Prepare and Defend Against a Software Audit A





- Slides: 13

Prepare and Defend Against a Software Audit A mishandled audit can result in financial consequences far more severe than a slap on the wrist. Info-Tech Research Group, Inc. is a global leader in providing IT research and advice. Info-Tech’s products and services combine actionable insight and relevant advice with Info-Tech's products and services combine actionable insight and advice ready-to-use tools and templates that cover the fullrelevant spectrum of IT with concerns. and templates that cover the full spectrum©of 1997 -2016 IT concerns. © 1997 -Research 2016 Info-Tech Group. Research Inc. Info-Tech Research Group 1

ANALYST PERSPECTIVE A vendor just requested an audit. Is your organization ready? Software audits have been on the rise as vendors attempt to recapture revenue. As licensing rules change on a yearly basis, it is difficult for many organizations to keep up to date. Being ready is critical, as it is a matter of time before there is a knock on the door. Taking preventative measures, in the form of a software asset management (SAM) practice and conducting annual internal audits, will allow your organization to be prepared and potentially avoid the audit altogether. Going on a spending spree to purchase licenses, ignoring the request, or moving to the cloud doesn’t relieve the organization of compliance obligations. Hundreds of thousands of dollars can be saved by having a strategy, knowing the organizational licensing position, and documentation of historical contracts. Scott Bickley Senior Director, Vendor Advisory Practice Info-Tech Research Group 2

Framing the project This Research is Is Designed For: This Research Will Help You: üIT departments attempting to defend a üPrepare for a successful audit üEnsure audit policies and staff behavior licensing audit üCIOs and IT directors with a mandate to build an audit defense strategy for the future üIT asset managers looking to understand software compliance and formalize audit processes üIT managers seeking to understand how to mitigate the risk of adverse findings üManage logistics to minimize business disruptions üManage your audit process üDispute inaccurate findings scope an audit This Research Will Also Assist: This Research Will Help You: Them: üCFOs and the Finance Department üVendor Management üIT/Technology Procurement üMitigate the risk of unplanned non-compliance expenditure and bad PR üDemonstrate a high level of ethics and integrity to the vendor base üObtain a balanced negotiating position with vendors Info-Tech Research Group 3

Executive summary Situation Info-Tech Insight • Software vendors amend licensing rules frequently, making it more 1. As complexity of licensing increases, so do penalties. If the environment is highly complex, prioritize effort by likelihood of audit and spend. difficult to stay compliant, and are increasing the volume of audits. • A failed audit may result in punitive fines and, in extreme cases, injunctions that disrupt continuing operations until violations are resolved. 2. Ensure electronic records exist for Complication • The amount of business disruption depends on the scope of the audit, the size, and the complexity of the organization coupled with the contractual audit clause in the contract. • These highly visible failures can be prevented through effective software asset management practices. 3. license documentation to provide fast access for audit and information requests. Verify accuracy of discovered data. Ensure all devices on the network are being audited. Without a complete discovery process, data will always be inaccurate. Resolution • Being able to respond quickly with accurate data is critical. When deadlines are tight, and internal resources don’t exist, hire a third party – their experience will allow a faster response. • Negotiate terms of the audit such as deadlines, proof of license entitlement, and who will complete the audit. • Create a methodology to quickly and efficiently respond to audit requests. • Conduct annual internal audits according to best practices contained in this research. Info-Tech Research Group 4

Apply audit management best practices and protect your company Prepare and prevent Deal with the audit • • • Understand red flags Conduct an internal audit Build an effective licensing positon How to communicate with vendors How to reduce the risk of adverse findings • • Clarify audit scope How to respond Which terms to negotiate What to expect Preventative practices can help find measured value ($) Cost of audit process Resource allocation and time Disruption to business During the audit Post-audit • • What to do and not to do Communication with staff Controls to implement if auditor comes on site Negotiate preliminary audit findings • • Examine auditor report and recommendations Understanding root causes Understand consequences to organization and develop action plan Build audit capabilities for the future Shortfall payment Penalties and back support Third-party, legal/SAM partners Info-Tech Research Group 5

