social Engineering its importance during Security Audits and
























- Slides: 31

social Engineering its importance during Security Audits and By: - Vismit Sudhir Rakhecha(Zhug)

There is no Patch, For human stupidity !

Case Studies

What is Social Engineering ? Famous hacker Kevin Mitnick helped popularize the term “social engineering” in the ‘ 90 s, but the simple idea itself has been around for ages. Social engineering is the art of gaining access to buildings, systems or data by exploiting human psychology, rather than by breaking in or using technical hacking techniques.

Our Life Today


How Social Engineering works? There an infinite number of social engineering exploits. A scammer may trick you into leaving a door open for him, visiting a fake Web page or downloading a document with malicious code, or he might insert a USB in your computer that gives him access to your corporate network.

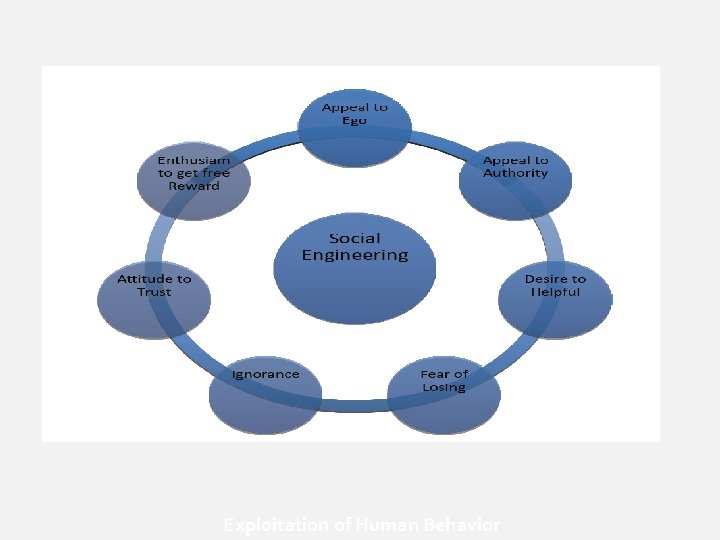
Exploitation of Human Behavior

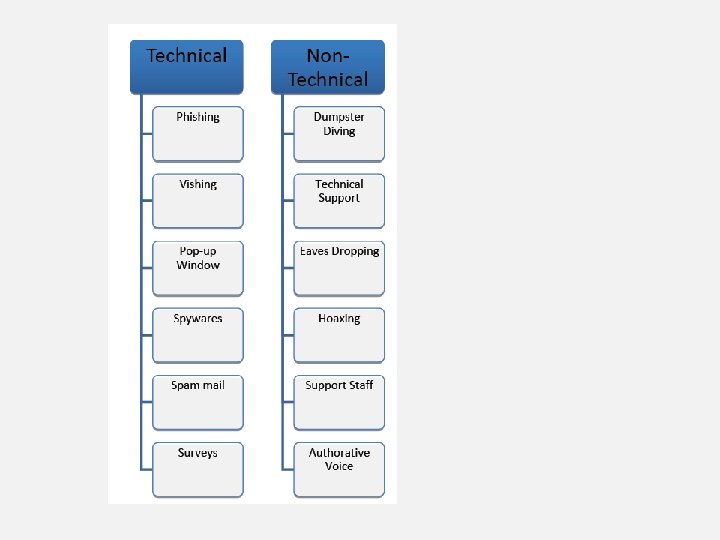
Types of Social Engineering There are two main categories under which all social engineering attempts could be classified. • Computer or Technology based • Human based or Non-Technical


SE and Security Audit We can break social engineering audits into two main categories, Internal and External, then from there break them down into smaller sub-categories.

Internal SE

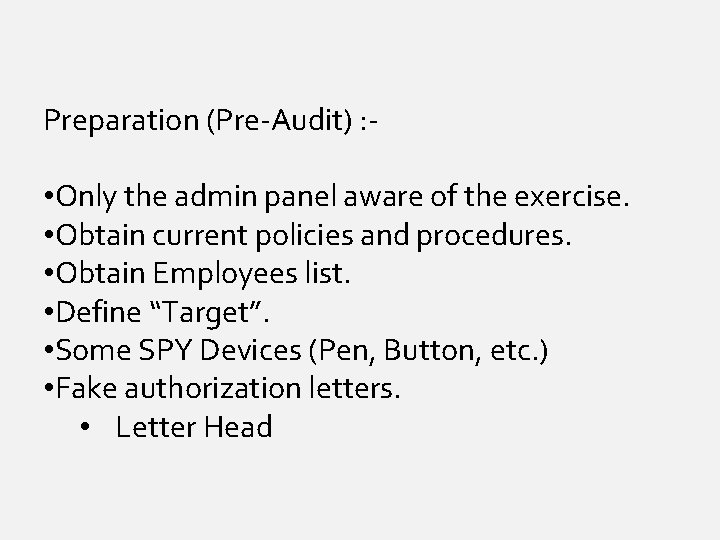
Preparation (Pre-Audit) : - • Only the admin panel aware of the exercise. • Obtain current policies and procedures. • Obtain Employees list. • Define “Target”. • Some SPY Devices (Pen, Button, etc. ) • Fake authorization letters. • Letter Head

Phase I (Info Gathering) The social engineer who begins his attack with little or no information is destined for failure. Gathering information about the company, its practices, and employees, and identifying potential weaknesses is the goal. Employee lists, internal phone numbers, corporate directories and sensitive security information are prized possessions to the social engineer.


