Whats New in Security with Dynamics 365 for









- Slides: 17

What’s New in Security with Dynamics 365 for Operations? Alex Meyer Director of AX/D 365 FO Development Fastpath, Inc. meyer@gofastpath. com Twitter: @alexmeyer_ITGuy

Agenda • • Welcome AX 2009 Security Model Overview AX 2012 Security Model Overview D 365 FO Security Model Overview Security Development Tool User Licensing Demo Questions

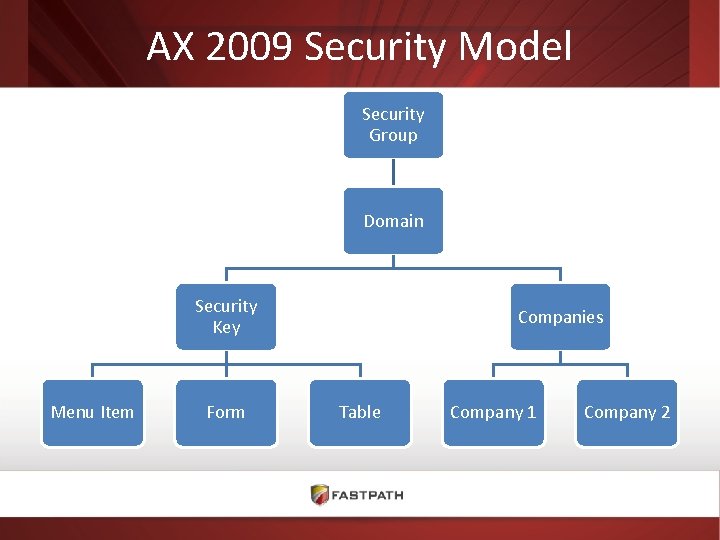
AX 2009 Security Model Security Group Domain Security Key Menu Item Form Companies Table Company 1 Company 2

AX 2009 Security Model • • • No out of box security groups Security Keys Domains control company access Optimistic security model Explicitly set table access Development security keys

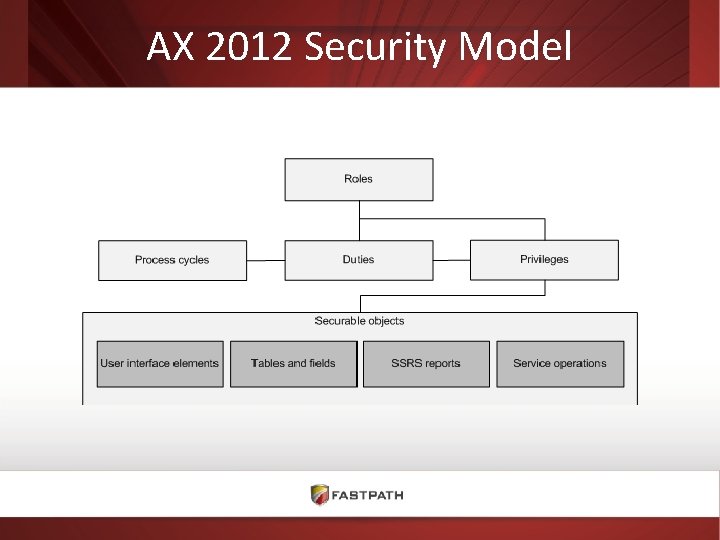
AX 2012 Security Model

AX 2012 Security Model • AX 2012 – – – Pessimistic security model Template Roles, Duties, Privileges are delivered Roles are system wide User roles can be restricted by legal entity Record level security is available • Replaced by Extensible Data Security (XDS) Policies – Setup users via Active Directory Groups – Security reports – limited • Dynamics 365 – Follows the same security model with minor differences

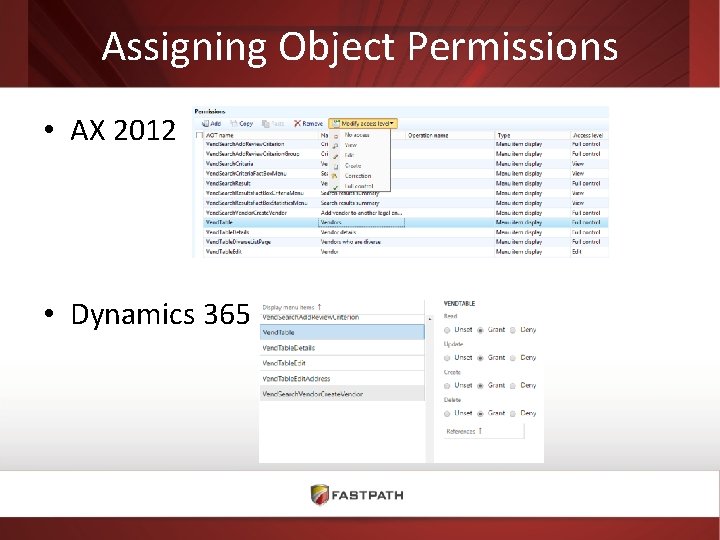
Assigning Object Permissions • AX 2012 • Dynamics 365

Environment Differences • In AX 2012, design time and runtime environments lived on same machine • In D 365 FO, design time lives completely separate from runtime • What does this mean for developing security?

