Software Security Comp Sci 725 Handout 12 Student





















- Slides: 28

Software Security Comp. Sci 725 Handout 12: Student Presentations, Watermarking & Obfuscation Clark Thomborson University of Auckland h 12. 15 -Mar-01 1

Choosing the Technical Article you will Present • Please refer to Handout 6: Bibliography. • Handout 9 is a class list, indicating the Order in which students will make presentations. • Pick a few papers you would like to present. • I will briefly discuss about half of these papers, then I’ll call for volunteers. If there is more than one volunteer, the person with the lowest “Order” will present this paper. h 12. 15 -Mar-01 2

Preparing your Presentation • • Read your paper carefully. Outline your paper: 1 “point” per page or section. Pick one “point” to present in detail in your presentation. If your article is more than 8 pages long, choose 5 to 8 pages that are suitable for a class handout – these pages should explain the “point” you will present in detail. • Outline your presentation: one sentence per slide. • Construct a first draft of your presentation: use Power. Point or your favourite presentation builder (not MS Word!) h 12. 15 -Mar-01 3

Presentation Requirements 1. Give your 5 - to 8 -page handout to me (so that I can duplicate it for distribution to the class) by 10 am Wednesday in the week BEFORE your presentation. 2. Your slideshow presentation must last 8 to 12 minutes, not counting time spent on questions and answers from the class. 3. Your question-and-answer time must last 2 to 8 minutes – you must initiate the discussion with at least one question printed in your slideshow. 4. Transmit the final version of your. pps or other online slideshow document to me by email to me, at cthombor@cs. auckland. ac. nz, so I can mount it on the class website. h 12. 15 -Mar-01 4

Contents of Your Presentation • You should prepare seven to ten slides: – – – title slide (possibly including a sample quotation) outline of your talk four to seven slides, explaining one topic in detail conclusion one or two questions, to stimulate discussion • Rehearse your presentation with a friend, at least once. • You may ask me for feedback by email – I’ll try for a 3 -day turnaround. • Revise your talk for clarity, and to fit the 8 -12 minute time limit. • You’ll spend 10+ hours preparing your presentation! h 12. 15 -Mar-01 5

My Expectations • Presenters should show appreciative and critical understanding of their article, through – the contents of their slides – their oral comments when presenting their slides, and – their handling of the discussion. • Non-presenters should have read the article before the presentation begins. • All students should have a working knowledge of what was presented & discussed in class. (This will be tested in your final examination. ) h 12. 15 -Mar-01 6

Your Term Project Report • When reading your article, you should start thinking about how to use it as a basis for a written report. Initial ideas: – Compare/contrast your article’s technology (or analysis or research finding) to some other published work – Discover an article describing an extension or application of this technology – Identify a point of confusion or difficulty in your article and explain it “better than the author did” (with appropriate references). h 12. 15 -Mar-01 7

Requirements for Reports • Your report should consist of nine to thirteen pages of 12 -point type with generous margins and 1. 5 line spacing. • If you use someone else’s words, put these in quotation marks and add a reference to your source. (We’ll talk about direct quotations, plagiarism and paraphrase next week. ) • You should make good use of at least three published works. Your sources must be listed with full (and accurate) bibliographic details at the end of your report. • Try to match the style of one of the articles you read in this class. • Technical words must be spelled and used correctly. • You should use a spell-checker and a grammar checker (e. g. MS Word), however I will not mark you down for grammatical mistakes and spelling errors on non-technical words. h 12. 15 -Mar-01 8

Watermarking, Tamper-Proofing and Obfuscation – Tools for Software Protection Christian Collberg & Clark Thomborson Computer Science Tech Report 170 University of Auckland 4 February 2000 accepted with minor revision by IEEE TSE h 12. 15 -Mar-01 9

Watermarking and Fingerprinting Watermark: a secret message embedded into a cover message. • Image, audio, video, text… • Visible or invisible marks • Fragile (“licensing marks”) or robust (“authorship marks”) • Watermarking 1. Discourages theft 2. Allows us to prove theft • Fingerprinting 3. Allows us to trace violators h 12. 15 -Mar-01 10

