The Secrecy of Compressed Sensing Measurements Yaron Rachlin



- Slides: 16

The Secrecy of Compressed Sensing Measurements Yaron Rachlin & Dror Baron

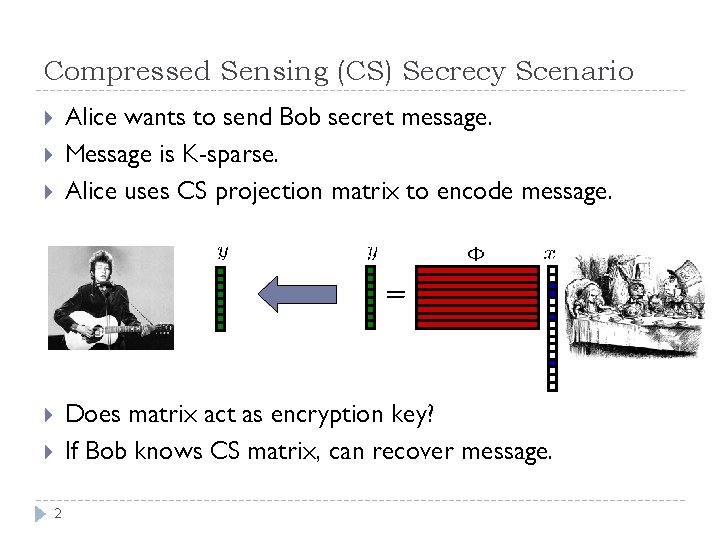
Compressed Sensing (CS) Secrecy Scenario Alice wants to send Bob secret message. Message is K-sparse. Alice uses CS projection matrix to encode message. Does matrix act as encryption key? If Bob knows CS matrix, can recover message. 2

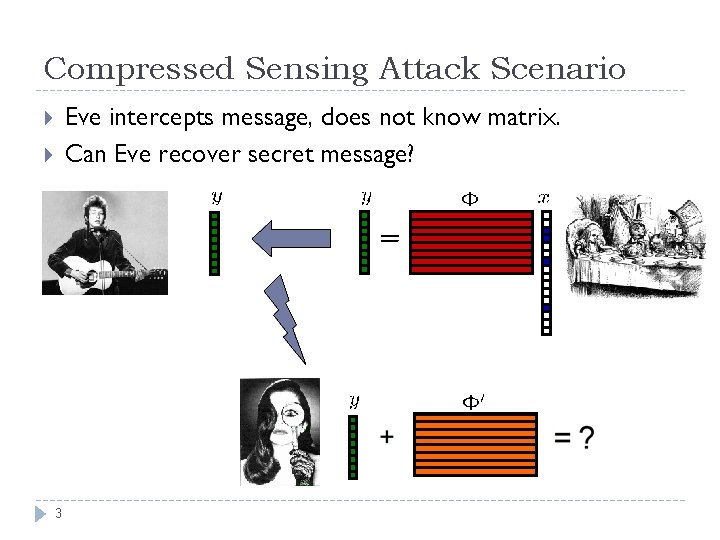
Compressed Sensing Attack Scenario Eve intercepts message, does not know matrix. Can Eve recover secret message? 3

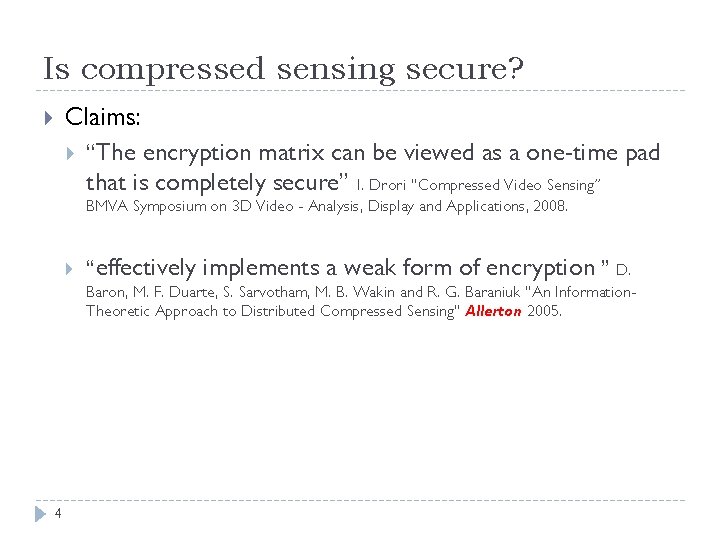
Is compressed sensing secure? Claims: “The encryption matrix can be viewed as a one-time pad that is completely secure” I. Drori “Compressed Video Sensing” BMVA Symposium on 3 D Video - Analysis, Display and Applications, 2008. “effectively implements a weak form of encryption ” D. Baron, M. F. Duarte, S. Sarvotham, M. B. Wakin and R. G. Baraniuk “An Information. Theoretic Approach to Distributed Compressed Sensing” Allerton 2005. 4

