TEL 581 INFORMATION ASSURANCE HONEYPOTS http www easyvmx
















- Slides: 25

TEL 581 INFORMATION ASSURANCE HONEYPOTS http: //www. easyvmx. com/blog/files/images/honeypot. jpg Presented by Stanley Chand & Damien Prescod

1. Introduction 2. Hackers 3. Goals of Honeypot 4. Common topologies for Honeypots 5. Different types of Honeypots 1. Based on deployment 2. Based on Involvement 6. Honeynets 1. Architecture 7. Honeyd 1. Architecture 8. Entrapments in Honeypots 9. Anti Honeypots 10. Conclusion CONTENTS

INTRODUCTION 1. Honeypots are often understood to refer to the English children’s character Winnie-the-pooh. 2. In computer terminology, a Honeypot is a trap set to detect, and aid in counter attacking attempts of unauthorized use of information systems. 3. Generally it consists of computer data or network sites that appears to be a part of a network but its actually isolated, (un)protected, and monitored, which seems to contain information that would be of value to the attackers.

INTRODUCTION Ø Often Honeypots are used as computers, but it can also be used in other forms like data records or even unused IP address space. Ø They must be handled carefully, else can become a risk to the internal networks. If they are not properly walled off, attackers can use them to break into the system. Ø These computers run special software, designed to appear to an intruder as being worth looking into. But in reality these programs are dummies, and are specifically constructed to foster interest in attackers.

HACKERS!! 1. A hacker can be defined as: a person using Computer skills 2. to manipulate private IS without authority for mal-intent. 3. Kevin Mitnick is a famous hacker who is the yardstick in 4. the CP black hat arena. http: //instructors. cwrl. utexas. edu/jbrown/fil 5. Why do they do it, Thrill (Kevin), Ego ( MS, Yahoo, Ebay), es/hackers_cartoons. jpg 6. But in most case malicious intent $$$. Ukrainian Credit card 7. extortion case. 8. Sentences if caught can vary from 5 -10 years, some special cases have cost the freedom of individuals indefinitely.

Goal of Honey. Pots 1. The goal of the honeypot is to trap or trace the events of the hackers with a pseudo operational network. 2. Key to the setup is constructing a FTP, DNS or web server outside of the DMZ* safe area. 3. The collected info can be used as legal evidence or for academic research in anti-hacker software or procedures. 4. Protect production networks while enticing hacker events. 5. Configure such that all public inbound IP’s are allowed whilst preventing outgoing traffic via a firewall.

Configuration of Honeypots Configuration Keys!! • Never leave access to secure data/production data networks. • Use moderate passwords not to strong neither easy!! Else you may give away the objective to smarter hackers. • Implement no productions ID’s or passwords in the honeypots. • Be sure to implement real time monitoring on the honeypot. • Have an alerting mechanism configured. You want to know!! • In any business architecture where internet usage is available never under estimate the usefulness of a honeypot in conjunction with your VPN. $$$ don’t let profit marginalize security.

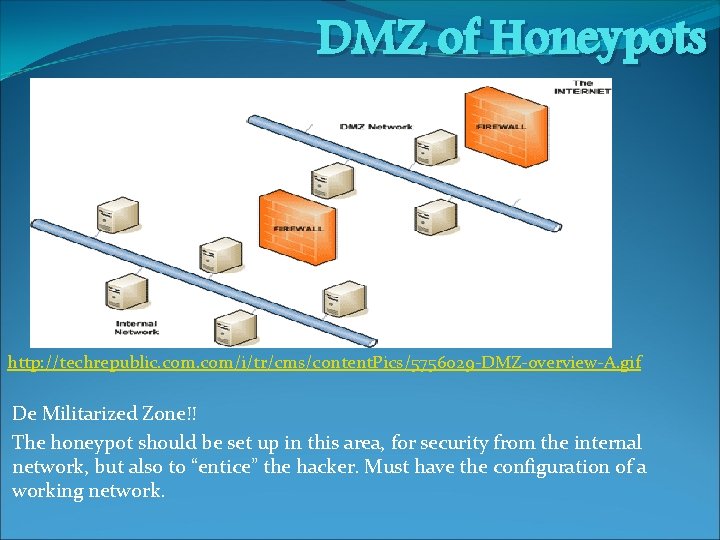
DMZ of Honeypots http: //techrepublic. com/i/tr/cms/content. Pics/5756029 -DMZ-overview-A. gif De Militarized Zone!! The honeypot should be set up in this area, for security from the internal network, but also to “entice” the hacker. Must have the configuration of a working network.

