Teachers Discovering Computers Integrating Technology and Digital Media















- Slides: 26

Teachers Discovering Computers Integrating Technology and Digital Media in the Classroom 7 th Edition Chapter 8 Security Issues and Ethics in Education

Computer security risk § Any event or action that has the potential of causing a loss of computer equipment, software, data and information, or processing capability Chapter 8: Security Issues and Ethics in Education 2

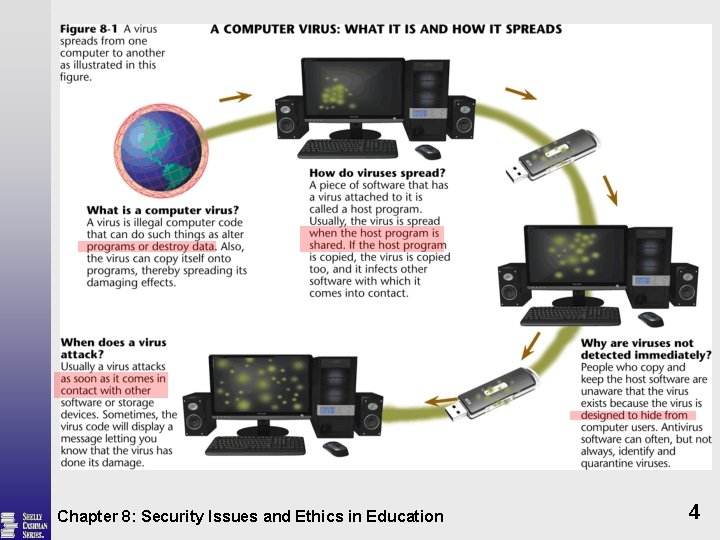
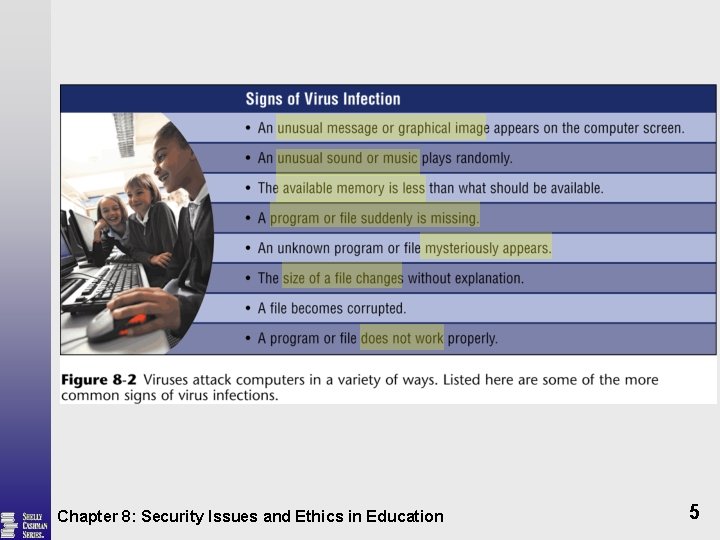
Computer Viruses § New virus programs found every day A segment of program code § Boot sector virus Replaces the boot program § File virus Inserts virus code into a specific file § Macro virus Hides the virus code § Worm A program that copies itself repeatedly § Trojan horse Looks like a legitimate program Chapter 8: Security Issues and Ethics in Education 3

Chapter 8: Security Issues and Ethics in Education 4

Chapter 8: Security Issues and Ethics in Education 5

Computer Viruses § Logic bomb program that activates when detects a certain condition § Time bomb program that activates on a particular date Chapter 8: Security Issues and Ethics in Education 6