Notions of security Information theoretic – H(message|ciphertext)=H(message) Computationally unbounded adversary Computational – Extracting message equivalent to solving computationally hard problem 5 Computationally bounded adversary

Perfect Secrecy? Definition of perfect secrecy (Shannon). X message, Y ciphertext, I(X; Y)=0 Does CS-based encryption achieve perfect secrecy? NO Noiseless case: If message X=0, ciphertext Y=0. CS matrices satisfying RIP roughly preserve l 2 norm. ð Mutual information is positive. Could mutual information be small? 6

Computational Secrecy Recovery is feasible, but hard for computationally bounded adversary. (Weaker) More widely used than perfect secrecy. How many matrices must an attacker try before finding the correct Phi matrix? Propose this as a computational notion of security for CS. 264 keys could be an unfortunate predicament. 7

Application Example: Biometrics Don’t want to store lots of data “in the clear. ” Can we just store features? (Reversible) If encryption key compromised, severe loss. Possible solution: Compress (lossy, enable revocation) Then encrypt (high overhead) Or, compress & encrypt in same step? Time critical application. 8

Other Applications Low power sensors Sensor Networks nodes have limited battery life. Provides low-cost encryption while performing compression. High bandwidth sensors 9 Networks of video cameras require low latency.

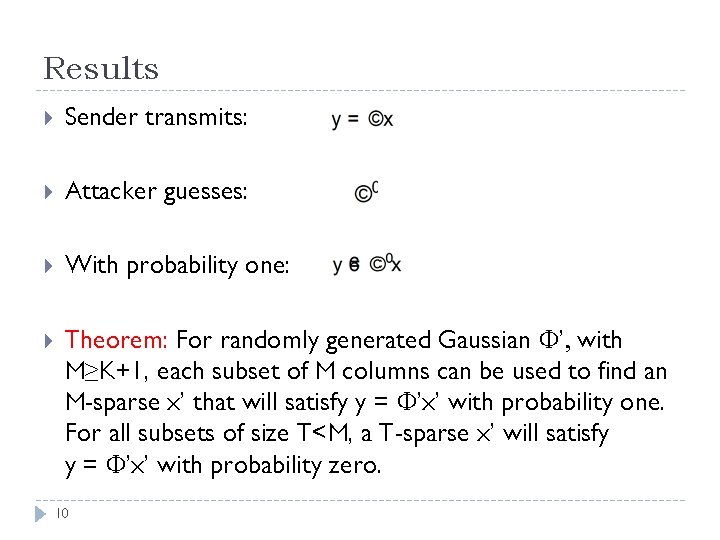
Results Sender transmits: Attacker guesses: With probability one: Theorem: For randomly generated Gaussian ’, with M≥K+1, each subset of M columns can be used to find an M-sparse x’ that will satisfy y = ’x’ with probability one. For all subsets of size T<M, a T-sparse x’ will satisfy y = ’x’ with probability zero. 10

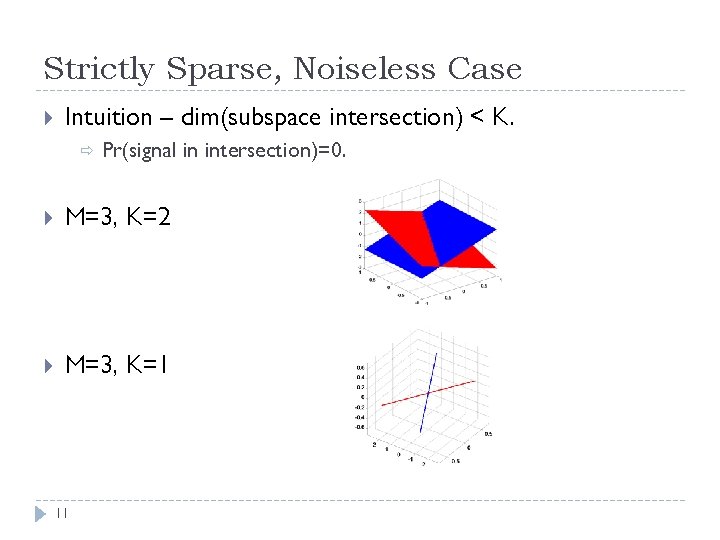
Strictly Sparse, Noiseless Case Intuition – dim(subspace intersection) < K. ð Pr(signal in intersection)=0. M=3, K=2 M=3, K=1 11