Watermarking Variants • The watermark may be visible and robust (difficult to remove), providing a proof of ownership or authorship. • The watermark may be fragile (obliterated by any modification, perhaps even including copying), proving authenticity or validity of a license. The watermark may be invisible and robust, providing proof of ownership and security from theft. • Fingerprinting is a variant of watermarking in which we put a unique customer-ID in each object we distribute. Piracy can be detected if we discover duplicate fingerprints, and these fingerprints identify the (witting or unwitting) source of the distribution. h 12. 15 -Mar-01 11

Our Desiderata for WMs • Watermarks should be stealthy -- difficult for an adversary to locate. • Watermarks should be resilient to attack -resisting attempts at removal even if they are located. • Watermarks should have a high data-rate -- so that we can store a meaningful message without significantly increasing the size of the object. h 12. 15 -Mar-01 12

Attacks on Watermarks • Subtractive attacks: remove the WM without damaging the cover. • Additive attacks: add a new WM without revealing “which WM was added first”. • Distortive attacks: modify the WM without damaging the cover. • Collusive attacks: examine two fingerprinted objects, or a watermarked object and its unwatermarked cover; find the differences; construct a new object without a recognisable mark. h 12. 15 -Mar-01 13

Defenses for Software Watermarks • Obfuscation: we can modify the software so that a reverse engineer will have great difficulty figuring out how to reproduce the cover without also reproducing the WM. • Tamperproofing: we can add integrity-checking code that (almost always) renders it unusable if the object is modified. h 12. 15 -Mar-01 14

Classification of SW Watermarks • Static code watermarks are stored in the section of the executable that contains instructions. • Static data watermarks are stored in other sections of the executable. Dynamic data watermarks are stored in a program’s execution state. Such watermarks are resilient to distortive (obfuscation) attacks. h 12. 15 -Mar-01 15

Dynamic Watermarks • Easter Eggs are revealed to any end-user who types a special input sequence. • Execution Trace Watermarks are carried (steganographically) in the instruction execution sequence of a program, when it is given a special input. Data Structure Watermarks are built (steganographically) by a program, when it is given a special input sequence (possibly null). h 12. 15 -Mar-01 16

Easter Eggs • The watermark is visible -- if you know where to look! • Not resilient, once the secret is out. • See www. eeggs. com h 12. 15 -Mar-01 17

Our Goals for Dynamic DS WMs • Stealth. Our WM should “look like” other structures created by the cover (search trees, hash tables, etc. ) • Resiliency. Our WM should have some properties that can be checked, stealthily and quickly at runtime, by tamperproofing code (triangulated graphs, biconnectivity, …) • Data Rate. We would like to encode 100 -bit WMs, or 1000 -bit fingerprints, in a few KB of data structure. Our fingerprints may be 1000 -bit integers that are products of two primes. h 12. 15 -Mar-01 18

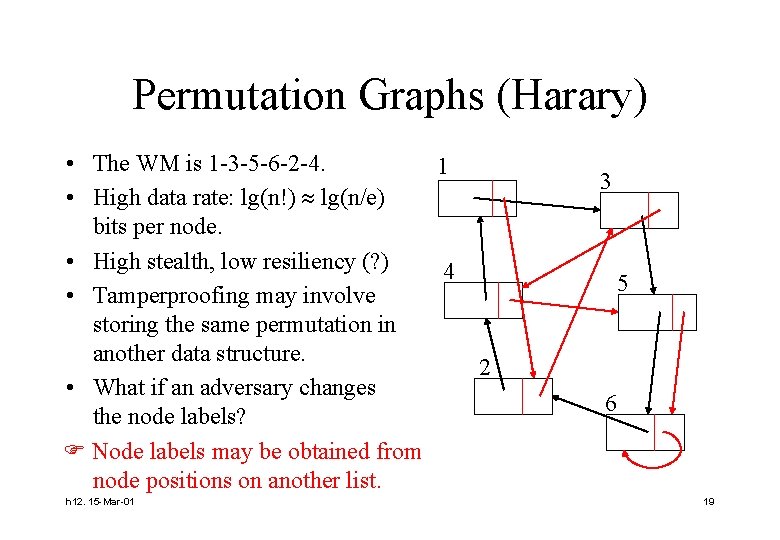
Permutation Graphs (Harary) • The WM is 1 -3 -5 -6 -2 -4. 1 • High data rate: lg(n!) lg(n/e) bits per node. • High stealth, low resiliency (? ) 4 • Tamperproofing may involve storing the same permutation in another data structure. 2 • What if an adversary changes the node labels? Node labels may be obtained from node positions on another list. h 12. 15 -Mar-01 3 5 6 19