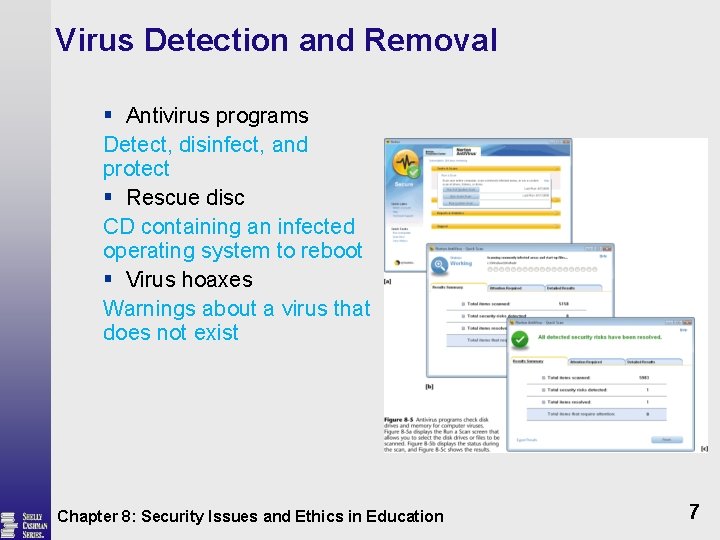
Virus Detection and Removal § Antivirus programs Detect, disinfect, and protect § Rescue disc CD containing an infected operating system to reboot § Virus hoaxes Warnings about a virus that does not exist Chapter 8: Security Issues and Ethics in Education 7

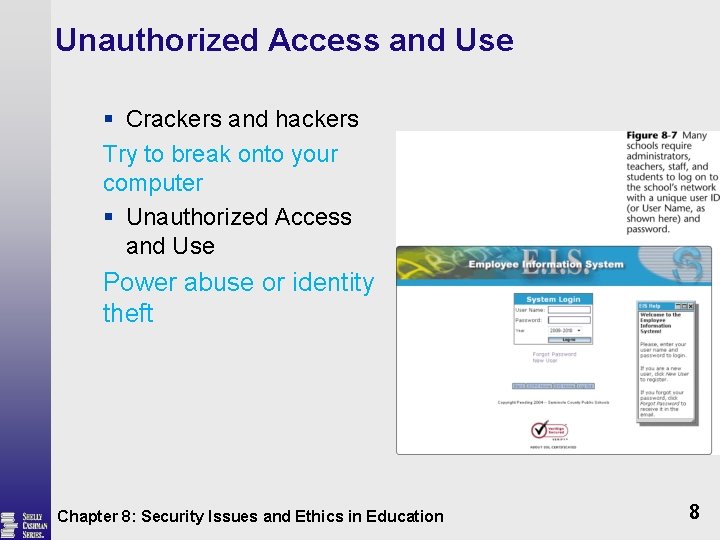
Unauthorized Access and Use § Crackers and hackers Try to break onto your computer § Unauthorized Access and Use Power abuse or identity theft Chapter 8: Security Issues and Ethics in Education 8

Possessed Objects and Biometric Devices § A possessed object is any item that you must carry to gain access to a computer or computer facility § Badges, cards, smart cards, and keys § Personal Identification Number (PIN) § Biometric devices authenticate a person’s identity with a personal characteristic Chapter 8: Security Issues and Ethics in Education 9

Computer Security: Risks and Safeguards § Firewall § A security system consisting of hardware and/or software that prevents unauthorized access to data and information on a network § Proxy server (screens all incoming and outgoing messages) Chapter 8: Security Issues and Ethics in Education 10

Computer Security: Risks and Safeguards § Hardware Theft and Vandalism § Cable lock devices § Portable equipment warrants special considerations § Computer vandalism § Cutting cables § Deleting software § Smashing computer Chapter 8: Security Issues and Ethics in Education 11

