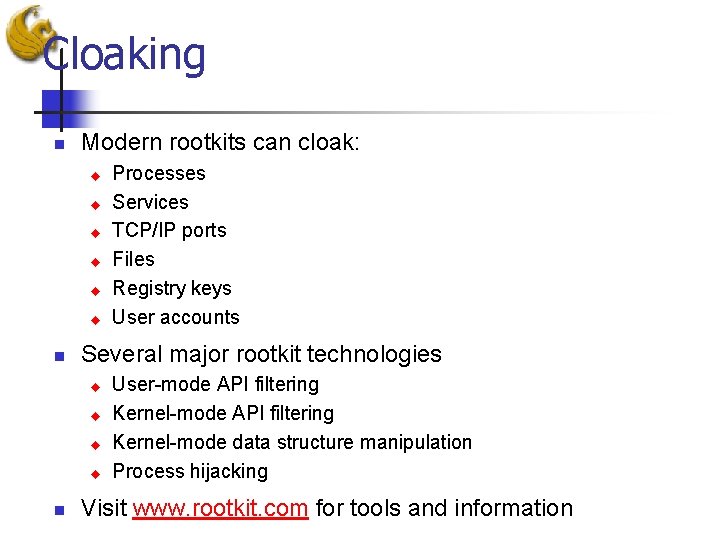
Cloaking n Modern rootkits can cloak: u u u n Several major rootkit technologies u u n Processes Services TCP/IP ports Files Registry keys User accounts User-mode API filtering Kernel-mode data structure manipulation Process hijacking Visit www. rootkit. com for tools and information

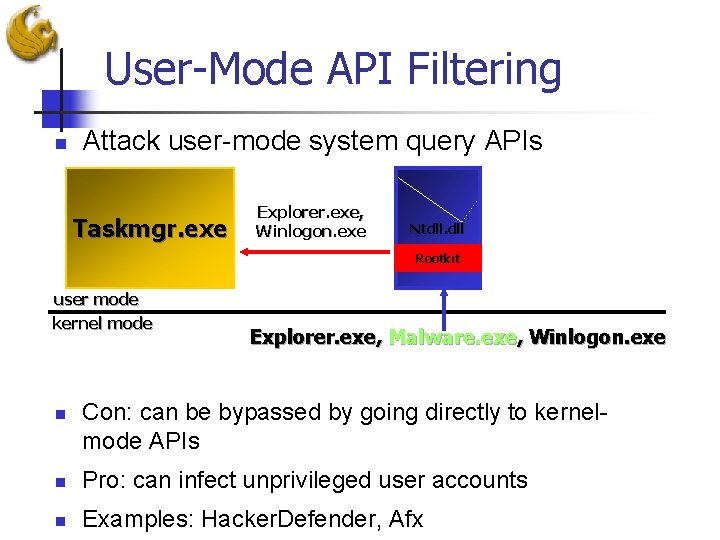
User-Mode API Filtering n Attack user-mode system query APIs Taskmgr. exe Explorer. exe, Winlogon. exe Ntdll. dll Rootkit user mode kernel mode n Explorer. exe, Malware. exe, Winlogon. exe Con: can be bypassed by going directly to kernelmode APIs n Pro: can infect unprivileged user accounts n Examples: Hacker. Defender, Afx

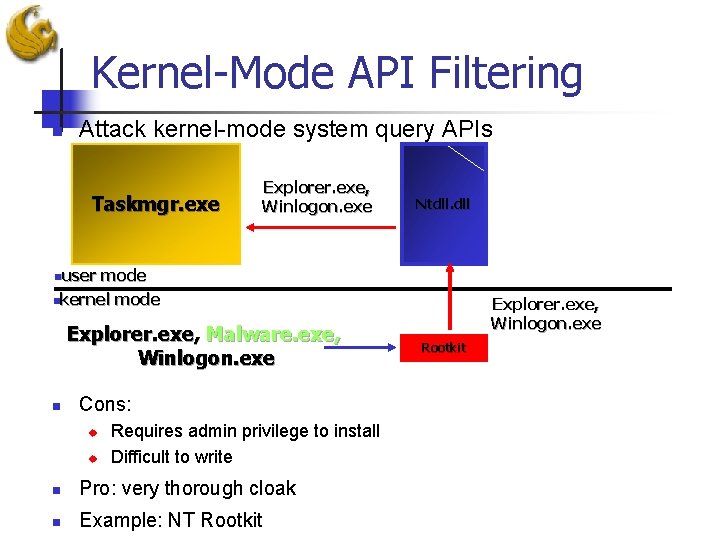
Kernel-Mode API Filtering n Attack kernel-mode system query APIs Taskmgr. exe Explorer. exe, Winlogon. exe Ntdll. dll nuser mode nkernel mode Explorer. exe, Malware. exe, Winlogon. exe n Cons: u u Requires admin privilege to install Difficult to write n Pro: very thorough cloak n Example: NT Rootkit Explorer. exe, Winlogon. exe Rootkit

