Why Using XACML as one M 2 M




- Slides: 16

Why Using XACML as one. M 2 M Access Control Policy Group Name: WG 4 Source: Wei Zhou, CATT, zhouwei@catt. cn Meeting Date: <2014 -09 -22> Agenda Item: <agenda item topic name>

What is XACML • e. Xtensible Access Control Markup Language (XACML) is an XML-based access control language defined by the Organization for the Advancement of Structured Information Standards (OASIS). XACML access control framework conforms to the Attribute Based Access Control (ABAC). (Version 2. 0, 2005; Version 3. 0, 2013) • The one. M 2 M authorization system shall select XACML as its access control policy description language.

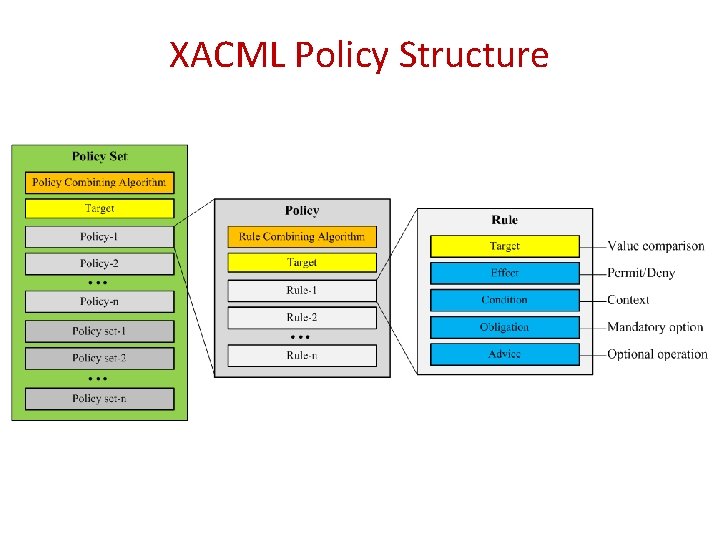
XACML Policy Structure

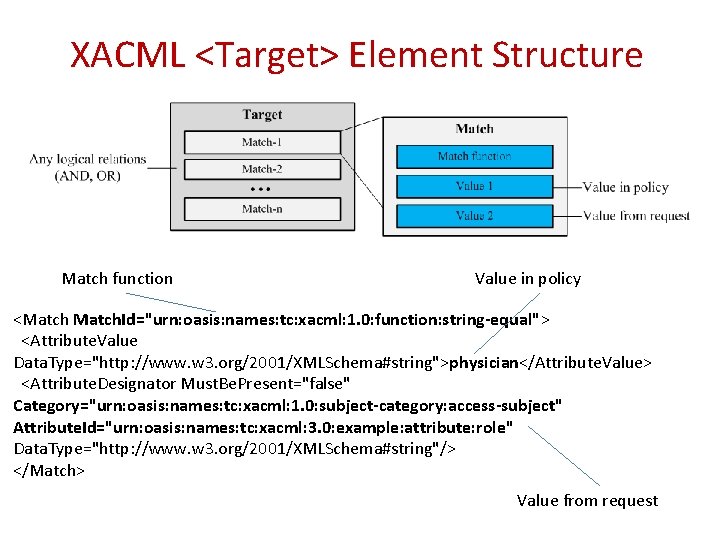
XACML <Target> Element Structure Match function Value in policy <Match. Id="urn: oasis: names: tc: xacml: 1. 0: function: string-equal"> <Attribute. Value Data. Type="http: //www. w 3. org/2001/XMLSchema#string">physician</Attribute. Value> <Attribute. Designator Must. Be. Present="false" Category="urn: oasis: names: tc: xacml: 1. 0: subject-category: access-subject" Attribute. Id="urn: oasis: names: tc: xacml: 3. 0: example: attribute: role" Data. Type="http: //www. w 3. org/2001/XMLSchema#string"/> </Match> Value from request

