UT DALLAS Erik Jonsson School of Engineering Computer














- Slides: 33

UT DALLAS Erik Jonsson School of Engineering & Computer Science Randomizing Smartphone Malware Profiles against Statistical Mining Techniques Abhijith Shastry Murat Kantarcioglu Yan Zhou Bhavani Thuraisingham FEARLESS engineering

Outline • • • Introduction Related Work Smartphone Malware Development Attacking Statistical Data Mining Tools Experimental Results Conclusions FEARLESS engineering

Introduction • Smartphone usage: – – Calling Web browsing Social networking Online banking FEARLESS engineering

Introduction (cont. ) • Smartphone OS: – – i. OS Android Symbian Microsoft windows phone OS FEARLESS engineering

Introduction (cont. ) • Common malicious activities on smartphones – – – – Collecting user information (61%) Sending premium-rate SMS messages (52%) Amusement Credential theft SMS spam Search engine optimization Ransom FEARLESS engineering

Introduction (cont. ) • Smartphone Defense Mechanisims – Application permission (Android) – Review (i. OS) – Review and sign (Symbian) FEARLESS engineering

Introduction (cont. ) • Smartphone application market – Apple app store • Applications are reviewed by Apple for security • Disallow personal spyware – Android market • Users can install applications from unofficial markets • Google does not review applications prior their listing • Google can remotely uninstall known malware from users’ devices – Nokia Ovi • Symbian does not prevent or discourage users from installing applications from other sources. • Symbian provides application signing services; only signed applications have permission to access dangerous privileges FEARLESS engineering

Introduction (cont. ) • User-approved permissions – Android: user-approved install-time permissions control access to the phone’s number, contact lists, camera, blue tooth, etc. – i. OS: requires user approval to access location and send notifications at runtime rather than installation time – Symbian: user permission is needed to install unsigned apps. FEARLESS engineering

Introduction (cont. ) • Smartphone malware incentives – Amusement – Selling user informaiton • Applications query mobile APIs for user’s location, lists of contacts, browser and download history, list of installed apps, IMEI (unique device id), inter-application data theft – Steal user credentials • Bank account credentials ($1000), credit card number ($25), email account password ($30) • Intercepting SMS messages, phishing, keylogging and document scanning – Premium rate calls and SMS • Android and Symbian, premium SMS can be sent completely unnoticed – SMS spam, search engine optimization, blackmail FEARLESS engineering

Introduction (cont. ) • Root exploit – Available 74% lifetime of a smartphone – Become available on average 5. 2 days after a firmware version – Prior to or on the official release date FEARLESS engineering

Introduction (cont. ) • Incentives for root exploits – Restricted app distributions – Users cannot perform complete system backup – Restrictions on sharing internet connetions with computers – Users cannot remove pre-installed apps – Users cannot install custom versions of the OS FEARLESS engineering

Introduction (cont. ) • Smartphone malware activities – eavesdropping on phone calls – reading e-mail and call-logs – tracking callers’ locations • Malware detection techniques – Static analysis – Dynamic analysis FEARLESS engineering

Related Work • Permission-based behavioral foot-printing (Zhou et al. ) • Behavior checker (Yap and Ewe) • Power signature (Kim et al. ) • Association rules and frequent episodes (Lee and Stolfo) FEARLESS engineering

Smartphone Malware Development • Android platform (Samsung Captivate) – We assume that either through a direct installation or an indirect installation (through the payload of a benign application), the victim’s mobile phone is infected with the developed malware • Six parameterized malware programs – Privacy intrusion – Information theft – Denial-of-service FEARLESS engineering

Smartphone Malware Development (cont. ) • Call recorder – Eavesdropping on incoming and outgoing calls – Recorded files stored locally or uploaded to a remote server – Parameters: max_duration, max_filesize, num_skipped_calls, interval_record, interval_sleep, _upload, delete_local FEARLESS engineering

Smartphone Malware Development (cont. ) • Smart recorder – Eavesdropping on specific phone numbers on both incoming and outgoing calls – Specific phone numbers can be changed at runtime – Phone numbers are stored on a remote server and the recorded phone calls are uploaded to the server – Parameters: max_duration, max_filesize, num_skipped_calls, interval_record, interval_sleep FEARLESS engineering