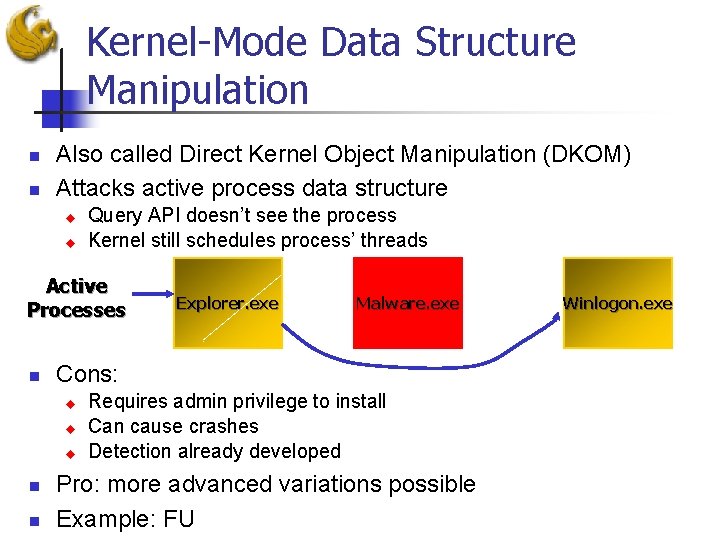
Kernel-Mode Data Structure Manipulation n n Also called Direct Kernel Object Manipulation (DKOM) Attacks active process data structure u u Query API doesn’t see the process Kernel still schedules process’ threads Active Processes n u u n Malware. exe Cons: u n Explorer. exe Requires admin privilege to install Can cause crashes Detection already developed Pro: more advanced variations possible Example: FU Winlogon. exe

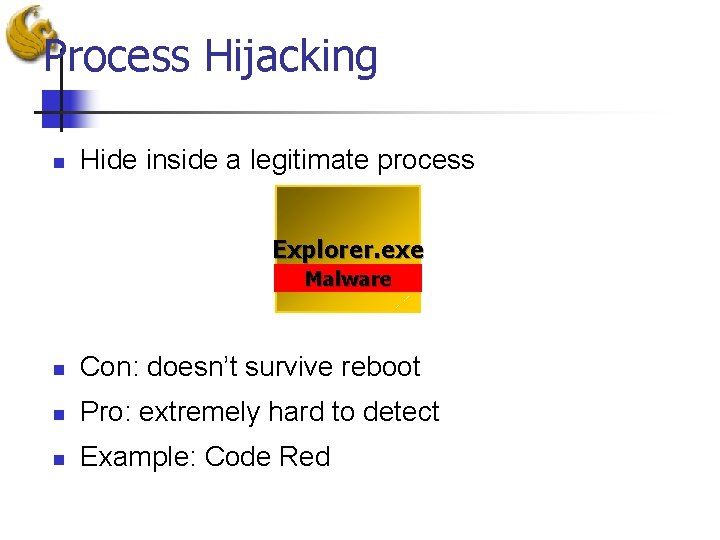
Process Hijacking n Hide inside a legitimate process Explorer. exe Malware n Con: doesn’t survive reboot n Pro: extremely hard to detect n Example: Code Red

Detecting Rootkits n All cloaks have holes Leave some APIs unfiltered u Have detectable side effects u Can’t cloak when OS is offline u n Rootkit detection attacks holes Cat-and-mouse game u Several examples u Ø Ø Microsoft Research Strider/Ghostbuster RKDetect Sysinternals Rootkit. Revealer F-Secure Black. Light