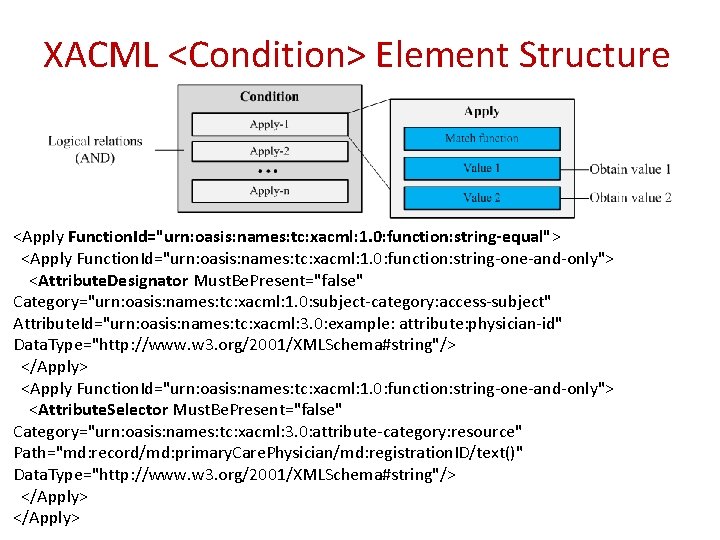
XACML <Condition> Element Structure <Apply Function. Id="urn: oasis: names: tc: xacml: 1. 0: function: string-equal"> <Apply Function. Id="urn: oasis: names: tc: xacml: 1. 0: function: string-one-and-only"> <Attribute. Designator Must. Be. Present="false" Category="urn: oasis: names: tc: xacml: 1. 0: subject-category: access-subject" Attribute. Id="urn: oasis: names: tc: xacml: 3. 0: example: attribute: physician-id" Data. Type="http: //www. w 3. org/2001/XMLSchema#string"/> </Apply> <Apply Function. Id="urn: oasis: names: tc: xacml: 1. 0: function: string-one-and-only"> <Attribute. Selector Must. Be. Present="false" Category="urn: oasis: names: tc: xacml: 3. 0: attribute-category: resource" Path="md: record/md: primary. Care. Physician/md: registration. ID/text()" Data. Type="http: //www. w 3. org/2001/XMLSchema#string"/> </Apply>

XACML Attribute Categories • Subject attribute category: Originator, Role, … • Resource attribute category: Resource URI, Creation time, … • Action attribute category: Retrieve, Update, … • Environment attribute category: current time, IP Address, … • It is extensible

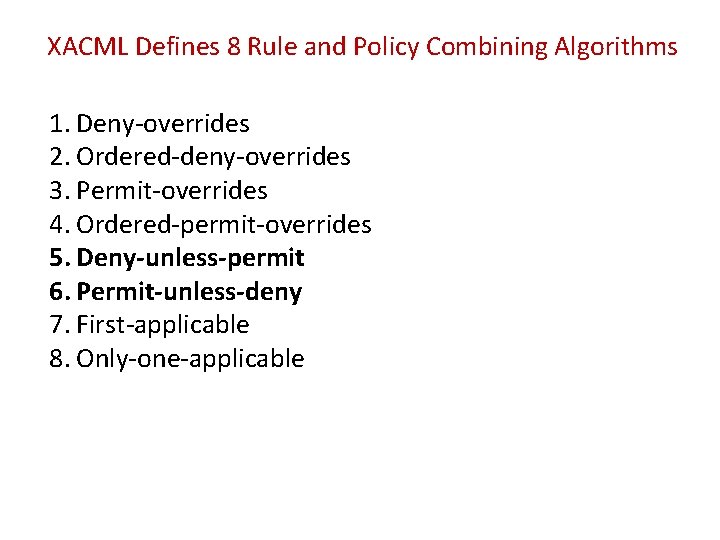
XACML Defines 8 Rule and Policy Combining Algorithms 1. Deny-overrides 2. Ordered-deny-overrides 3. Permit-overrides 4. Ordered-permit-overrides 5. Deny-unless-permit 6. Permit-unless-deny 7. First-applicable 8. Only-one-applicable