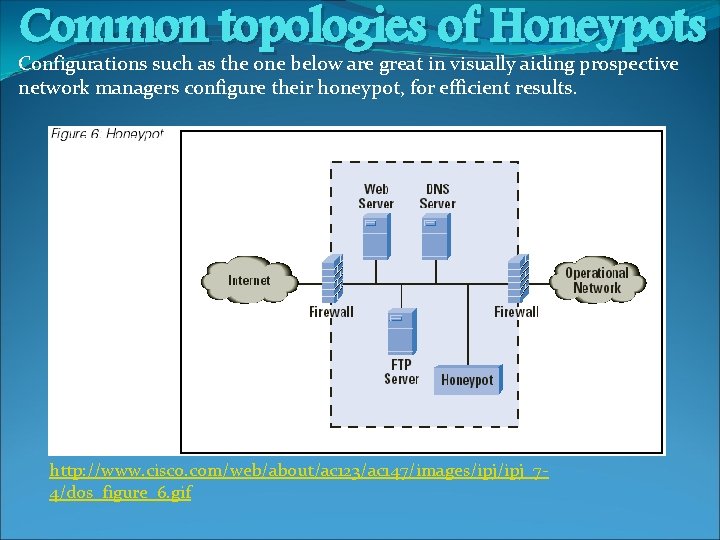
Common topologies of Honeypots Configurations such as the one below are great in visually aiding prospective network managers configure their honeypot, for efficient results. http: //www. cisco. com/web/about/ac 123/ac 147/images/ipj_74/dos_figure_6. gif

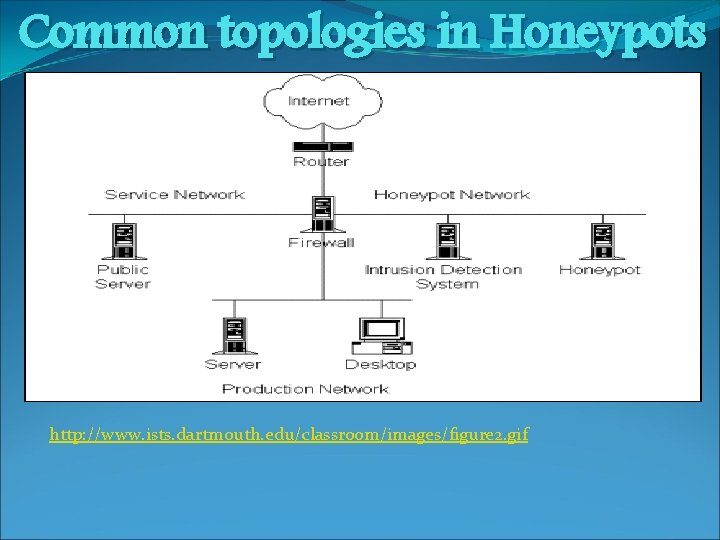
Common topologies in Honeypots http: //www. ists. dartmouth. edu/classroom/images/figure 2. gif

BASED ON THERE DEPLOYMENT Ø There are mainly two types of Honeypots: § Production Honeypots. § Research Honeypots. Ø Production Honeypots: - These are easy to use, capture only limited information and are used primarily by companies. These Honeypots are easier to deploy, and gives less information about the attackers than the Research Honeypots do. Ø Research Honeypots : - They are mainly used by non profit research organizations or an educational institution to gather information about the motives and tactics of the Blackhat community targeting different networks.

BASED ON LEVEL OF INVOLVEMENT Ø There again two types of Honeypots (Involvement): § High Interaction Honeypots. § Low Interaction Honeypots. Ø High Interaction Honeypots: - Honeypots installed on complex architectures with complex functions are based on high interaction systems. Honeynets, and Decoy server are good example of High Interaction Honeypots. Ø Low Interaction Honeypots: - They are useful when the maintainers are not able to guarantee that the process will be excluded from rest of the network activities during the attack. Honeyd, and Specters are good example of Low Interaction Honeypots.