Smartphone Malware Development (cont. ) • Mass Uploader – Upload contents of memory to the server – Also download contents from a remote server – Parameters: upload/download_BW, upload/download_interval, upload/download_inter_lim FEARLESS engineering

Smartphone Malware Development (cont. ) • Do. S – Spawn a large number of threads, each performing expensive multiplications – Freeze smartphone with 200 threads – Parameters: max_threads, num_multiplications, interval_restart, interval_sleep FEARLESS engineering

Smartphone Malware Development (cont. ) • Spy recorder – Remotely turn on the microphone and start recording any voice input – Initiated and terminated by a phone call from a specific number – Microphone is turned on when a call comes from the number and the call is automatically rejected afterwards – User is notified – Parameters: max_duration, max_filesize, inverval_record, interval_sleep, _upload, delete_local FEARLESS engineering

Smartphone Malware Development (cont. ) • Spy camera – – Taking snap shots from the camera Pictures uploaded to a remote server User is notified when pictures are taken Parameters: snap_interval, pic_dsample_ratio, pic_comp_quality, _upload, delete_local FEARLESS engineering

Attacking Statistical Data Mining Tools • Data mining tools – – – Decision Tree Logistic Regression Naïve Bayes Artificial neural network Support vector machine • Common assumption – training data and test data are identically independently distributed (iid). FEARLESS engineering

Attacking Statistical Data Mining Tools (cont. ) • Randomizing malware profiles – Malware parameters are randomized with an expected mean value. – Each randomized malware profile varies from the other with respect to the amount of deviation from the mean value of a parameter. • For example, Randx refers to a profile in which the variance from the mean value of the parameters is x. – Randomized profiles violate the iid assumption. FEARLESS engineering

Experimental Results • Data collection – Recording run-time behavior of applications – Features including CPU consumption, network traffic, memory usage, power, etc. – Features are recorded every five seconds and stored in a database on the mobile phone. • Data sets – 20 benign apps • 10 tools, 10 games – 6 malware programs plus their randomized profiles FEARLESS engineering

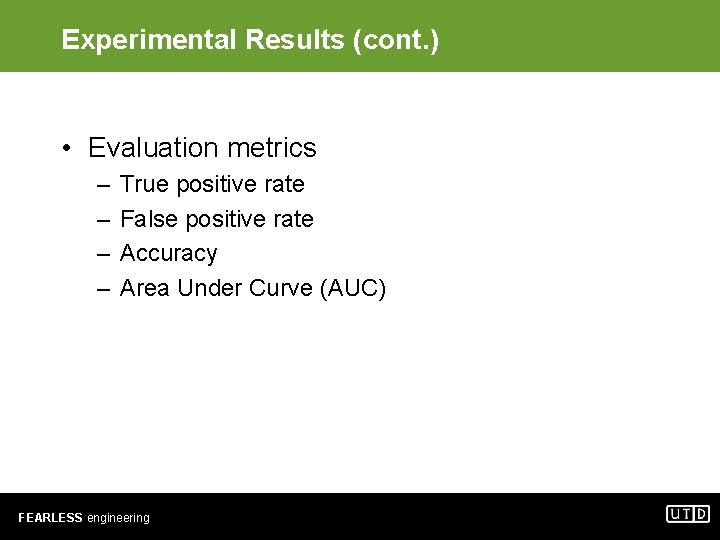
Experimental Results (cont. ) • Evaluation metrics – – True positive rate False positive rate Accuracy Area Under Curve (AUC) FEARLESS engineering

