SAML XACML the Terrorism Information Sharing Environment Martin



- Slides: 8

SAML, XACML & the Terrorism Information Sharing Environment Martin Smith Program Manager for IT Information Sharing DHS CIO Office “Interoperable Trust Networks” Justice GLOBAL April 28, 2005 v. 20050428 b

The Information-Sharing Environment: Vision of Executive Order 13356 l EO 13356, Aug 27, 2004, called for “establishment of an interoperable terrorism information sharing environment to facilitate automated sharing of terrorism information” l Interagency group in homeland-security mission space (OMB Chair, DHS, IC, DOD, DOJ, others) delivered recommendations to President 12/24/2004 l Vision was a National shared information-sharing “environment”, based on SOA l “Environment”, not “network”: boundary defined by flexible access control Version: 20050428 b 2

Access-Control Requirements l “Federated” to support common pool of credentials, roles, permissions with distributed maintenance – “harvest” existing trust relationships at Federal, regional and local levels l Fine-grained: for this application, need accountability to individual person and individual transaction – sharing requires control – comprehensive audit capability l Beyond RBAC, to ABAC and PBAC Version: 20050428 b 3

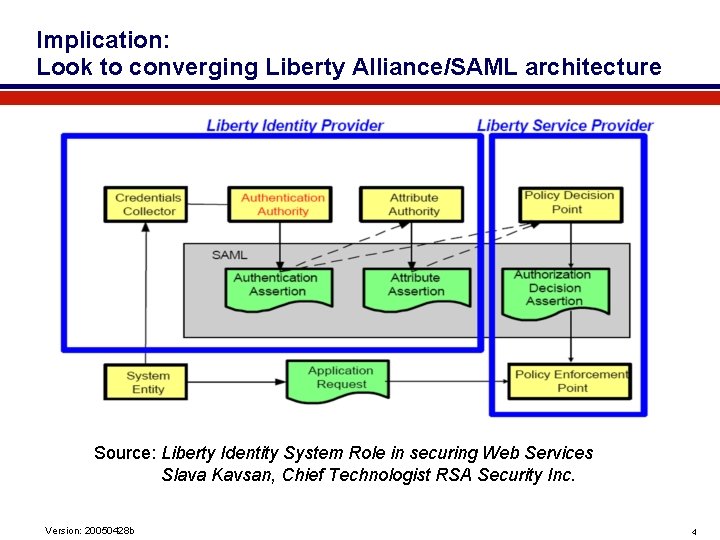
Implication: Look to converging Liberty Alliance/SAML architecture Source: Liberty Identity System Role in securing Web Services Slava Kavsan, Chief Technologist RSA Security Inc. Version: 20050428 b 4

Key XML Standard: Security Assertion Markup Language (SAML) l Basis for exchanging detailed info (credentials, attributes, preferences) to support access decisions l Architecture includes federation capability l Standardization status - – 02 -Sept-2003: SAML V 1. 1 approved as an OASIS Standard. – 16 -Feb-2005: Voting begins on approval of SAML V 2. 0 specifications and schemas as OASIS Standard. Ballot closes 28 -Feb-2005 – SAML V 1. 1 not backwardly compatible with V 1. 0 Version: 20050428 b 5

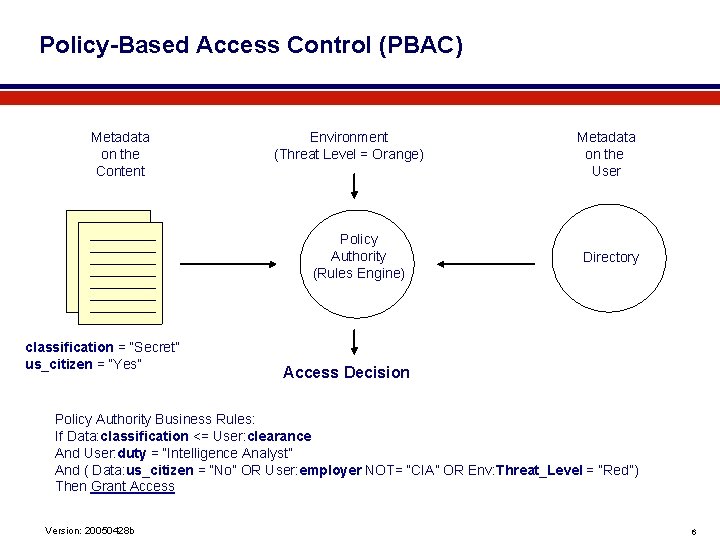
Policy-Based Access Control (PBAC) Metadata on the Content Environment (Threat Level = Orange) Policy Authority (Rules Engine) classification = “Secret” us_citizen = “Yes” Metadata on the User Directory Access Decision Policy Authority Business Rules: If Data: classification <= User: clearance And User: duty = “Intelligence Analyst” And ( Data: us_citizen = “No” OR User: employer NOT= “CIA” OR Env: Threat_Level = “Red”) Then Grant Access Version: 20050428 b 6

More on PBAC l l Framework to determine appropriate distribution (mandatory access control and need-to-know), required to automate access decisions – Three sources of data (about the content; about the requestor; about the environment or situation) plus policy rule-set – Key assertion: the distribution decision is not made by the data custodian – “Separation of concerns”: originator is expert on the content; directory holds user credentials and roles; policy is created by management Benefits of implementing the model for the sharing environment – Order-of-magnitude gain in speed, cost & consistency of decisions – Instant, consistent response to changes in environment or in policy – Can be implemented gradually, via “refer to human decision” option – Superior alternative to originator control, can be enforced via digital rights management technologies – Automated process can provide full audit, data for process improvement Version: 20050428 b 7

Key XML Standard: Extensible Access-Control Markup Language (XACML) l Supports greatly increased complexity of access-control decisions: capable of applying “business rules” and not just roles – “provide a method for basing an authorization decision on attributes of the subject and resource. ” – designed to be used by “policy decision points” in Liberty/SAML architecture l Not the only policy language, but leading contender for access-control application – access control ~= digital rights management l Standardization status - – XACML 2. 0 and all the associated profiles approved as OASIS Standards on 1 February 2005 – e. Xtensible Access Control Markup Language (XACML) Version 1. 0 OASIS Standard, 18 February 2003 Version: 20050428 b 8