A Smart Metering Scenario Jorge Cuellar Jan Stijohann






- Slides: 18

A Smart Metering Scenario Jorge Cuellar, Jan Stijohann, Santiago Suppan Siemens AG 14. 05. 2013

Agenda General Context: Smart Grid Security § Common Terminology Description of the Scenario Environment § Case Overview Tomorrow: Possible worst case scenarios § Threat and Attack Analysis 2

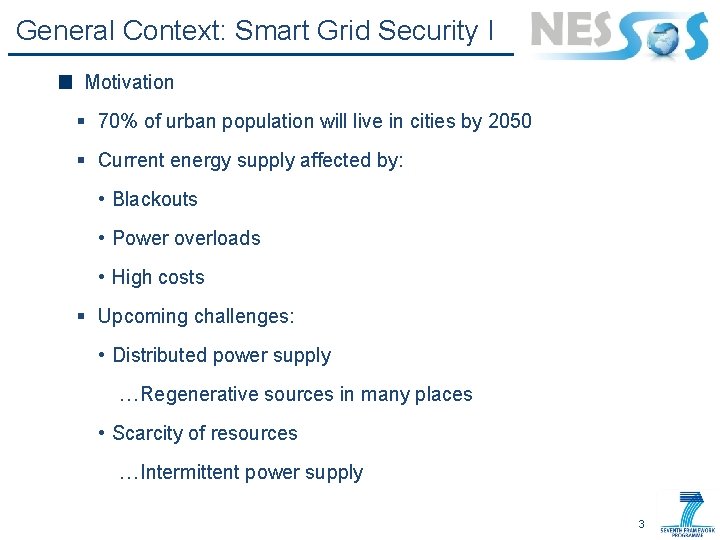
General Context: Smart Grid Security I Motivation § 70% of urban population will live in cities by 2050 § Current energy supply affected by: • Blackouts • Power overloads • High costs § Upcoming challenges: • Distributed power supply …Regenerative sources in many places • Scarcity of resources …Intermittent power supply 3

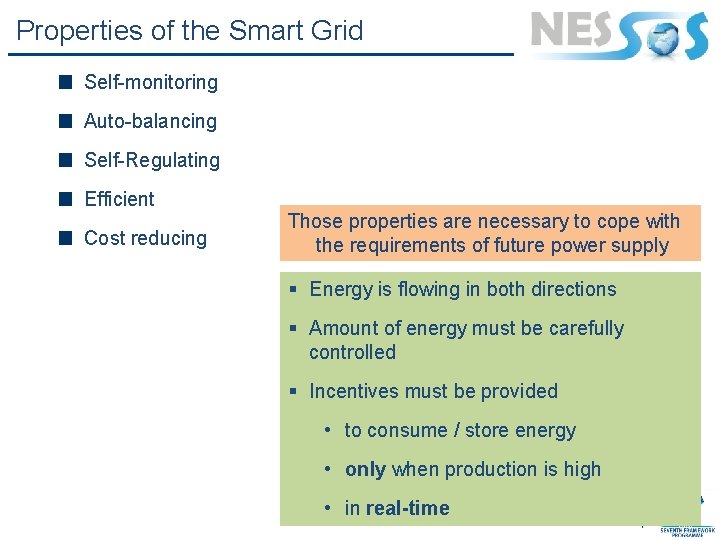
Properties of the Smart Grid Self-monitoring Auto-balancing Self-Regulating Efficient Cost reducing Those properties are necessary to cope with the requirements of future power supply § Energy is flowing in both directions § Amount of energy must be carefully controlled § Incentives must be provided • to consume / store energy • only when production is high • in real-time 4

Entities (Roles) Energy Generators Energy Suppliers § Data Communication Network § Network Gateway § Energy Supply Server Prosumer & Home Domain § Smart Appliances § Smart Meter § (Wireless) Home Area Network § Home Gateway § Home Energy Management System Meter Point Operator 5

