1 Managed Security 2 Managed Security Managed Security














- Slides: 22

1 Managed Security

2 Managed Security • Managed Security provides a comprehensive suite of security services to manage and protect your network assets – – – Managed Firewall Secure Remote Access Remote Data Protection Asset Management Laptop Security Empower your business • Lower upfront capital resources • Simplify IT management • Reduce staff burden • Rapidly scale up and down Lower the time and cost of managing day-to-day IT operations, and free your IT budget and staff to focus on strategic initiatives.

Managed Firewall • Three options are provided for firewall services – Premises Based firewall • Designed for 1+ sites – Data Center Based firewall • Shared • Dedicated – Cloud Based firewall • Designed for 25+ sites Secure managed firewall to reduce Internet threats by stopping both inbound and outbound security threats. We lower cost and ensure that your most valuable and confidential information stays secure. 3

Premises Based Firewall • Managed firewall based on customer premises • Industry leading firewall devices – Juniper SRX series – Juniper SSG series – Sonic. WALL 4

Premises Based Firewall Options • Basic Option – – – Policy Management Backup/Restore Performance Monitoring Troubleshooting and Alerting 5 Policy Changes per month • Enhanced Option (Includes Basic Option plus) – – URL Filtering Web Content Filtering Application Control (Sonic. WALL Only) 10 Policy Changes per month • Premium Option (Includes Enhanced Option plus) – Customized Content Filtering and Application Control – Intrusion Detection (IDS) and Intrusion Prevention (IPS) 5

Data Center Based Firewall • Customer Firewall Based in Earth. Link data center – Similar firewall options as Premises based • Advanced firewall services ICB • Shared and dedicated options • Firewall solution designed to protect hosted services in the data center 6

Cloud Based Firewall • Cloud Based Firewall provides firewall services via the Earth. Link Business network – Only available via Earth. Link MPLS services of 25+ locations – Redundant network architecture built on Fortinet Forti. Gate platform • Atlanta, GA • Sunnyvale, CA 7

Cloud Based Firewall Options • Basic Option – Firewall with stateful inspection – NAT and PAT • Advanced Option (Include Basic Option plus) – URL filtering – Web Content filtering – Application Control • Premier Option (Includes Advanced Option plus) – Custom Content filtering – Data Leak Prevention – Intrusion Detection (IDS) and Intrusion Prevention (IPS) – Anti-Virus, Anti-Malware and Anti-Spyware 8

Firewall Reports • Cloud provides extensive standard reporting • Examples of Reports available – – – – Firewall IPS, IDS Anti-Virus, Anti-Malware, Anti-Spyware Web Content filtering Application Control Data Leak Prevention 9

Managed Firewall Benefits • Fully managed security solution – Experts on staff to support your business – Proactively maintain latest security patches • • Protects against theft Protects your key business information assets 24/7 Reduces need for security experts on staff Eliminates maintenance and management of customerowned firewall • Improves network performance by blocking data from non-approved sites, applications and content 10

Secure Remote Access • Provides remote access options to your network – Customers control adding or removing users – Restrict access based on security Access method for mobile users, telecommuters, small offices, provided as firewall feature or standalone. 11

Secure Remote Access Benefits • Secure connectivity • Improve employee productivity with network access while traveling • Improve business productivity with instant access to network and information 12

Remote Data Protection • Remote Data Protection provides data backup via the Internet and stores data in a remote data center for the following: – Servers – Desktops – Laptops • Back up your key business data Minimize cost while enabling you to prioritize recovery of your most critical operations in the event of a natural or man-made disaster, with round the clock real-time backups. 13

Remote Data Protection • • • Back up files seamlessly Supports: Windows, Mac, Linux Encrypts and compresses data Extensive scheduling options Easy to use – Customer manages users 14

Remote Data Protection Benefits • • Reduce vulnerability Reduce risk to your business Real-time 24/7/365 backups Rapid recovery anytime, anywhere 15

Asset Management • Manage network assets with a powerful asset management tool – Inventory management • Servers, Laptops, Desktops • Software – Patch Management – Remote Monitoring – Remote Control Ability to view and audit all PCs and devices in a centralized location to reduce cost, increase uptime and align your IT Security policies with the overall strategy of your business. 16

Asset Management • 3 Service Levels – Basic • Self Service – Enhanced • Co-managed – Premium • Fully Managed 17

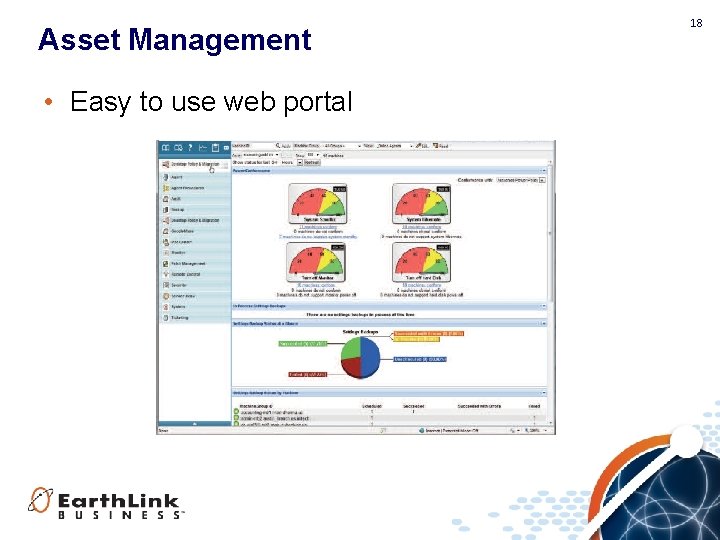
Asset Management • Easy to use web portal 18

Asset Management Benefits • Establish baseline of all hardware and software connected to your network • Deliver instant alerts on network device changes • Provide control and visibility to your infrastructure assets • Facilitate Acceptable Use Policy compliance 19

Laptop Security • Laptop Security provides protection for the information on your corporate laptops in event of theft or loss – Enforces encryption policies on Windows machines – Remotely wipes data off of hard drives A comprehensive and cost effective laptop security service. Automatically encrypts data and overwrites information in the event the device is reported lost or stolen. 20

Laptop Security Benefits • • Protect data against theft and misuse Mitigate risk of lawsuits Ensure regulatory compliance Adhere to acceptable use policy 21

Managed Security Benefits • Shifts the burden of security management from the customer to Earth. Link Business • Provides an outsourced security solution with 24/7 monitoring, protection and support • Reduces the amount of internal human resources a customer needs to manage network security and administration 22