Using Kojoney Open Source Low Interaction Honeypot to













- Slides: 27

Using Kojoney Open Source Low Interaction Honeypot to Develop Defensive Strategies and Fingerprint Post-Compromise Behavior Justin C. Klein Keane Sr. Info. Sec Specialist University of Pennsylvania, School of Arts and Sciences Copyright 2010 Justin C. Klein Keane

Background SSH Secure replacement for telnet RFC defined protocol (open) Available on most Linux/Unix machines Ongoing brute force attacks are seen on SSH servers Unfortunately we don't know what are attackers after Tempting logical fallacy to assume motivation Threat modeling and risk analysis depend on knowing motivation Copyright 2010 Justin C. Klein Keane

Honeypots What is a honeypot? Service deliberately configured to attract malicious attention Why would you use one? Tar pit, waste attacker time Early warning, warn of attacks Profiling, determine the types of attacks that are being utilized against your resources Copyright 2010 Justin C. Klein Keane

Types of Honeypots High interaction Full system installation Advantage is attacker has a full stack to interact with Disadvantage is attacker has more tools, could hide or break out of the honeypot Low interaction Software implementation that simulates a system Controlled environment, but is much easier for attackers to detect Copyright 2010 Justin C. Klein Keane

Danger! Downstream liability Attackers could user your honeypot as a launching pad to attack others Attackers could host malicious content on your server Attacker could use your honeypot as a dump site for illegal material Pivot point Attackers could end-run access control to internal resources using the honeypot Copyright 2010 Justin C. Klein Keane

Logistical Considerations Resource intensive Set up is time consuming, installation of OS and configuring software Analysis – it takes time to pore through logs and recreate attacker activity Redeployment can be a hassle, although virtual machine snap-shots make this much easier Copyright 2010 Justin C. Klein Keane

Kojoney Open source low interaction SSH honeypot Written in Python so it should work on any platfrom http: //kojoney. sourceforge. net/ Has some flaws. . . Static timestamps, many commands unsupported, limited filesystem, etc. Copyright 2010 Justin C. Klein Keane

How Kojoney Works How it works Negotiates a full SSH session with attackers Takes attacker input, logs it, examines it and responds with simulated output Allows attackers to download toolkits with wget and curl, but stores the files outside the sandbox Copyright 2010 Justin C. Klein Keane

Customization Modified interaction to appear more dynamic Updated directories, using the defaults can be a dead giveaway Added directory functionality so attackers can navigate the structure, create and remove directories Added support for “requested” commands, if we saw attempts to use an unsupported command we built support in Added My. SQL database support where all login data and commands are stored which makes reporting and analysis much easier Copyright 2010 Justin C. Klein Keane

Setup Kojoney running October 27, 2009, through May 3, 2010. Commodity desktop hardware, just an old Pentium powered machine with 512 MB RAM Dedicated IP Separate management interface Copyright 2010 Justin C. Klein Keane

Data Set Observed 109, 121 login attempts 596 distinct IP addresses 70 IP's participated in multiple attacks Longest span between attacks was 135 days Copyright 2010 Justin C. Klein Keane

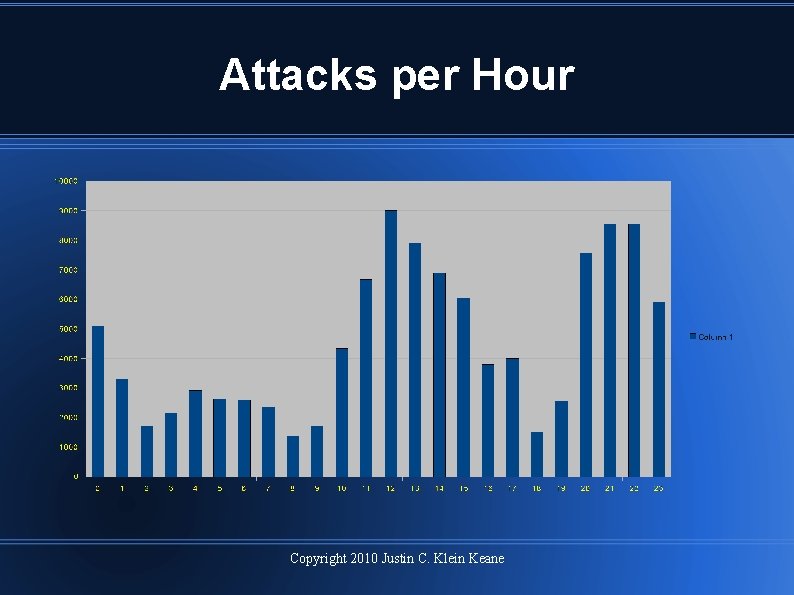
Attacks per Hour Copyright 2010 Justin C. Klein Keane

