Standard Operating Procedures for Treatment of Critical Infrastructure
















- Slides: 17

Standard Operating Procedures for Treatment of Critical Infrastructure Information Roger Koelpin GIS Critical Infrastructure Planning and Assessment Branch rkoelpin@dhs. in. gov 317 -232 -0181

Standard Operating Procedures for Treatment of Critical Infrastructure Information • What is Critical Infrastructure? • The Problem • Why do we need an SOP for CII? • Methods • IDHS SOP

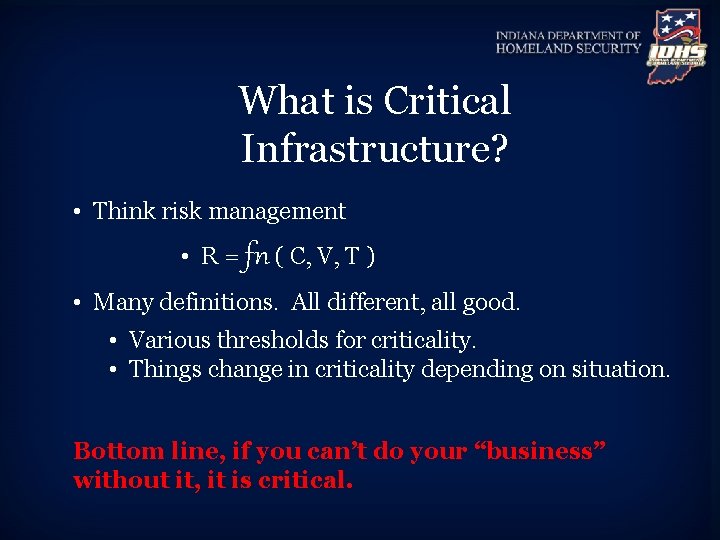
What is Critical Infrastructure? • Think risk management • R = fn ( C, V, T ) • Many definitions. All different, all good. • Various thresholds for criticality. • Things change in criticality depending on situation. Bottom line, if you can’t do your “business” without it, it is critical.

The Problem We have a need to withhold some information about critical infrastructure. • Because we promised. • Because it is “risky” to publish. Members of the general public have a reasonable expectation of…

The Problem …knowing that Company XYZ has an office located there. (Geography? ) Members of the general public DO NOT have a reasonable expectation of knowing that the 3 rd switch on the left, room 911, building 666, will turn off the sun, forever. (Capabilities, capacity. . ? ) Not always a set of binary options.

Why do we need an SOP? Indiana Access to Public Records Act • IC 5 -14 -3 • It is the law. • Bad things happen when you don’t follow the law. Worse things happen if we promise to keep secrets and don’t. Very real need to continue getting information from private sector!

Why do we need an SOP? Indiana Access to Public Records Act – exceptions • IC 5 -14 -3 -4(b)(19) …reasonable likelihood of threatening public safety by exposing a vulnerability to terrorist attack.

Why do we need an SOP? Indiana Access to Public Records Act – exceptions • Can successfully withhold if (IC 5 -14 -3 -8. 5) • prove that the records are exempted records, and • denial of access is NOT arbitrary or capricious.

Methods Prove that the records are exempted • Define “Critical Infrastructure Information” and • Beyond “a member of the general public has a reasonable expectation…”

Methods OBJECT ORIENTED POLICY Prove that the records are exempted • Define “Critical Infrastructure Information” Created a retention schedule for IDHS, for CII through Indiana Public Access Commission • Retention schedule is “shred CII when obsolete. ” • CII defined as anything under IC 5 -14 -3 -4(b)

Methods Denial of access is NOT arbitrary or capricious • Have an SOP for treatment of CII • Train and exercise staff on the SOP • Apply SOP consistently • Part of the SOP establishes a process for assuring that members of the general public DO NOT have a reasonable expectation… • Covers those “non-binary” cases

IDHS SOP 1. Retention and Safeguarding 2. Types of CII Records 3. Distribution

IDHS SOP Retention and Safeguarding 1. Retention 2. Safeguarding • Includes attachment for best practices 3. Labeling 4. Training 5. Updates

IDHS SOP Types of CII Records 1. Submitted to IDHS as CII by public sector 2. Submitted to IDHS as CII by private sector 3. Generated by IDHS • With an attachment for identification of records where members of the general public DO NOT have a reasonable expectation of… • Includes allowances for redaction

IDHS SOP Distribution 1. General public – not allowed 2. Response partners • Public sector with SOPs for CII • Public sector without SOPs for CII • Private sector partners

Standard Operating Procedures for Treatment of Critical Infrastructure Information • What is Critical Infrastructure? • The Problem • Why do we need an SOP for CII? • Methods • IDHS SOP

Standard Operating Procedures for Treatment of Critical Infrastructure Information Questions? Roger Koelpin GIS Critical Infrastructure Section Chief Planning and Assessment Branch rkoelpin@dhs. in. gov 317 -232 -0181
 Critical semi critical and non critical instruments
Critical semi critical and non critical instruments Semi critical
Semi critical Operating room cleaning procedures
Operating room cleaning procedures Critical infrastructure cybersecurity trends
Critical infrastructure cybersecurity trends Critical infrastructure sectors
Critical infrastructure sectors Ceii ferc
Ceii ferc Critical infrastructure security coordination centre
Critical infrastructure security coordination centre Critical infrastructure protection board
Critical infrastructure protection board Nist framework for improving critical infrastructure
Nist framework for improving critical infrastructure Improving critical infrastructure cybersecurity
Improving critical infrastructure cybersecurity Improving critical infrastructure cybersecurity
Improving critical infrastructure cybersecurity Man made disasters conclusion
Man made disasters conclusion Compare non-critical readers with critical readers.
Compare non-critical readers with critical readers. Unstructured cabling
Unstructured cabling Standard operating procedure software
Standard operating procedure software Operating performance measures
Operating performance measures Standard cost model
Standard cost model Fspos vägledning för kontinuitetshantering
Fspos vägledning för kontinuitetshantering