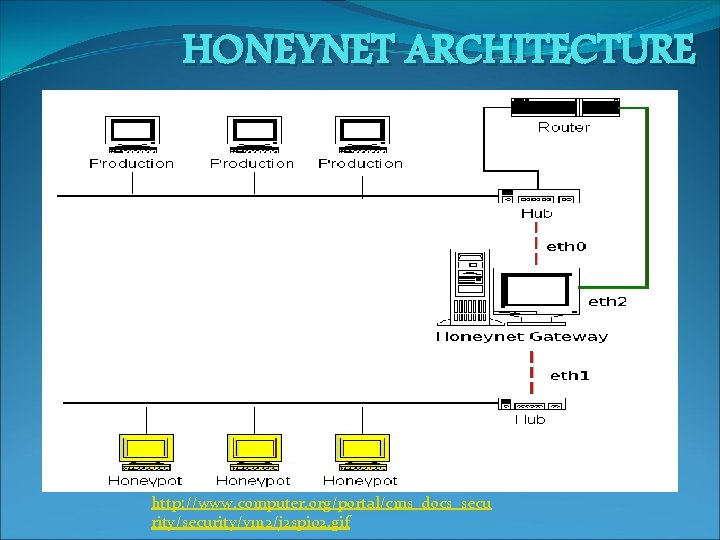
HONEYNETS 1. Honeynets are the complex architecture made up of various types of Honeypots. 2. It’s a network of Honeypots simulating a production environment. 3. Data Control: - Mechanism for containing attacker activities within the Honeynet, without attackers realizing it. 4. Data Capture: - Logging of attackers activities without attackers knowledge.

HONEYNET ARCHITECTURE http: //www. computer. org/portal/cms_docs_secu rity/security/v 1 n 2/j 2 spi 02. gif

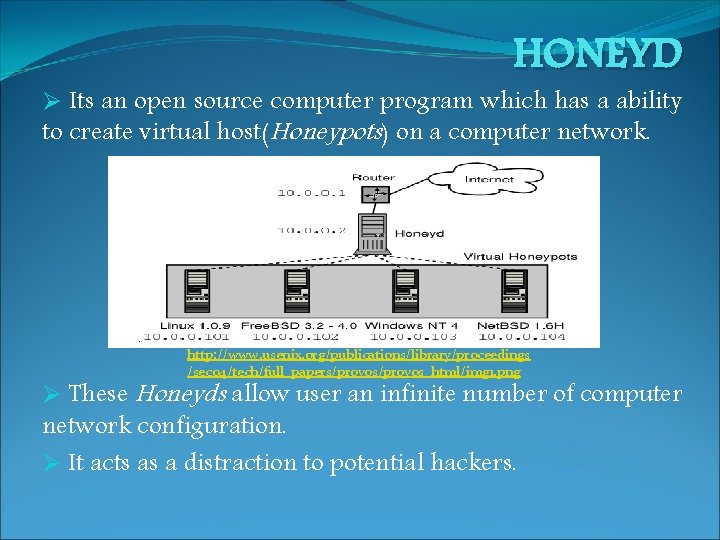
HONEYD Ø Its an open source computer program which has a ability to create virtual host(Honeypots) on a computer network. http: //www. usenix. org/publications/library/proceedings /sec 04/tech/full_papers/provos_html/img 1. png Ø These Honeyds allow user an infinite number of computer network configuration. Ø It acts as a distraction to potential hackers.

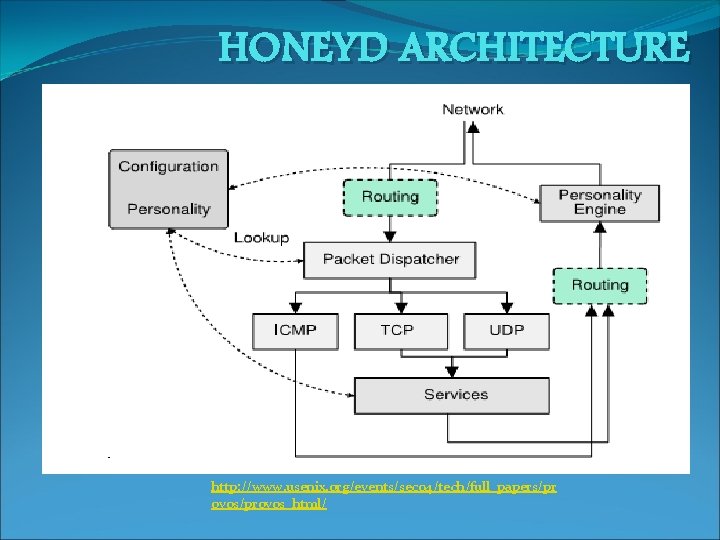
HONEYD ARCHITECTURE http: //www. usenix. org/events/sec 04/tech/full_papers/pr ovos/provos_html/