Phase II (Physical Entry) While the social engineer will generally attempt to accomplish his mission without ever physically stepping foot on company property, sometimes it is necessary to gain physical access to gather further information. There are many common tricks that the social engineer can use to gain physical access to a facility. The security auditor can also use these to test physical security procedures.


Results


I Gained

• Sensitive Information on Technology used • Network architecture. • Lots of Technical Information reveled to “College Student”. • Official letter in store room. • Gained Access to Server Room.

External SE

In External SE, the base is our PHASE I. Over here we will use Computer or Electric Device to perform audit.

Phishing

Spyware

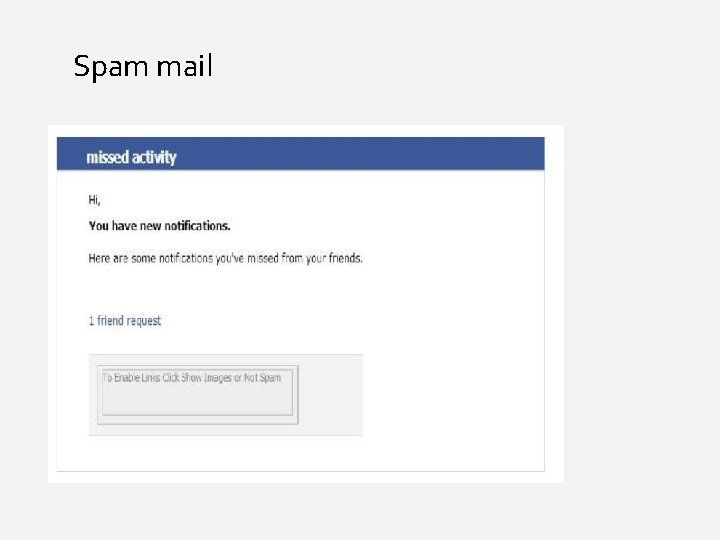
Spam mail

Baiting

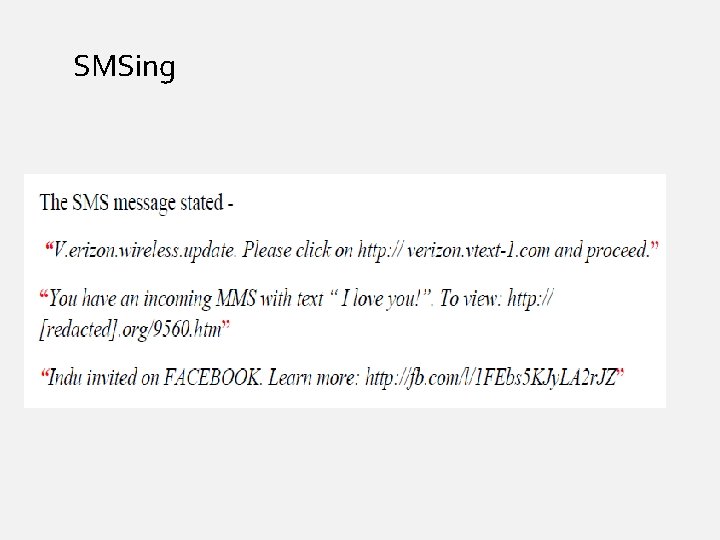
SMSing

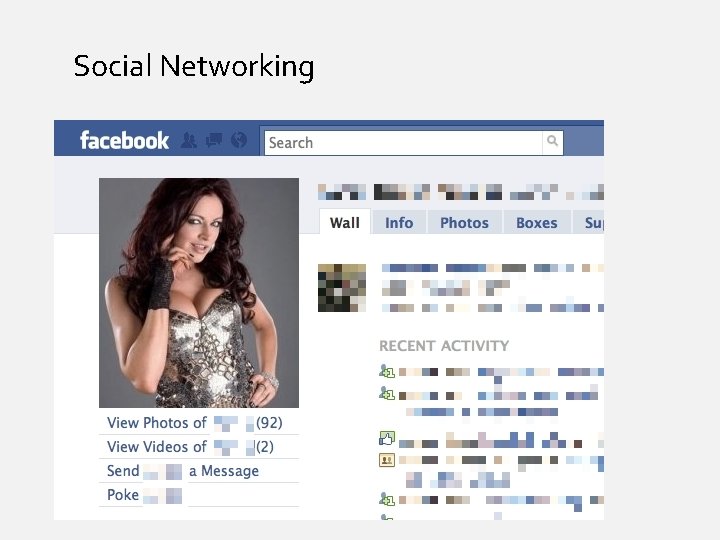
Social Networking

QUESTIONS ? ? ? Contact : rvismit@gmail. com www. facebook. com/rvismit
