Security Testing The importance of security testing Security









- Slides: 14

Security Testing Ø Ø Ø The importance of security testing Security vulnerabilities Are we secure ? How much security testing WE DO ? Security testing software tools Starting directions in developing security testing 1

The importance of security testing System testing is a must to identify and address web application security vulnerabilities to avoid any of the following: A permanent loss in customer confidence Damage company brand Website downtime, devastating productivity Expensive vulnerability remediation costs Cost associated with securing web applications against future attacks Legal sanctions and civil lawsuits, depending on the case in question 2

Secure application checklist: Confidentiality – only those with authorized access Integrity – information providing is correct Authentication – establishes the identity of the user Authorization – perform an action for which he has permission Availability – ready for use when expected Non-repudiation – information exchange with proof 3

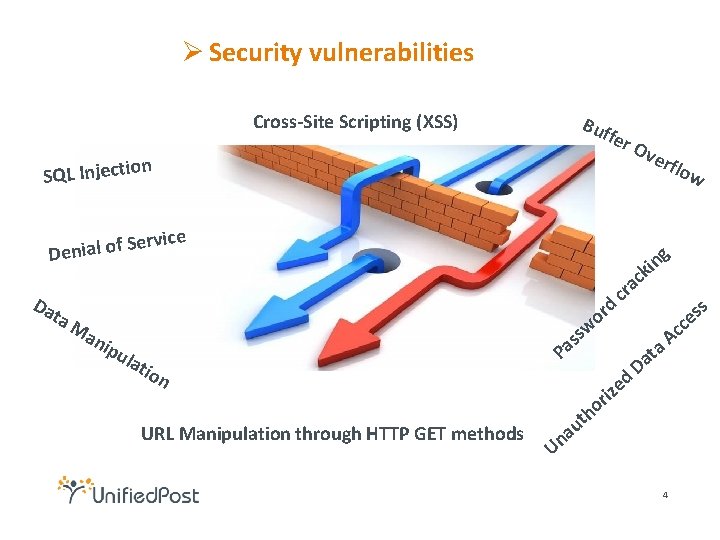
Ø Security vulnerabilities Cross-Site Scripting (XSS) Buf fer n SQL Injectio Ov erf ice v r e S f o l a Deni Da ta Ma low g n i k c a c r d nip u lat ion or sw s Pa a at D o URL Manipulation through HTTP GET methods s th u na es c Ac d e riz U 4

Security testing example SQL Injection http: //www. cobranet. org/about. php? id=1 5

Are we secure ? How much security testing WE DO ? 6

OWASP 7

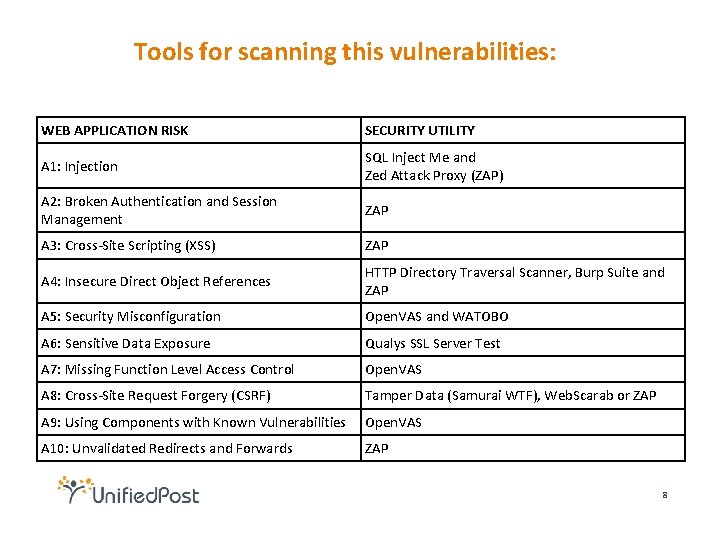
Tools for scanning this vulnerabilities: WEB APPLICATION RISK SECURITY UTILITY A 1: Injection SQL Inject Me and Zed Attack Proxy (ZAP) A 2: Broken Authentication and Session Management ZAP A 3: Cross-Site Scripting (XSS) ZAP A 4: Insecure Direct Object References HTTP Directory Traversal Scanner, Burp Suite and ZAP A 5: Security Misconfiguration Open. VAS and WATOBO A 6: Sensitive Data Exposure Qualys SSL Server Test A 7: Missing Function Level Access Control Open. VAS A 8: Cross-Site Request Forgery (CSRF) Tamper Data (Samurai WTF), Web. Scarab or ZAP A 9: Using Components with Known Vulnerabilities Open. VAS A 10: Unvalidated Redirects and Forwards ZAP 8

Penetration Testing v v Simulating Attack from a Malicious Source Includes Network Scanning and Vulnerability Scanning Simulates Attack from someone Unfamiliar with the System Simulates Attack by having access to Source Code, Network, Passwords 9

Security testing software tools: OWASP ZAP Metasploit Nessus Vulnerability Scanner Nmap SQLmap W 3 af Burp Suite CORE Impact 10

ZAP Report 11

My starting directions in developing security testing üWhat is security testing ? üWhat are the most common security attacks, technologies, tools ? üDetect vulnerabilities in your software application üFind the right tool that can be used to scan vulnerabilities üWrite Security testing plan üExecute security scan üReport the threats and recommendations 12

Starting directions in developing security testing Ø Ø Ø Ø Study of Security Architecture Analysis of Security Requirements Classifying Security Testing Developing Objectives Threat Modeling Test Planning Execution Reports 13

Thank You 14