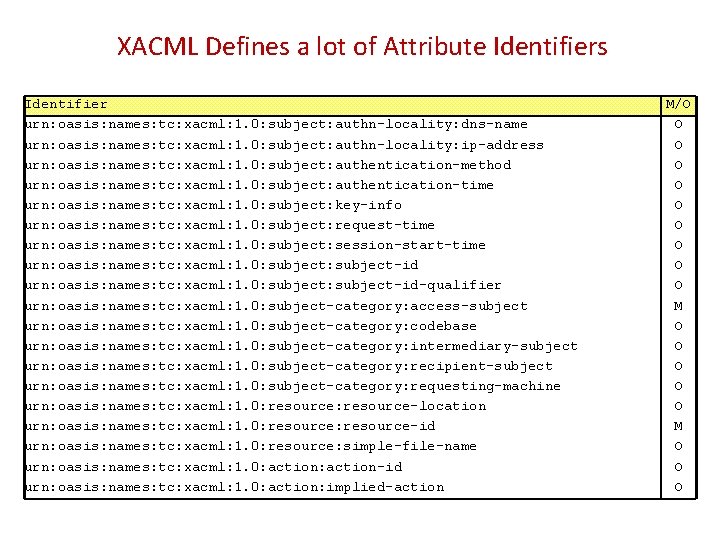
XACML Defines a lot of Attribute Identifiers Identifier urn: oasis: names: tc: xacml: 1. 0: subject: authn-locality: dns-name urn: oasis: names: tc: xacml: 1. 0: subject: authn-locality: ip-address urn: oasis: names: tc: xacml: 1. 0: subject: authentication-method urn: oasis: names: tc: xacml: 1. 0: subject: authentication-time urn: oasis: names: tc: xacml: 1. 0: subject: key-info urn: oasis: names: tc: xacml: 1. 0: subject: request-time urn: oasis: names: tc: xacml: 1. 0: subject: session-start-time urn: oasis: names: tc: xacml: 1. 0: subject: subject-id-qualifier urn: oasis: names: tc: xacml: 1. 0: subject-category: access-subject urn: oasis: names: tc: xacml: 1. 0: subject-category: codebase urn: oasis: names: tc: xacml: 1. 0: subject-category: intermediary-subject urn: oasis: names: tc: xacml: 1. 0: subject-category: recipient-subject urn: oasis: names: tc: xacml: 1. 0: subject-category: requesting-machine urn: oasis: names: tc: xacml: 1. 0: resource-location urn: oasis: names: tc: xacml: 1. 0: resource-id urn: oasis: names: tc: xacml: 1. 0: resource: simple-file-name urn: oasis: names: tc: xacml: 1. 0: action-id urn: oasis: names: tc: xacml: 1. 0: action: implied-action M/O O O O O M O O O

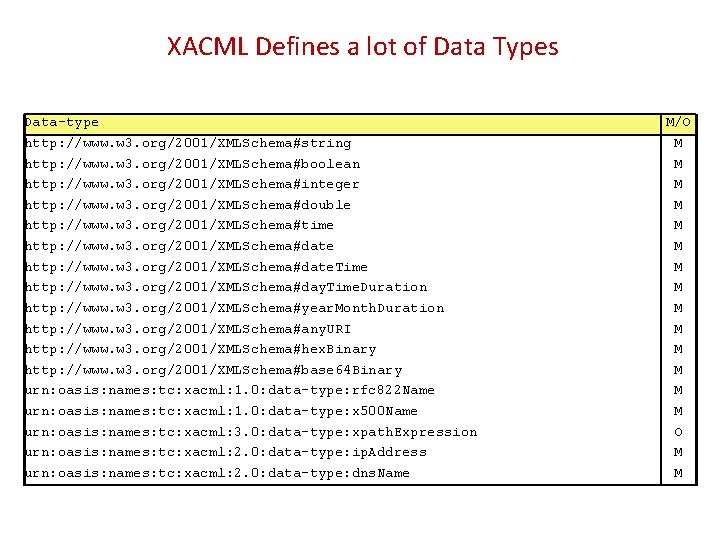
XACML Defines a lot of Data Types Data-type http: //www. w 3. org/2001/XMLSchema#string http: //www. w 3. org/2001/XMLSchema#boolean http: //www. w 3. org/2001/XMLSchema#integer http: //www. w 3. org/2001/XMLSchema#double http: //www. w 3. org/2001/XMLSchema#time http: //www. w 3. org/2001/XMLSchema#date. Time http: //www. w 3. org/2001/XMLSchema#day. Time. Duration http: //www. w 3. org/2001/XMLSchema#year. Month. Duration http: //www. w 3. org/2001/XMLSchema#any. URI http: //www. w 3. org/2001/XMLSchema#hex. Binary http: //www. w 3. org/2001/XMLSchema#base 64 Binary urn: oasis: names: tc: xacml: 1. 0: data-type: rfc 822 Name urn: oasis: names: tc: xacml: 1. 0: data-type: x 500 Name urn: oasis: names: tc: xacml: 3. 0: data-type: xpath. Expression urn: oasis: names: tc: xacml: 2. 0: data-type: ip. Address urn: oasis: names: tc: xacml: 2. 0: data-type: dns. Name M/O M M M M O M M