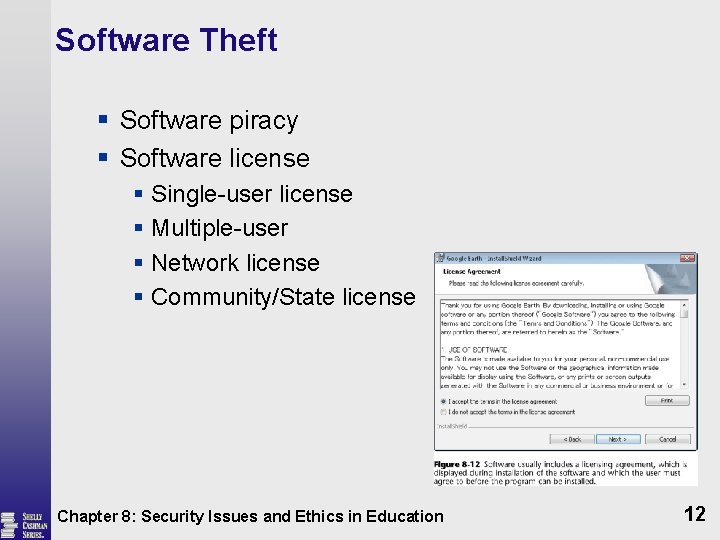
Software Theft § Software piracy § Software license § Single-user license § Multiple-user § Network license § Community/State license Chapter 8: Security Issues and Ethics in Education 12

Information Theft § Encryption Chapter 8: Security Issues and Ethics in Education 13

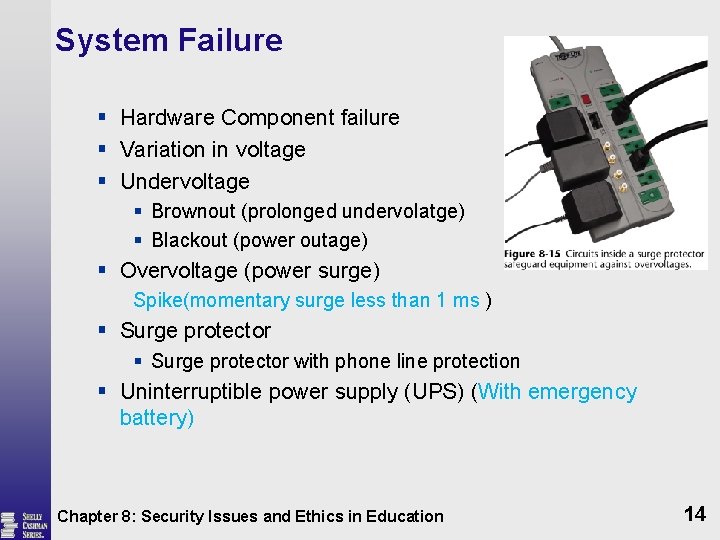
System Failure § Hardware Component failure § Variation in voltage § Undervoltage § Brownout (prolonged undervolatge) § Blackout (power outage) § Overvoltage (power surge) Spike(momentary surge less than 1 ms ) § Surge protector with phone line protection § Uninterruptible power supply (UPS) (With emergency battery) Chapter 8: Security Issues and Ethics in Education 14

Computer Security: Risks and Safeguards § Backing Up – The Ultimate Safeguard § Backup § Duplicate of a file, program, or disk that may be used if the original is lost, damaged, or destroyed § Backup procedures policies in schools and school districts § Backup programs Chapter 8: Security Issues and Ethics in Education 15

Chapter 8: Security Issues and Ethics in Education 16

Ethics and the Information Age § Phishing § Email attempting to obtain personal and financial information § Spam § An unsolicited e-mail mess or newsgroup posting sent to many recipients or newsgroups at once § Average user receives more than 1, 000 spam email messages each year § Spam sent through instant messaging is called spim § Spam sent via Internet Telephony is called split Chapter 8: Security Issues and Ethics in Education 17

Ethics and the Information Age § Privacy Laws § Business or government agencies should only collect information necessary to carry out their functions § Restrict data access to those who must use it to perform job duties § Release personal information only after agreement to disclosure by individual § Must inform the individual when collecting information Chapter 8: Security Issues and Ethics in Education 18

Chapter 8: Security Issues and Ethics in Education 19

Internet Ethics and Objectionable Materials § Three categories of objectionable material § Pornographic material § Racist literature, gambling § Incorrect or inappropriate material Chapter 8: Security Issues and Ethics in Education 20