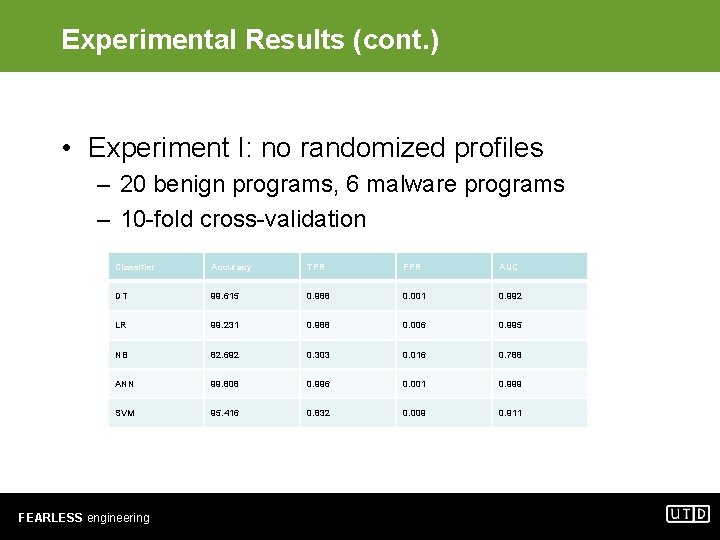
Experimental Results (cont. ) • Experiment I: no randomized profiles – 20 benign programs, 6 malware programs – 10 -fold cross-validation Classifier Accuracy TPR FPR AUC DT 99. 615 0. 988 0. 001 0. 992 LR 99. 231 0. 988 0. 006 0. 995 NB 82. 692 0. 303 0. 016 0. 788 ANN 99. 808 0. 996 0. 001 0. 999 SVM 95. 416 0. 832 0. 009 0. 911 FEARLESS engineering

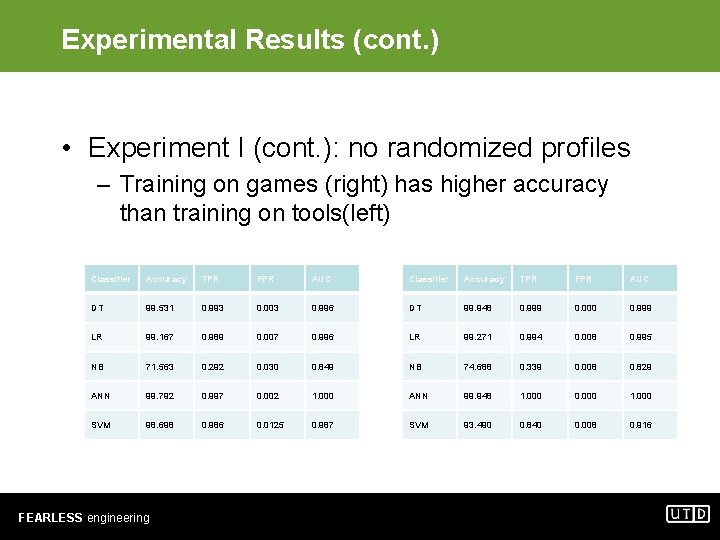
Experimental Results (cont. ) • Experiment I (cont. ): no randomized profiles – Training on games (right) has higher accuracy than training on tools(left) Classifier Accuracy TPR FPR AUC DT 99. 531 0. 993 0. 003 0. 996 DT 99. 948 0. 999 0. 000 0. 999 LR 99. 167 0. 989 0. 007 0. 996 LR 99. 271 0. 994 0. 008 0. 995 NB 71. 563 0. 292 0. 030 0. 849 NB 74. 688 0. 339 0. 008 0. 829 ANN 99. 792 0. 997 0. 002 1. 000 ANN 99. 948 1. 000 0. 000 1. 000 SVM 98. 698 0. 986 0. 0125 0. 987 SVM 93. 490 0. 840 0. 008 0. 916 FEARLESS engineering