Dynamics 365 Data Security • Transparent Data Encryption – Data and logs in Azure SQL are encrypted at rest • Table Permissions Framework (TPF) – Used for High Business Impact (HBI) data – Users must be given explicit access to field otherwise it will be hidden – Can be applied at field level • Extensible Data Security (XDS) still available

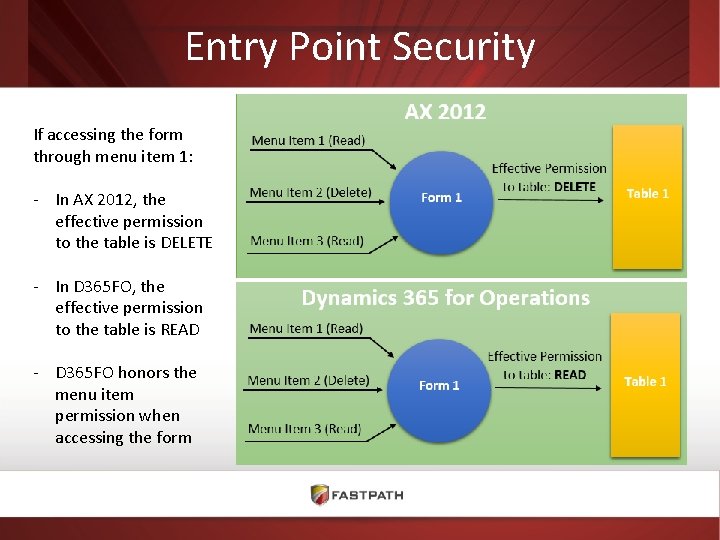
Entry Point Security If accessing the form through menu item 1: - In AX 2012, the effective permission to the table is DELETE - In D 365 FO, the effective permission to the table is READ - D 365 FO honors the menu item permission when accessing the form

Data Entities • New to Dynamics 365 • Encapsulates a business concept that may exist across multiple tables with Dynamics 365 • Allows for easy CRUD operations (especially from outside of Dynamics 365) • Template Data Entities come out of the box, can create customized ones as well • Have their own security property called Integration Mode

Security Development Tool in AX • • ‘Beta’ tool from Microsoft Security reporting Task Recording Test workspace – Reduces need for test user accounts – Limitations • Cannot open test multi-role assignment (Can use sub-roles) • Does not work if you use AD Groups for user provisioning • Licensing • D 365 – Where’d it go?

Common Security Challenges • Access security is low priority for project team • Everyone assigned System Administrator • Security is in the domain of IT/Sys Admin not BPOs • Expensive customizations in place of security • No consideration for segregation of duties • Process controls not part of the design • Dilution of ‘go-live’ security design

Reviewing Security • • Take a risk based approach to reviews Monitor and report on user access BPOs should review access Update process controls and SOD rules to reflect security changes

Links • • • • Dynamics 365 For Operations Blog (Personal Blog) You. Tube Tutorial on Simulating the Security Development Tool in Dynamics 365 for Operations (5: 35) D 365 Wiki Task Recorder in Microsoft Dynamics 365 for Operations Security Development Tool User Guide Microsoft Dynamics AX 2012 R 3 Licensing Guide Introduction to Microsoft Dynamics 365 licensing Dynamics AX Server Team Blog Role-based Security Use Patterns for Developers Developing Extensible Data Security Policies Security Roles & Licensing Whitepaper Table Permissions Framework Transparent Data Encryption Understanding Security in Microsoft Dynamics AX 2009

Fastpath for Dynamics AX/365 Fastpath ensures our customers can confidently answer these three critical questions: Who has access to their systems? Assure Segregation of Duties and Security Access Reviews What did they do with that access? Audit Trail Track changes to Critical Data Where are they vulnerable? Identity Manager Provision Users and Assign Temporary Access

Questions? Alex Meyer Director of AX/D 365 FO Development Fastpath, Inc. meyer@gofastpath. com Twitter: @alexmeyer_ITGuy