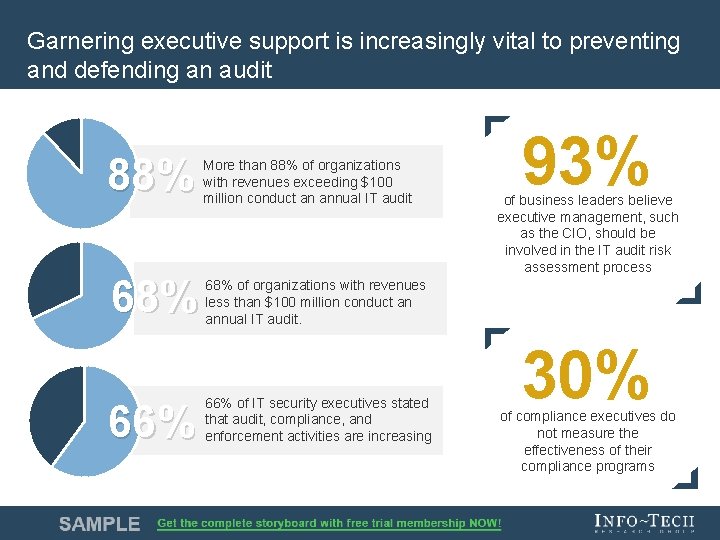
Garnering executive support is increasingly vital to preventing and defending an audit 88% More than 88% of organizations with revenues exceeding $100 million conduct an annual IT audit 68% of organizations with revenues less than $100 million conduct an annual IT audit. 66% of IT security executives stated that audit, compliance, and enforcement activities are increasing 93% of business leaders believe executive management, such as the CIO, should be involved in the IT audit risk assessment process 30% of compliance executives do not measure the effectiveness of their compliance programs Info-Tech Research Group 6

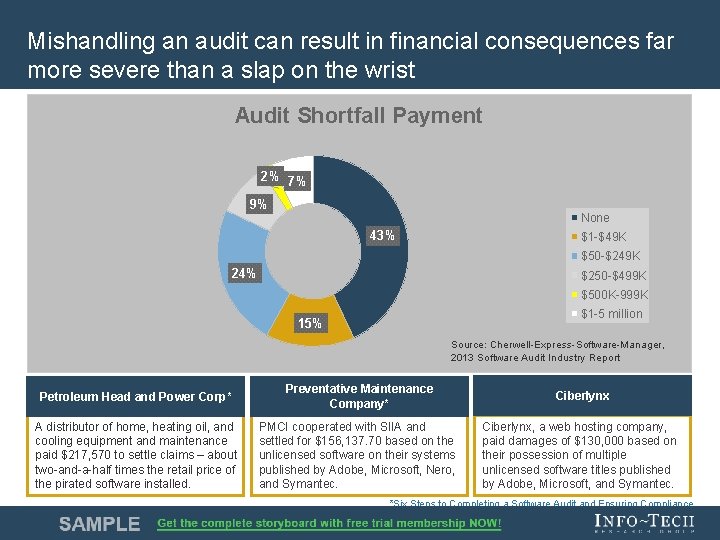
Mishandling an audit can result in financial consequences far more severe than a slap on the wrist Audit Shortfall Payment 2% 7% 9% None 43% $1 -$49 K $50 -$249 K 24% $250 -$499 K $500 K-999 K $1 -5 million 15% Source: Cherwell-Express-Software-Manager, 2013 Software Audit Industry Report Petroleum Head and Power Corp* Preventative Maintenance Company* Ciberlynx A distributor of home, heating oil, and cooling equipment and maintenance paid $217, 570 to settle claims – about two-and-a-half times the retail price of the pirated software installed. PMCI cooperated with SIIA and settled for $156, 137. 70 based on the unlicensed software on their systems published by Adobe, Microsoft, Nero, and Symantec. Ciberlynx, a web hosting company, paid damages of $130, 000 based on their possession of multiple unlicensed software titles published by Adobe, Microsoft, and Symantec. *Six Steps to Completing a Software Audit and Ensuring Compliance Info-Tech Research Group 7

