A Lowcost Attack on a Microsoft CAPTCHA Yan









- Slides: 18

A Low-cost Attack on a Microsoft CAPTCHA Yan Qiang, 2008 -12 -9

Conference & Authors • CCS 08’ • Newcastle University, UK – Jeff Yan – Ahmad Salah El Ahmad

Outline • • • Introduction Segmentation Attack on MSN Scheme Experimental Result Suggestion on Countermeasures Conclusion

What is CAPTCHA • Completely Automated Public Turing Test to Tell Computers and Humans Apart – CAPTCHA is a brand registered by CMU 1. Text-based CAPTCHA: Type the Letter in the image 2. Image-based CAPTCHA Choose a word that relates to all the images.

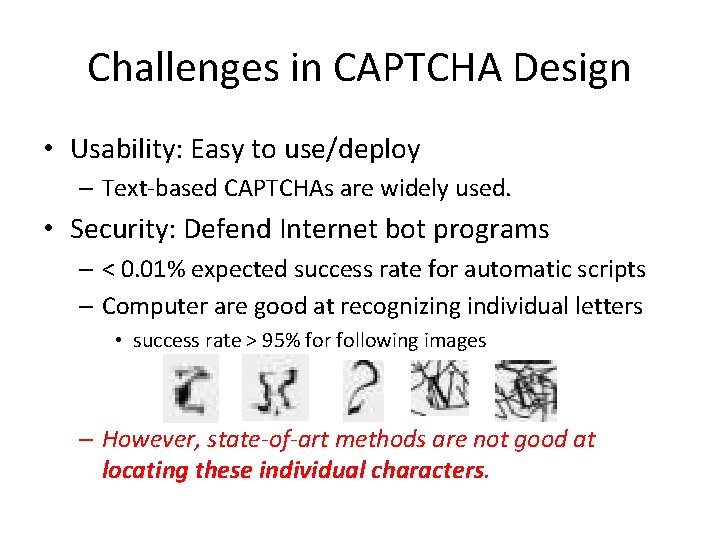
Challenges in CAPTCHA Design • Usability: Easy to use/deploy – Text-based CAPTCHAs are widely used. • Security: Defend Internet bot programs – < 0. 01% expected success rate for automatic scripts – Computer are good at recognizing individual letters • success rate > 95% for following images – However, state-of-art methods are not good at locating these individual characters.

‘Common Knowledge’ & Terminology • If breaking a text-based CAPTCHA can be successfully reduced to a problem of individual character recognition, then this scheme is effectively broken. – This paper addresses a low-cost technique to locate these individual characters. – This kind of attacks are called segmentation attacks. – Every secure text-based CAPTCHA should be segmentation resistance against segmentation attacks. – Each CAPTCHA test can be referred to as challenge.

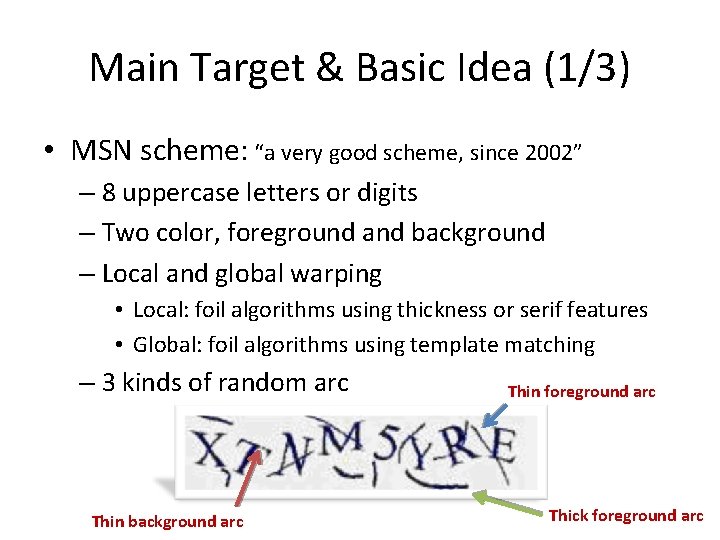
Main Target & Basic Idea (1/3) • MSN scheme: “a very good scheme, since 2002” – 8 uppercase letters or digits – Two color, foreground and background – Local and global warping • Local: foil algorithms using thickness or serif features • Global: foil algorithms using template matching – 3 kinds of random arc Thin background arc Thin foreground arc Thick foreground arc

Main Target & Basic Idea (2/3) • Task: – remove random arcs and find character boundaries • Key Observations: – A character contain more pixel than an arcs. – A character consisted of connected strokes. – A character cannot be too flat or too wide. – Arcs usually don’t form a circle. – Characters are juxtaposed according to some base line.