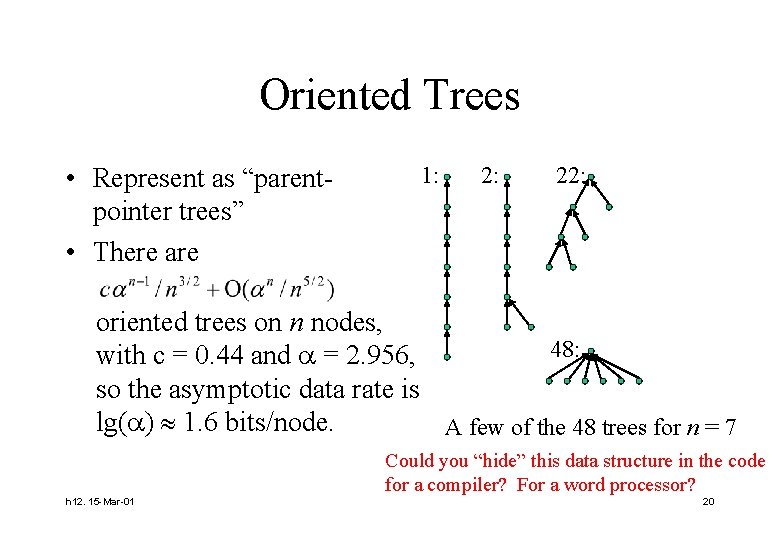
Oriented Trees • Represent as “parentpointer trees” • There are 1: 22: oriented trees on n nodes, 48: with c = 0. 44 and = 2. 956, so the asymptotic data rate is lg( ) 1. 6 bits/node. A few of the 48 trees for n = 7 Could you “hide” this data structure in the code for a compiler? For a word processor? h 12. 15 -Mar-01 20

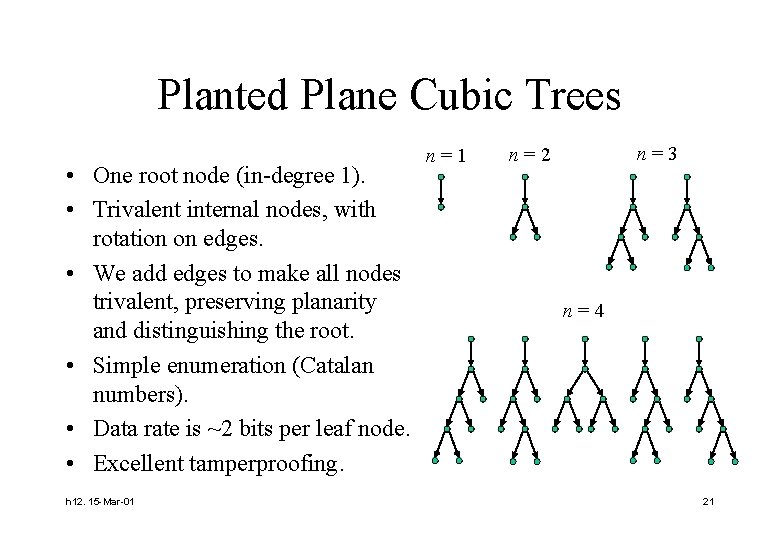
Planted Plane Cubic Trees • One root node (in-degree 1). • Trivalent internal nodes, with rotation on edges. • We add edges to make all nodes trivalent, preserving planarity and distinguishing the root. • Simple enumeration (Catalan numbers). • Data rate is ~2 bits per leaf node. • Excellent tamperproofing. h 12. 15 -Mar-01 n=3 n=2 n=4 21

Open Problems in Watermarking • We can easily build a “recogniser” program to find the WM and therefore demonstrate ownership… but can we release this recogniser to the public without compromising our watermarks? • Can we design a “partial recogniser” that preserves resiliency, even though it reveals the location of some part of our WM? h 12. 15 -Mar-01 22

State of the Art in SW Watermarking • First dynamic DS watermarks installed in 1999. • Recognition SW being developed. • Ongoing search for graph structures that are suitable for carrying fingerprints. Requirements: – easily enumerable – low outdegree (but high data rate) – quickly-checked properties (for tamperproofing) h 12. 15 -Mar-01 23