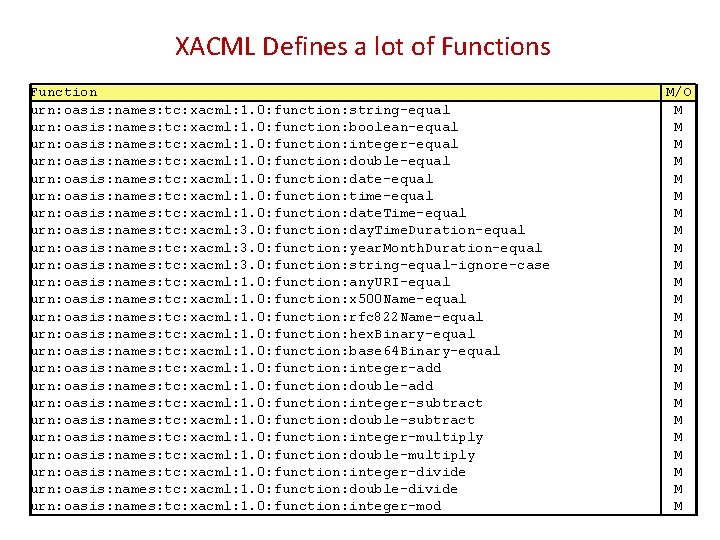
XACML Defines a lot of Functions Function urn: oasis: names: tc: xacml: 1. 0: function: string-equal urn: oasis: names: tc: xacml: 1. 0: function: boolean-equal urn: oasis: names: tc: xacml: 1. 0: function: integer-equal urn: oasis: names: tc: xacml: 1. 0: function: double-equal urn: oasis: names: tc: xacml: 1. 0: function: date-equal urn: oasis: names: tc: xacml: 1. 0: function: time-equal urn: oasis: names: tc: xacml: 1. 0: function: date. Time-equal urn: oasis: names: tc: xacml: 3. 0: function: day. Time. Duration-equal urn: oasis: names: tc: xacml: 3. 0: function: year. Month. Duration-equal urn: oasis: names: tc: xacml: 3. 0: function: string-equal-ignore-case urn: oasis: names: tc: xacml: 1. 0: function: any. URI-equal urn: oasis: names: tc: xacml: 1. 0: function: x 500 Name-equal urn: oasis: names: tc: xacml: 1. 0: function: rfc 822 Name-equal urn: oasis: names: tc: xacml: 1. 0: function: hex. Binary-equal urn: oasis: names: tc: xacml: 1. 0: function: base 64 Binary-equal urn: oasis: names: tc: xacml: 1. 0: function: integer-add urn: oasis: names: tc: xacml: 1. 0: function: double-add urn: oasis: names: tc: xacml: 1. 0: function: integer-subtract urn: oasis: names: tc: xacml: 1. 0: function: double-subtract urn: oasis: names: tc: xacml: 1. 0: function: integer-multiply urn: oasis: names: tc: xacml: 1. 0: function: double-multiply urn: oasis: names: tc: xacml: 1. 0: function: integer-divide urn: oasis: names: tc: xacml: 1. 0: function: double-divide urn: oasis: names: tc: xacml: 1. 0: function: integer-mod M/O M M M M M M

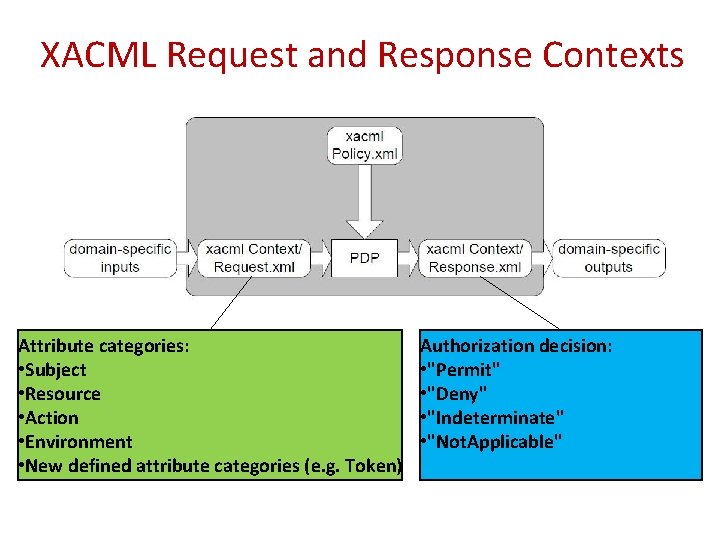
XACML Request and Response Contexts Attribute categories: • Subject • Resource • Action • Environment • New defined attribute categories (e. g. Token) Authorization decision: • "Permit" • "Deny" • "Indeterminate" • "Not. Applicable"