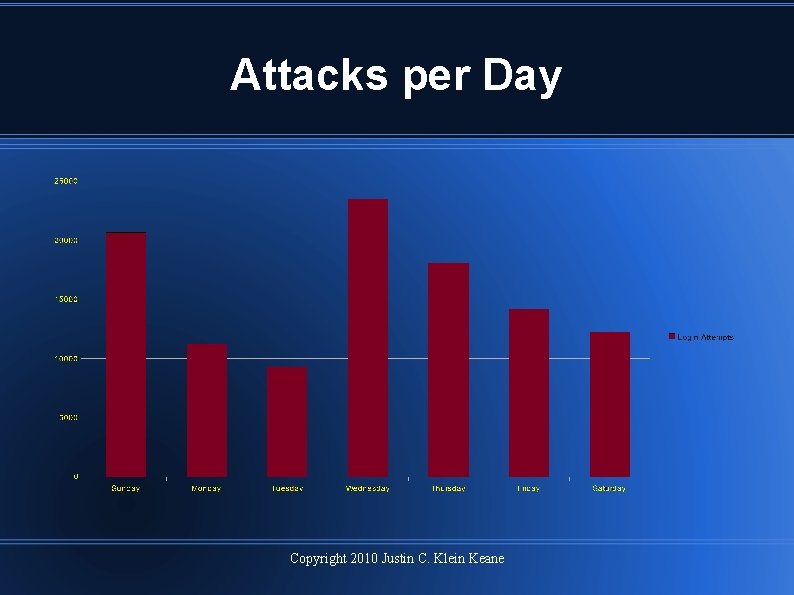
Attacks per Day Copyright 2010 Justin C. Klein Keane

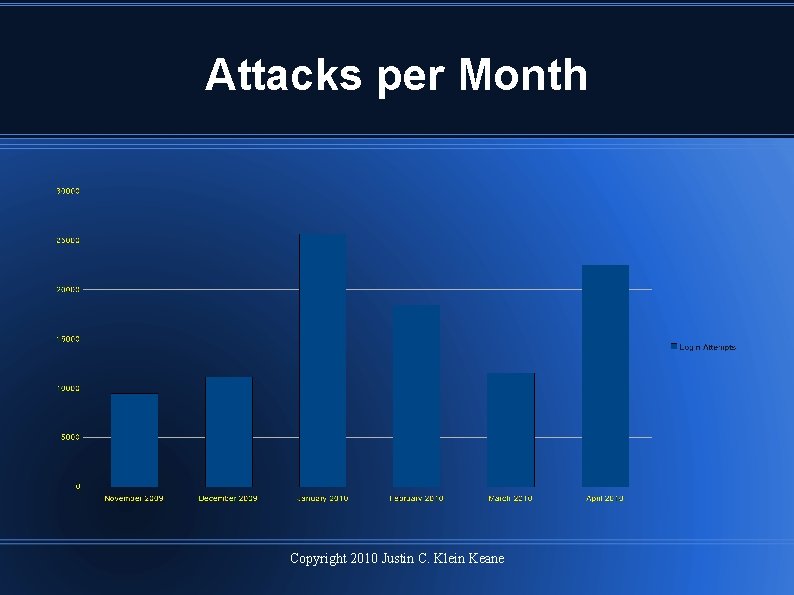
Attacks per Month Copyright 2010 Justin C. Klein Keane

Top 16 Attacks by Country Copyright 2010 Justin C. Klein Keane

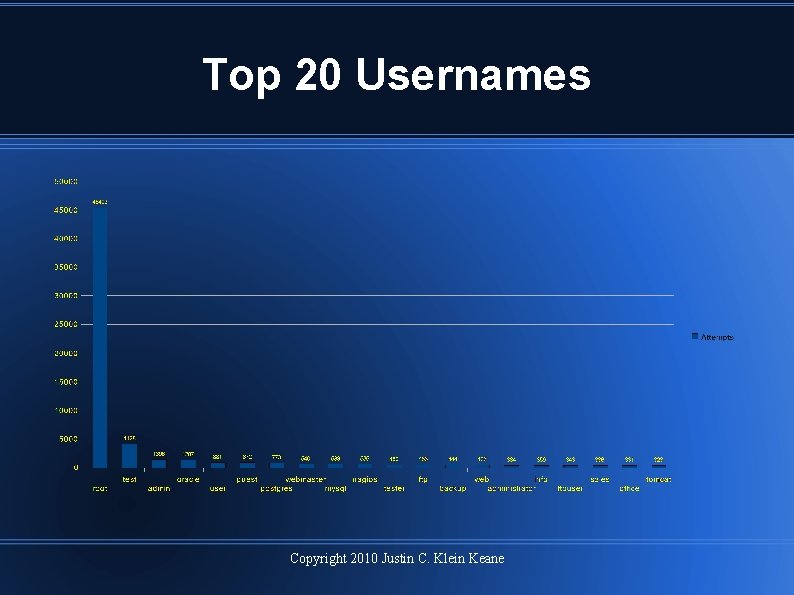
Top 20 Usernames Copyright 2010 Justin C. Klein Keane