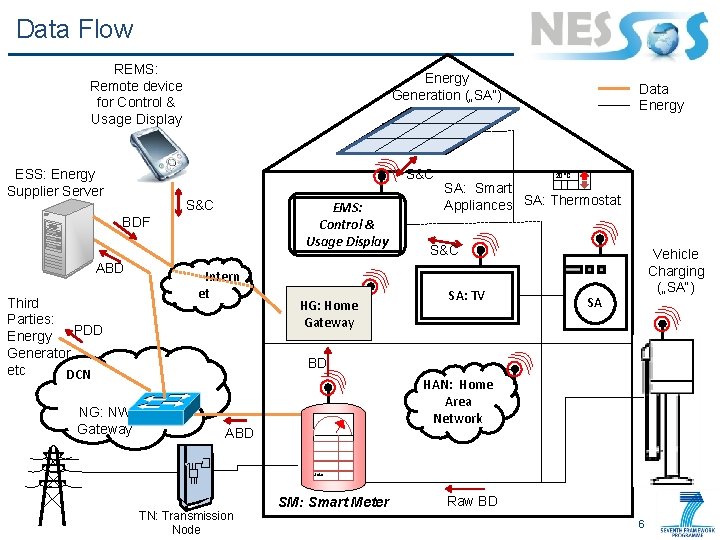
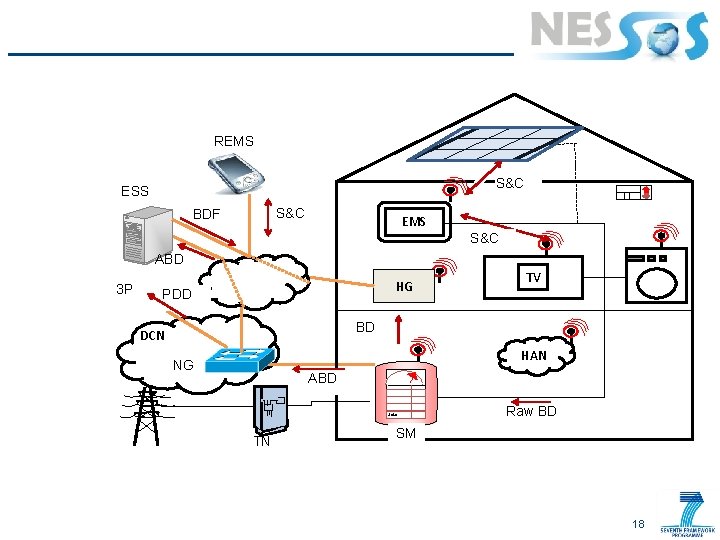
Data Flow REMS: Remote device for Control & Usage Display ESS: Energy Supplier Server Energy Generation („SA“) S&C EMS: Control & Usage Display BDF ABD Third Parties: PDD Energy Generator etc DCN NG: NW Gateway Intern et HG: Home Gateway Data Energy 20°C SA: Smart Appliances SA: Thermostat S&C SA: TV Vehicle Charging („SA“) SA BD HAN: Home Area Network ABD Solar TN: Transmission Node SM: Smart Meter Raw BD 6

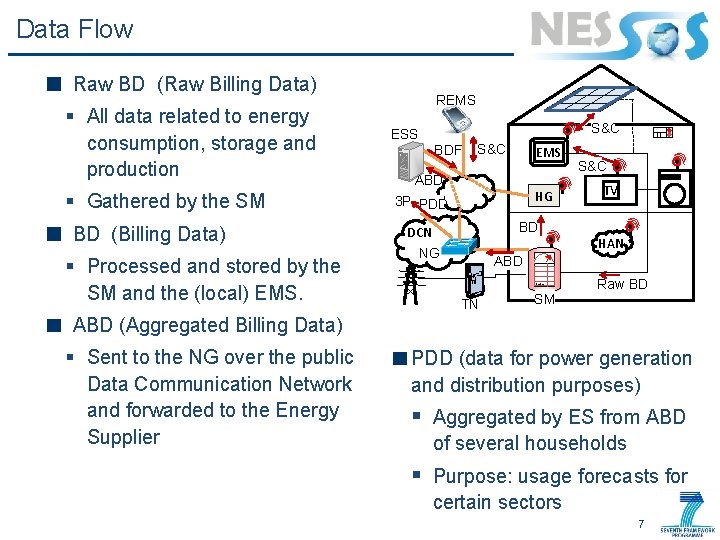
Data Flow Raw BD (Raw Billing Data) § All data related to energy consumption, storage and production § Gathered by the SM BD (Billing Data) § Processed and stored by the SM and the (local) EMS. REMS S&C ESS BDF S&C EMS ABD HG 3 P PDD S&C TV BD DCN NG HAN ABD Solar TN SM Raw BD ABD (Aggregated Billing Data) § Sent to the NG over the public Data Communication Network and forwarded to the Energy Supplier PDD (data for power generation and distribution purposes) § Aggregated by ES from ABD of several households § Purpose: usage forecasts for certain sectors 7