Software Obfuscation • Many authors, websites and even a few commercial products offer “automatic obfuscation” as a defense against reverse engineering. • Existing products generally operate at the lexical level of software, for example by removing or scrambling the names of identifiers. • We seem to have been the first (in 1997) to use “opaque predicates” to obfuscate the control structure of software. h 12. 15 -Mar-01 24

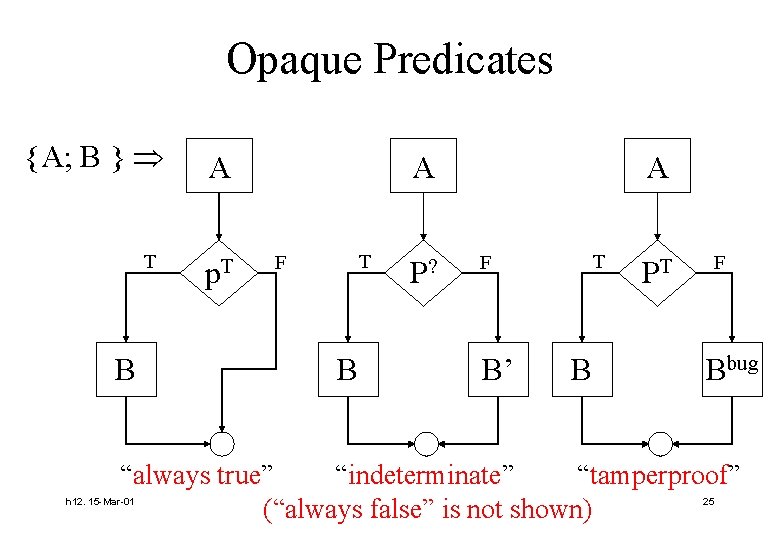
Opaque Predicates {A; B } T B A p. T A F T B P? A F B’ T B PT F Bbug “always true” “indeterminate” “tamperproof” (“always false” is not shown) h 12. 15 -Mar-01 25

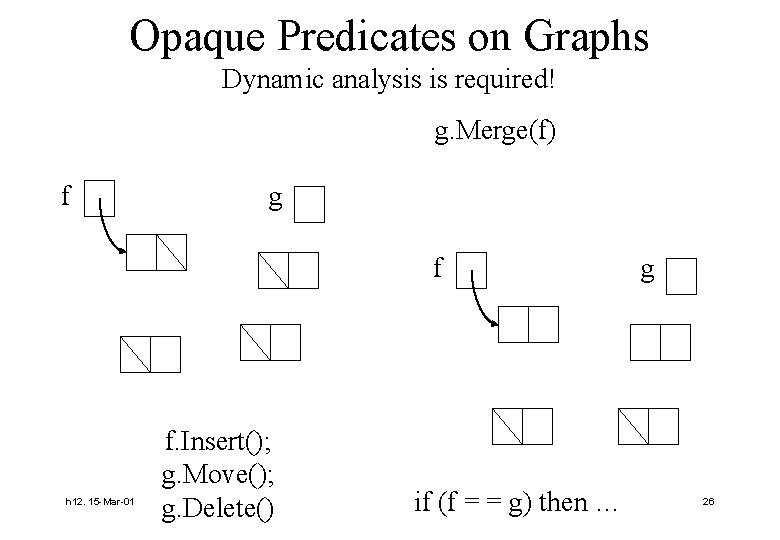
Opaque Predicates on Graphs Dynamic analysis is required! g. Merge(f) f g f h 12. 15 -Mar-01 f. Insert(); g. Move(); g. Delete() if (f = = g) then … g 26

Conclusion • New art in software obfuscation can make it more difficult for pirates to defeat standard tamperproofing mechanisms, or to engage in other forms of reverse engineering. • New art in software watermarking can embed “ownership marks” in software, that will be very difficult for anyone to remove. • More R&D is required before robust obfuscating and watermarking tools are easy to use and readily available to software developers. h 12. 15 -Mar-01 27

Schedule • Tuesday, 20 March: – Software Obfuscation. – Direct quotations, plagiarism and paraphrase. • Wednesday, 21 March: – Introduction to Cryptography. – Handouts due, from students #3 - #9 • Friday, 23 March: – Chess, “Security Issues…” – Student presentation #2 (Bellare? ) h 12. 15 -Mar-01 28