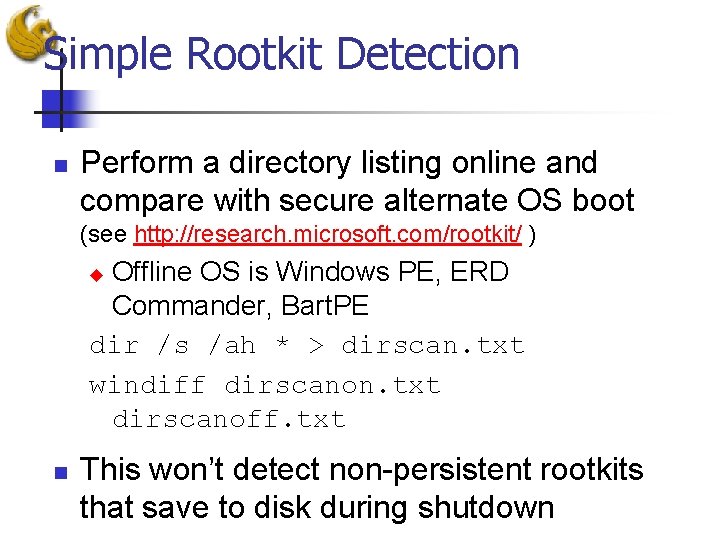
Simple Rootkit Detection n Perform a directory listing online and compare with secure alternate OS boot (see http: //research. microsoft. com/rootkit/ ) Offline OS is Windows PE, ERD Commander, Bart. PE dir /s /ah * > dirscan. txt windiff dirscanon. txt dirscanoff. txt u n This won’t detect non-persistent rootkits that save to disk during shutdown

Rootkit. Revealer n Rootkit. Revealer (RKR) runs online n RKR tries to bypass rootkit to uncover cloaked objects u u u All detectors listed do the same RKR scans HKLMSoftware, HKLMSystem and the file system Performs Windows API scan and compares with raw data structure scan Rootkit. Revealer Filtered Windows API omits malware files and keys Rootkit Windows API Raw file system, Raw Registry hive Malware files and keys are visible in raw scan

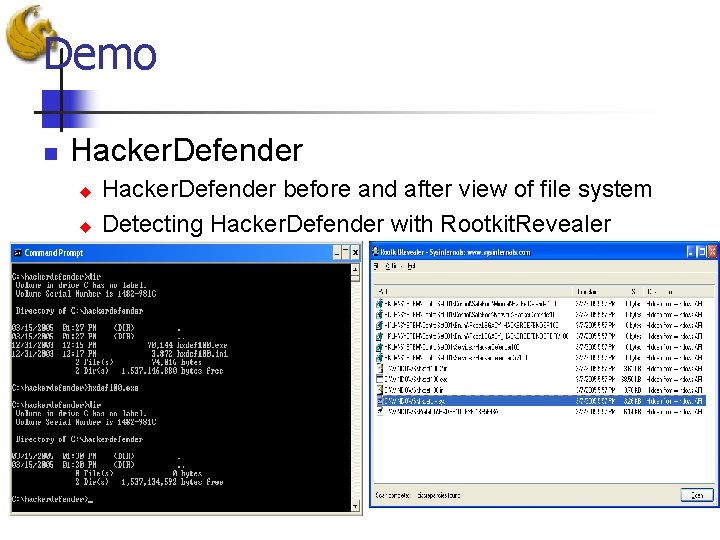
Demo n Hacker. Defender u u Hacker. Defender before and after view of file system Detecting Hacker. Defender with Rootkit. Revealer

Dealing with Rootkits n Unless you have specific uninstall instructions from an authoritative source: Reformat the system and reinstall Windows! n Don’t rely on “rename” functionality offered by some rootkit detectors It might not have detected all a rootkit’s components u The rename might not be effective u
 Antigentest åre
Antigentest åre Open source honeypot
Open source honeypot Conpot github
Conpot github Kfsensor download
Kfsensor download Honeypot virtual machine
Honeypot virtual machine Easyvmx
Easyvmx Shadow honeypot
Shadow honeypot Honeypot introduction
Honeypot introduction Honeypot
Honeypot Argos honeypot
Argos honeypot Honeypot
Honeypot Honeypot setup
Honeypot setup Specter honeypot
Specter honeypot Some say the world will end in fire some say in ice
Some say the world will end in fire some say in ice Sometimes you win some sometimes you lose some
Sometimes you win some sometimes you lose some Some say the world will end in fire some say in ice
Some say the world will end in fire some say in ice Cakes is countable or uncountable
Cakes is countable or uncountable They say it only takes a little faith to move a mountain
They say it only takes a little faith to move a mountain Some trust in chariots and some in horses song
Some trust in chariots and some in horses song What are some contact forces and some noncontact forces?
What are some contact forces and some noncontact forces? University of sydney acknowledgement of country
University of sydney acknowledgement of country Acknowledgement slides
Acknowledgement slides Acknowledgment slide
Acknowledgment slide Expectational acknowledgement
Expectational acknowledgement