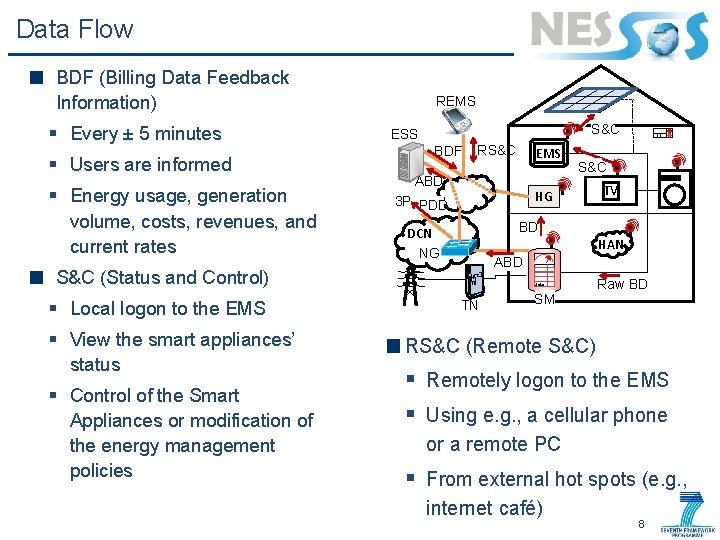
Data Flow BDF (Billing Data Feedback Information) § Every ± 5 minutes § Users are informed § Energy usage, generation volume, costs, revenues, and current rates REMS S&C ESS BDF RS&C ABD § View the smart appliances’ status § Control of the Smart Appliances or modification of the energy management policies S&C HG 3 P PDD TV BD DCN NG HAN ABD S&C (Status and Control) § Local logon to the EMS Solar TN SM Raw BD RS&C (Remote S&C) § Remotely logon to the EMS § Using e. g. , a cellular phone or a remote PC § From external hot spots (e. g. , internet café) 8

Suggestions for Worst Cases Threat and Attack Analysis Jorge Cuellar, Jan Stijohann, Santiago Suppan Siemens AG 14. 05. 2013

Questions / Tasks Assume a variety of home environments § Some clever, some less clever devices § Legacy and not legacy systems § From a variety of vendors Describe attackers & attacks in some detail: § External attackers § Insiders which are either malicious or careless • Employees, family members, neighbours, installers, manufacturers Identify security requirements Identify security controls and measures to provide § First line of defence § Defence in depth or redundancies 10

1: Family with children § Which information could the attacker obtain? • What can he deduce? Possible weak point …How many persons live? § Possible tracing? • Combination of information useful for burglary or … ? Attacker: insider / outsider 11

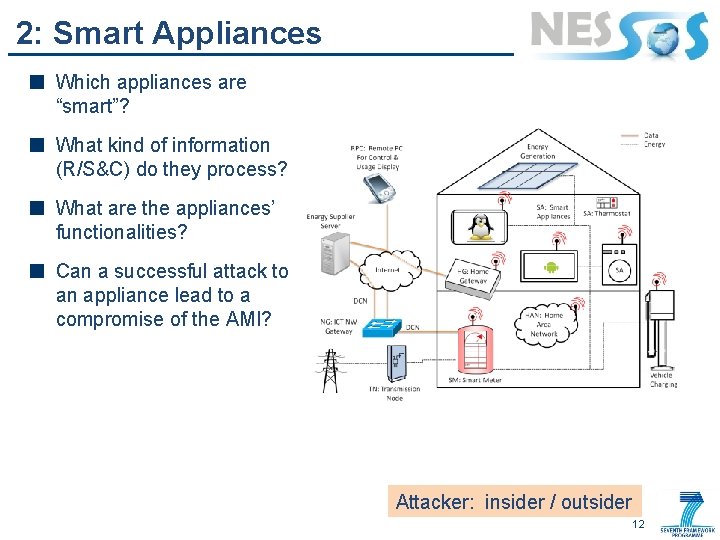
2: Smart Appliances Which appliances are “smart”? What kind of information (R/S&C) do they process? What are the appliances’ functionalities? Can a successful attack to an appliance lead to a compromise of the AMI? Attacker: insider / outsider 12

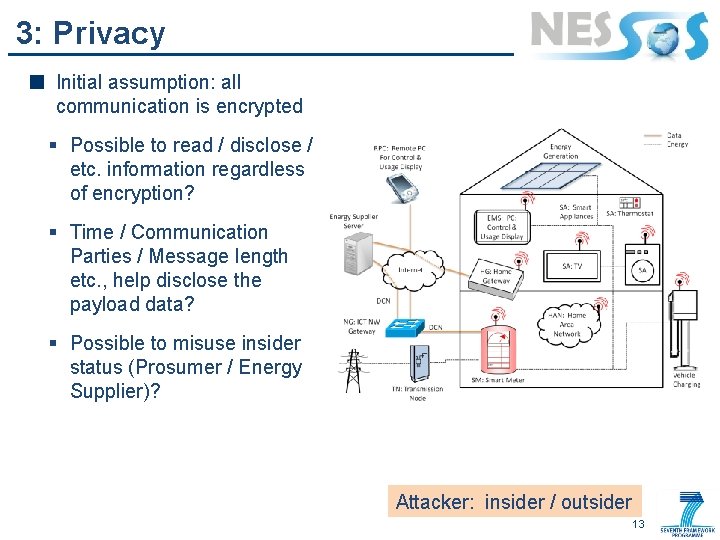
3: Privacy Initial assumption: all communication is encrypted § Possible to read / disclose / etc. information regardless of encryption? § Time / Communication Parties / Message length etc. , help disclose the payload data? § Possible to misuse insider status (Prosumer / Energy Supplier)? Attacker: insider / outsider 13