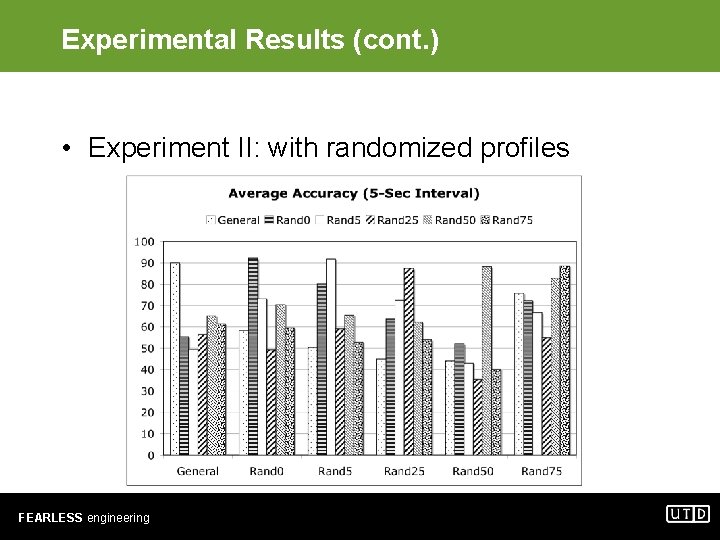
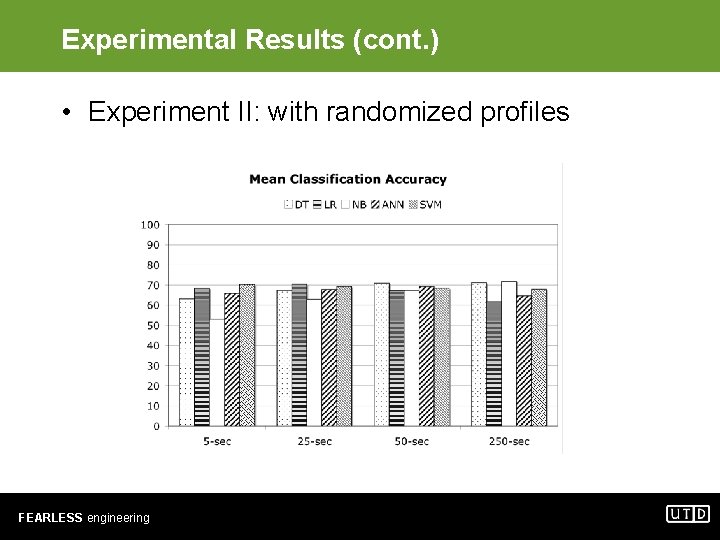
Experimental Results (cont. ) • Experiment II: with randomized profiles FEARLESS engineering

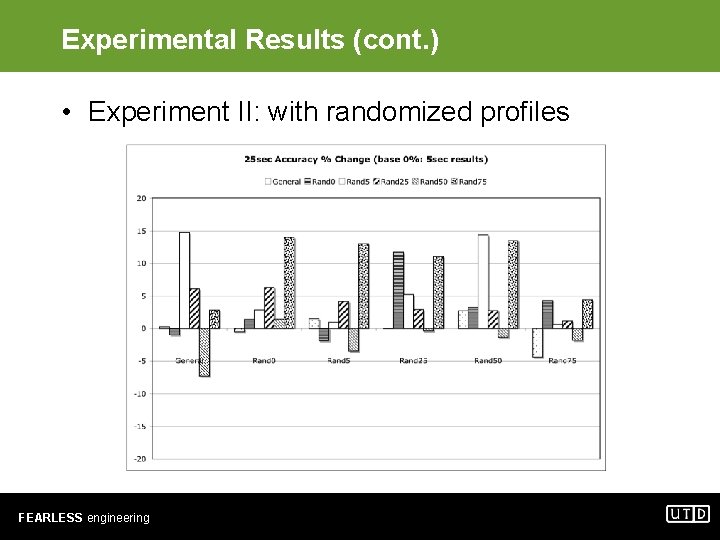
Experimental Results (cont. ) • Experiment II: with randomized profiles FEARLESS engineering

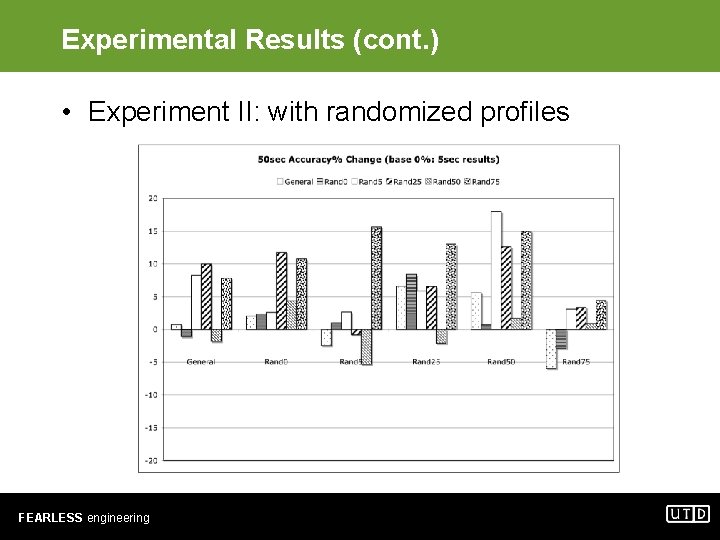
Experimental Results (cont. ) • Experiment II: with randomized profiles FEARLESS engineering