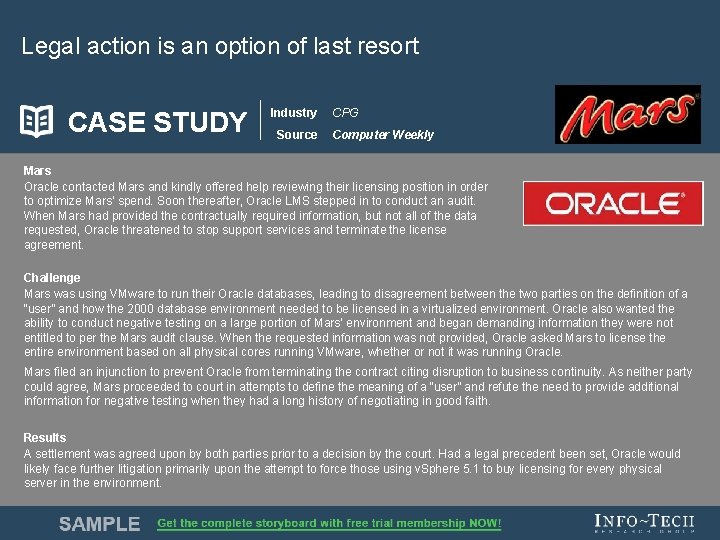
Legal action is an option of last resort CASE STUDY Industry Source CPG Computer Weekly Mars Oracle contacted Mars and kindly offered help reviewing their licensing position in order to optimize Mars’ spend. Soon thereafter, Oracle LMS stepped in to conduct an audit. When Mars had provided the contractually required information, but not all of the data requested, Oracle threatened to stop support services and terminate the license agreement. Challenge Mars was using VMware to run their Oracle databases, leading to disagreement between the two parties on the definition of a “user” and how the 2000 database environment needed to be licensed in a virtualized environment. Oracle also wanted the ability to conduct negative testing on a large portion of Mars’ environment and began demanding information they were not entitled to per the Mars audit clause. When the requested information was not provided, Oracle asked Mars to license the entire environment based on all physical cores running VMware, whether or not it was running Oracle. Mars filed an injunction to prevent Oracle from terminating the contract citing disruption to business continuity. As neither party could agree, Mars proceeded to court in attempts to define the meaning of a “user” and refute the need to provide additional information for negative testing when they had a long history of negotiating in good faith. Results A settlement was agreed upon by both parties prior to a decision by the court. Had a legal precedent been set, Oracle would likely face further litigation primarily upon the attempt to force those using v. Sphere 5. 1 to buy licensing for every physical server in the environment. Info-Tech Research Group 8

Use these icons to help direct you as you navigate this research Use these icons to help guide you through each step of the blueprint and direct you to content related to the recommended activities. This icon denotes a slide where a supporting Info-Tech tool or template will help you perform the activity or step associated with the slide. Refer to the supporting tool or template to get the best results and proceed to the next step of the project. This icon denotes a slide with an associated activity. The activity can be performed either as part of your project or with the support of Info-Tech team members, who will come onsite to facilitate a workshop for your organization. Info-Tech Research Group 9

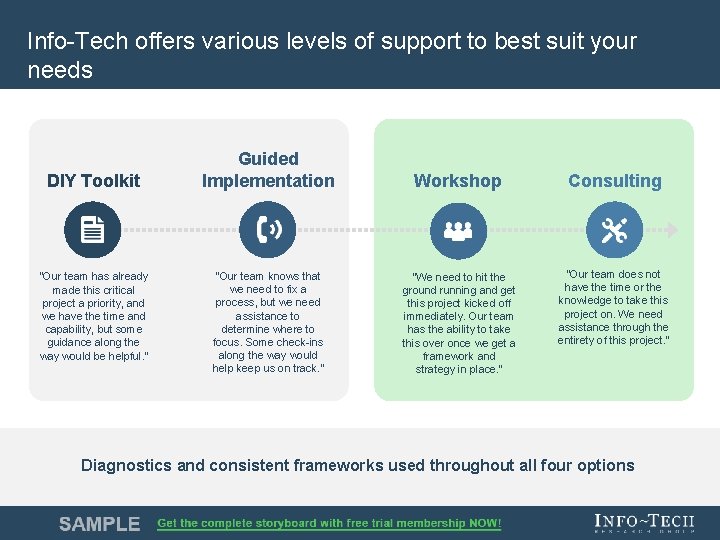
Info-Tech offers various levels of support to best suit your needs DIY Toolkit “Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful. ” Guided Implementation Workshop Consulting “Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track. ” “We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place. ” “Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project. ” Diagnostics and consistent frameworks used throughout all four options Info-Tech Research Group 10