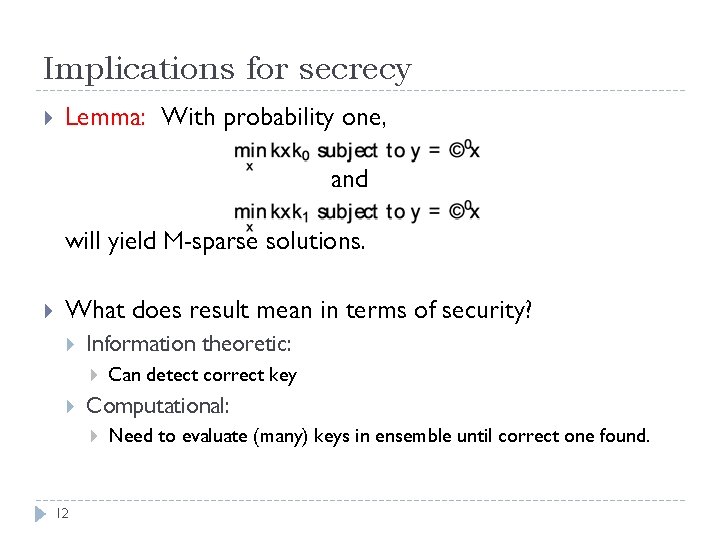
Implications for secrecy Lemma: With probability one, and will yield M-sparse solutions. What does result mean in terms of security? Information theoretic: Computational: 12 Can detect correct key Need to evaluate (many) keys in ensemble until correct one found.

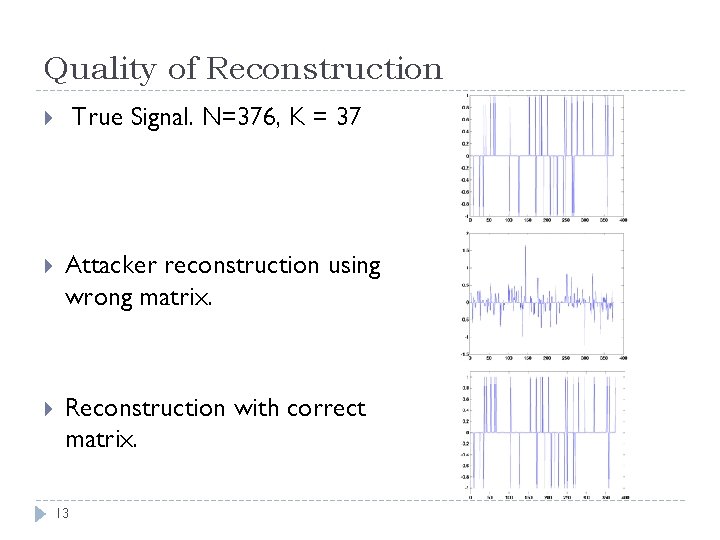
Quality of Reconstruction True Signal. N=376, K = 37 Attacker reconstruction using wrong matrix. Reconstruction with correct matrix. 13

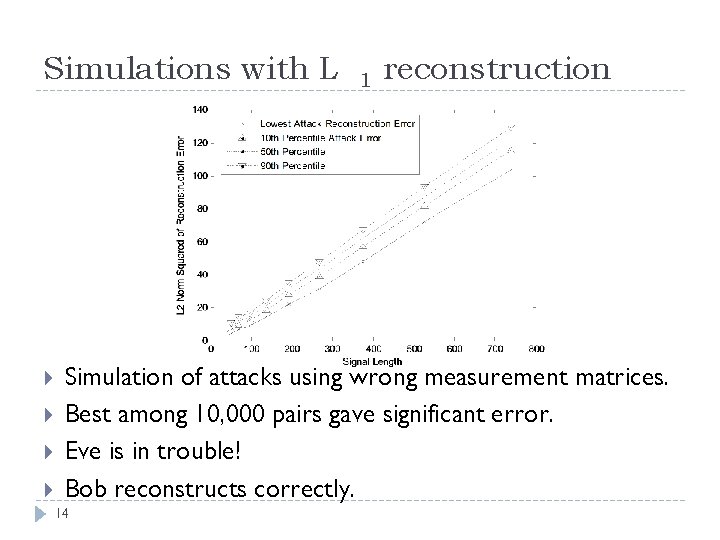
Simulations with L 1 reconstruction Simulation of attacks using wrong measurement matrices. Best among 10, 000 pairs gave significant error. Eve is in trouble! Bob reconstructs correctly. 14

Other Settings Strictly Sparse, Noiseless (Results, Simulations) Compressible, Noiseless Strictly Sparse, Noisy (Ongoing Work) Compressible, Noisy Preliminary analysis indicates similar results feasible in other settings. 15

Thank you for your attention. Questions? 16
 Ainslie-rachlin
Ainslie-rachlin Yaron ernst
Yaron ernst Yaron shohat
Yaron shohat Power modulation
Power modulation Dr rubina yasmin
Dr rubina yasmin Communication theory of secrecy systems
Communication theory of secrecy systems Compressed gas definition
Compressed gas definition Calendering moulding
Calendering moulding Wilkerson desiccant air dryer
Wilkerson desiccant air dryer Compressed rvc foam
Compressed rvc foam Compressed air energy storage
Compressed air energy storage Visual search
Visual search Suffix trie example
Suffix trie example 29 cfr 1910 compressed gas cylinder storage
29 cfr 1910 compressed gas cylinder storage Compressed air supercharging
Compressed air supercharging Compressed gas cylinder safety ppt
Compressed gas cylinder safety ppt Stretches and compressions of linear functions
Stretches and compressions of linear functions