Access Management ITIL V 3 Service Operation Access








- Slides: 16

Access Management & ITIL V 3

Service Operation Access Management

Access Management The process for granting authorized users the right to use a Service while preventing access to non-authorized users. Access Management helps to protect the confidentiality, integrity and availability (CIA) of assets, therefore it is the execution of policies and actions defined in Security and Availability Management.

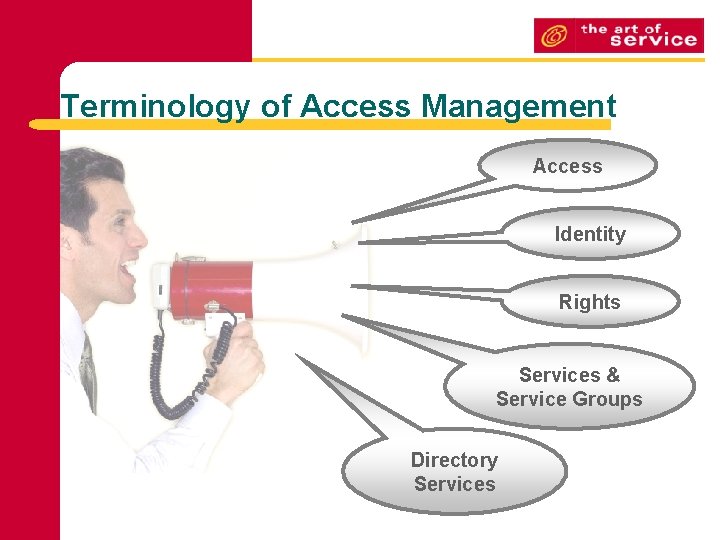
Terminology of Access Management Access Identity Rights Services & Service Groups Directory Services

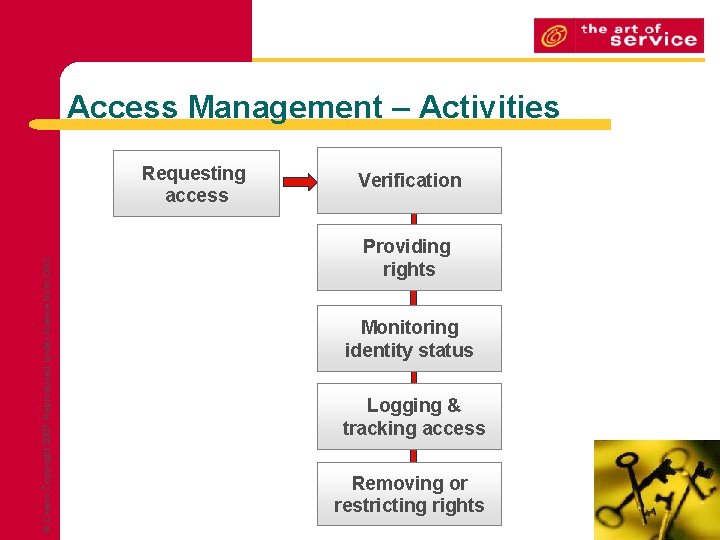
Access Management – Activities © Crown Copyright 2007 Reproduced under license from OGC Requesting access Verification Providing rights Monitoring identity status Logging & tracking access Removing or restricting rights

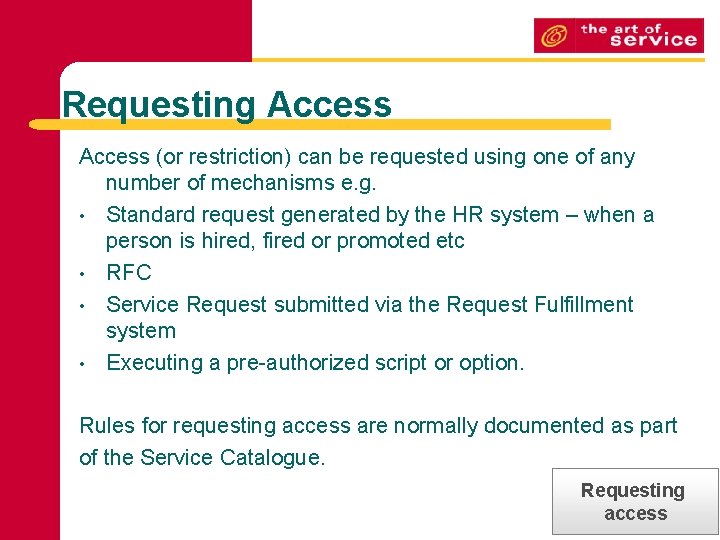
Requesting Access (or restriction) can be requested using one of any number of mechanisms e. g. • Standard request generated by the HR system – when a person is hired, fired or promoted etc • RFC • Service Request submitted via the Request Fulfillment system • Executing a pre-authorized script or option. Rules for requesting access are normally documented as part of the Service Catalogue. Requesting access