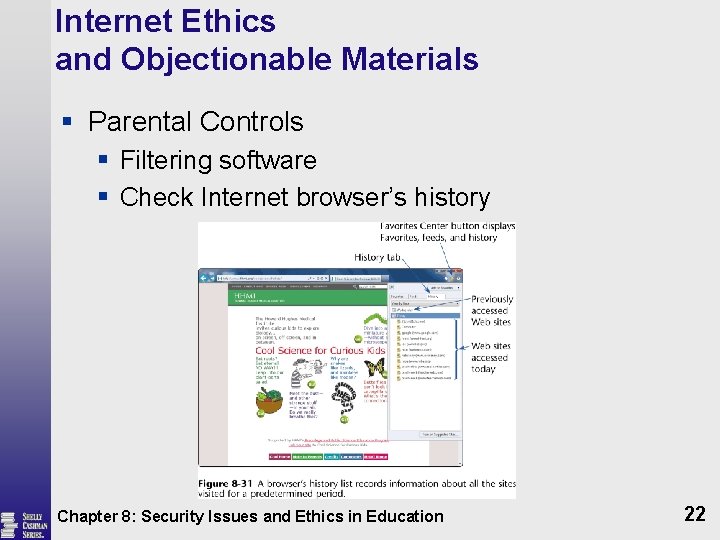
Internet Ethics and Objectionable Materials § Parental Controls § Available in Windows and Mac operating systems § Determine proper controls for children in different age groups § Monitor child’s use of computer Chapter 8: Security Issues and Ethics in Education 21

Internet Ethics and Objectionable Materials § Parental Controls § Filtering software § Check Internet browser’s history Chapter 8: Security Issues and Ethics in Education 22

Educational Controls § Curriculum resource pages § Acts as guides for students § Sites are pre-evaluated by teachers § Eliminates typing mistakes when typing URLs Chapter 8: Security Issues and Ethics in Education 23

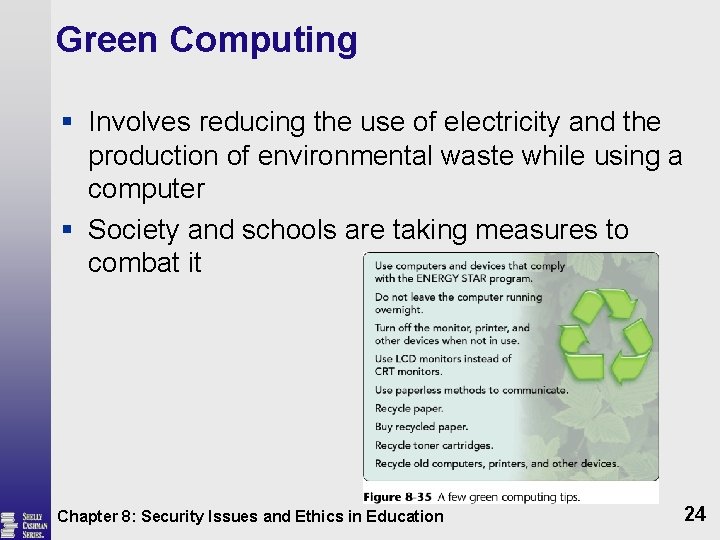
Green Computing § Involves reducing the use of electricity and the production of environmental waste while using a computer § Society and schools are taking measures to combat it Chapter 8: Security Issues and Ethics in Education 24

Health Issues § Computers and Health Issues § Musculoskeletal Disorder (MSD) § Repetitive Strain Injury (RSI) § Carpal Tunnel Syndrome (CTS) § Hand Exercises § Computer Vision Syndrome (CVS) § Techniques to ease eyestrain Chapter 8: Security Issues and Ethics in Education 25

Health Issues § Ergonomics § An applied science devoted to incorporating comfort, efficiency, and safety into the design of items in the workplace Chapter 8: Security Issues and Ethics in Education 26