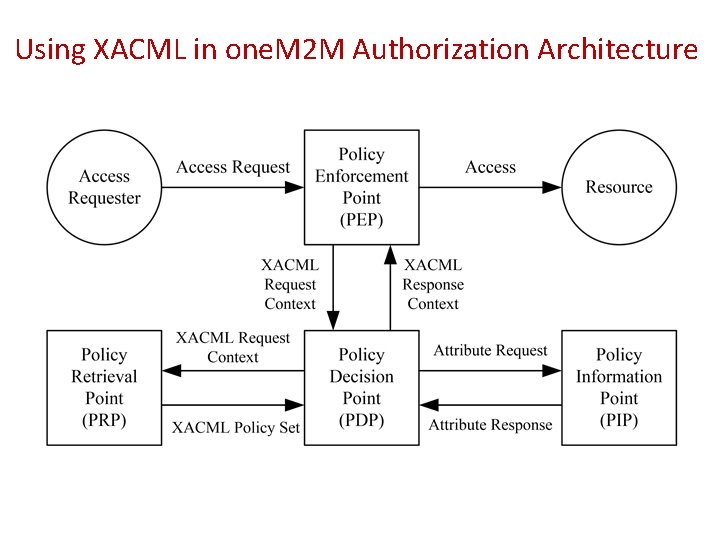
Using XACML in one. M 2 M Authorization Architecture

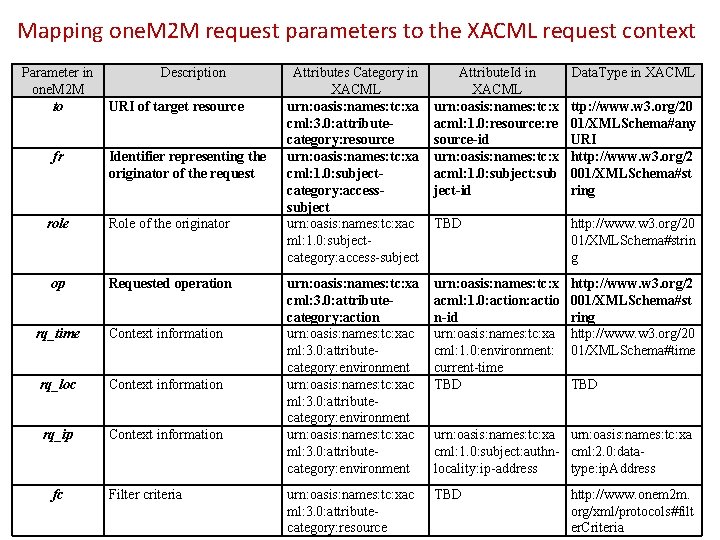
Mapping one. M 2 M request parameters to the XACML request context Parameter in one. M 2 M to fr Description URI of target resource Identifier representing the originator of the request role Role of the originator op Requested operation rq_time Context information rq_loc Context information rq_ip Context information fc Filter criteria Attributes Category in XACML urn: oasis: names: tc: xa cml: 3. 0: attributecategory: resource urn: oasis: names: tc: xa cml: 1. 0: subjectcategory: accesssubject urn: oasis: names: tc: xac ml: 1. 0: subjectcategory: access-subject Attribute. Id in XACML urn: oasis: names: tc: x acml: 1. 0: resource: re source-id urn: oasis: names: tc: x acml: 1. 0: subject: sub ject-id Data. Type in XACML TBD http: //www. w 3. org/20 01/XMLSchema#strin g urn: oasis: names: tc: xa cml: 3. 0: attributecategory: action urn: oasis: names: tc: xac ml: 3. 0: attributecategory: environment urn: oasis: names: tc: x acml: 1. 0: action: actio n-id urn: oasis: names: tc: xa cml: 1. 0: environment: current-time TBD http: //www. w 3. org/2 001/XMLSchema#st ring http: //www. w 3. org/20 01/XMLSchema#time urn: oasis: names: tc: xac ml: 3. 0: attributecategory: resource TBD ttp: //www. w 3. org/20 01/XMLSchema#any URI http: //www. w 3. org/2 001/XMLSchema#st ring TBD urn: oasis: names: tc: xa cml: 1. 0: subject: authn- cml: 2. 0: datalocality: ip-address type: ip. Address http: //www. onem 2 m. org/xml/protocols#filt er. Criteria