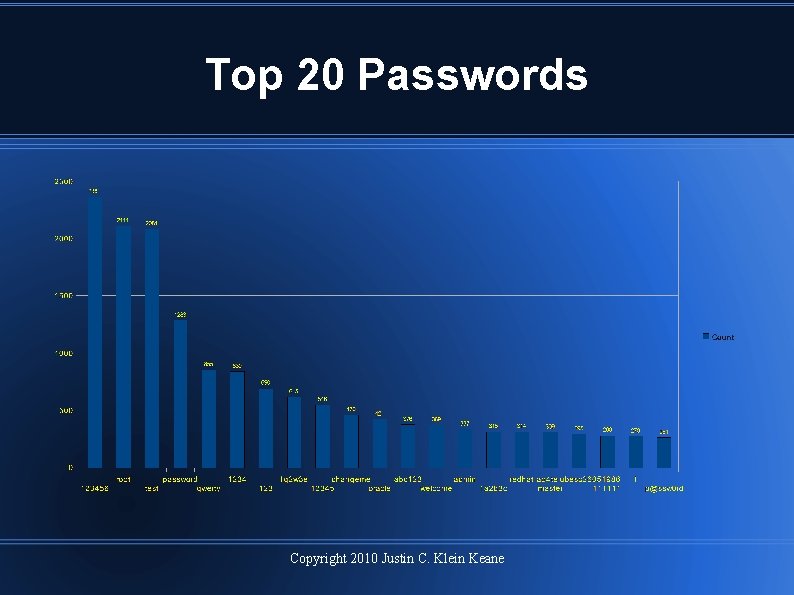
Top 20 Passwords Copyright 2010 Justin C. Klein Keane

Most Popular Commands (3, 062 issued, 181 distinct) Copyright 2010 Justin C. Klein Keane

Distinct Commands Copyright 2010 Justin C. Klein Keane

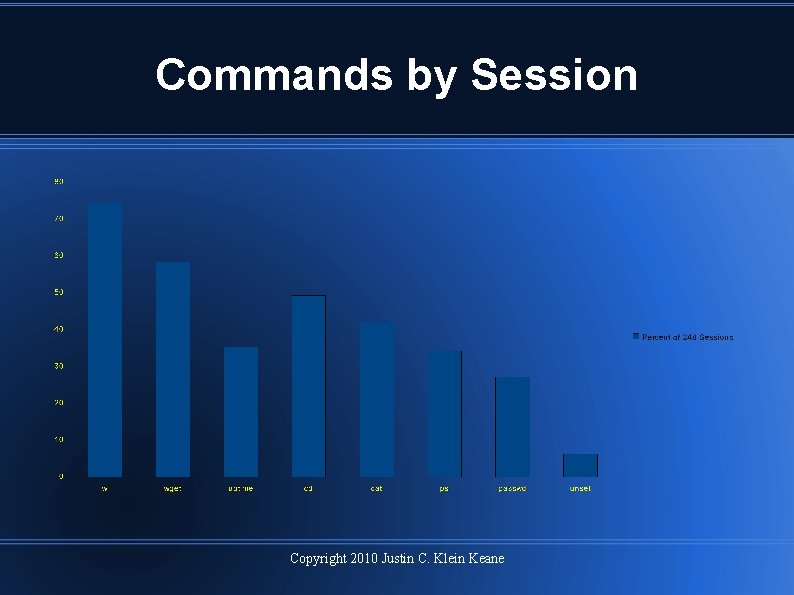
Commands by Session Copyright 2010 Justin C. Klein Keane

Wget Downloads 282 downloads captured Windows XP SP 3 downloaded 41 times Other popular downloads: Psy. BNC Other IRC bots UDP Ping Flooders Port scanners SSH brute force tools Copyright 2010 Justin C. Klein Keane

Attack Command Analysis Context is key In 94/150 times 'cat' was used as: cat /proc/cpuinfo Some attacker commands innocuous, others not: w uptime wget unset Copyright 2010 Justin C. Klein Keane

Target Accounts System accounts favorite targets Dictionary lists were uncommon Passwords were relatively complex Dictionary attack was uncommon Username 'alice' with password 'password' would withstand attacks Copyright 2010 Justin C. Klein Keane

Defensive Strategies Use SSH keys Disable remote root login over SSH Run SSH on an alternate port Use login attempt limits to frustrate brute force Copyright 2010 Justin C. Klein Keane

Detection Mechanisms Blacklist using: OSSEC http: //www. ossec. net SSH Black http: //www. pettingers. org/code/sshblack. html Copyright 2010 Justin C. Klein Keane

Conclusions Blocking by source IP may be feasible Limit access by time of day Use IP to seed examination of other logs 'trojan' certain programs to log activity Copyright 2010 Justin C. Klein Keane

Known Hostile Traffic Look for internal source Use IP as seed for log analysis Fingerprint malware captures Look for traceable activity Creating directories with names like. tmp unset history Copyright 2010 Justin C. Klein Keane