Main Target & Basic Idea (3/3) • Attack Steps – 1. Transform the CAPTCHA image into a black-white image using a manually selected threshold – 2. Reconnect disconnected strokes by removing thin back ground arcs. (Filling gap less than 2 pixel) – 3. partition the image by bit counting and connected component detection. – 4. Remove thick foreground arcs by information on pixel count, location, shape, interplay between shape and location. – 5. Divide evenly for remaining wide fragment into estimated parts.

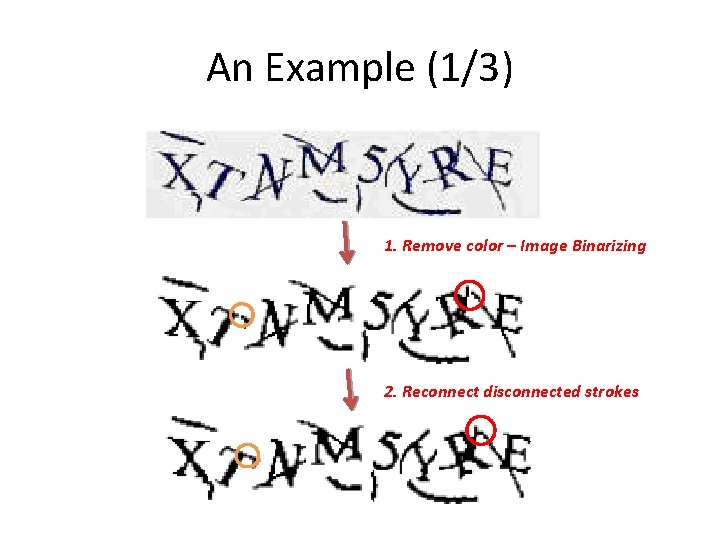
An Example (1/3) 1. Remove color – Image Binarizing 2. Reconnect disconnected strokes

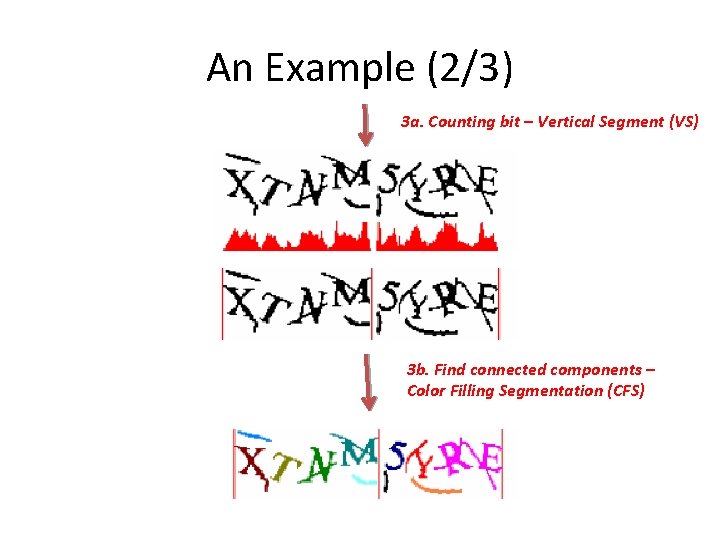
An Example (2/3) 3 a. Counting bit – Vertical Segment (VS) 3 b. Find connected components – Color Filling Segmentation (CFS)

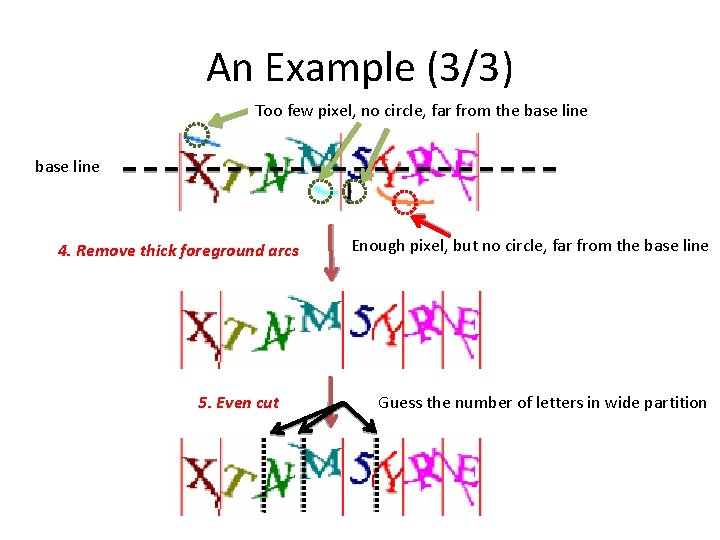
An Example (3/3) Too few pixel, no circle, far from the base line 4. Remove thick foreground arcs 5. Even cut Enough pixel, but no circle, far from the base line Guess the number of letters in wide partition