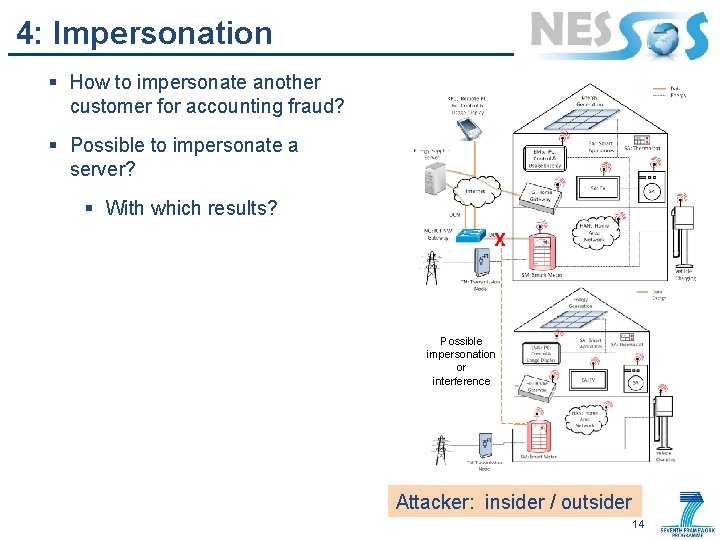
4: Impersonation § How to impersonate another customer for accounting fraud? § Possible to impersonate a server? § With which results? X Possible impersonation or interference Attacker: insider / outsider 14

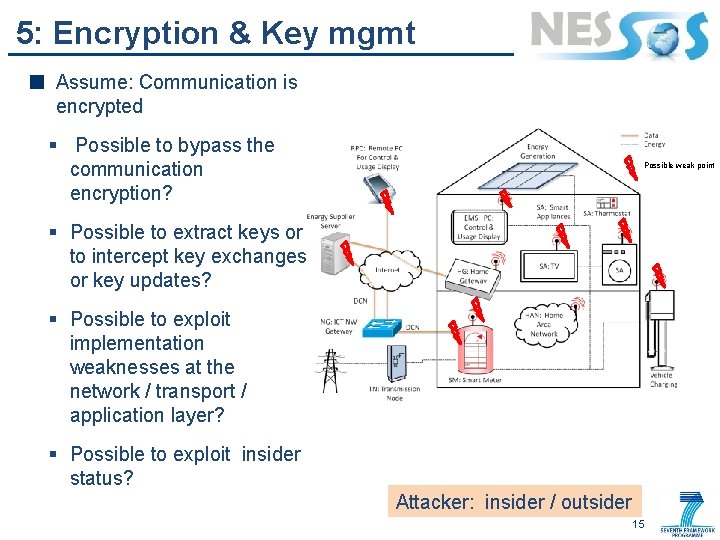
5: Encryption & Key mgmt Assume: Communication is encrypted § Possible to bypass the communication encryption? Possible weak point § Possible to extract keys or to intercept key exchanges or key updates? § Possible to exploit implementation weaknesses at the network / transport / application layer? § Possible to exploit insider status? Attacker: insider / outsider 15

6: Electric Mobility Assumption: Electric vehicles share an unique vehicle ID § Possible impersonation? § Possible fraud? uv. ID § Possible tracing? § Possible theft? § … Attacker: insider / outsider 16

Thank You! Any questions? e. Rise Challenge 2013 14. 05. 2013

REMS S&C ESS S&C BDF EMS S&C ABD 3 P HG PDD TV BD DCN HAN NG ABD Solar TN Raw BD SM 18
 Ami rotary dials
Ami rotary dials Smart metering implementation programme
Smart metering implementation programme Smart metering telekom
Smart metering telekom Amanda cuellar
Amanda cuellar Jillian cuellar
Jillian cuellar Jaime ramirez cuellar
Jaime ramirez cuellar Lissette alvarez cuellar
Lissette alvarez cuellar Jennifer cuellar ruiz
Jennifer cuellar ruiz A combination valve could include
A combination valve could include Mt carmel electric net metering
Mt carmel electric net metering Leopold lagco flume
Leopold lagco flume District metered areas
District metered areas Mid directive
Mid directive Sage metering
Sage metering Power of choice metering
Power of choice metering Sage prime gas meter
Sage prime gas meter Ameren net metering
Ameren net metering Multicircuit meters
Multicircuit meters Net metering punjab
Net metering punjab