Prepare and Defend Against a Software Audit Project Overview Prevent an audit 1. 1 Audits are on the rise 1. 2 Conduct a maturity assessment and internal audit 1. 3 Build a cross-functional audit team Best-Practice Toolkit Guided Implementations Onsite Workshop Prepare for an audit 2. 1 Create an audit strategy and process for the when an audit notification is received 2. 2 Understand types of requests and how to respond Conduct the audit Manage postaudit activities 3. 1 Ensure the audit allows for business continuity 4. 1 Conduct an exit meeting to negotiate findings 3. 2 Mitigate the risk of damaging findings 4. 2 Decipher results and tactfully deal with negative findings 2. 3 Define the scope of the audit 4. 3 Negotiate payment and close out the audit Red flags leading to increased odds of an audit Steps to take upon notification Overview of processes conducted Discuss the results of the audit Maturity assessment and conducting an internal audit Examine the various engagement requests from self-audit to formal Kick off and discuss the confirmed audit scope Discuss the validity of the findings Structuring and preparing an audit team Defining the scope and how to respond Prioritize business continuity Negotiation terms and close out Working with auditor personality types Module 1: Prevent an Audit Module 2: Prepare Staff and Management Module 3: Conduct the Audit Effectively Module 4: Manage Post-Audit Activities Phase 1 Results: • Audit defense starts long before you get audited. Maintaining a documented consolidated licensing position ensures that you are not blindsided by a sudden audit request. Phase 2 Results: • Don’t panic when you receive a notification. Take control of the situation and prepare a measured response. Phase 3 Results: • Kick off and understand the audit process. The vendor’s approach towards compliance will dictate what motivates them, how they operate, and how you should work with them. Phase 4 Results: • Leave knowing what hands you lost and why. Come to a consensus on which findings truly necessitate organizational change. Info-Tech Research Group 11

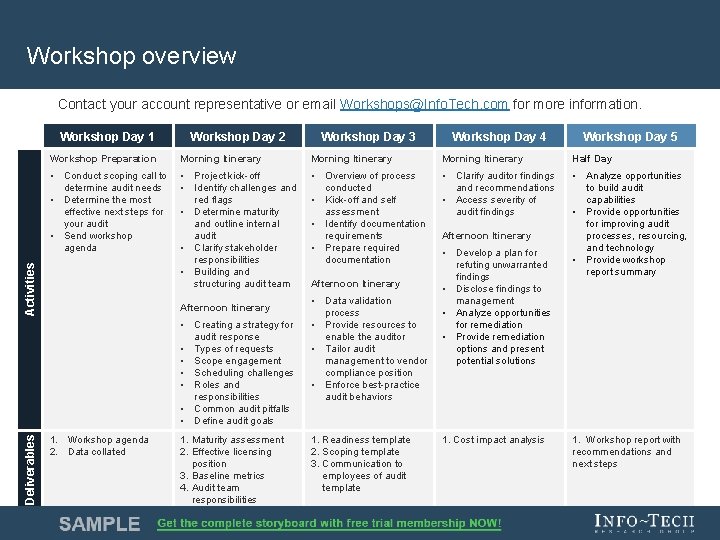
Workshop overview Contact your account representative or email Workshops@Info. Tech. com for more information. Workshop Day 1 Workshop Day 2 Workshop Day 4 Workshop Day 5 Morning Itinerary Half Day • Conduct scoping call to determine audit needs • Determine the most effective next steps for your audit • Send workshop agenda • Project kick-off • Identify challenges and red flags • Determine maturity and outline internal audit • Clarify stakeholder responsibilities • Building and structuring audit team • Overview of process conducted • Kick-off and self assessment • Identify documentation requirements • Prepare required documentation • Clarify auditor findings and recommendations • Access severity of audit findings • Analyze opportunities to build audit capabilities • Provide opportunities for improving audit processes, resourcing, and technology • Provide workshop report summary Activities Workshop Preparation Afternoon Itinerary • Creating a strategy for audit response • Types of requests • Scope engagement • Scheduling challenges • Roles and responsibilities • Common audit pitfalls • Define audit goals Deliverables Workshop Day 3 1. Workshop agenda 2. Data collated 1. Maturity assessment 2. Effective licensing position 3. Baseline metrics 4. Audit team responsibilities Afternoon Itinerary • Data validation process • Provide resources to enable the auditor • Tailor audit management to vendor compliance position • Enforce best-practice audit behaviors 1. Readiness template 2. Scoping template 3. Communication to employees of audit template Afternoon Itinerary • Develop a plan for refuting unwarranted findings • Disclose findings to management • Analyze opportunities for remediation • Provide remediation options and present potential solutions 1. Cost impact analysis 1. Workshop report with recommendations and next steps Info-Tech Research Group 12

Info-Tech Research Group Helps IT Professionals To: ü ü ü Quickly get up to speed with new technologies ü Manage business expectations ü Justify IT spending and prove the value of IT ü Train IT staff and effectively manage an IT department Make the right technology purchasing decisions – fast Deliver critical IT projects, on time and within budget Sign up for free trial membership to get practical solutions for your IT challenges • “Info-Tech helps me to be proactive instead of reactive – a cardinal rule in a stable and leading edge IT environment. - ARCS Commercial Mortgage Co. , LP Toll Free: 1 -888 -670 -8889 www. infotech. com Info-Tech Research Group 13