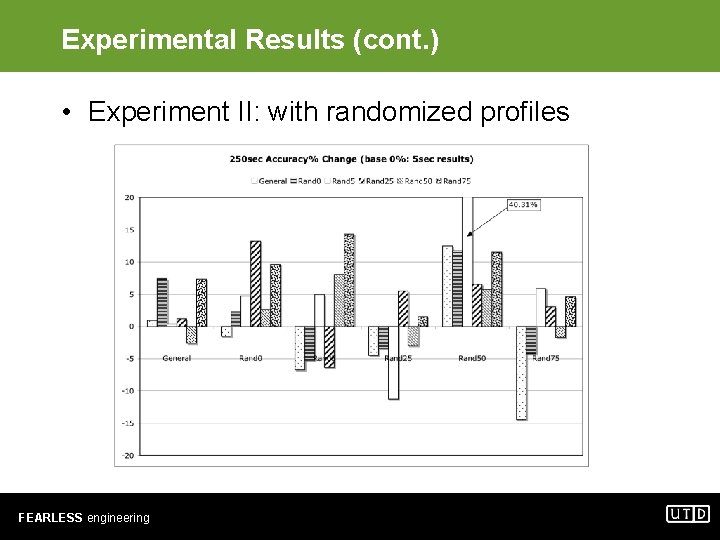
Experimental Results (cont. ) • Experiment II: with randomized profiles FEARLESS engineering

Experimental Results (cont. ) • Experiment II: with randomized profiles FEARLESS engineering

Experimental Results (cont. ) • Experiment II: observations – No consistent winner – When training set does not contain randomized malware profiles, accuracy is limited to below 70%. – When training set contains Randx and test set contains Randy, good accuracy is obtained only when x ≈ y. – Averaging samples in 25 -sec durations helps improve predictive accuracy. Longer durations do not result in further improvement. FEARLESS engineering

Conclusions • We developed six custom parameterized malware programs on the Android platform. • We demonstrate that data mining algorithms are vulnerable to attacks with randomized malware profiles. • We also demonstrate that simple consolidation may effectively improve classification performance. FEARLESS engineering
 Erik jonsson school of engineering and computer science
Erik jonsson school of engineering and computer science Erik jonsson school of engineering and computer science
Erik jonsson school of engineering and computer science Erik jonsson school of engineering
Erik jonsson school of engineering Weitzel and jonsson’s model of organizational decline
Weitzel and jonsson’s model of organizational decline Lars jonsson uppsala
Lars jonsson uppsala Ets6
Ets6 Computer based system engineering in software engineering
Computer based system engineering in software engineering Klipsch school of electrical and computer engineering
Klipsch school of electrical and computer engineering Tams sat score
Tams sat score Progressive era
Progressive era Cherry valance character traits
Cherry valance character traits Iec dallas pay scale
Iec dallas pay scale Mark bailey dallas theological seminary
Mark bailey dallas theological seminary Doing business in dallas
Doing business in dallas Dfwima
Dfwima Venacure dallas
Venacure dallas Loop 9 schematics
Loop 9 schematics Veterinary radiology dallas county
Veterinary radiology dallas county Ut dallas hr
Ut dallas hr Dallas crown horse slaughter plant
Dallas crown horse slaughter plant Dallas midwife associates
Dallas midwife associates Johnny cade physical traits
Johnny cade physical traits Safpf dallas county
Safpf dallas county Dallas best robotics
Dallas best robotics Dr kogut dallas
Dr kogut dallas Sprinkles dallas
Sprinkles dallas Cfa society dallas
Cfa society dallas Physical features of texas
Physical features of texas Dallas arboretum staff
Dallas arboretum staff Criterios de dallas
Criterios de dallas Dallas willard healing the heart
Dallas willard healing the heart Federal reserve bank of atlanta careers
Federal reserve bank of atlanta careers Dallas 63
Dallas 63 Practice lab taxslayer
Practice lab taxslayer