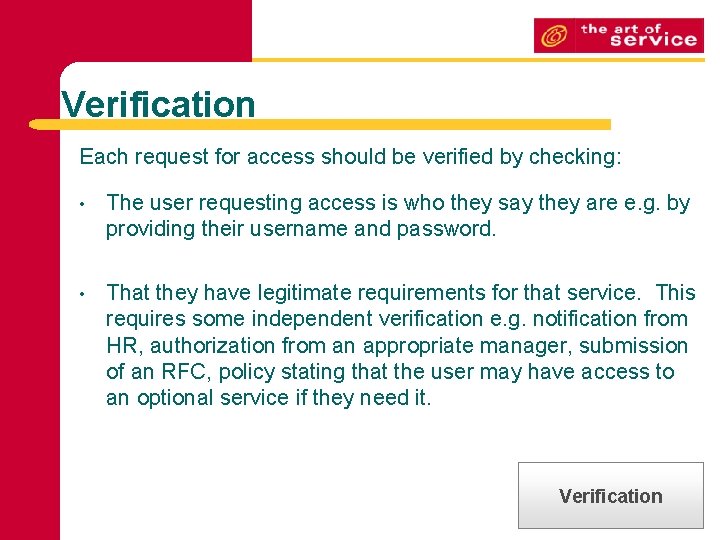
Verification Each request for access should be verified by checking: • The user requesting access is who they say they are e. g. by providing their username and password. • That they have legitimate requirements for that service. This requires some independent verification e. g. notification from HR, authorization from an appropriate manager, submission of an RFC, policy stating that the user may have access to an optional service if they need it. Verification

Providing Rights Access Management does not decide who has access to which IT service. It executes the policies and regulations defined during Service Strategy and Service Design and enforces decision to restrict or provide access, rather than making the decision. As soon as the user is verified, they are provided with the user rights for the requested service. Providing rights

Monitoring identity status As users work in the organization, their roles change and so also do their needs to access services. E. g. • • Job Changes Promotions or demotions Transfers Resignation or death Retirement Disciplinary action Dismissals Monitoring identity status

Logging & tracking access Access Management not only responds to requests, but is also responsible for ensuring that the rights provided are being properly used. Information Security Management plays an important role in detecting unauthorized access and comparing it with the rights that were provided by Access Management. Logging & tracking access

Removing or restricting rights Access Management is also responsible for revoking rights to use a service. It executes decisions and policies made during the design phase and also decisions made by managers in the organization. Removing access is normally done for the following reasons: • • • Death Resignation Dismissal User changes roles User transfers or travels to an area where different regional access applies. Removing or restricting rights

Inputs & Outputs Access Management is triggered by a request for a user(s) to access a service(s). This could originate from any of the following areas: • RFC • Service Request • Human Resources Management • Manager of a department

Information Management Identity of users, includes information about them that distinguishes them as an individual and verifies their status e. g. • Name • Address • Contact information • Physical documentation • Employee number • Tax number • Drivers license number etc • Fingerprints • Retinal images • Voice recognition patterns • DNA

Metrics that can be used to measure the effectiveness and efficiency of the Access Management process are: • Number of requests for access (e. g. Service Requests, RFC’s) • Instances of access granted, by service, user and department etc • Instances of access granted by department or individual granting rights • Number of incidents requiring a rest of access rights • Number of incidents caused by incorrect access settings.

Challenges Ability to: • Verify the identity of users • Verify the identity of the approving person or body • Verify that a user qualifies for access to a specific service • Link multiple access rights to a user • Determine status of a user at any time • Manage changes to a user’s access requirements • Restrict access rights to unauthorized users • And develop and maintain a database of all users and the rights they have been granted.

Value to business Access Management provides the following value: • • • Controlled access to services ensures that the organization is able to maintain more effectively the confidentiality of its information. Employees have the right level of access to execute their jobs effectively. Less likelihood of errors being made in data entry or in the use of a critical service by an unskilled user. Ability to audit use of services and to trace the abuse of services Ability to more easily revoke access rights when needed Could be needed for regulatory compliance (e. g. COBIT, SOX etc).