Experimental Result • Hardware – 1. 86 GHz Intel Core 2 CPU – 2 G RAM • Assume success rate >95% for recognizing individual character. • Use 500 random samples from websites. • 92% for segmentation attack on MSN scheme – Breaking rate > 0. 92 * (0. 95^8) = 61% • 77% for Yahoo CAPTCHA, average text length is 5 – Breaking rate > 0. 77 * (0. 95^5) = 60% • 12% for Google CAPTCHA, average text length is 6. 25 – Breaking rate > 0. 12 * (0. 95^6. 25) = 8. 7%

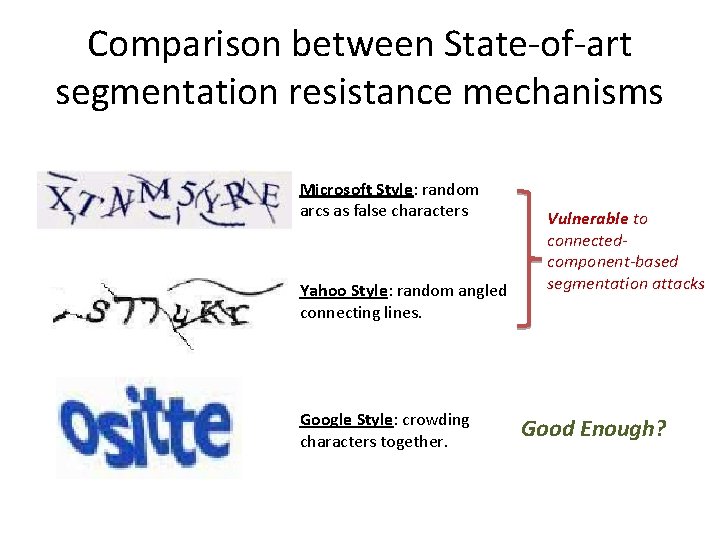
Comparison between State-of-art segmentation resistance mechanisms Microsoft Style: random arcs as false characters Yahoo Style: random angled connecting lines. Google Style: crowding characters together. Vulnerable to connectedcomponent-based segmentation attacks Good Enough?

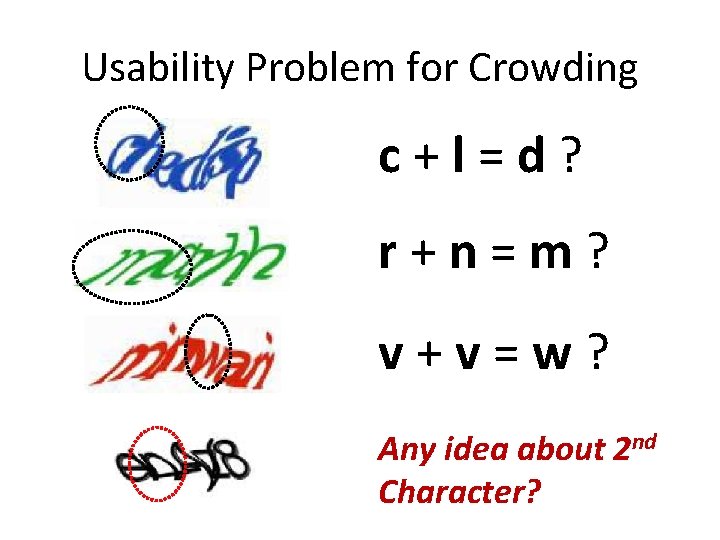
Usability Problem for Crowding c+l=d? r+n=m? v+v=w? Any idea about 2 nd Character?

Suggestion on Countermeasures • Crowding characters together is good, but should be used carefully to avoid confusing characters. • Make it harder to tell characters and arcs apart by juxtaposing them in any directions. • Make guessing the number of letters and even cut inefficient by using randomly varied widths for characters.

Conclusion • Segmentation resistance is a sound principle, but the design details are more critical. • This paper demonstrate new methods for evaluating the strength of segmentation resistance mechanisms. • Future work – Universal segmentation attack for all text-based CAPTCHAs – design a toolbox for evaluating the strength of CAPTCHAs

Q&A Thanks