Legality of Honeypots 1. Depending on the objective of the honeypot system, research or production. 2. The use of data acquired must be done so legally. 3. The setup of the website topology/browser must adhere to legal ramifications. 4. It can “entice” but not “entrap” potential subjects. 5. Malicious intent must not be coerced!!

Entrapment in Honeypots Not the movie, but the action of misleading! ØThe information on the web must not trick subjects into thinking that there is something to be had publically. ØNot only will this evidence not hold up in court as plaintiff material it can backfire and lead to an anti-suit for the respective Honeypot owners. http: //www. impawards. com/1999/posters/entr apment_ver 1. jpg

Send safe honeypot hunter. Why? ? ? • HP’s hurt spammers. Anti-Honeypots HP’s are detectable. • TCP sequence analysis, ARP request analysis. What does the Anti-HP do? ? ? • It test the open proxy connections and label them as Good, Bad or Traps. Hackers- can open a false mail server at port 25 (proxy test) Connect to this port Attempt to proxy back to its own false mail server. HP may suggest connection, but if hacker does not get any valid connection he can correctly assume it maybe an HP. More anti-Hp’s to come!!!

Honeypots Current HP’s aren't the solution- detectable Must evolve with hacker environment. Can be poisoned or attacked by hackers If compromised addresses can be made public Some Honey D’s have fixed response messages that if not changed by network administrators can prove backwardly constructive.

DISADVANTAGE Ø Narrow Field of view: - They can only see activities directed towards them. Ø Fingerprinting : - This is when an attacker can identify the true identity of Honeypots. Ø Risk: - Once Honeypots are attacked, can be used to attack or harm other systems.

Future Ø From misunderstanding to acceptance. Ø Improving ease of use. Ø Easier administration. Ø Pre-packaged solution.

SOURCES 1. Honey Pot Project- Know your enemy- Anderson Wesley 2002. 2. Security + Exam Guide-Christopher Crayton 3. CISSP-Shon Harris 4. A Virtual Honeypot frame work, Internet article (n. d). Retrieved on (2 nd Feb 2008) http: //www. citi. umich. edu/u/provos/papers/honeyd. pdf 5. Anti Honeypot Technology , Internet article (n. d). Retrieved on (2 nd Feb 2008) http: //www. ccc. de/congress/2004/fahrplan/files/208 -anti-honeypottechnology-slides. pdf 6. http: //en. wikipedia. org/wiki/Honeypot_%28 computing%29

Questions? ?

THANK YOU
 Easyvms
Easyvms Honeypots and honeynets
Honeypots and honeynets Cpsc 581
Cpsc 581 Cpsc 581
Cpsc 581 Cis581
Cis581 Cis 581 upenn
Cis 581 upenn Cpsc 581
Cpsc 581 Cpsc 581
Cpsc 581 618 ad
618 ad Da form 1804
Da form 1804 Supercom 581
Supercom 581 Reformatio in pejus
Reformatio in pejus Emu information assurance and cyber defense
Emu information assurance and cyber defense Msr cube
Msr cube Tel mixto
Tel mixto Clasificacion de rapin y allen
Clasificacion de rapin y allen Tel aviv university electrical engineering
Tel aviv university electrical engineering Tel mixto
Tel mixto Mammoth oil stock 1920
Mammoth oil stock 1920 Tel ve levha haline getirilebilen elementler
Tel ve levha haline getirilebilen elementler 12345678123
12345678123 Irodalmi stíluseszközök
Irodalmi stíluseszközök Tel 104
Tel 104 Picture tel
Picture tel Gerard tel
Gerard tel Laminar 37m
Laminar 37m















