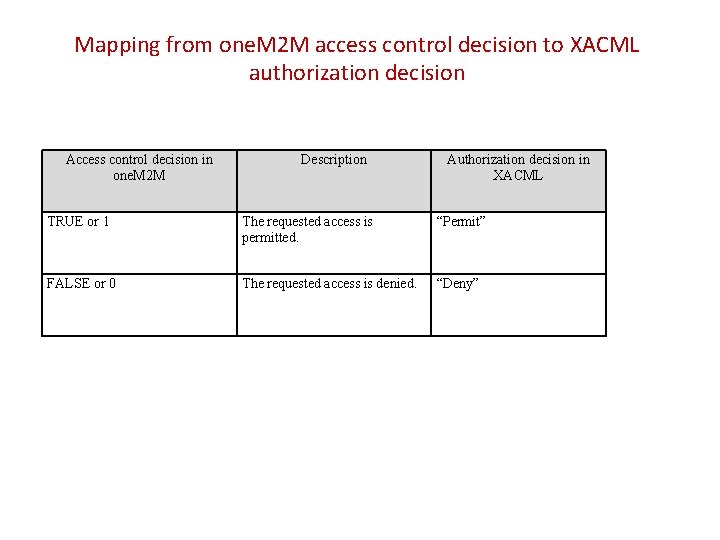
Mapping from one. M 2 M access control decision to XACML authorization decision Access control decision in one. M 2 M Description Authorization decision in XACML TRUE or 1 The requested access is permitted. “Permit” FALSE or 0 The requested access is denied. “Deny”

XACML is Extensible Example of adding role and token in XACML request context <Attributes Category="urn: oasis: names: tc: xacml: 1. 0: subjectcategory: access-subject"> <Attribute Include. In. Result="false" Attribute. Id="urn: onem 2 m: names: attribute: role" Issuer="onem 2 m. example. com"> <Attribute. Value Data. Type="http: //www. w 3. org/2001/XMLSchema#string" >002 -Device Configuration</Attribute. Value> </Attribute> <Attribute Include. In. Result="false" Attribute. Id="urn: onem 2 m: names: attribute: token" Issuer="onem 2 m. example. com"> <Attribute. Value Data. Type="http: //www. w 3. org/2001/XMLSchema#base 64 Binary">TWFu. IGlz. IGR pc 3 Rpbmd 1 a. XNo. ZWQs. IG 5 vd. CBvbmx 5 IGJ 5 IGhpcy. By. ZWFzb 24 s. IGJ 1 d. CBie. SB 0 a. Glz. IHN pbmd 1 b. GFy. IHBhc 3 Npb 24 g. Zn. Jvb. SBvd. Ghlci. Bhbmlt. YWxz. LCB 3 a. Glja. CBpcy. Bh. IGx 1 c 3 Q gb 2 Ygd. Ghl. IG 1 pbm. Qs. IHRo. YXQg. Ynkg. YSBw. ZXJz. ZXZlcm. Fu. Y 2 Ugb 2 Yg. ZGVsa. Wdod. CBpbi. B 0 a. GUg. Y 29 ud. Glud. WVk. IGFu. ZCBpbm. Rl. Zm. F 0 a. Wdh. Ymxl. IGdlbm. Vy. YXRpb 24 gb 2 Yga 25 vd 2 x l. ZGdl. LCBle. GNl. ZWRz. IHRo. ZSBza. G 9 yd. CB 2 ZWhlb. WVu. Y 2 Ugb 2 Yg. YW 55 IGNhcm 5 hb. CBwb. GV hc 3 Vy. ZS 4= </Attribute. Value> </Attributes>

What we should do if XACML is used in one. M 2 M • Defining new attribute IDs, e. g. attribute ID for role • Defining new attribute categories, e. g. security token • Defining new functions, e. g. functions for location and wildcard matching. • And so on…